Embed presentation
Download as PDF, PPTX











The document discusses specialized Medium Access Control (MAC) methods in wireless communication, focusing on the motivations for their use and various access methods including SDMA, FDMA, TDMA, and CDMA. It explains how these methods allow multiple users to share a communication medium using techniques based on space, frequency, time, and code, while addressing challenges such as interference and synchronization. The document also highlights specific protocols like CSMA and variations for managing channel access.
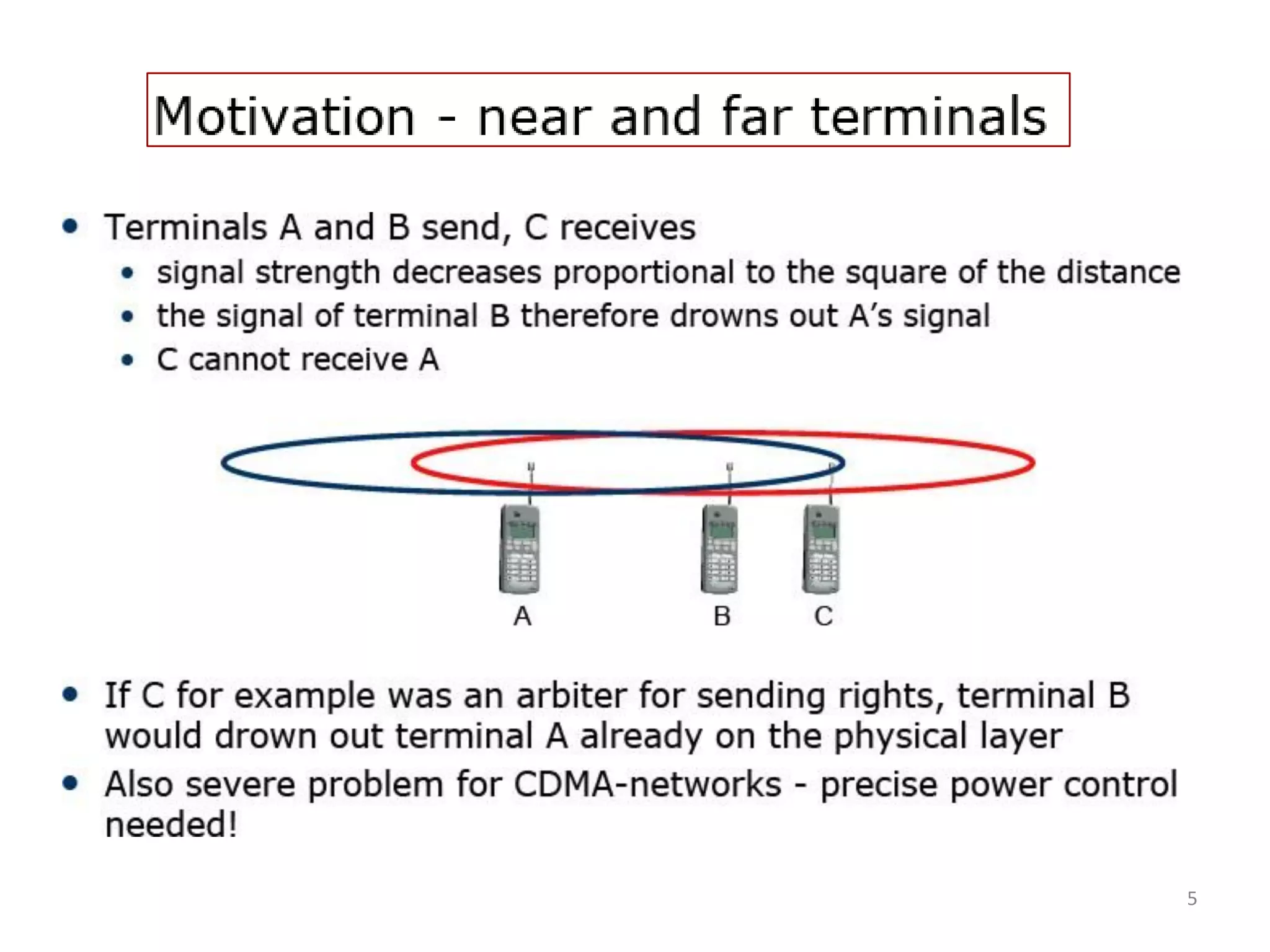
Overview of Wireless MAC, motivation for specialized methods addressing hidden/exposed terminals.
Multiplexing enables multiple users to share a medium in wireless communication through space, time, frequency, and code.
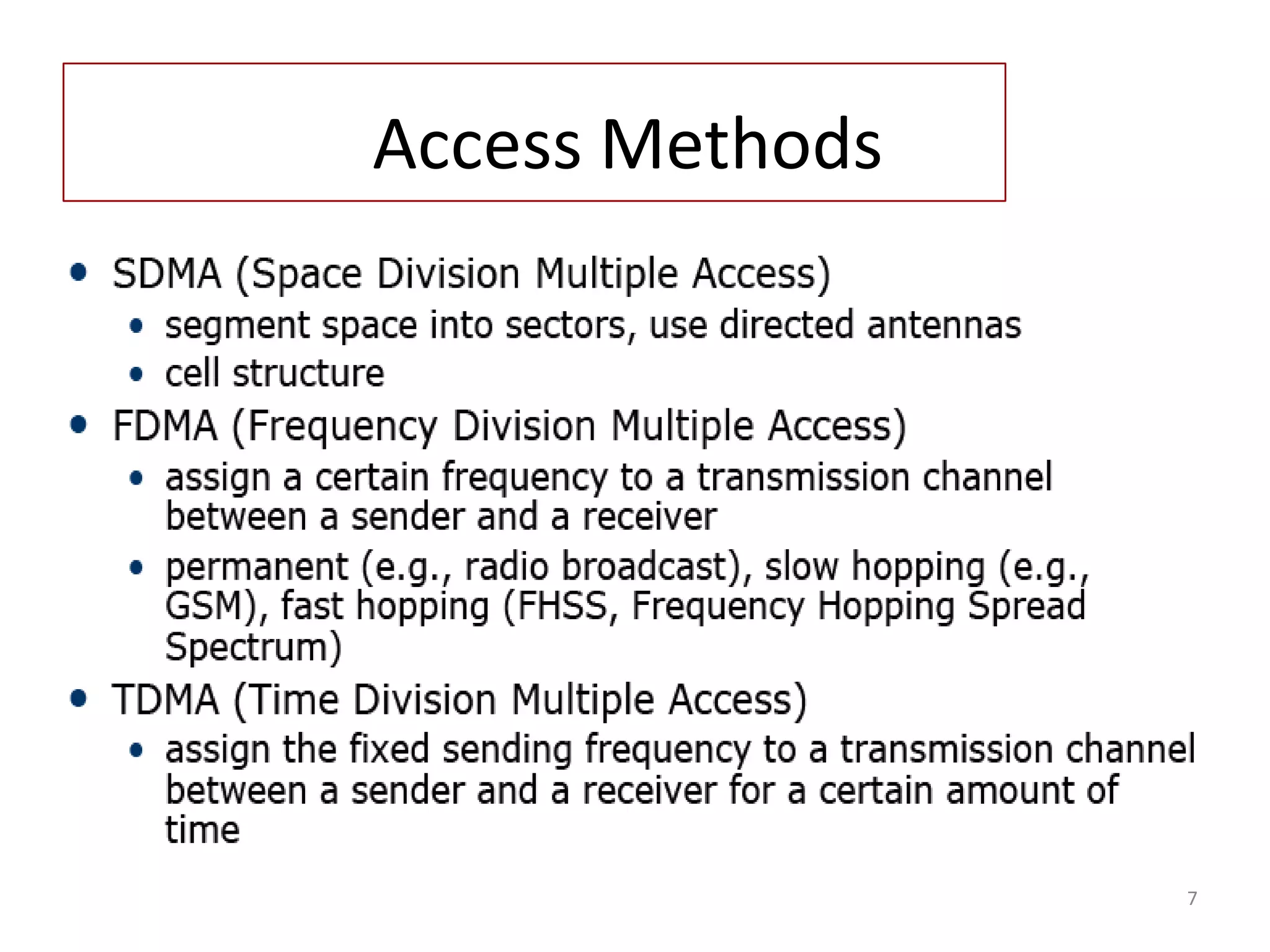
Introduction to various access methods including SDMA, FDMA, TDMA, and CDMA for medium access management.
