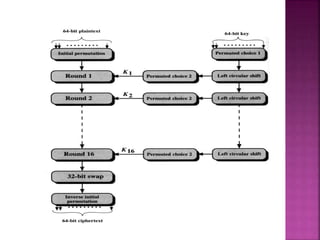
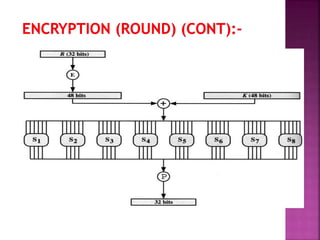
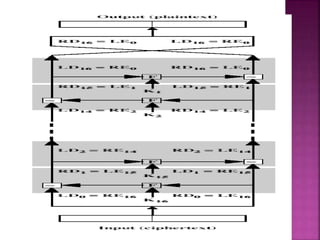
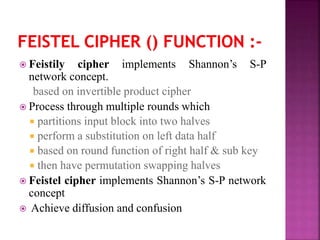
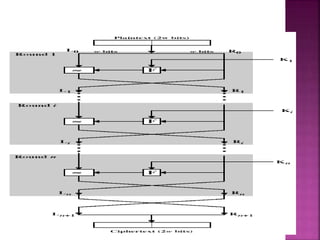
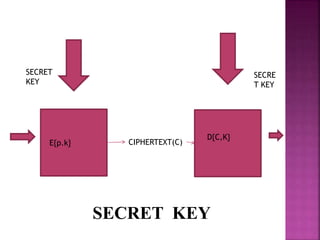
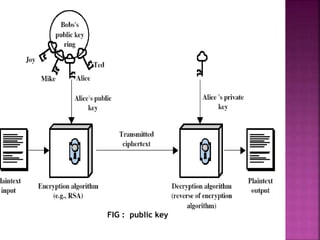
The document discusses encryption, detailing its definition, history, types, and importance in data security. It covers symmetric (private-key) and asymmetric (public-key) cryptography, along with key concepts like hashing and Feistel cipher structures. It emphasizes the necessity of encryption methods to ensure the confidentiality and integrity of transmitted information.