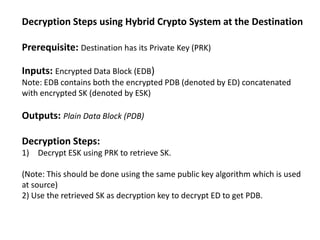
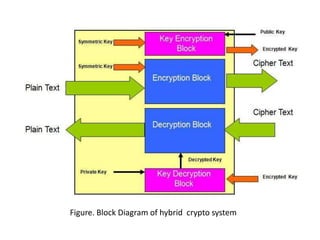
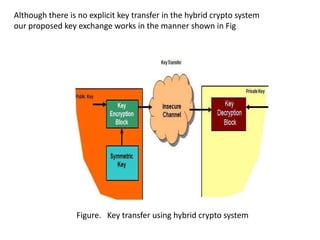
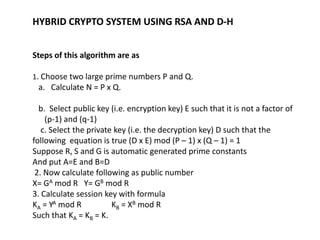
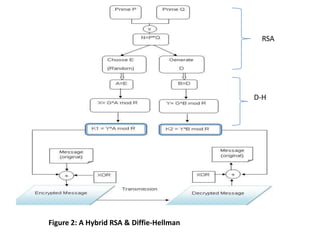
Hybrid encryption combines asymmetric and symmetric encryption algorithms to provide increased security. It uses a public key algorithm like RSA to encrypt a randomly generated symmetric key, which is then used with a symmetric algorithm like AES to encrypt the plaintext. The encrypted symmetric key is sent along with the encrypted plaintext. To decrypt, the recipient uses their private key to recover the symmetric key and decrypts the ciphertext with that key. Hybrid encryption leverages the strengths of both types of algorithms to improve security compared to either one alone.