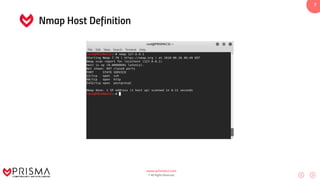
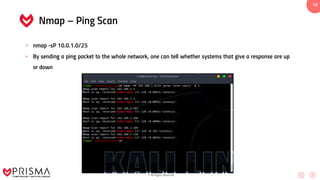
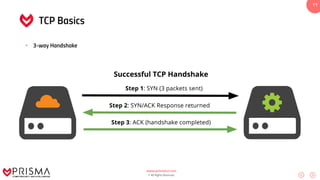
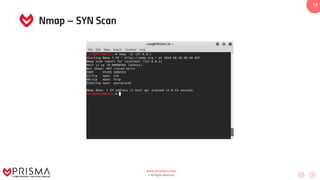
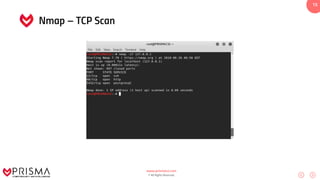
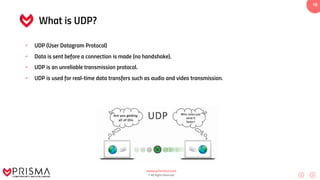
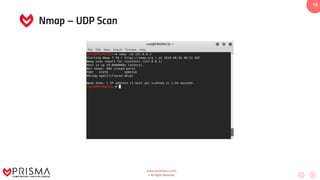
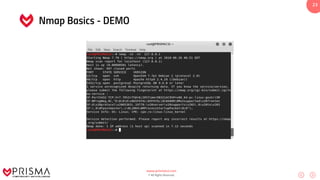
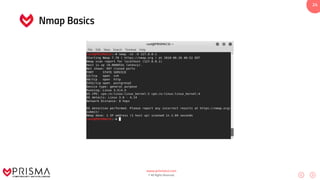
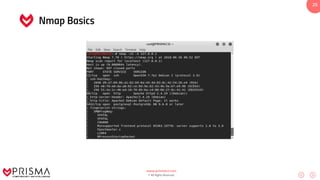
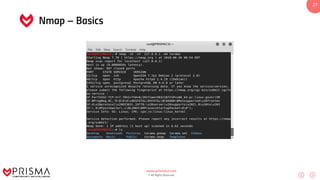
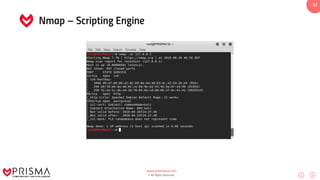
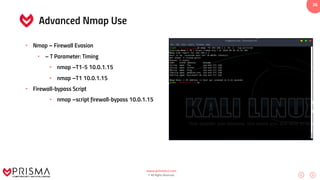
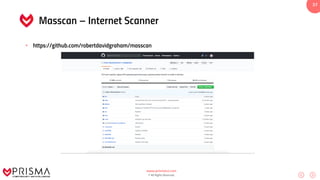
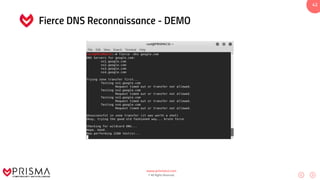
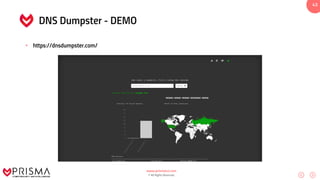
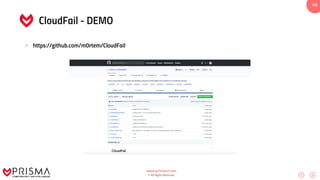
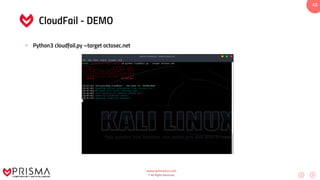
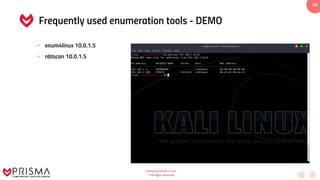
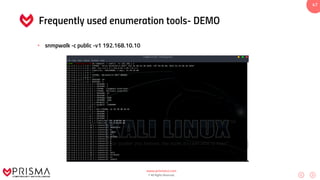
This document serves as a comprehensive training resource for practical white hat hacking, focusing on active information gathering using tools like nmap. It covers nmap basics, scanning methods, and techniques for reconnaissance, firewall evasion, and scripting, including various scanning techniques (e.g., SYN scan, TCP scan, UDP scan). Additionally, it discusses advanced nmap usage and anonymizing scanning operations, along with DNS information collection methods.