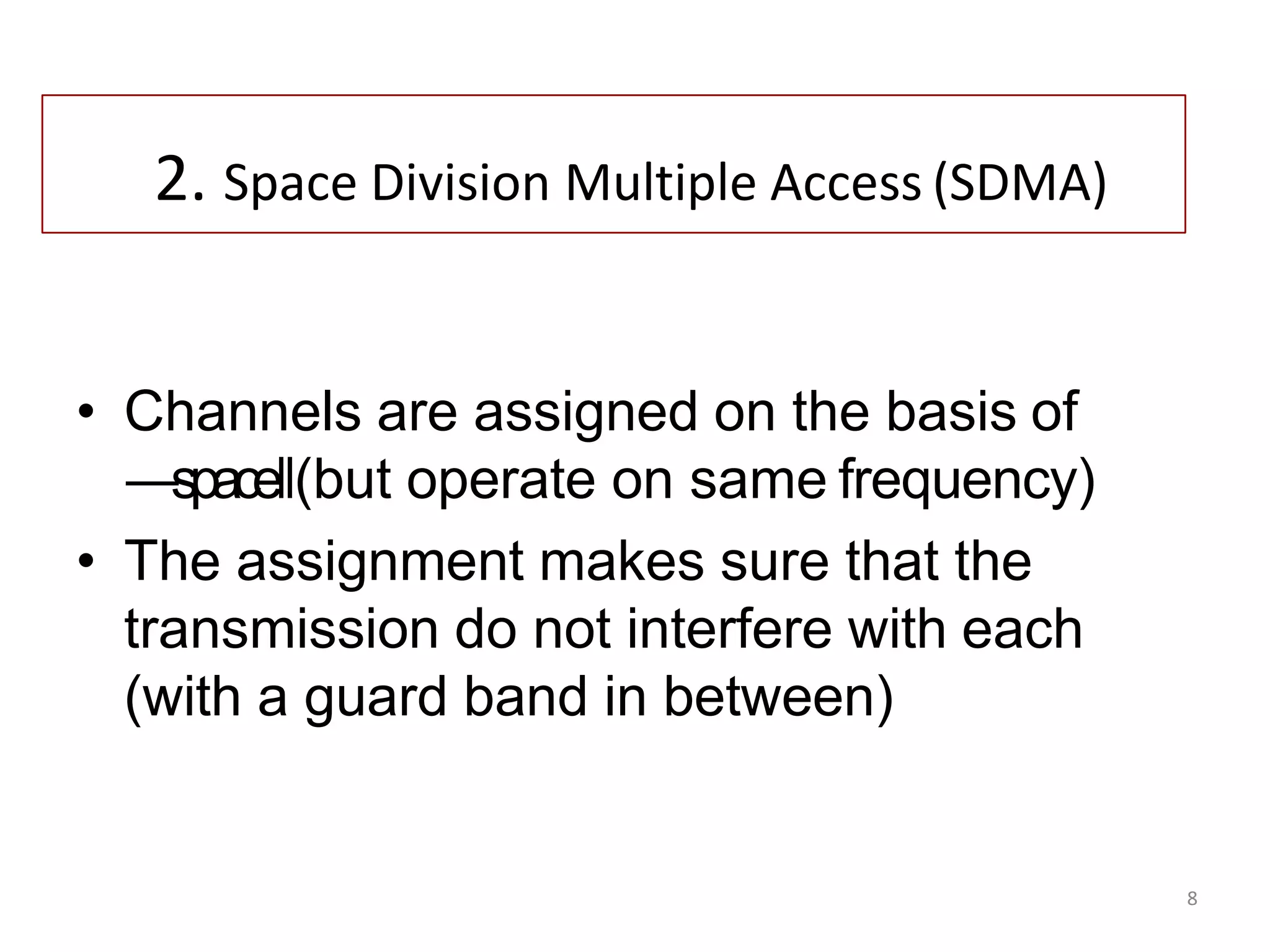
SDMA assigns channels based on space, using the same frequency without interference, maintained by guard bands.
