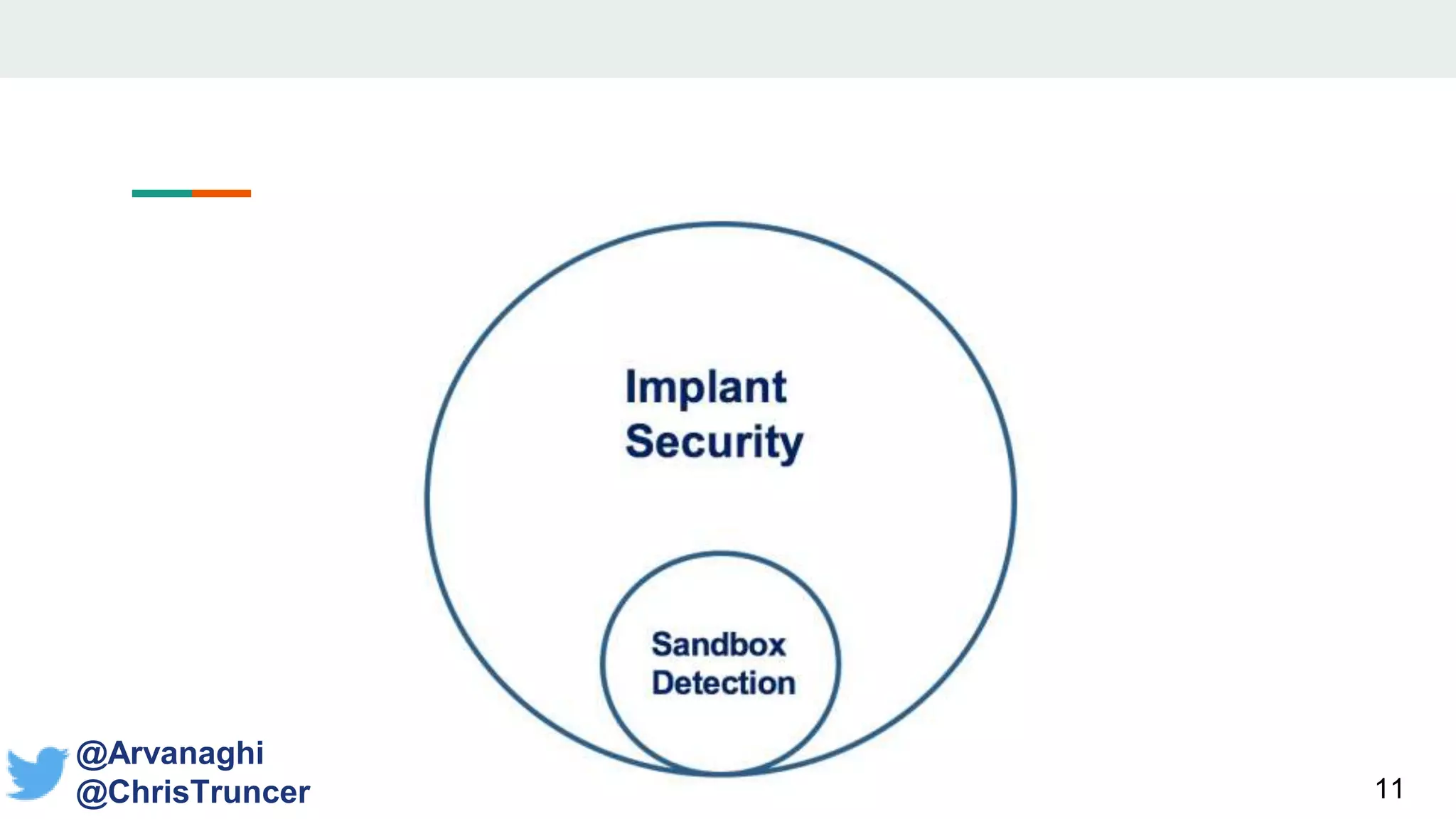
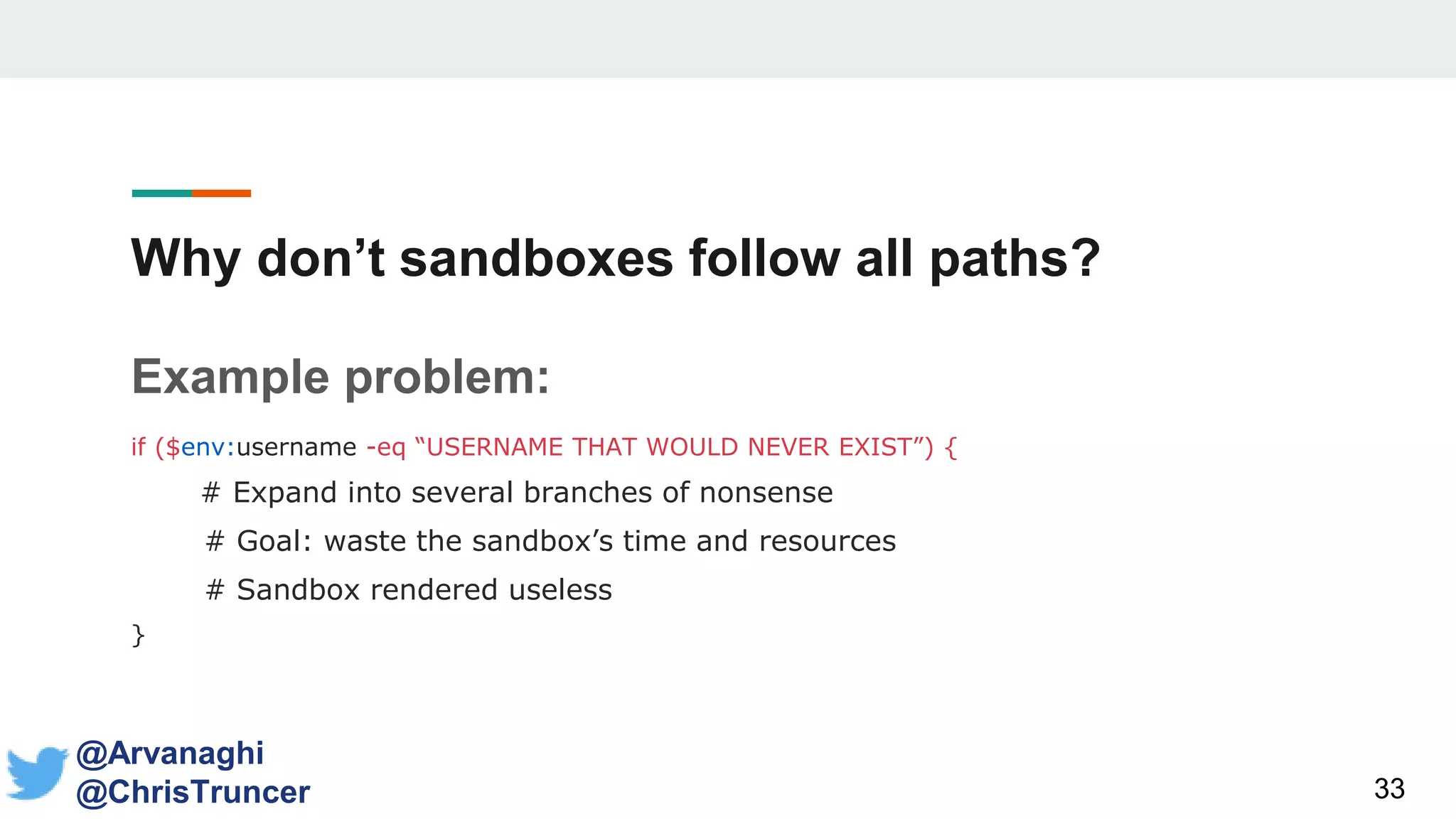
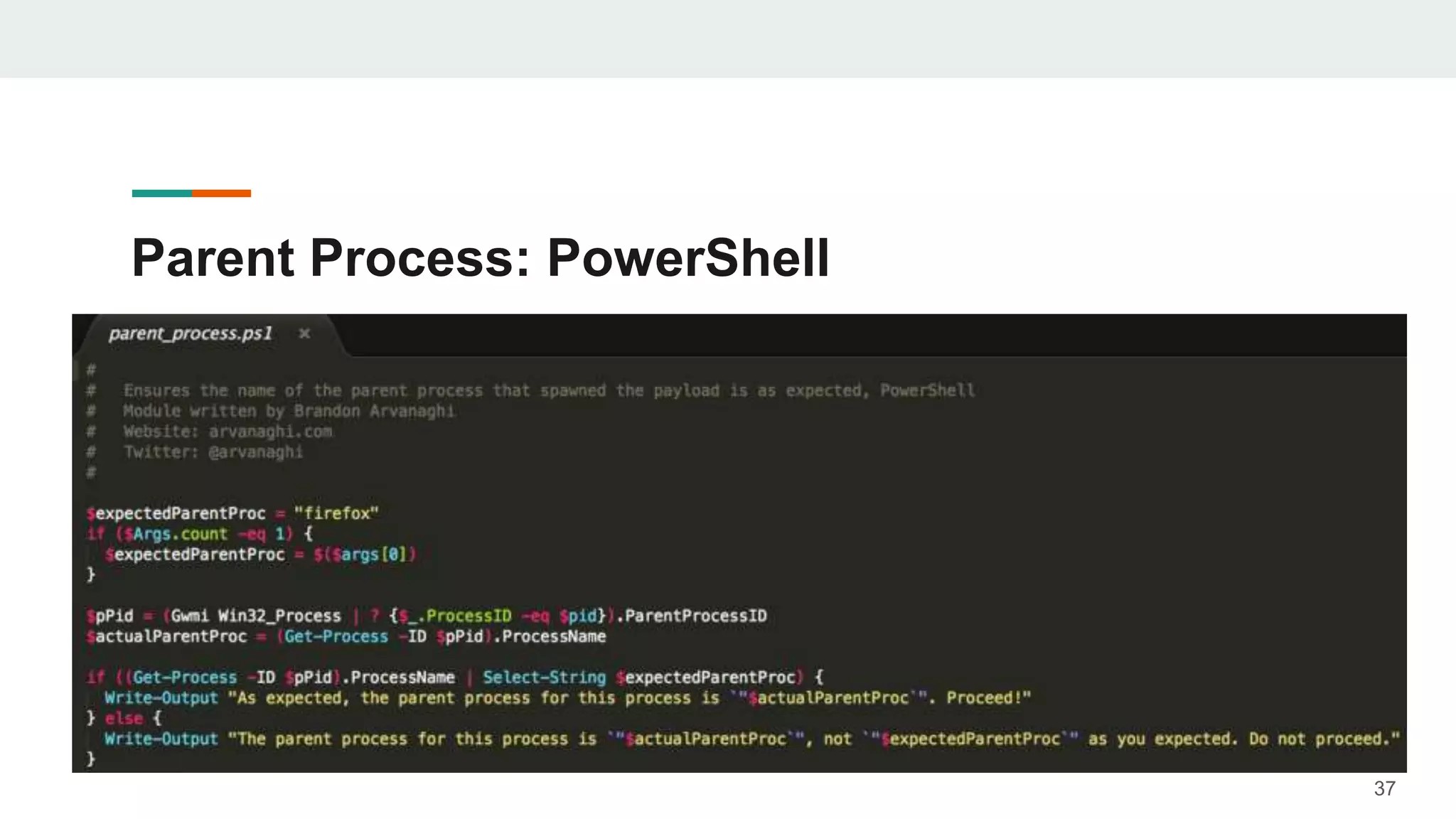
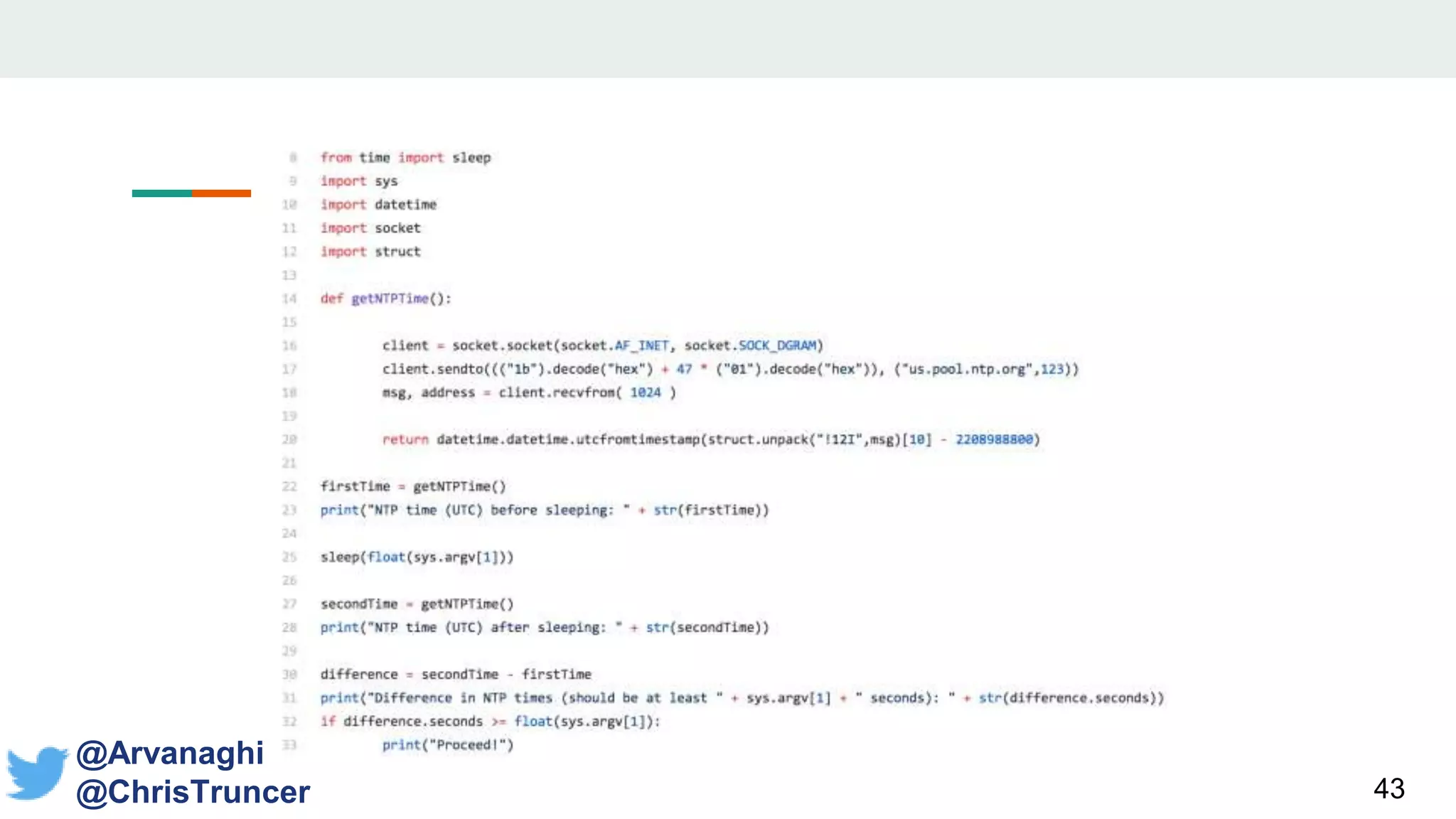
