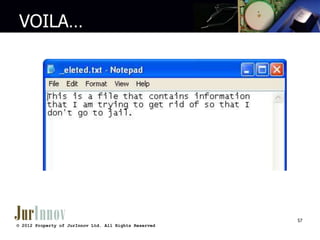
This document provides an overview of a three-day computer forensics training hosted by JurInnov Ltd. It introduces the trainers and covers topics including understanding computing environments, collecting electronically stored information, forensic analysis demonstrations, and types of cases where computer forensics are useful. The document outlines concepts like what computer forensics is, sources of electronically stored information, reasons for using computer forensics, how computers operate, and methods for collecting, imaging, and analyzing various types of digital evidence from computers, networks, phones and other devices.