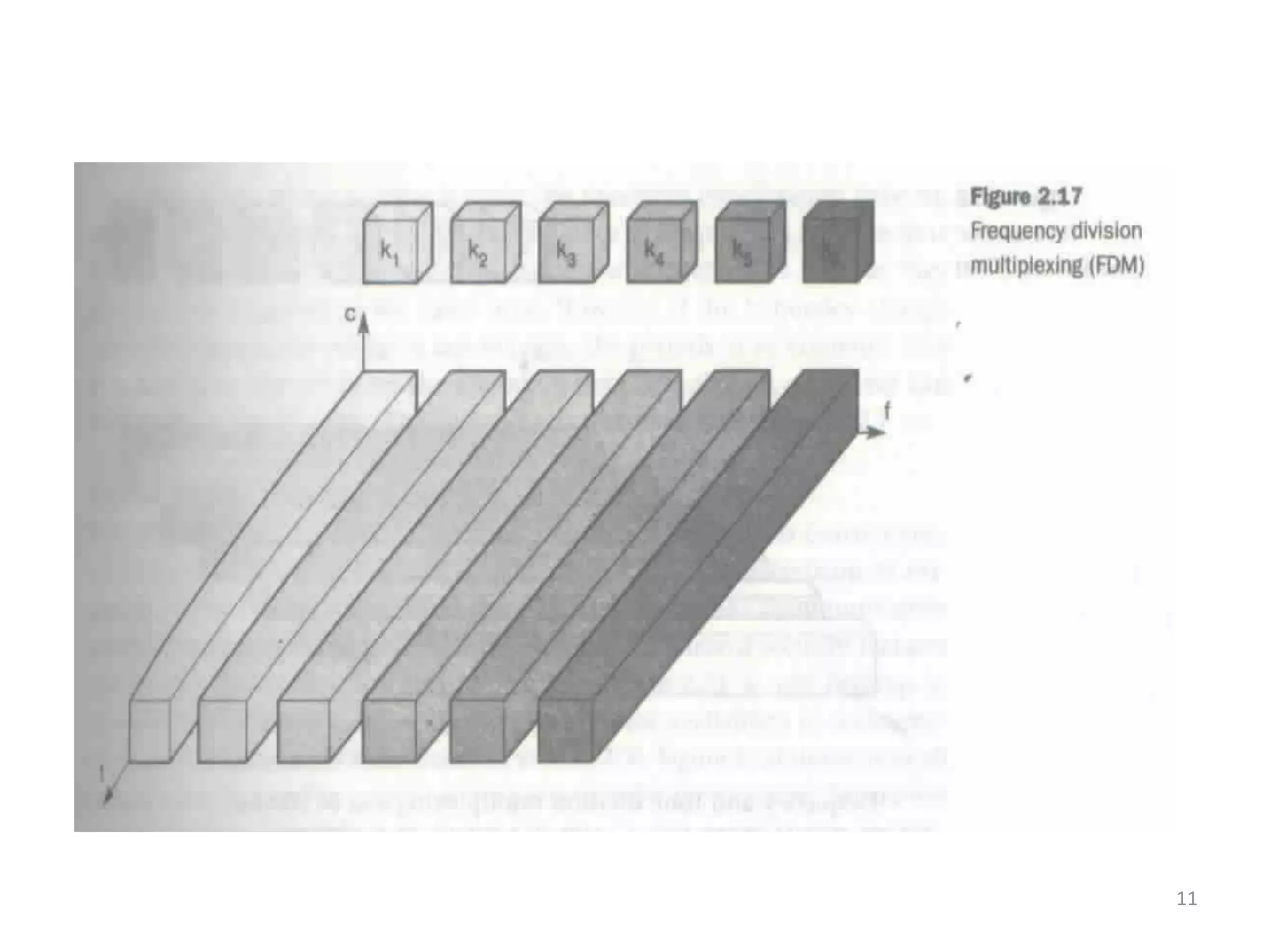
FDMA subdivides frequency into non-overlapping bands, assigning unique bands to each channel.
