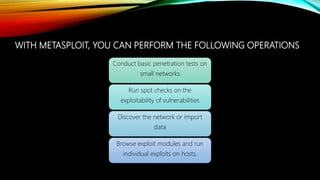
The document provides an overview of the Metasploit framework. It describes Metasploit as an open-source penetration testing software that contains exploits, payloads, and other tools to help identify vulnerabilities. Key points covered include Metasploit's architecture and modules for scanning, exploitation, and post-exploitation. Examples of tasks that can be performed include port scanning, vulnerability assessment, exploiting known issues, and gaining access to systems using payloads and meterpreter sessions. The document warns that Metasploit should only be used for legitimate security testing and cautions about the potential risks if misused.