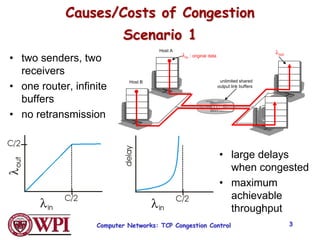
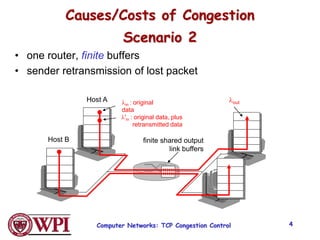
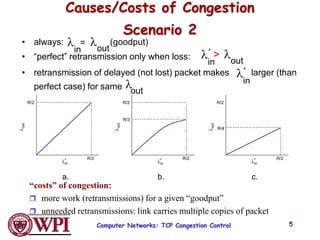
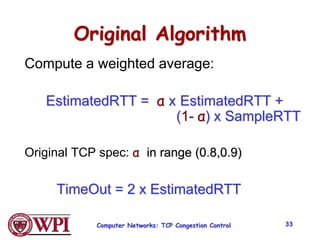
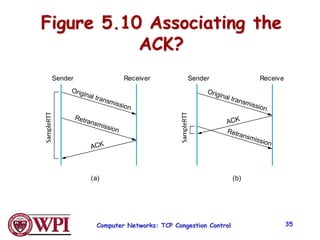
1) Congestion occurs when there are too many sources sending too much data too fast for the network to handle, leading to lost packets and long delays. TCP uses congestion control to address this problem.
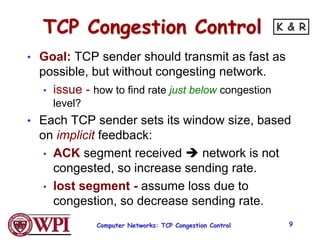
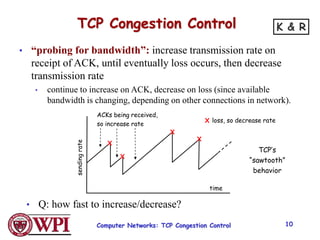
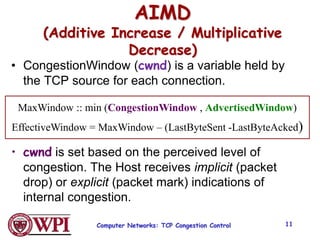
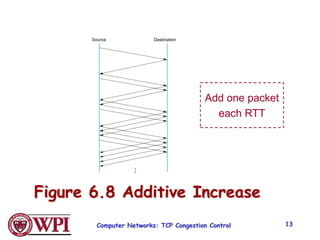
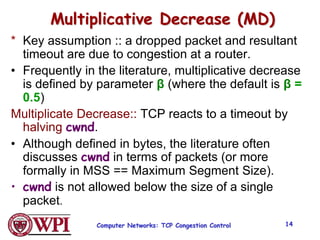
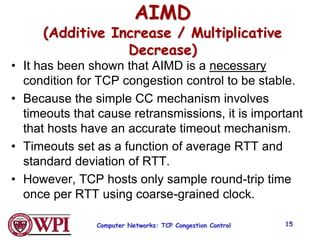
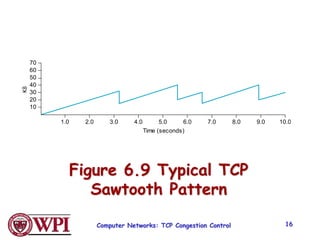
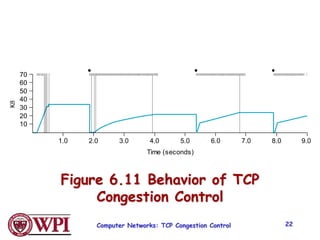
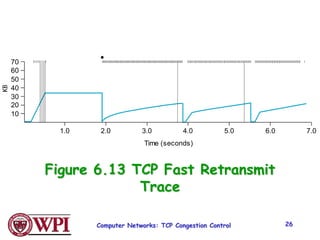
2) TCP uses Additive Increase Multiplicative Decrease (AIMD) congestion control, where it slowly increases the transmission rate and halves it upon detecting packet loss, exhibiting a sawtooth pattern.
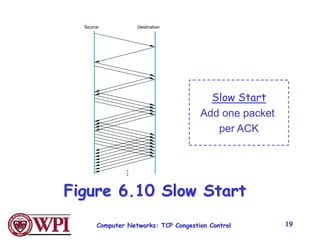
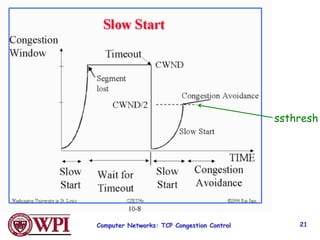
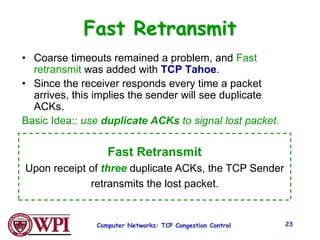
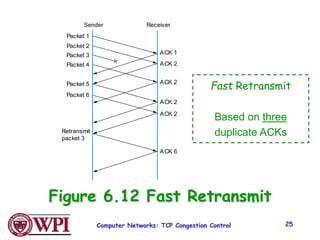
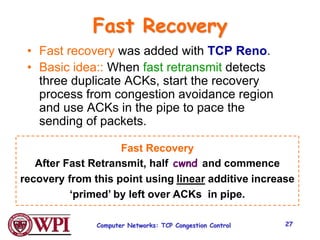
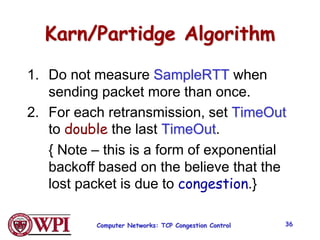
3) Key TCP congestion control mechanisms include slow start for initial exponential increase, fast retransmit to quickly retransmit lost packets based on duplicate ACKs, and fast recovery to resume transmission after a fast retransmit.