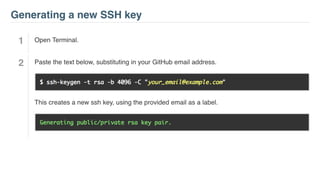
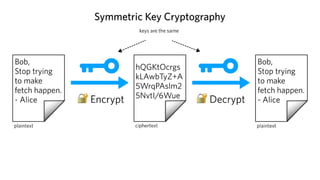
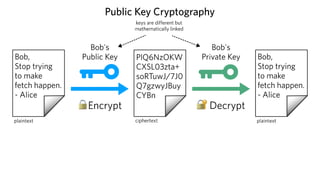
This document provides an introduction to public key cryptography. It explains that public key crypto uses two keys - a public key that can be shared and a private key that is kept secret. The document discusses how public key crypto works using RSA encryption as an example. It also covers other common public key crypto algorithms like Diffie-Hellman key exchange and elliptic curve cryptography. The document discusses key sizes and their relationship to security strength and provides examples of public key crypto implementations in Python.












![Elliptic-Curve Cryptography (ECC)
y2 = x3 + ax + b
Elliptic Curve Addition (Image By SuperManu [GFDL or CC BY-SA 3.0], via Wikimedia Commons)](https://image.slidesharecdn.com/disclosureconf2020-publickeycrypto-200902205857/85/Introduction-to-Public-Key-Cryptography-20-320.jpg)





![]](https://image.slidesharecdn.com/disclosureconf2020-publickeycrypto-200902205857/85/Introduction-to-Public-Key-Cryptography-30-320.jpg)
![@kelleyrobinson
]
Public key
on the Authy
servers](https://image.slidesharecdn.com/disclosureconf2020-publickeycrypto-200902205857/85/Introduction-to-Public-Key-Cryptography-31-320.jpg)
![@kelleyrobinson
]
Private key
on your
device](https://image.slidesharecdn.com/disclosureconf2020-publickeycrypto-200902205857/85/Introduction-to-Public-Key-Cryptography-32-320.jpg)
![@kelleyrobinson
]
Your device
signs with your
private key](https://image.slidesharecdn.com/disclosureconf2020-publickeycrypto-200902205857/85/Introduction-to-Public-Key-Cryptography-33-320.jpg)