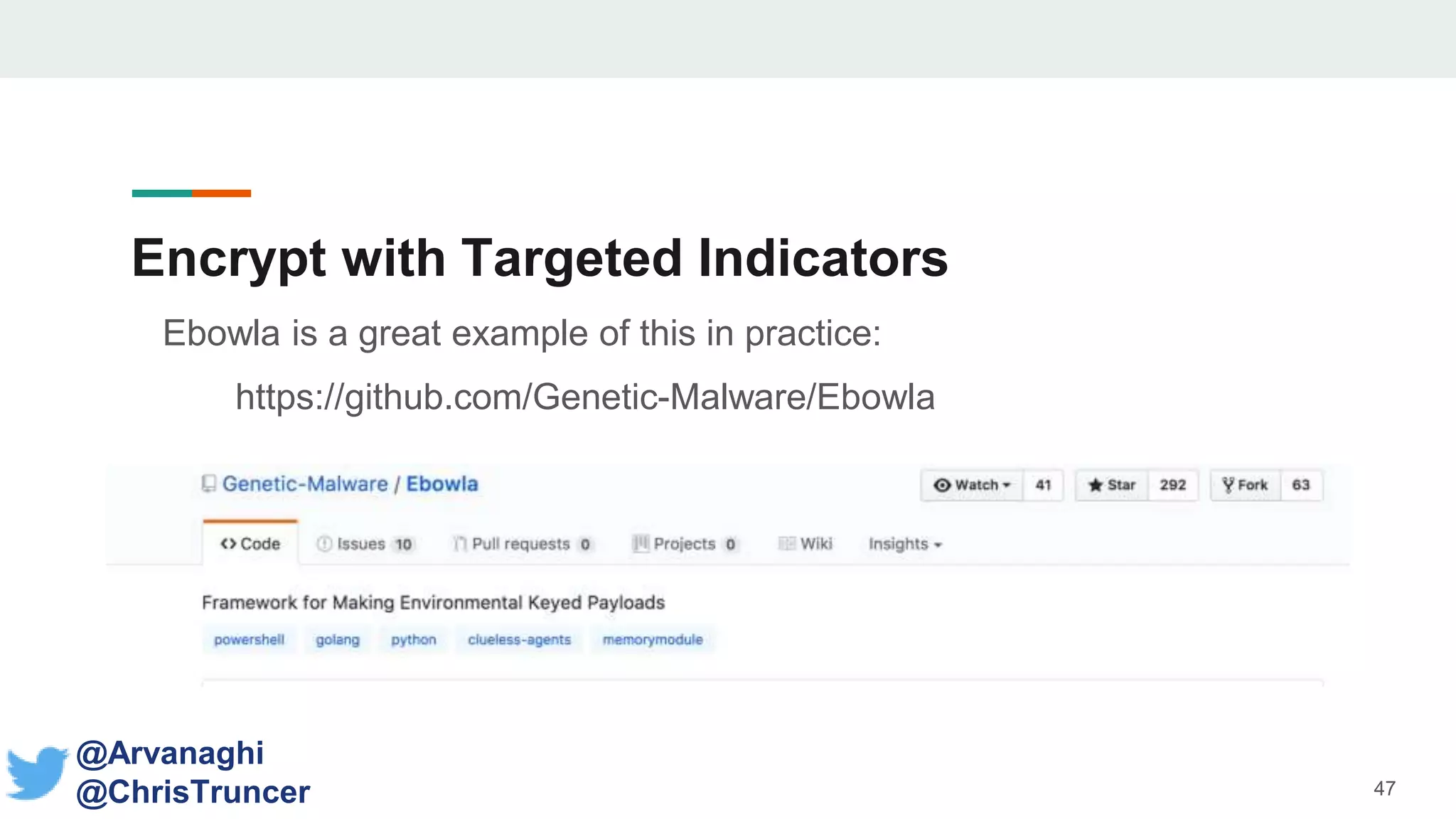
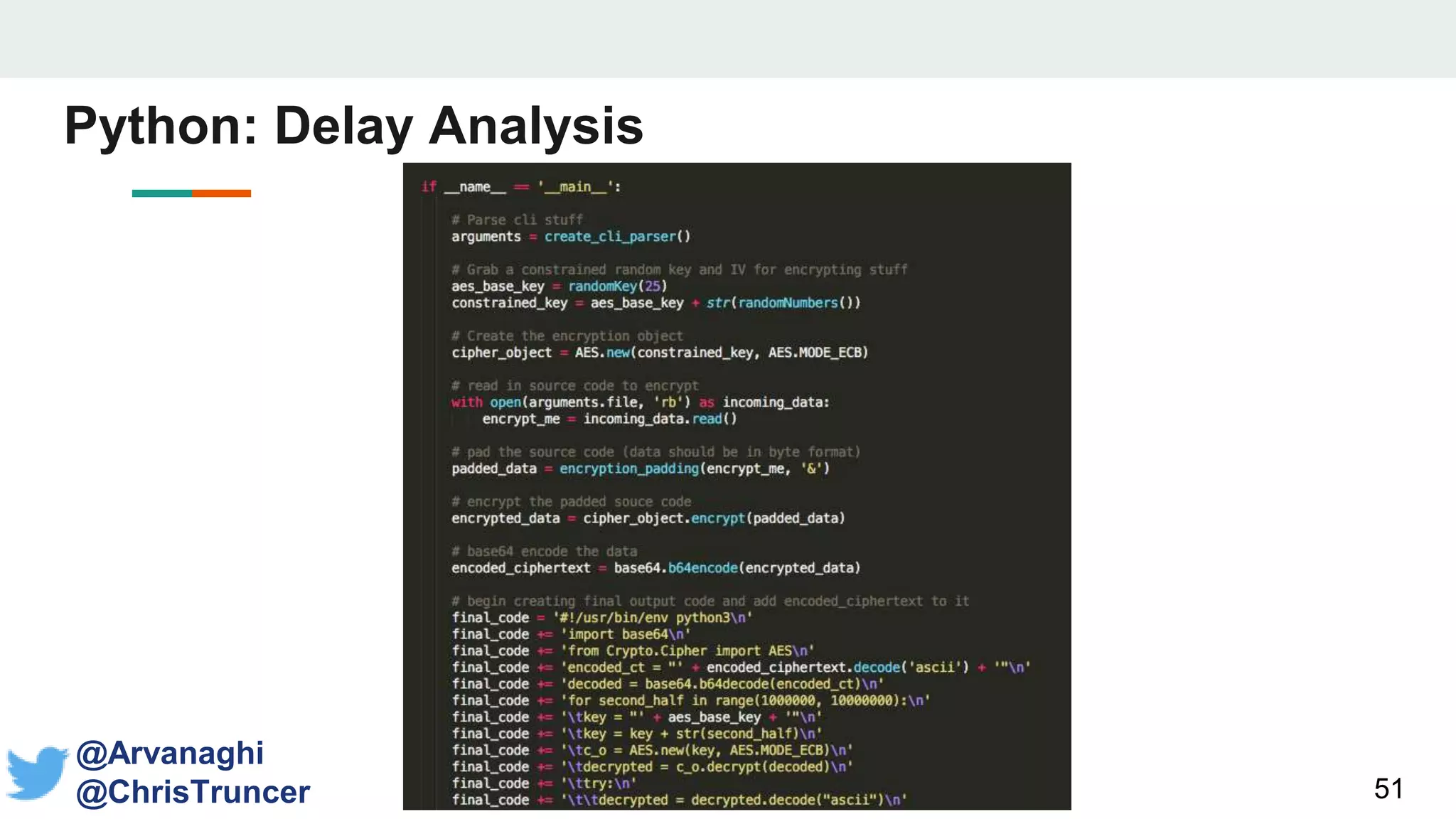
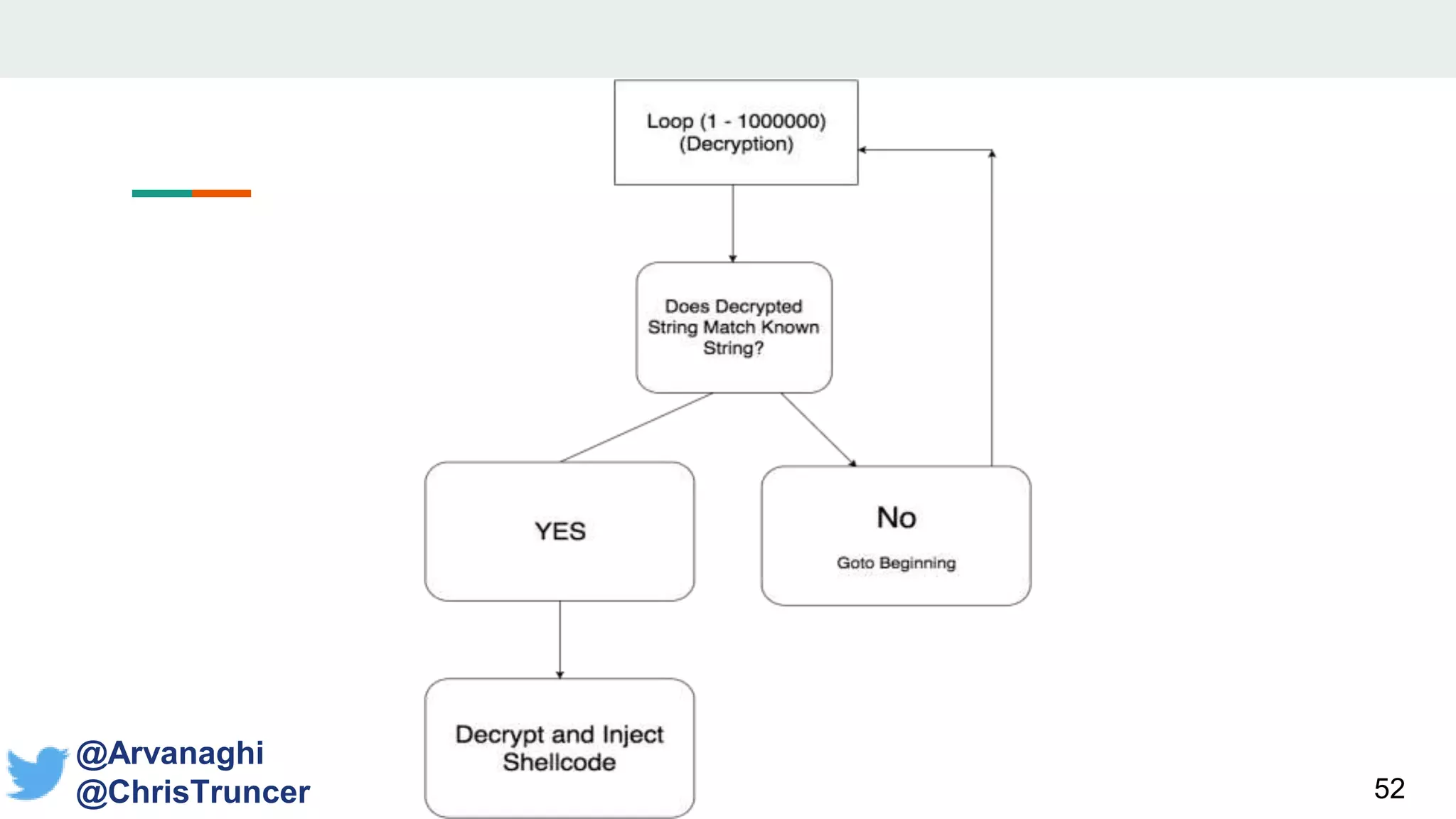
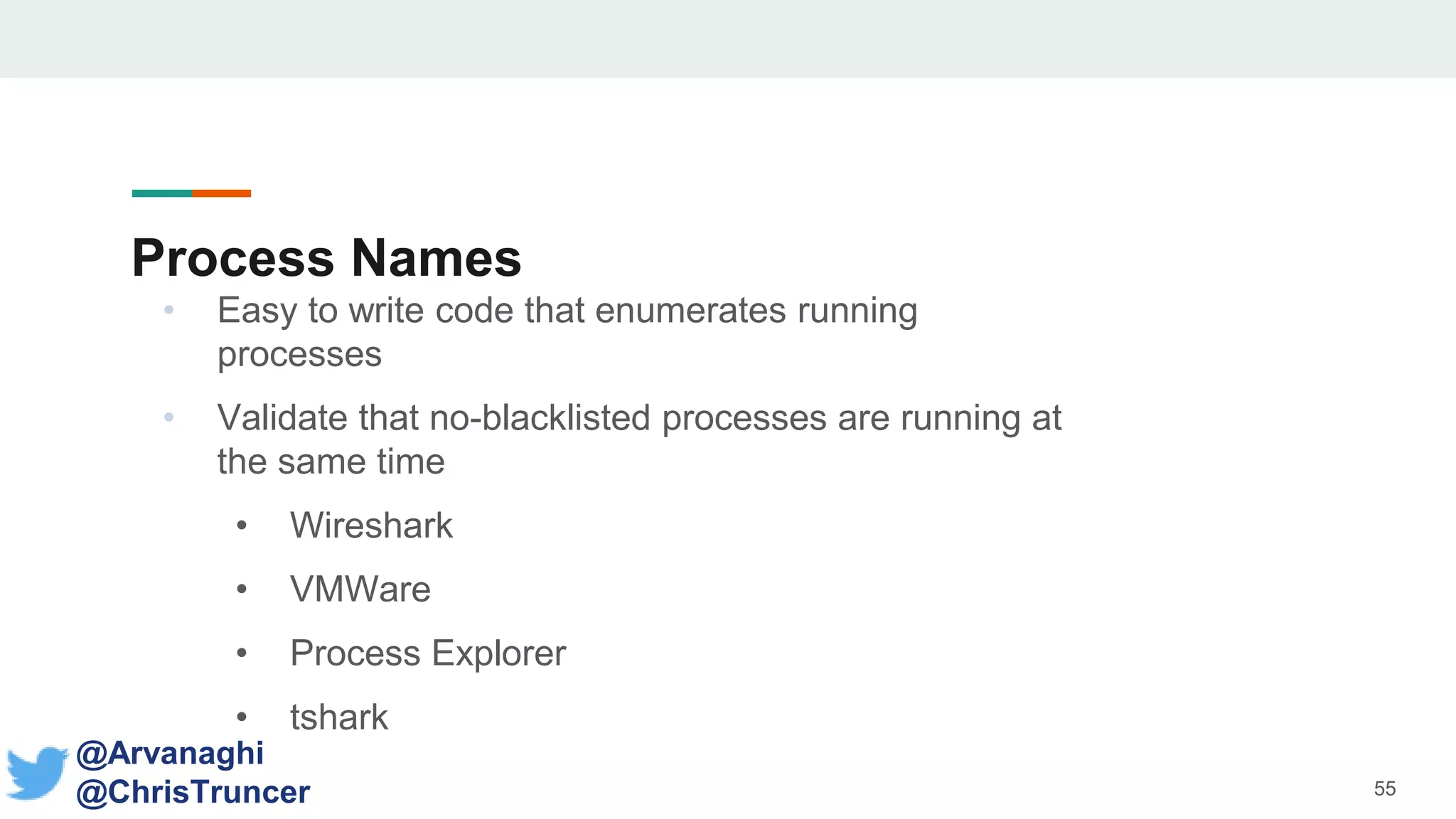
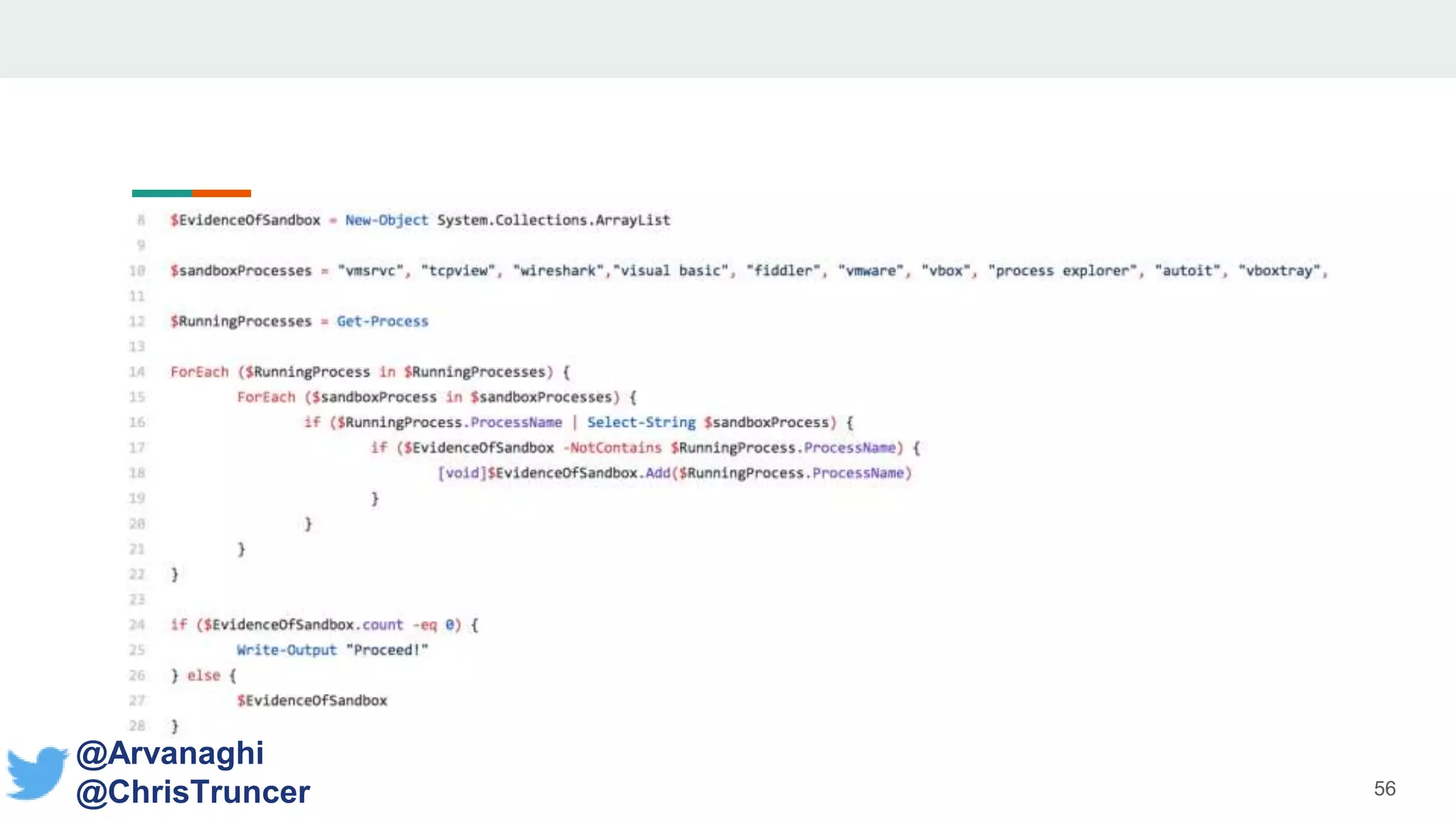