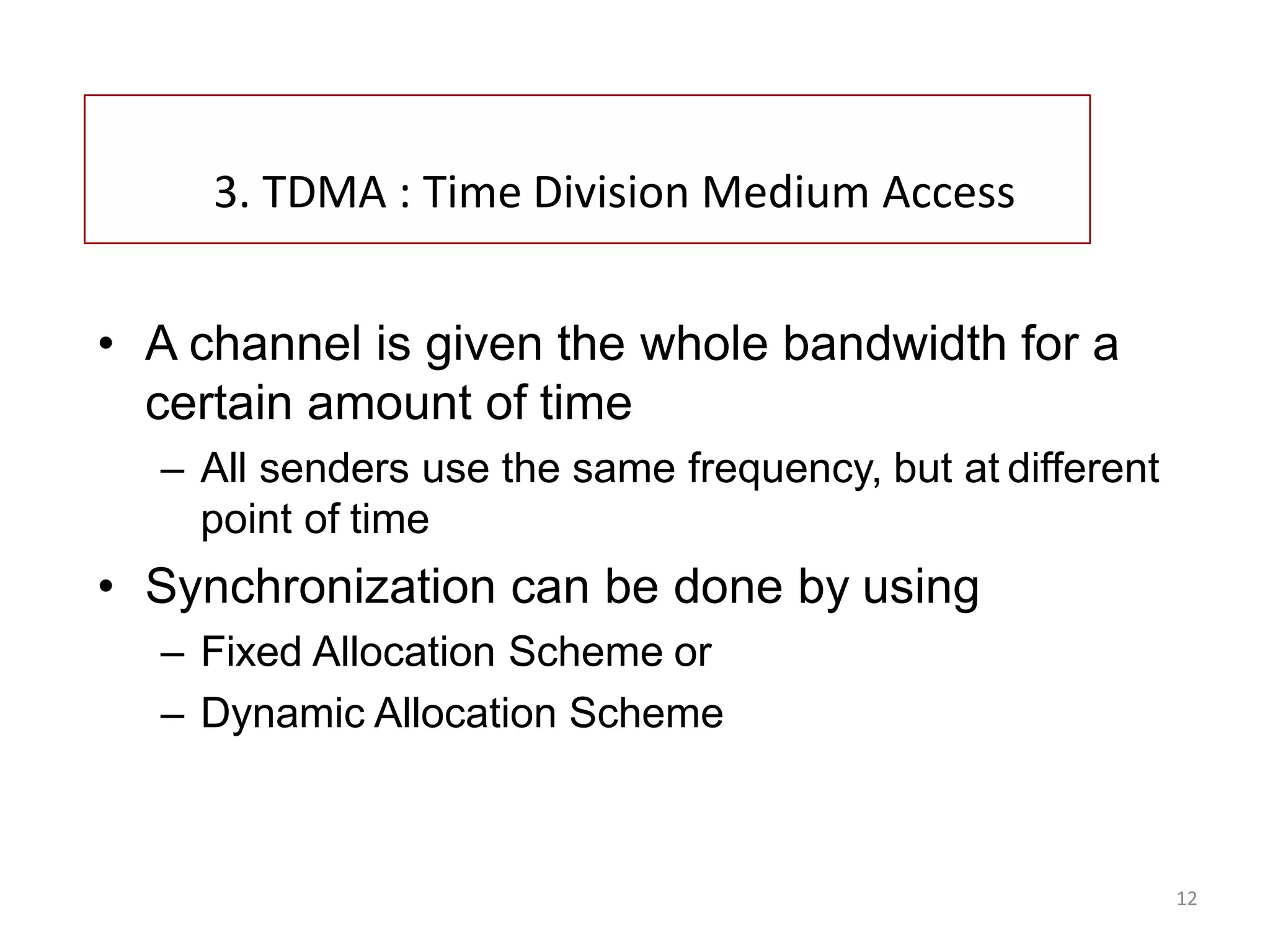
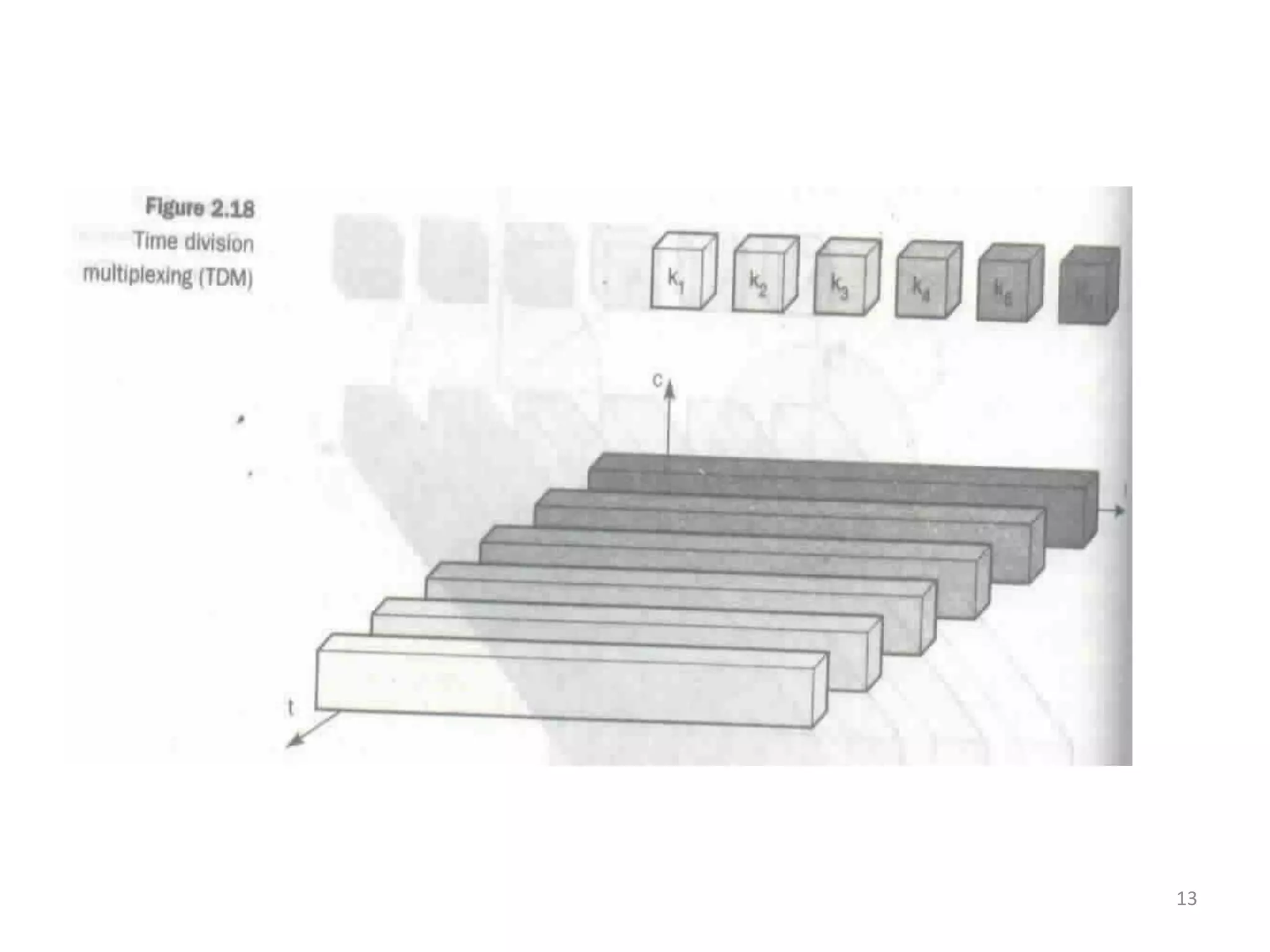
TDMA allocates the entire bandwidth at intervals to each channel using