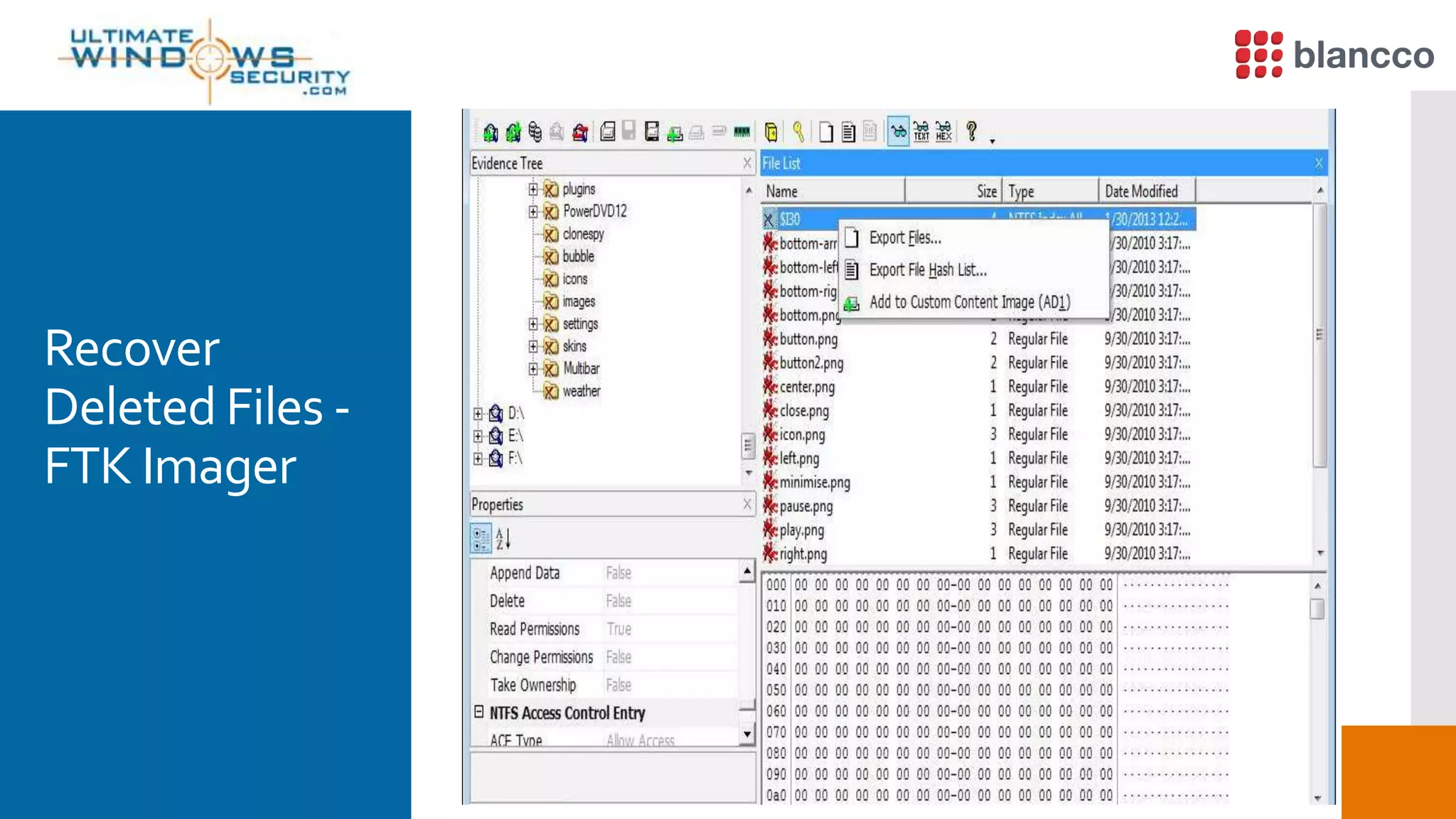