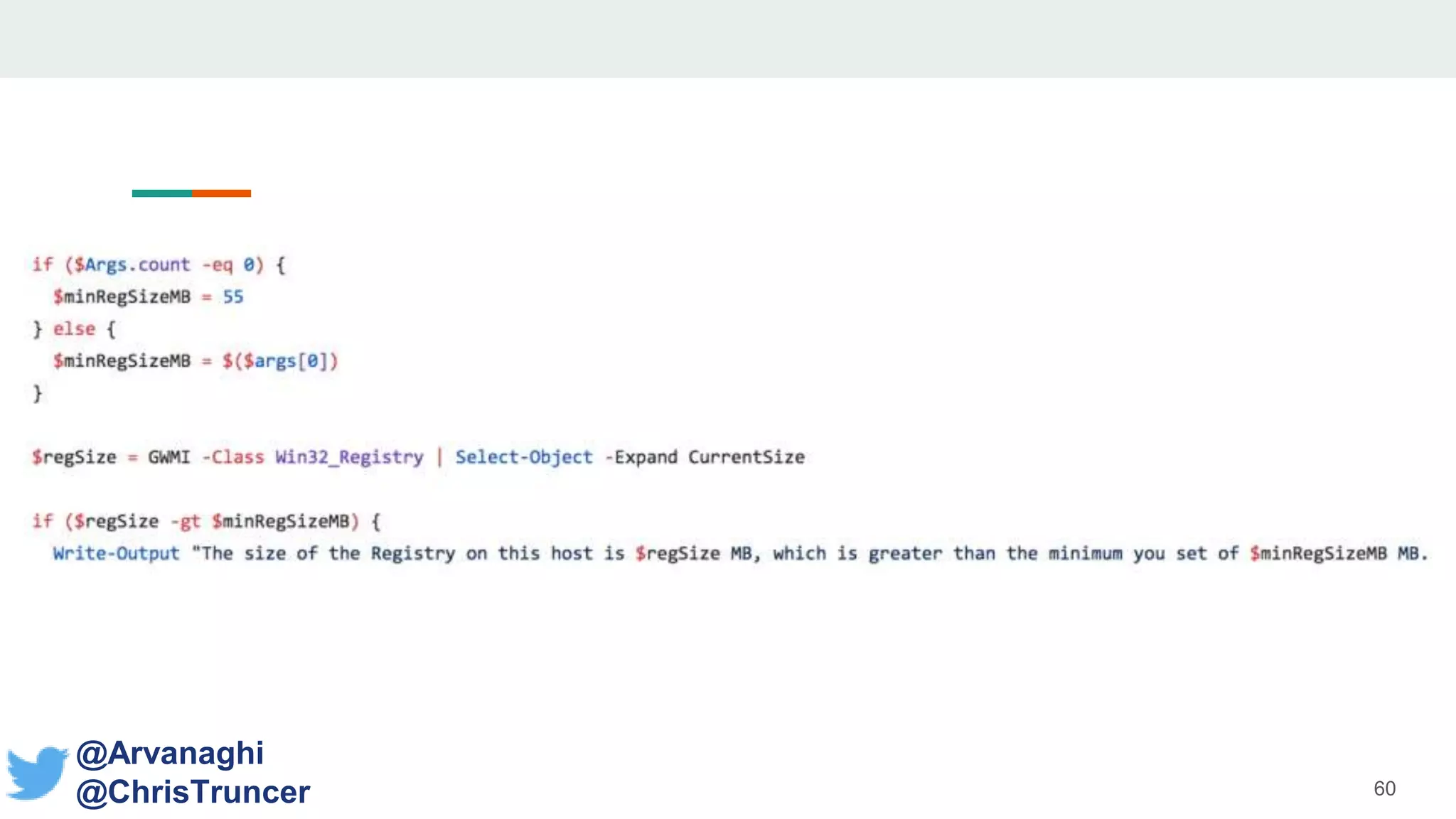
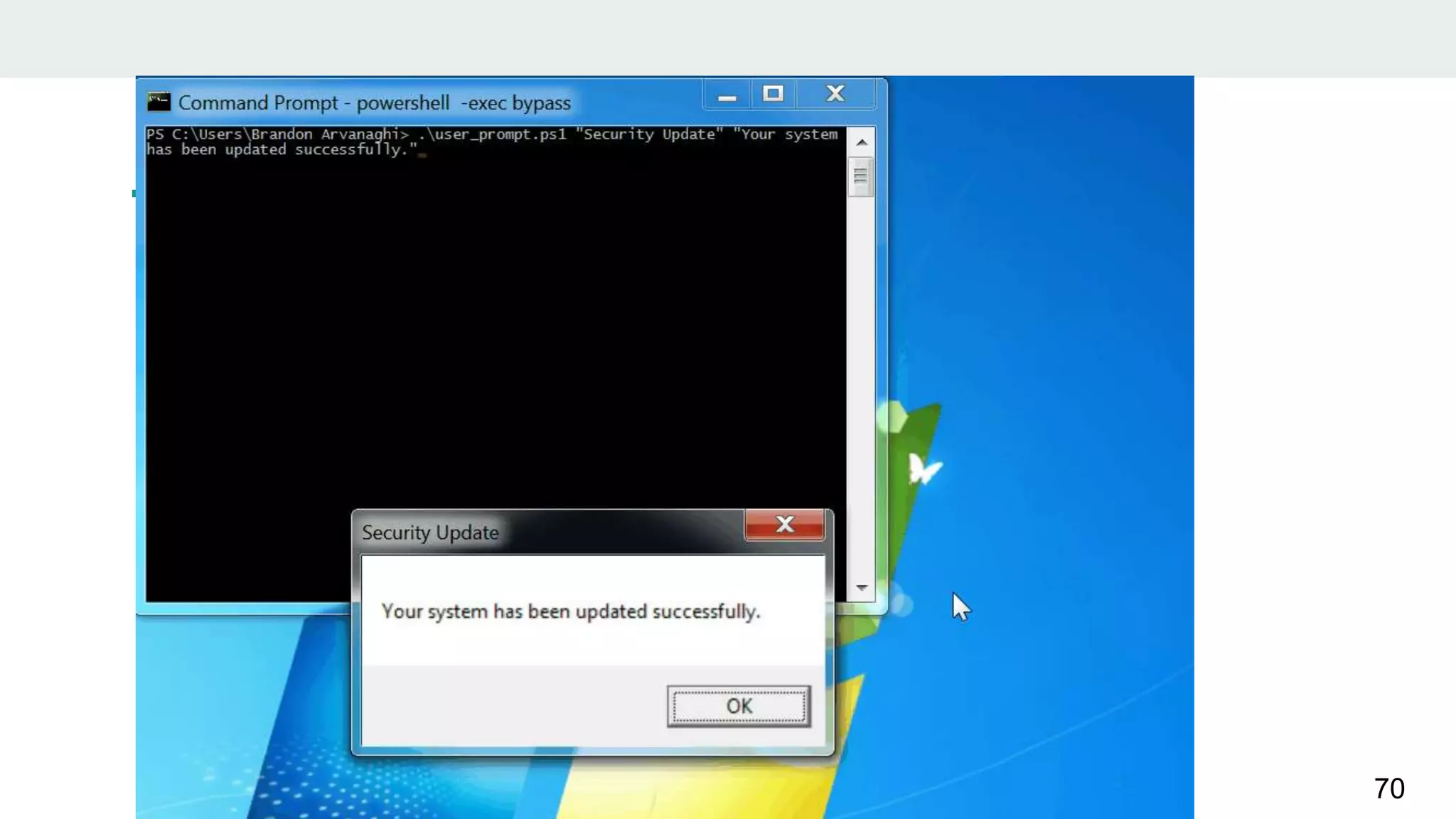
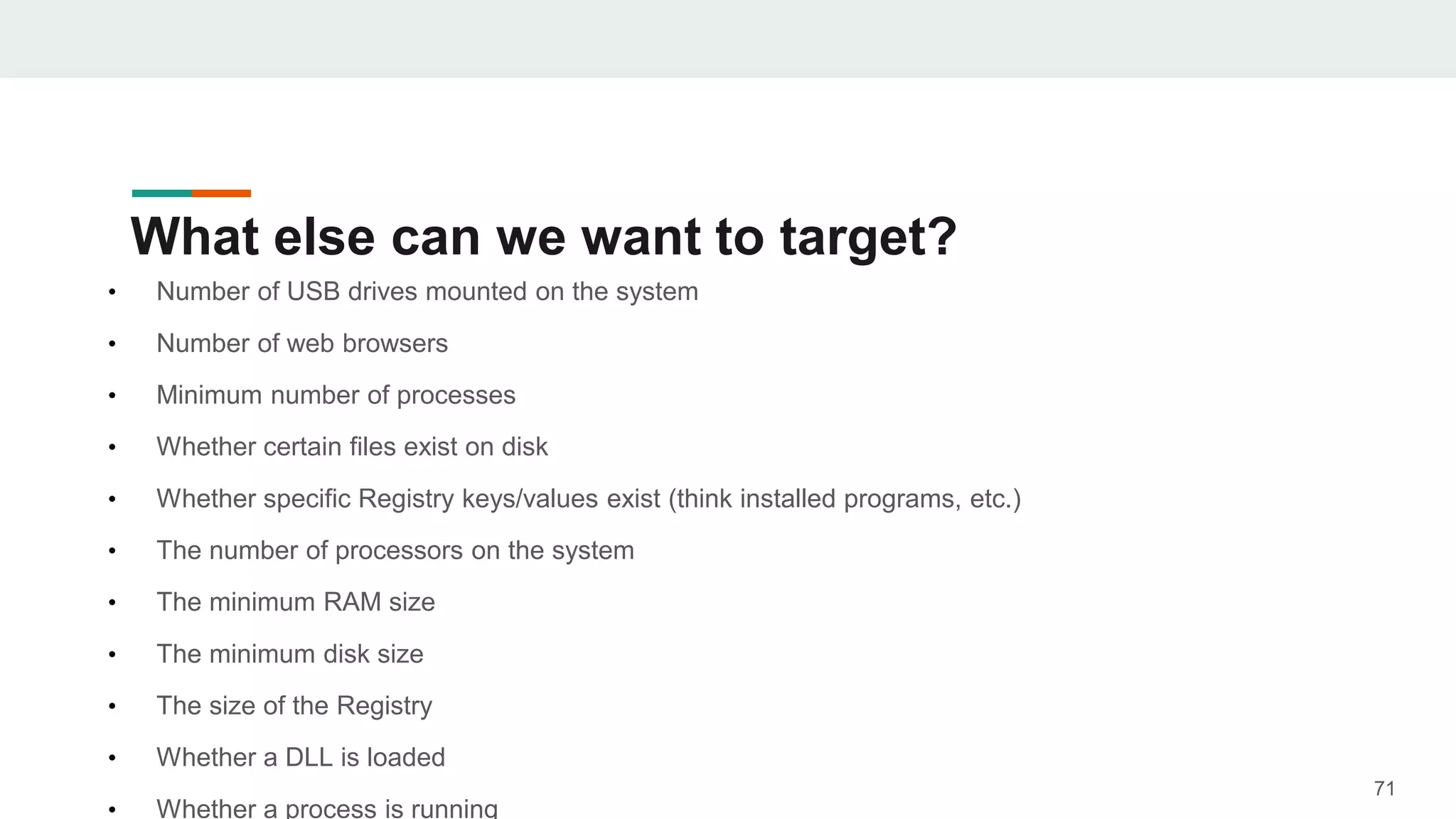
- The document discusses techniques for making payloads more