synchronization schemes.
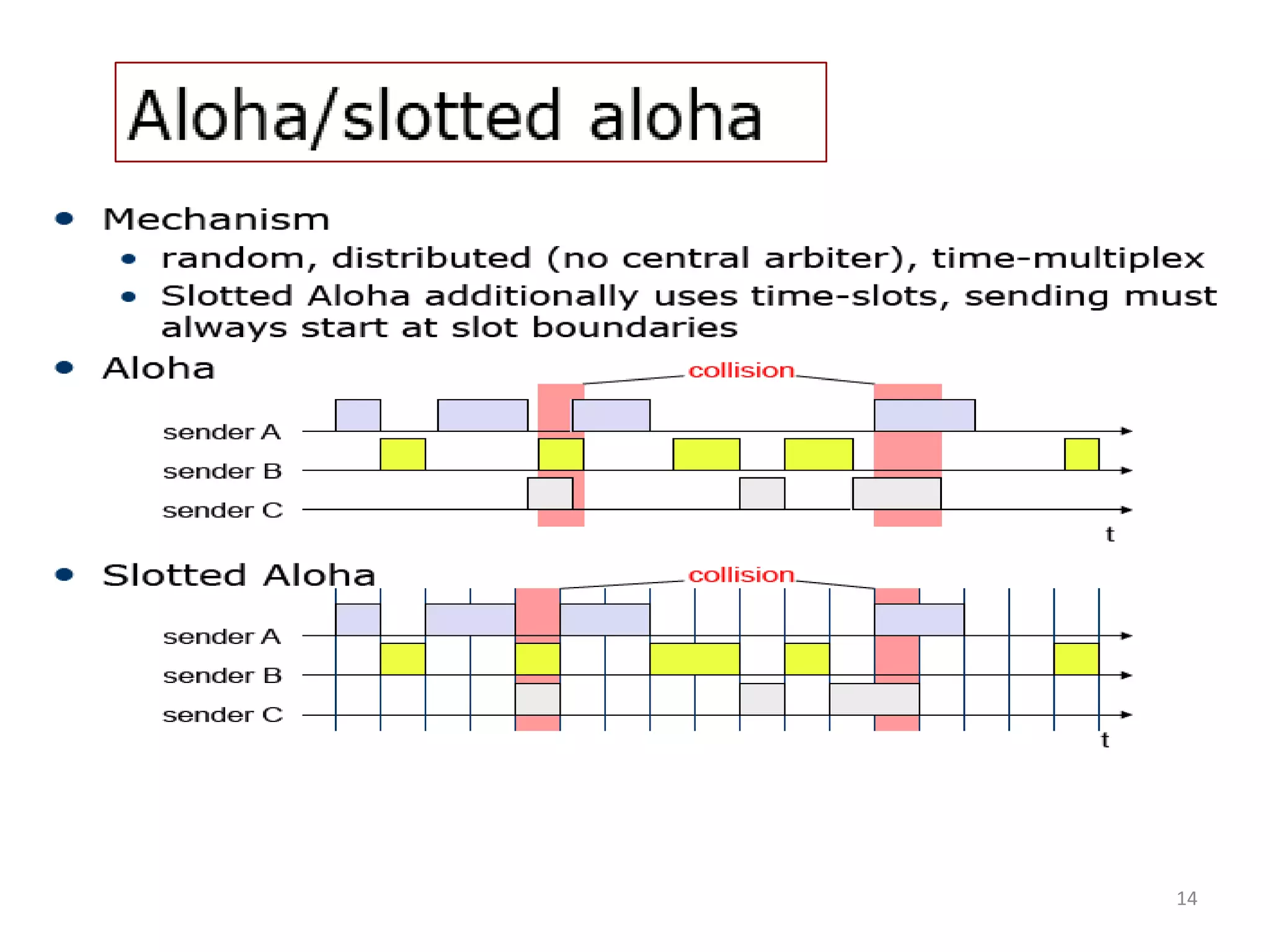
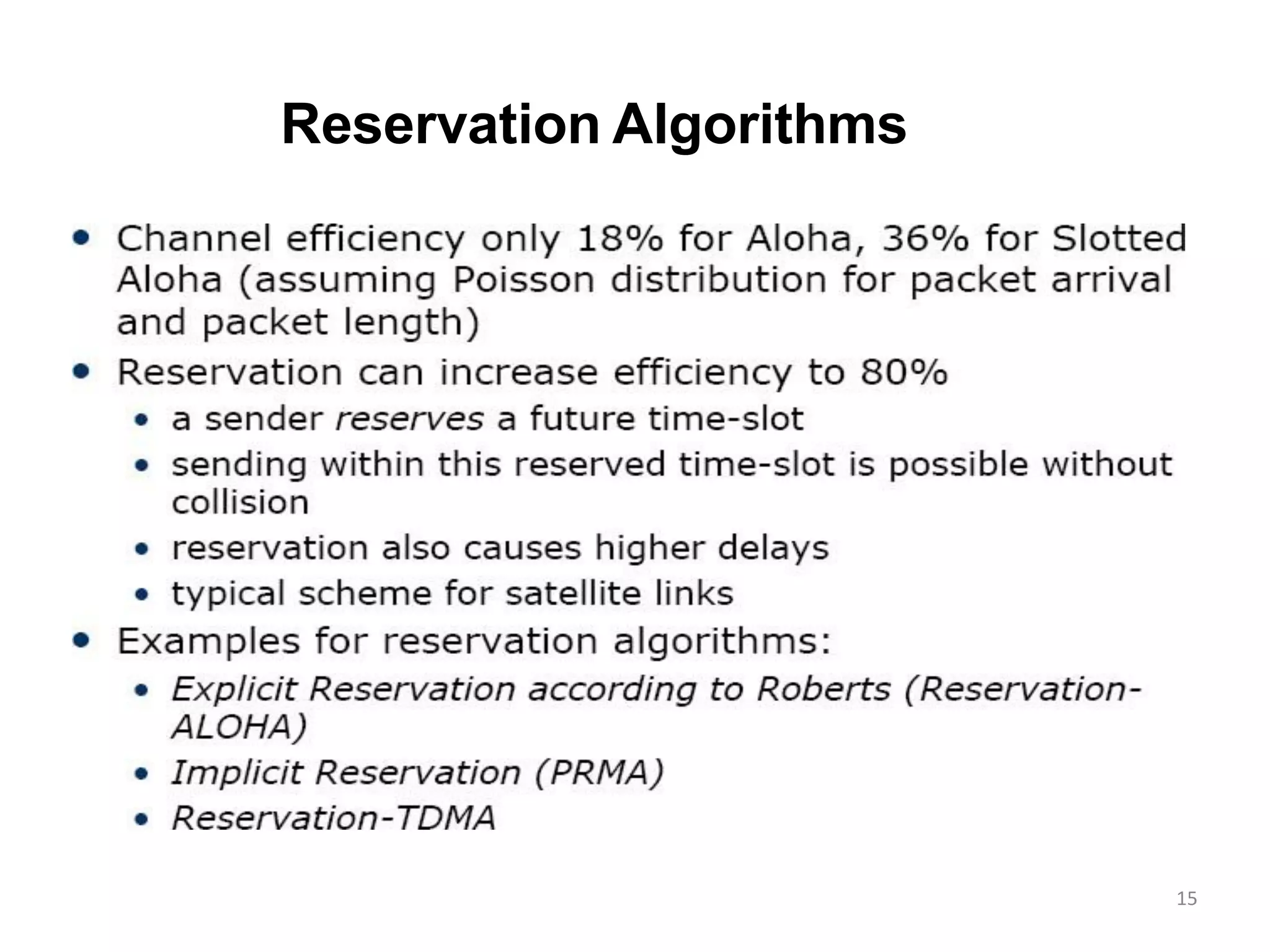
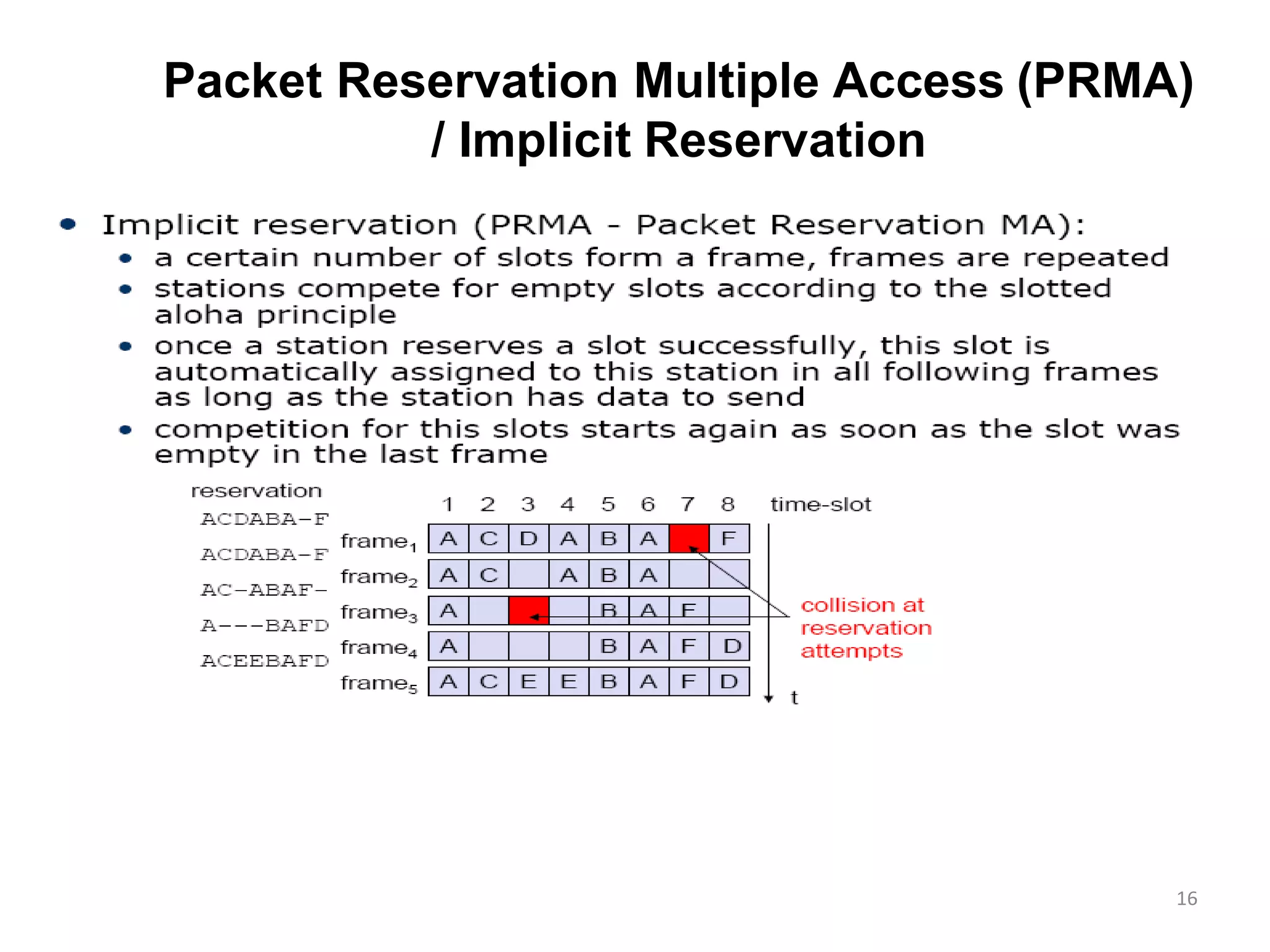
