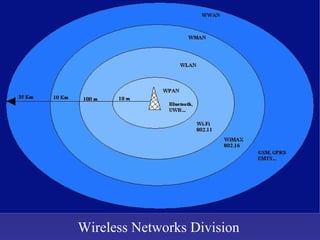
The document summarizes several routing protocols used in wireless networks. It discusses both table-driven protocols like DSDV and on-demand protocols like AODV. It provides details on how each protocol performs routing and maintains routes. It also outlines some advantages and disadvantages of protocols like DSDV, AODV, DSR, and TORA.