targeted and resistant to sandbox analysis, including checking for expected parent processes, encrypting payloads with host-specific keys, and checking for signs of user interaction.
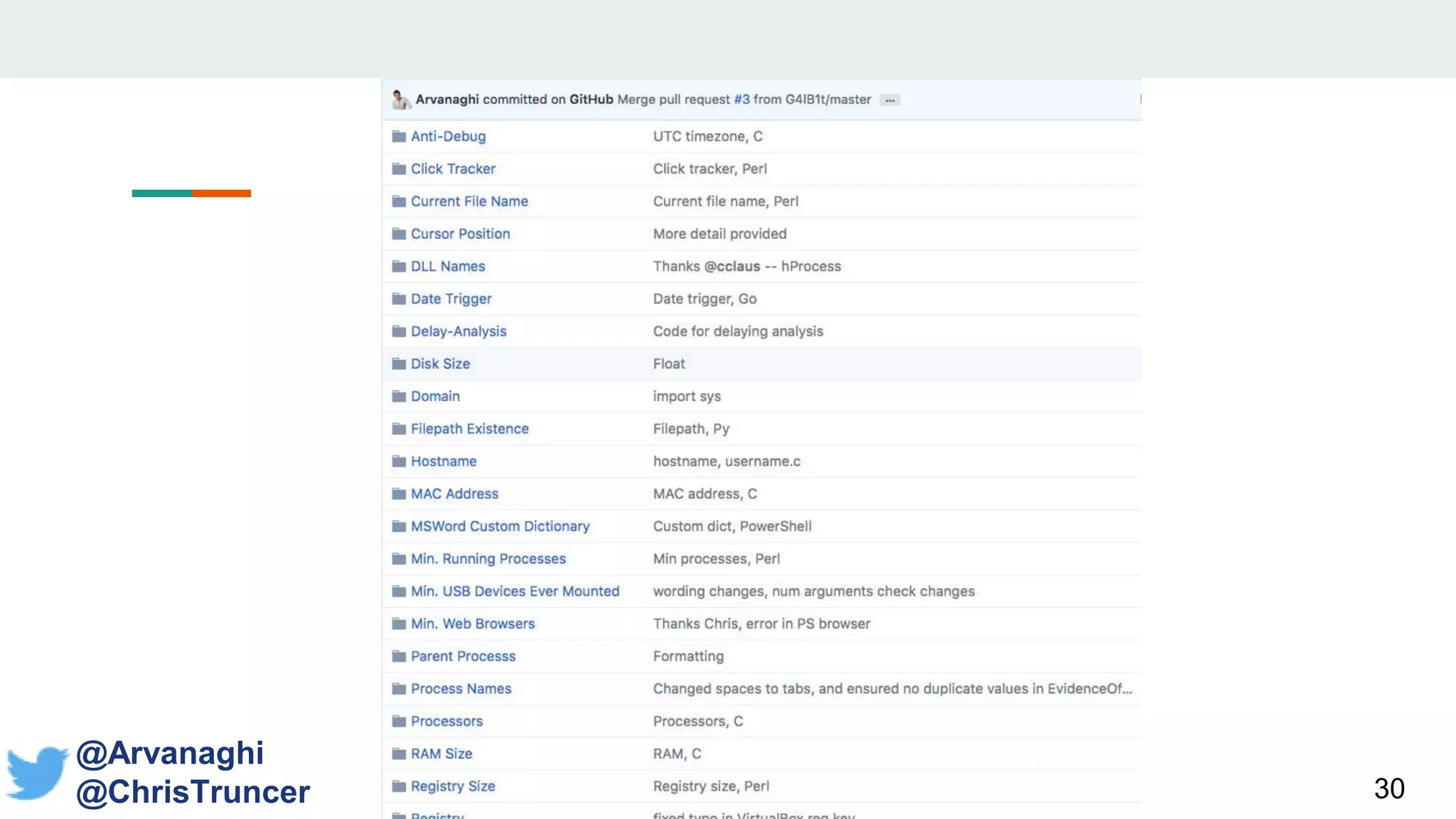
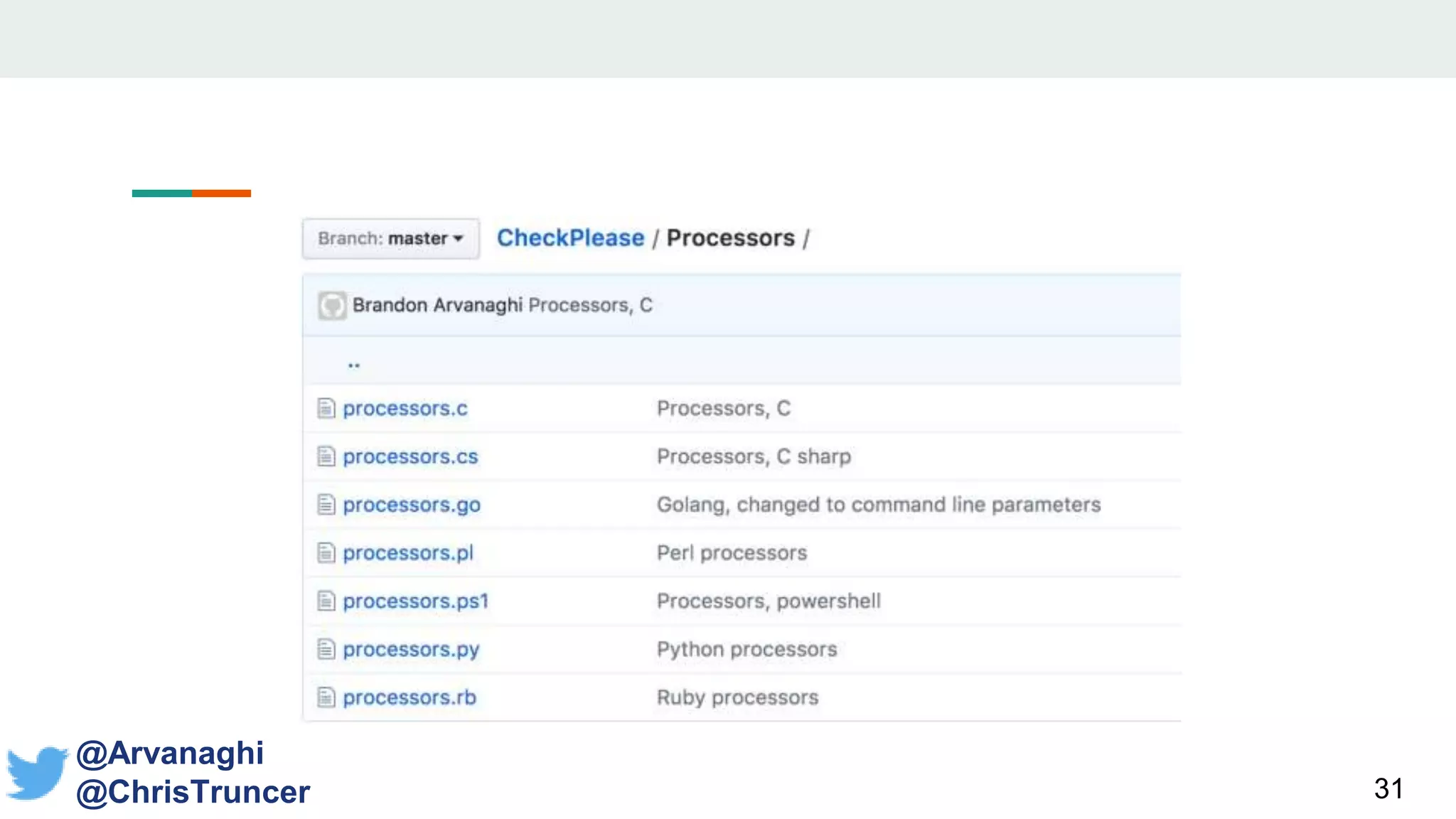
- It proposes a new open-source library called "CheckPlease" that implements these techniques across