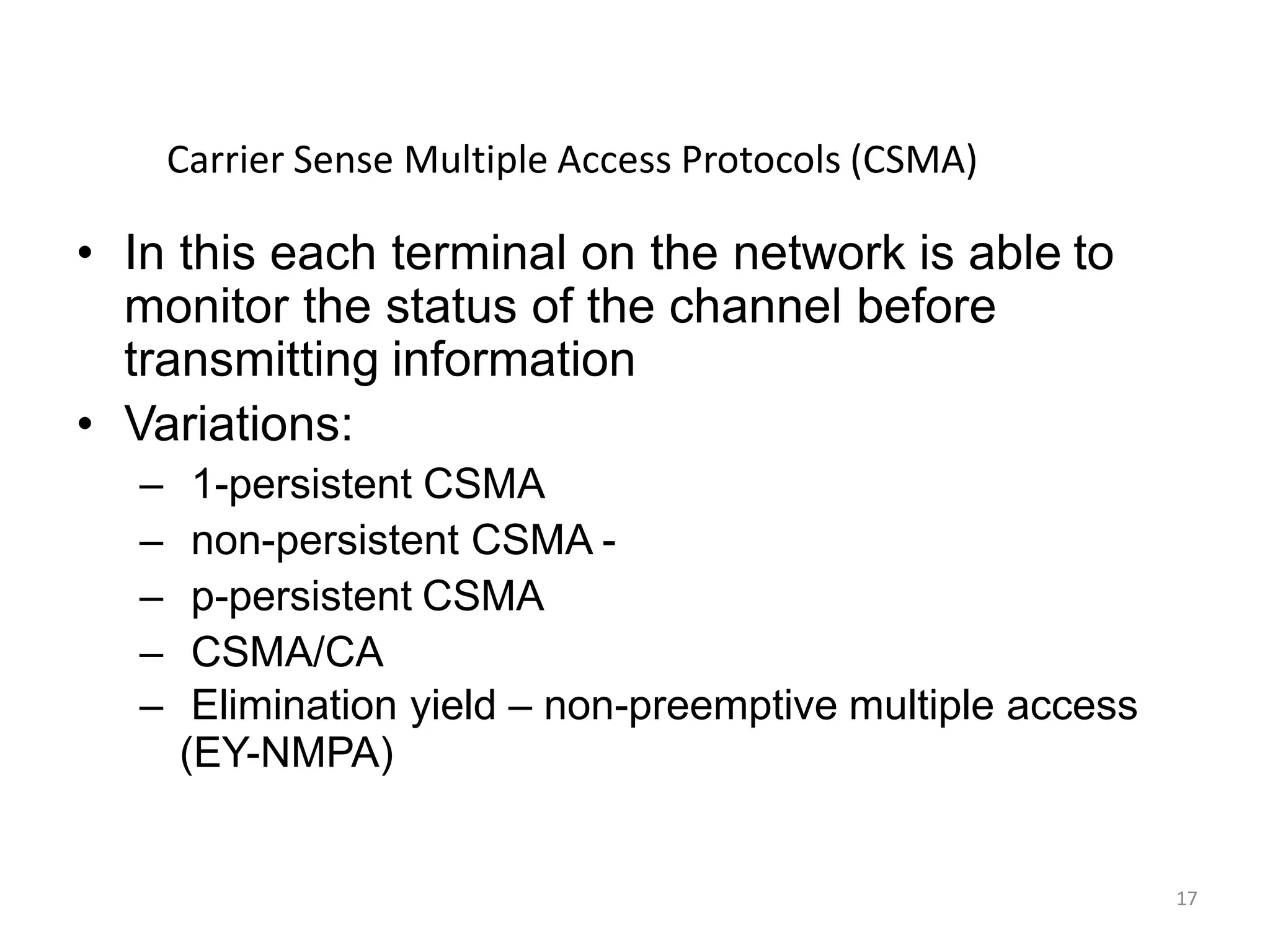
Packet Reservation Multiple Access (PRMA), examining channel monitoring and various CSMA methodologies.
