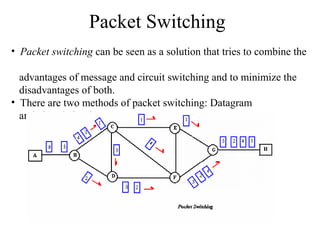
Circuit switching directly connects the sender and receiver through a dedicated physical path. Message switching transmits entire messages from node to node without establishing a dedicated path. Packet switching breaks messages into packets that can take different routes to the destination and are reassembled, allowing for more efficient use of bandwidth but introducing complexity.