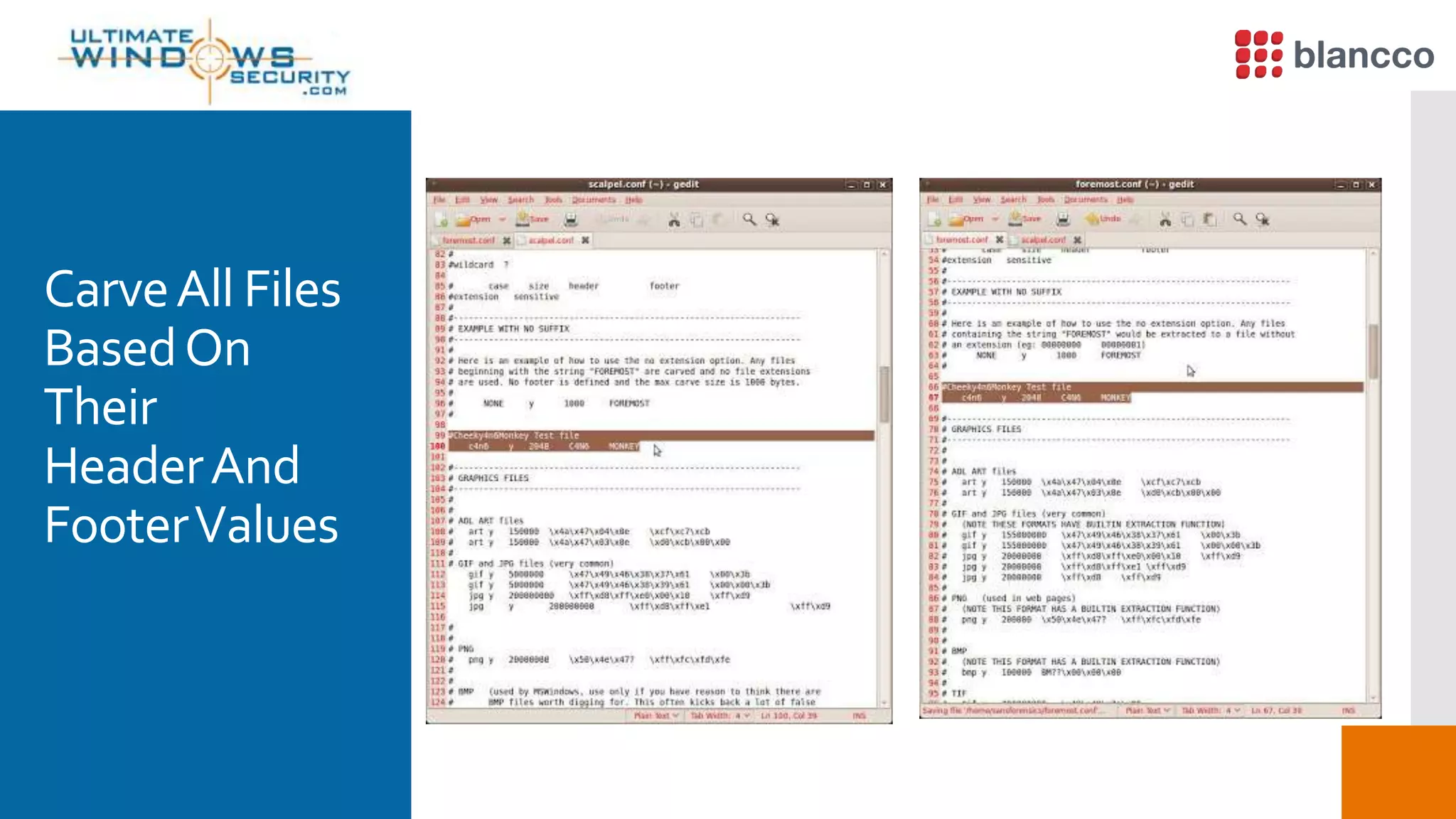