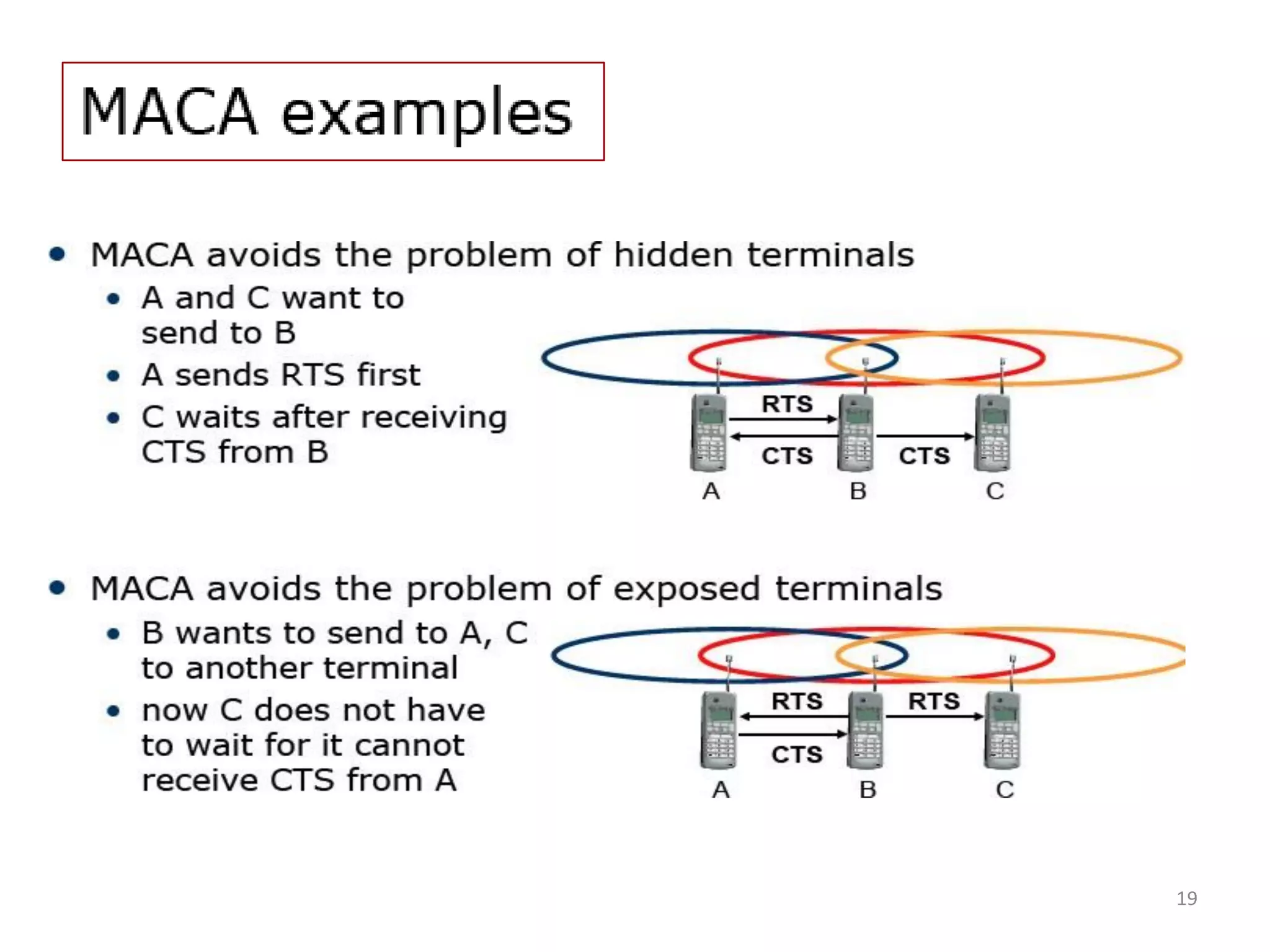
Discussion on MAC protocols with collision avoidance, including Inhibit Sense and Polling techniques.
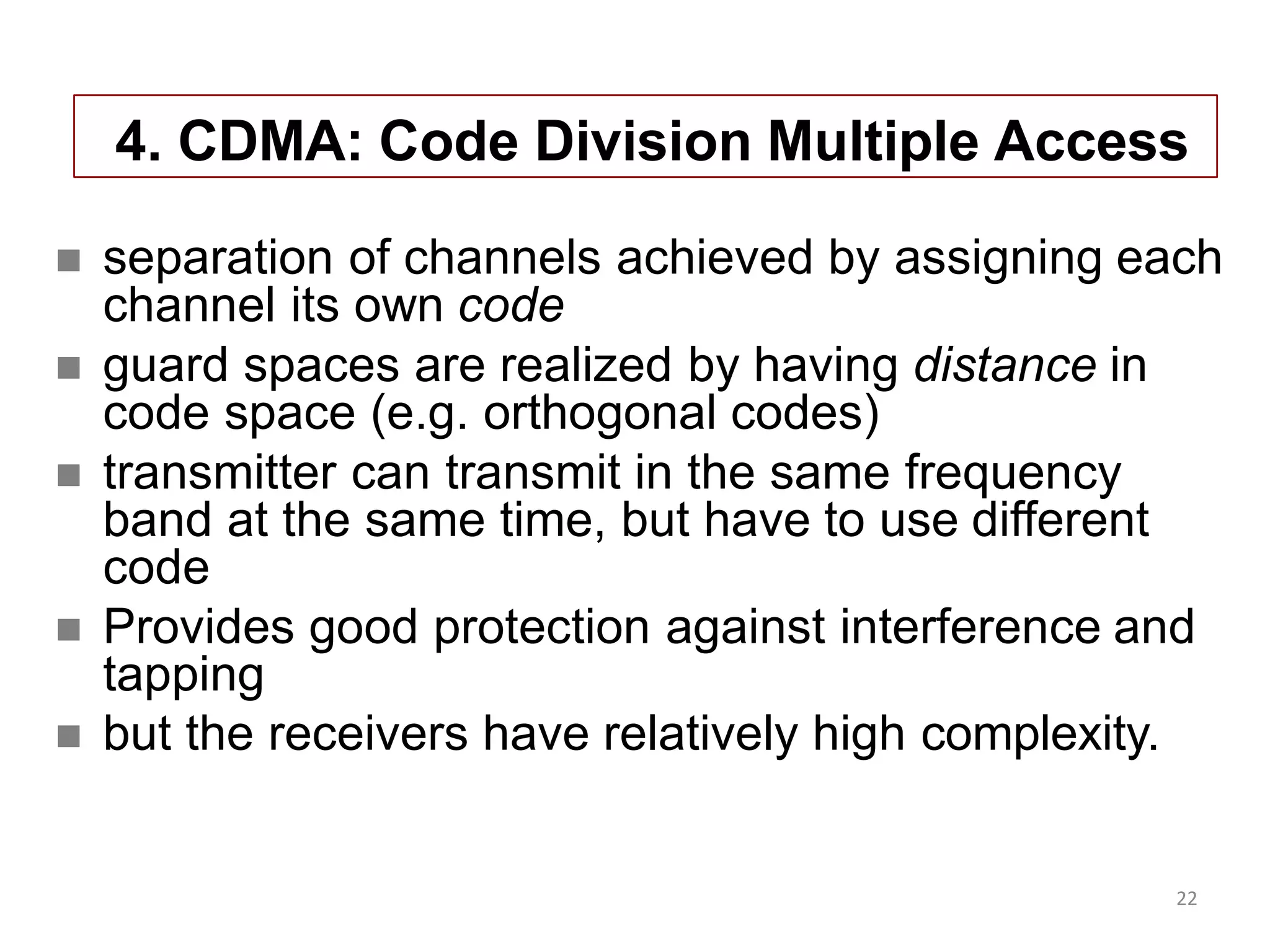
CDMA uses unique codes for channels allowing simultaneous transmission, providing interference protection.