multiple programming languages to help red and blue teams.
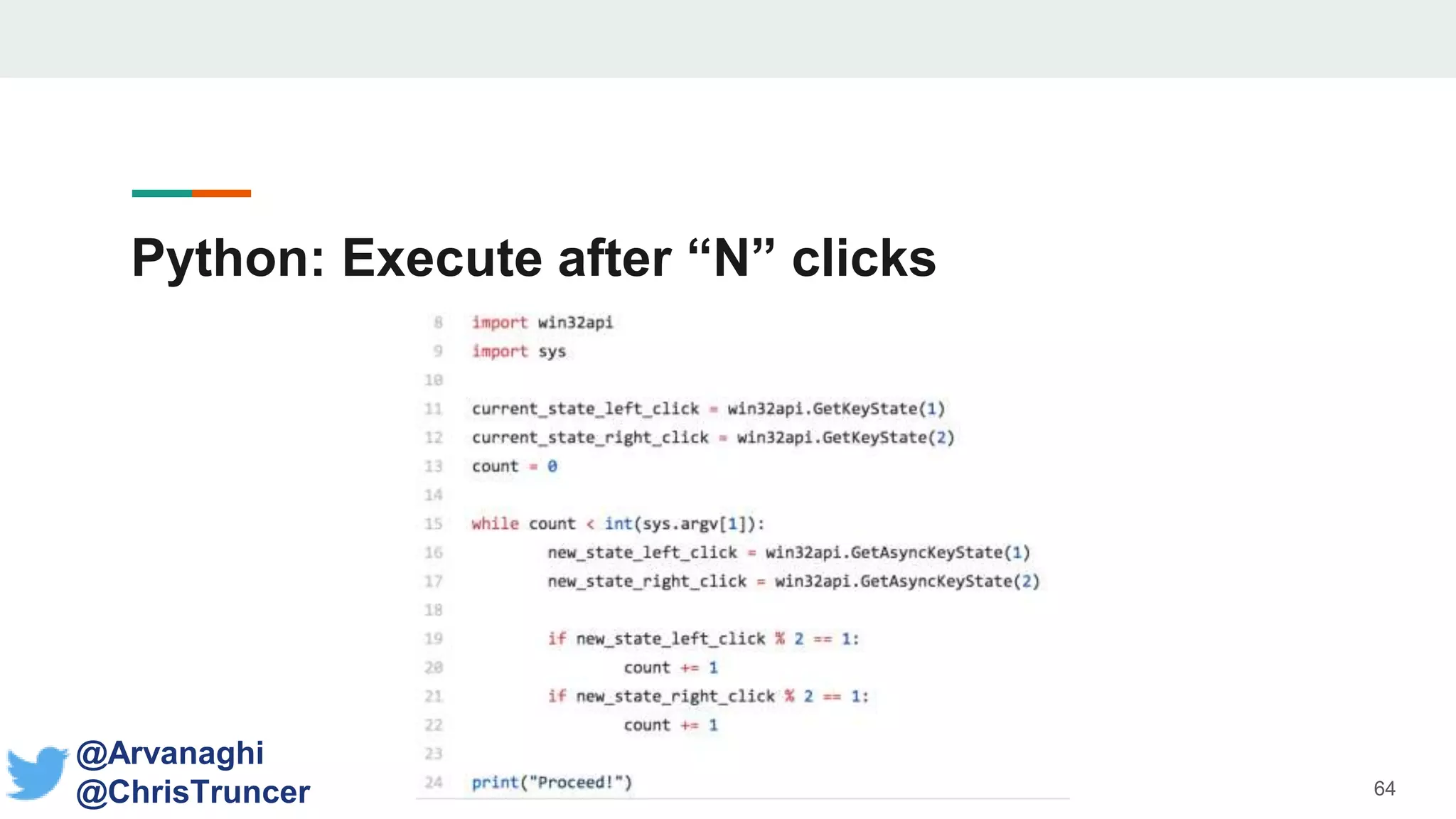
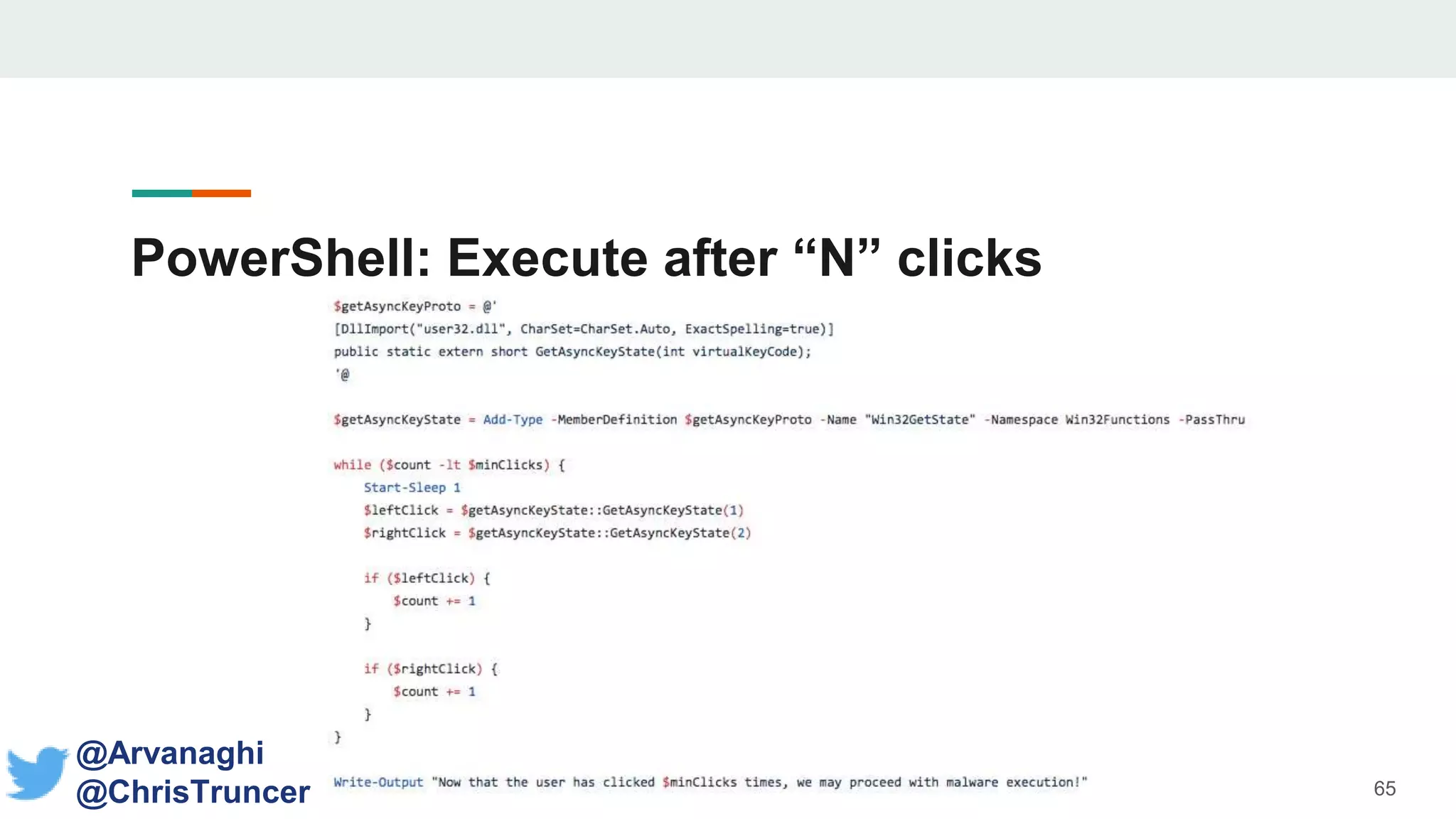
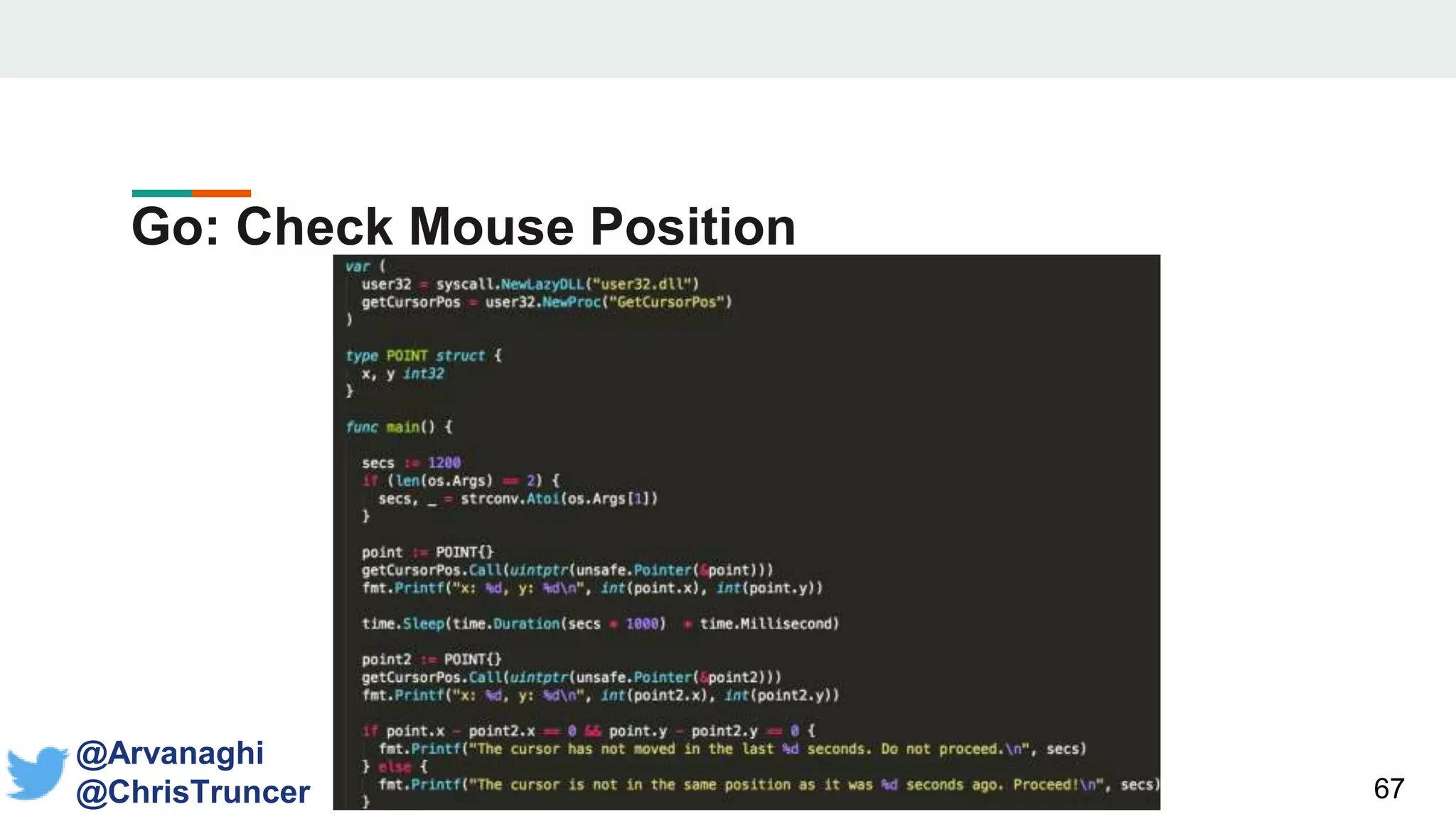