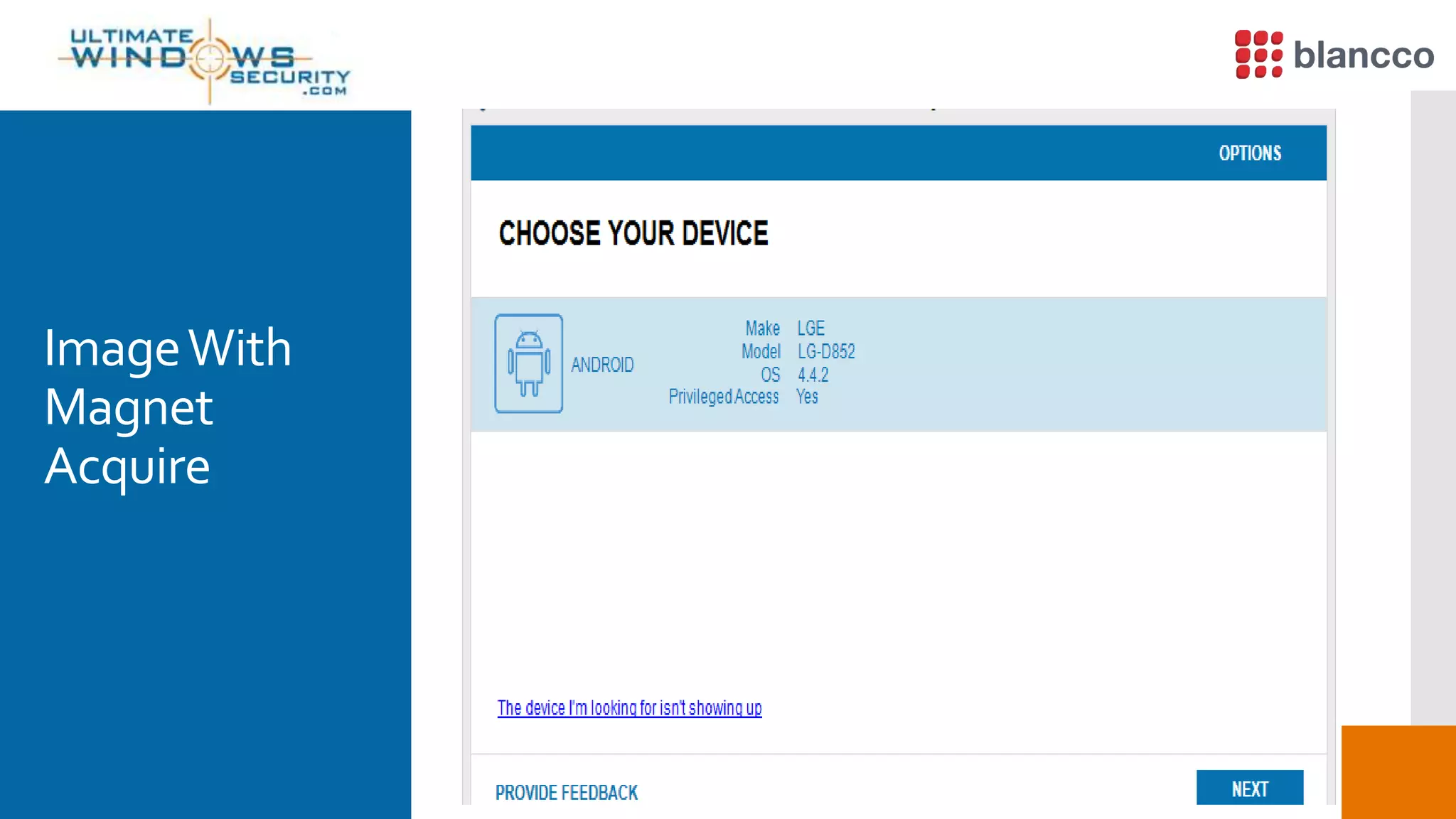