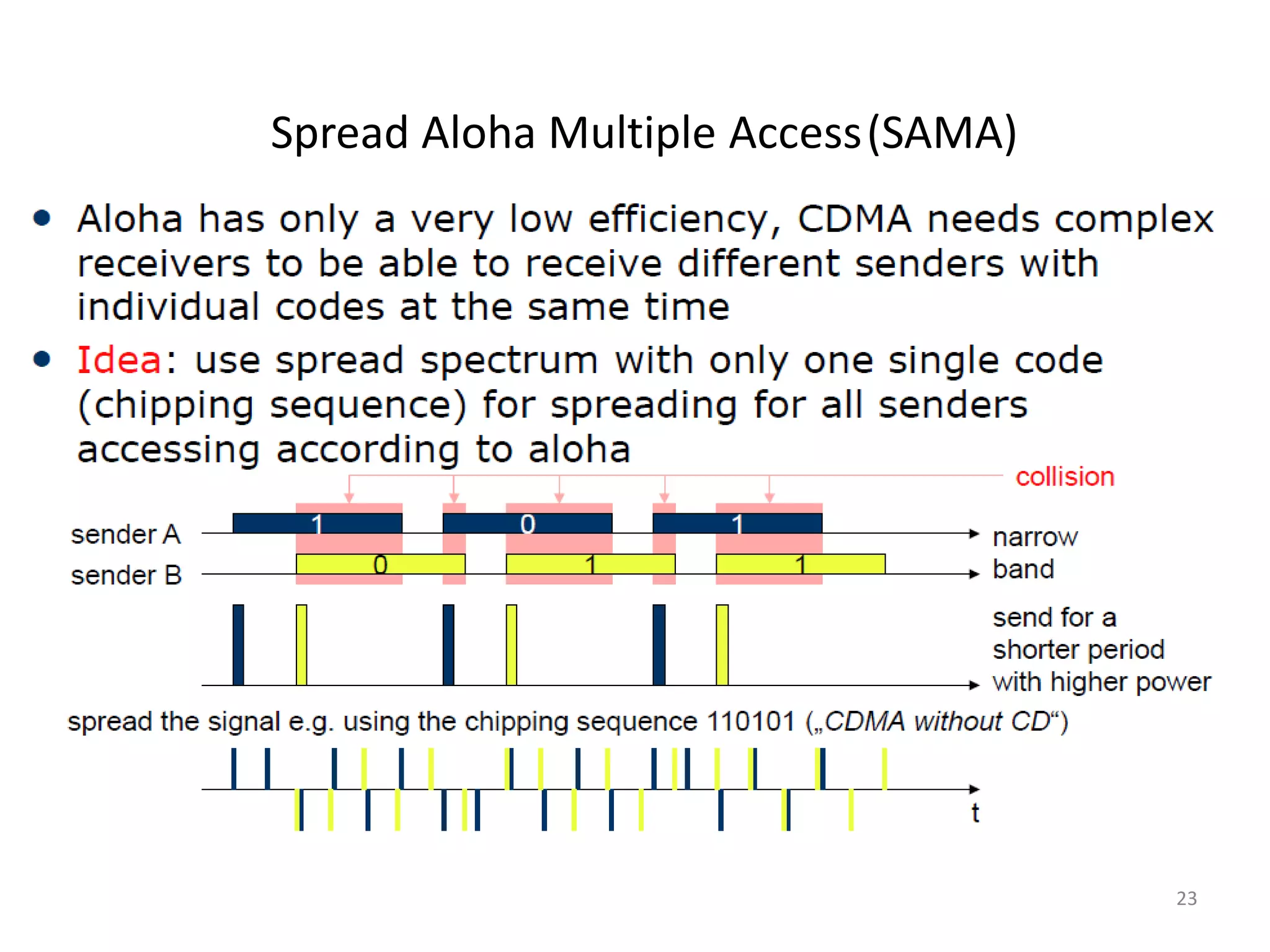
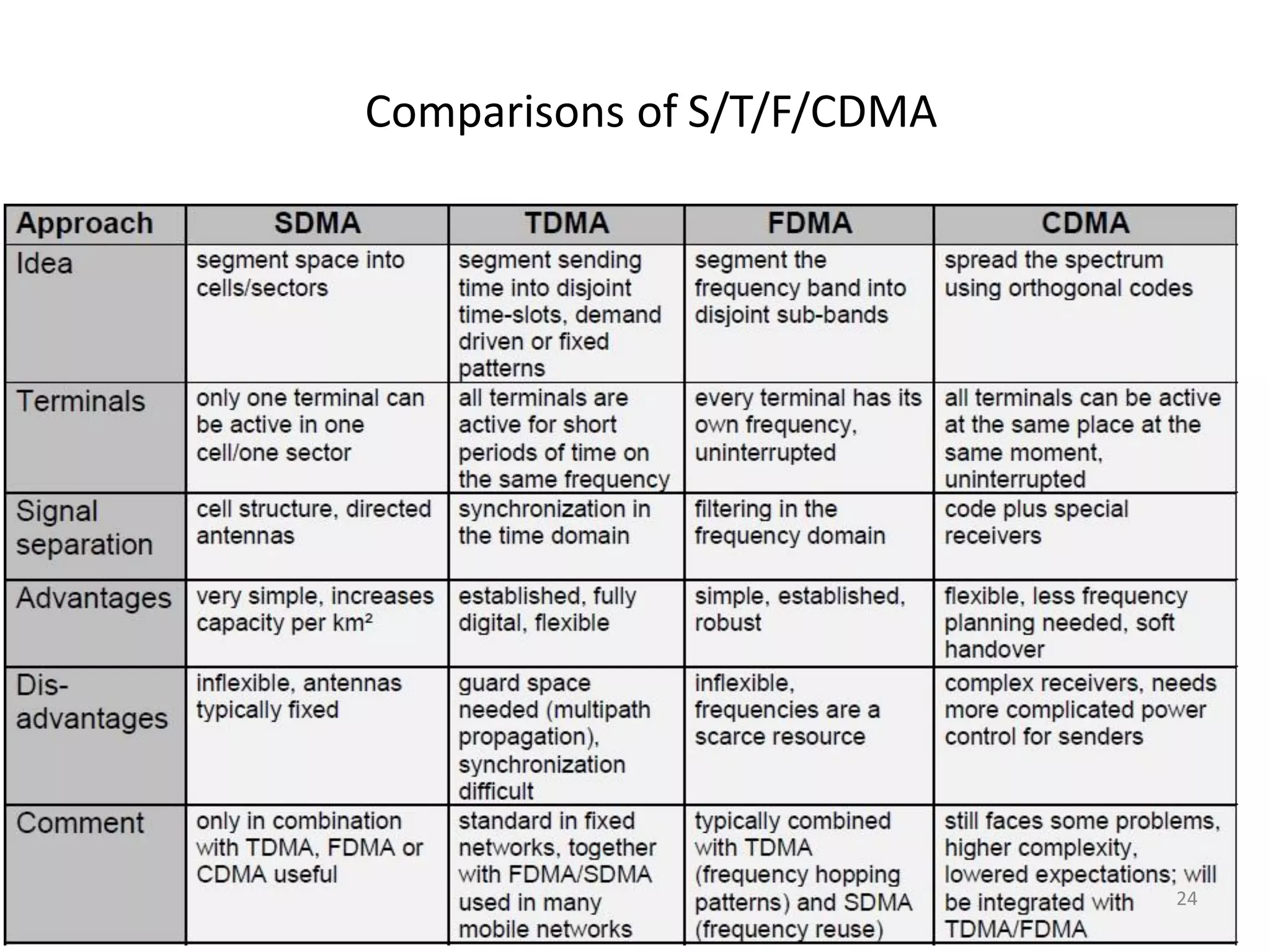
Overview of Spread Aloha Multiple Access and comparisons among SDMA, FDMA, TDMA, and CDMA.
Conclusion of the presentation with a thank you note.
