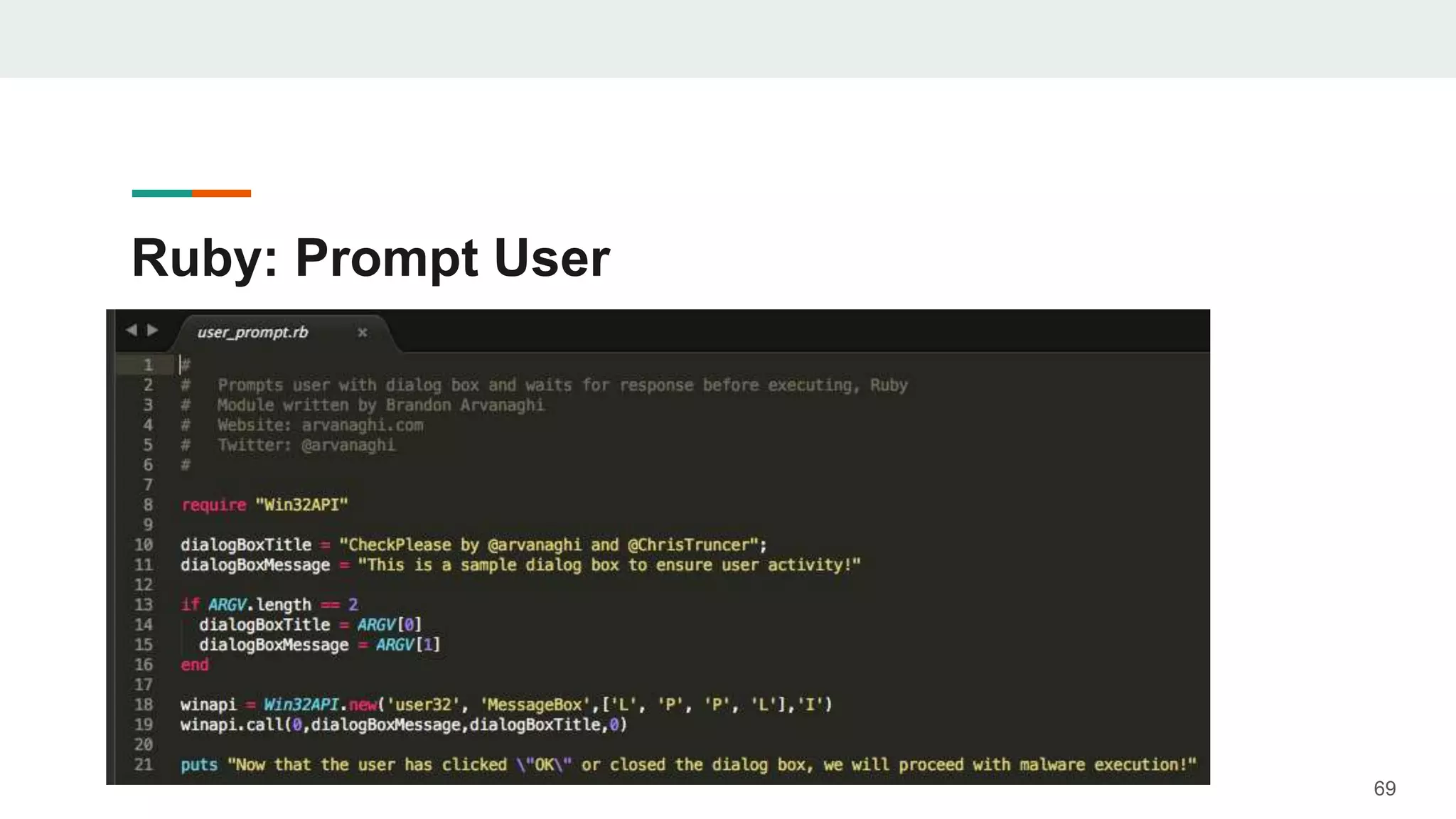
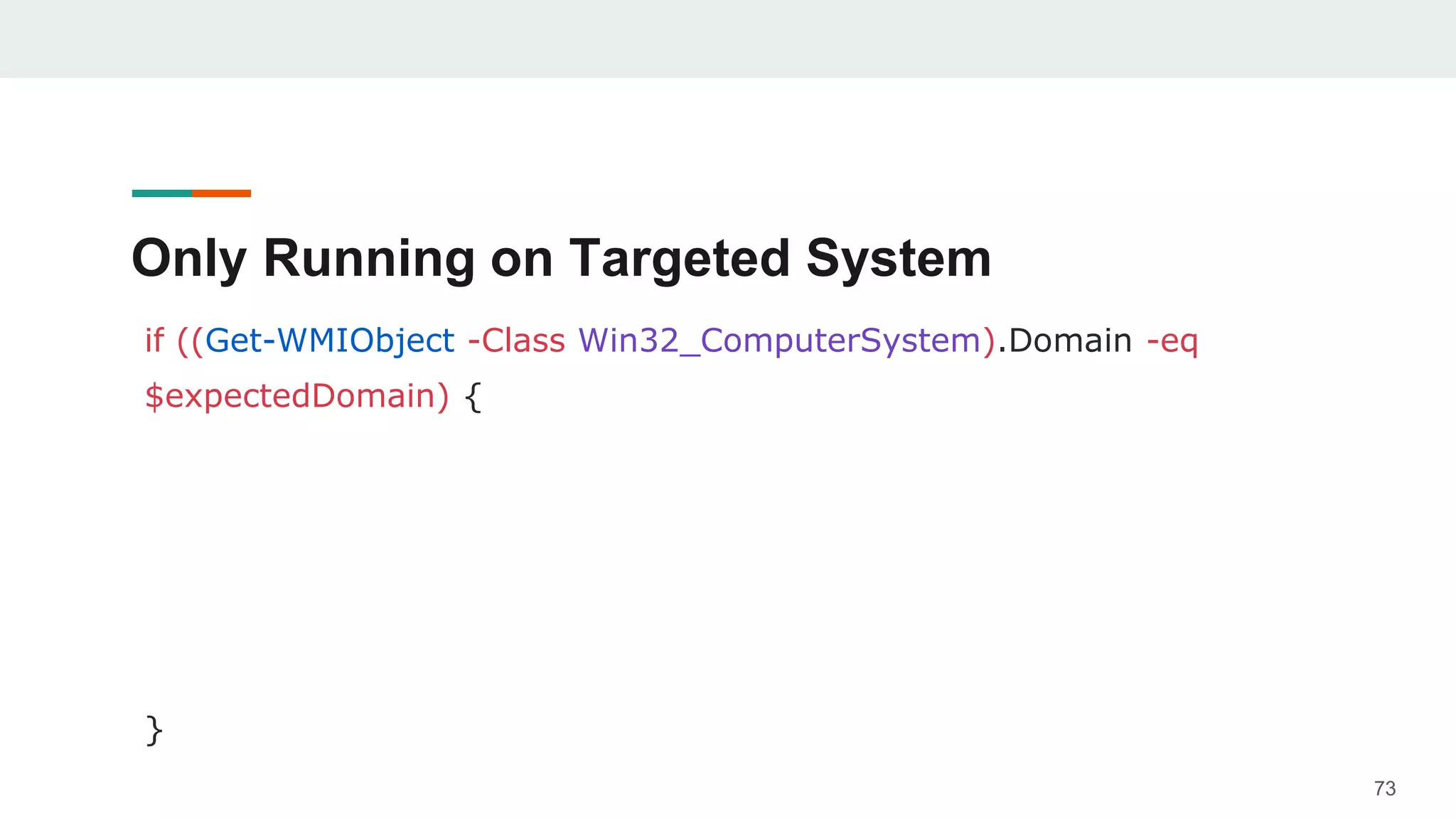
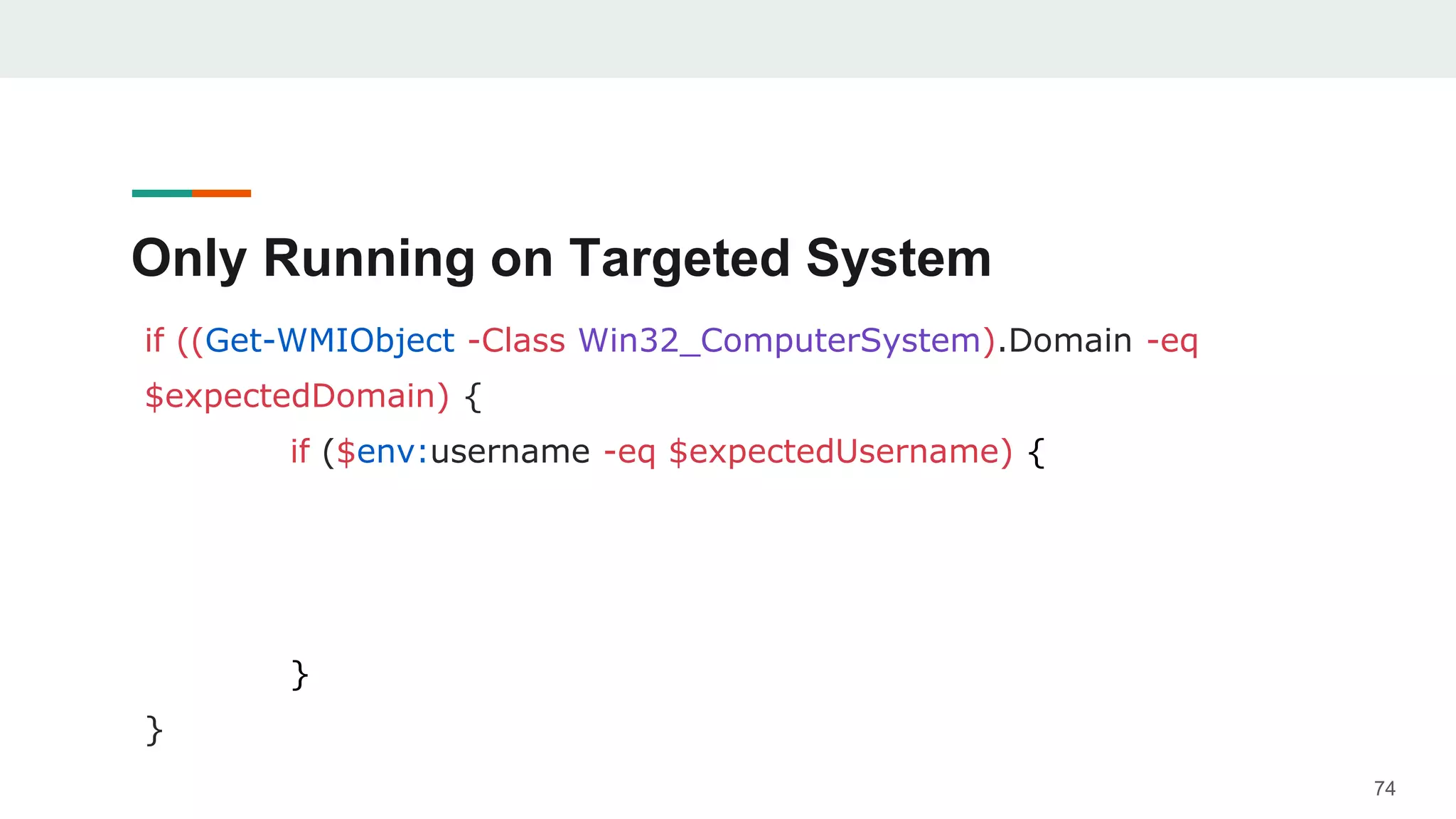
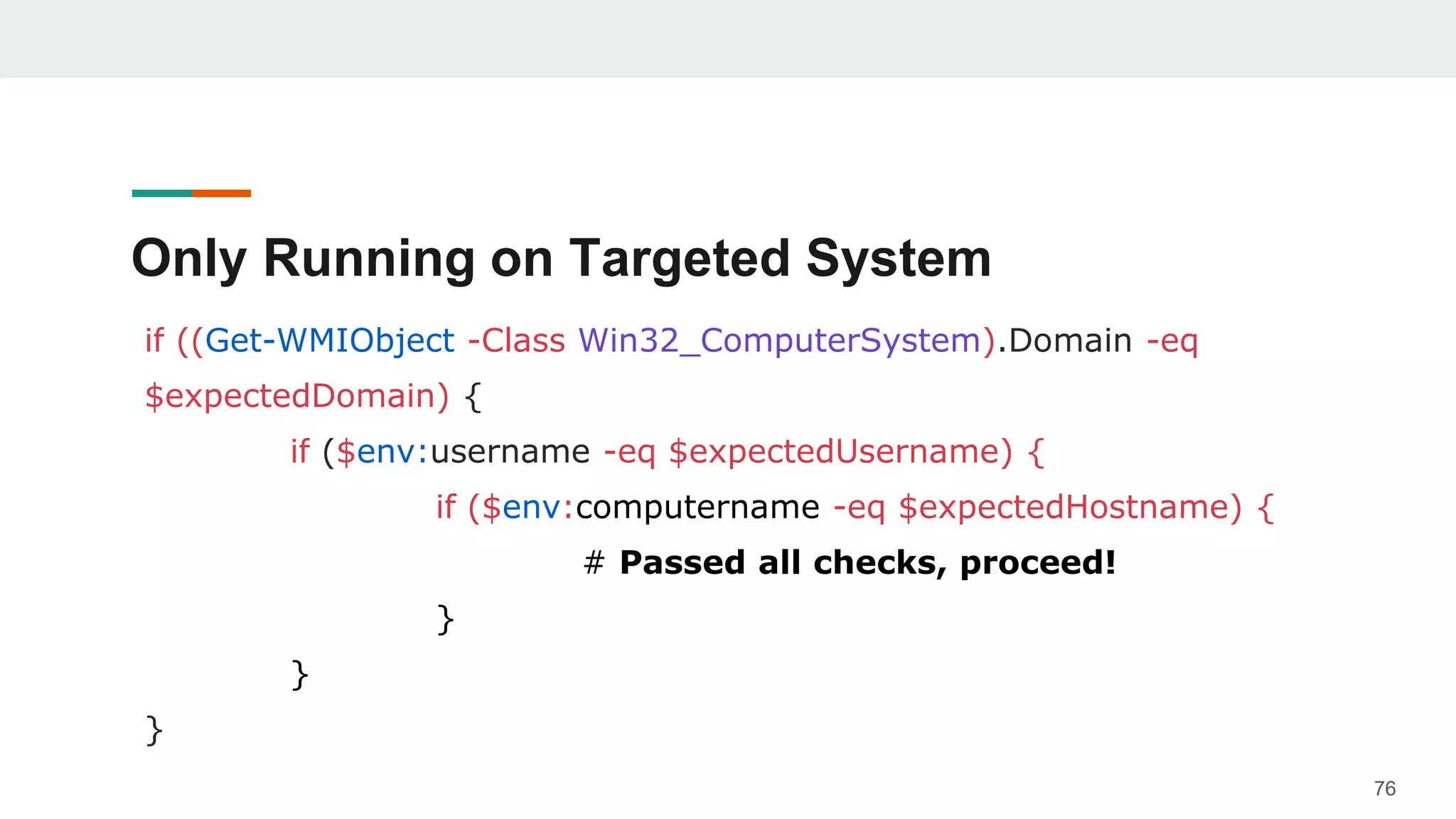
- Examples are given of how to check for things like expected Windows domains, user accounts, mouse clicks or positions to ensure a payload is running in the intended targeted environment and not a sandbox.