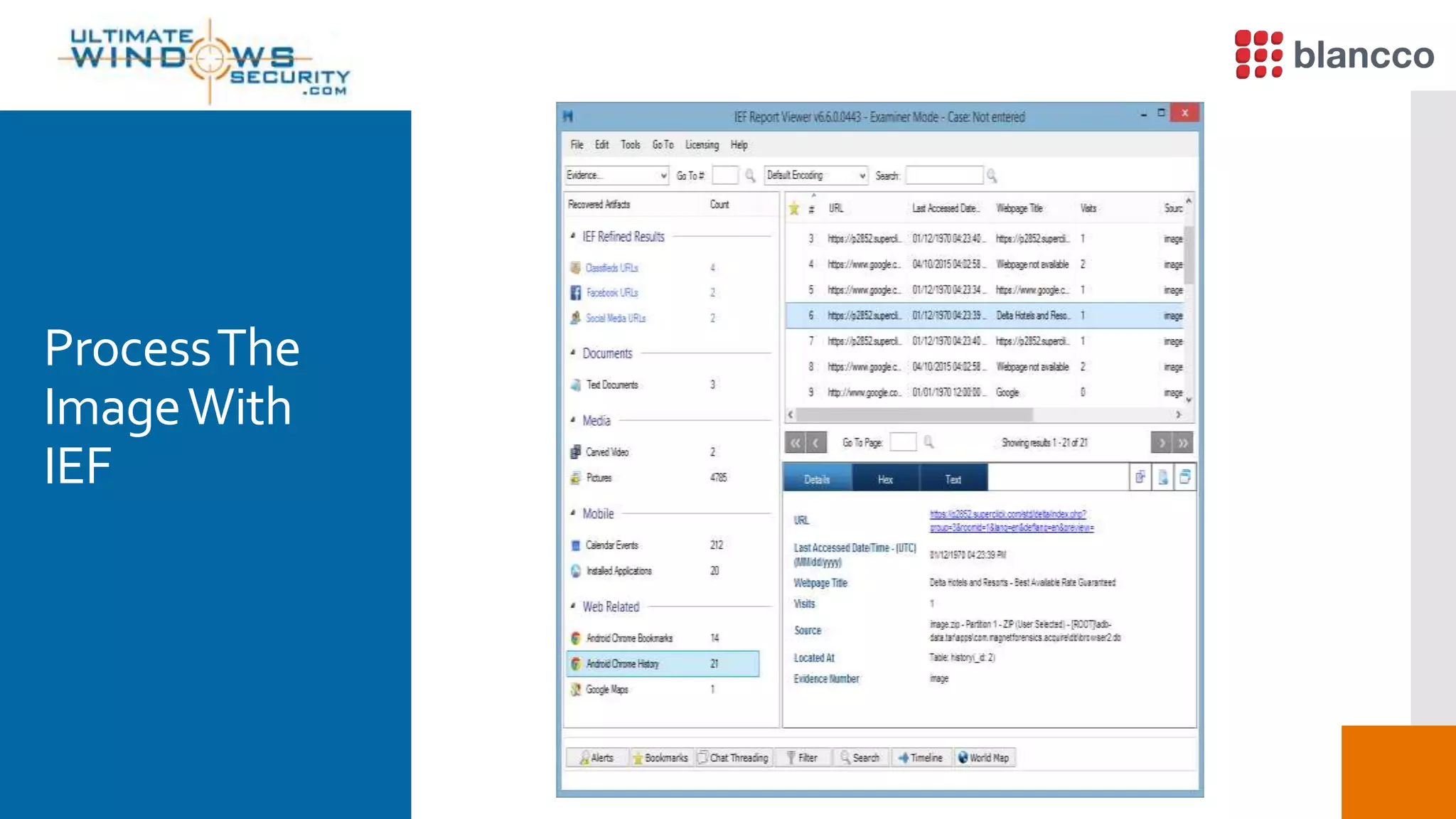
