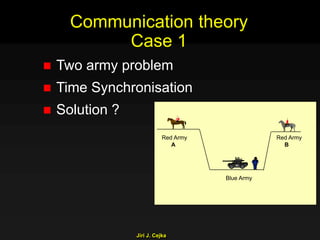
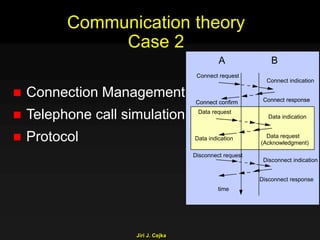
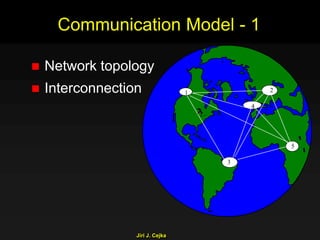
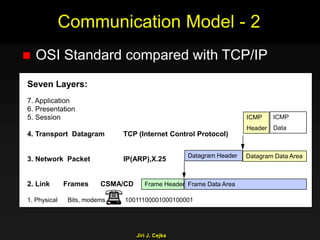
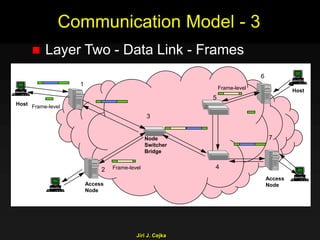
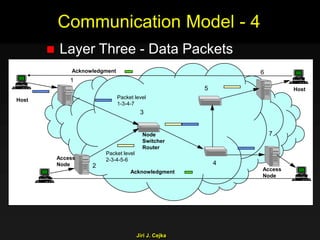
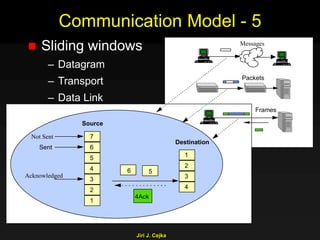
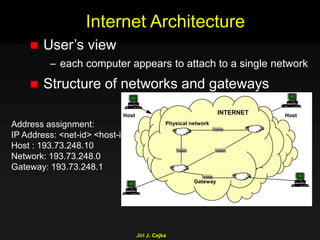
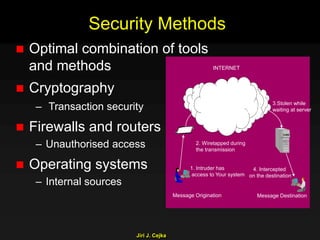
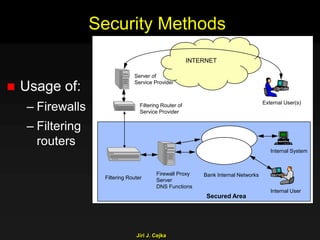
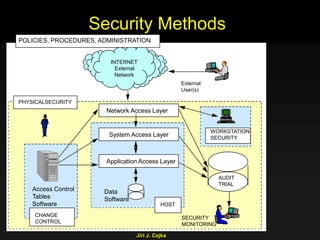
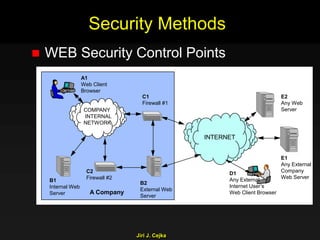
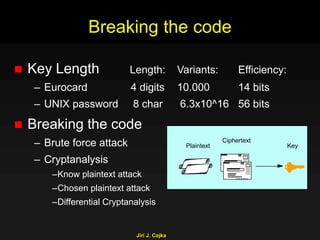
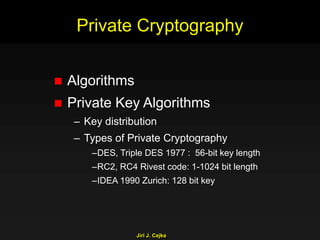
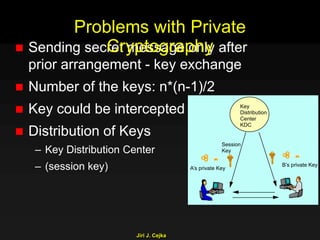
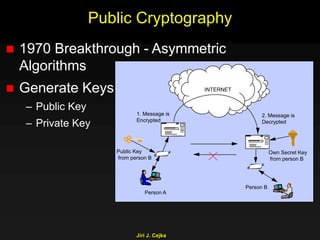
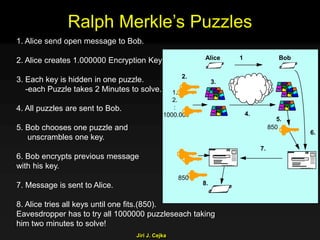
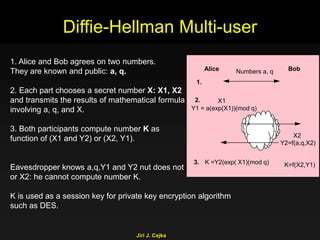
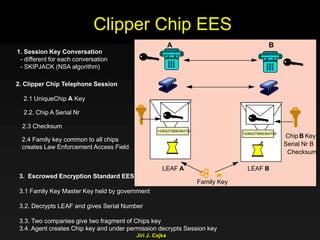
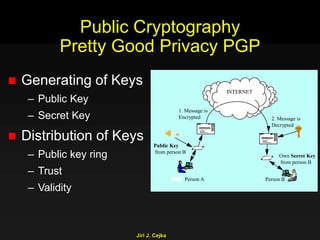
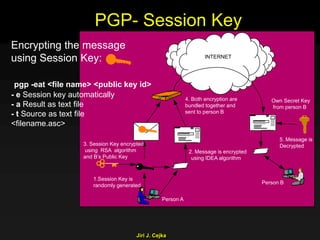
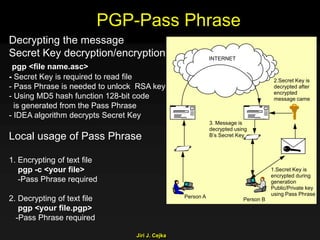
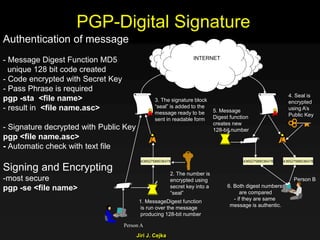
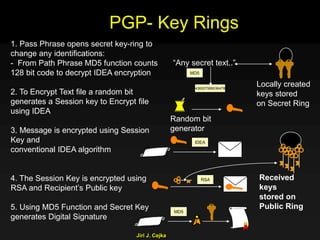
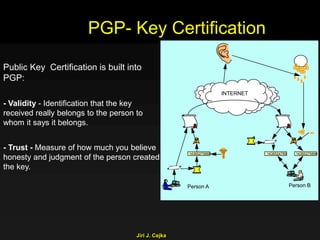
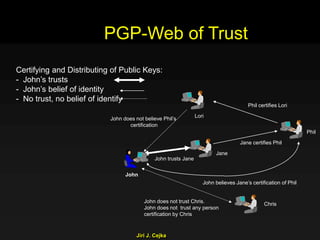
This document provides an extensive overview of the internet and security, covering key concepts such as communication theory, network models, internet architecture, security methods, and cryptography. It discusses both public and private cryptography, including their algorithms, standards, and applications in securing communications. Additionally, it touches upon historical developments in cryptographic techniques and standards, as well as privacy and public policy implications related to digital communications.