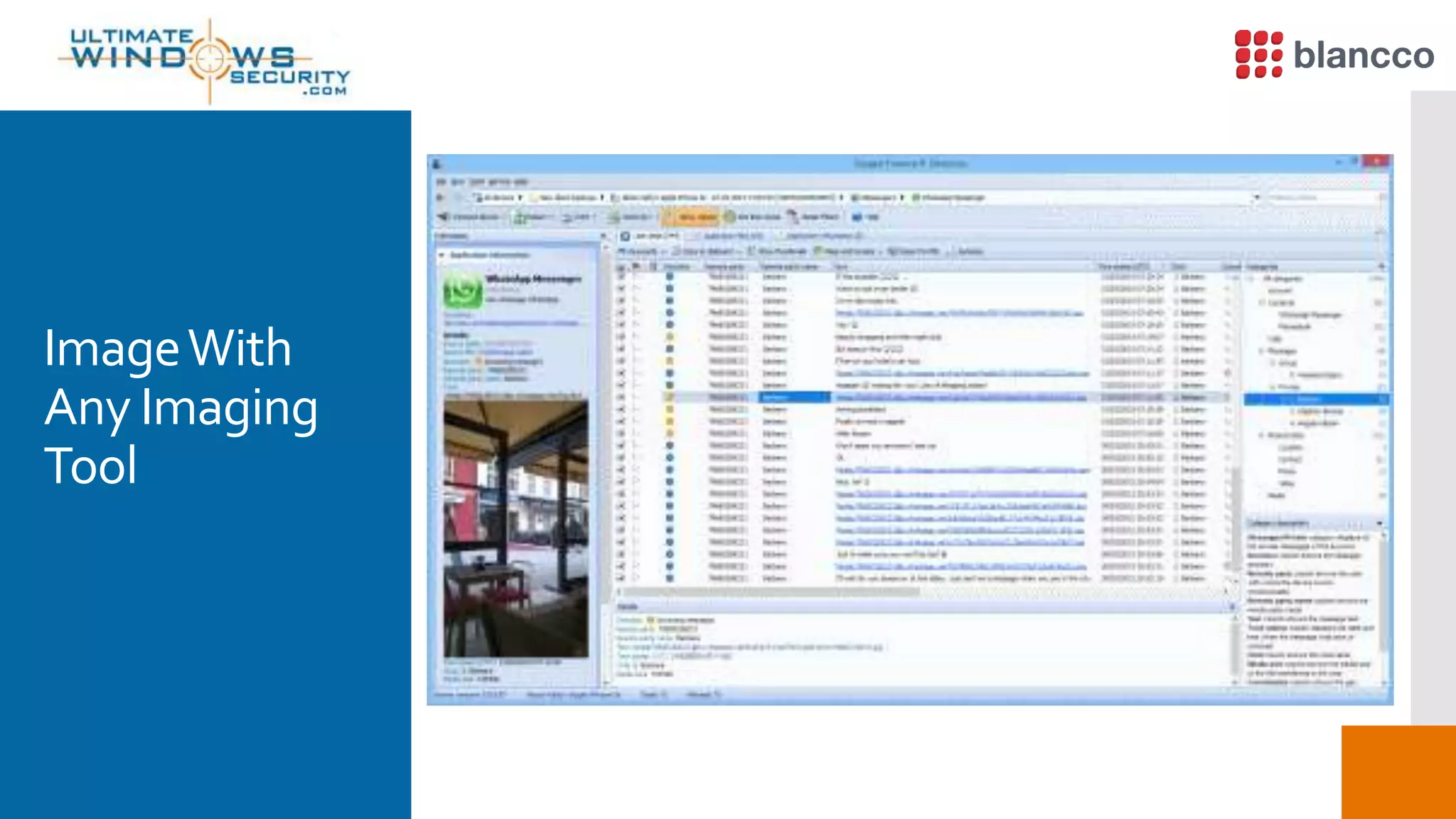
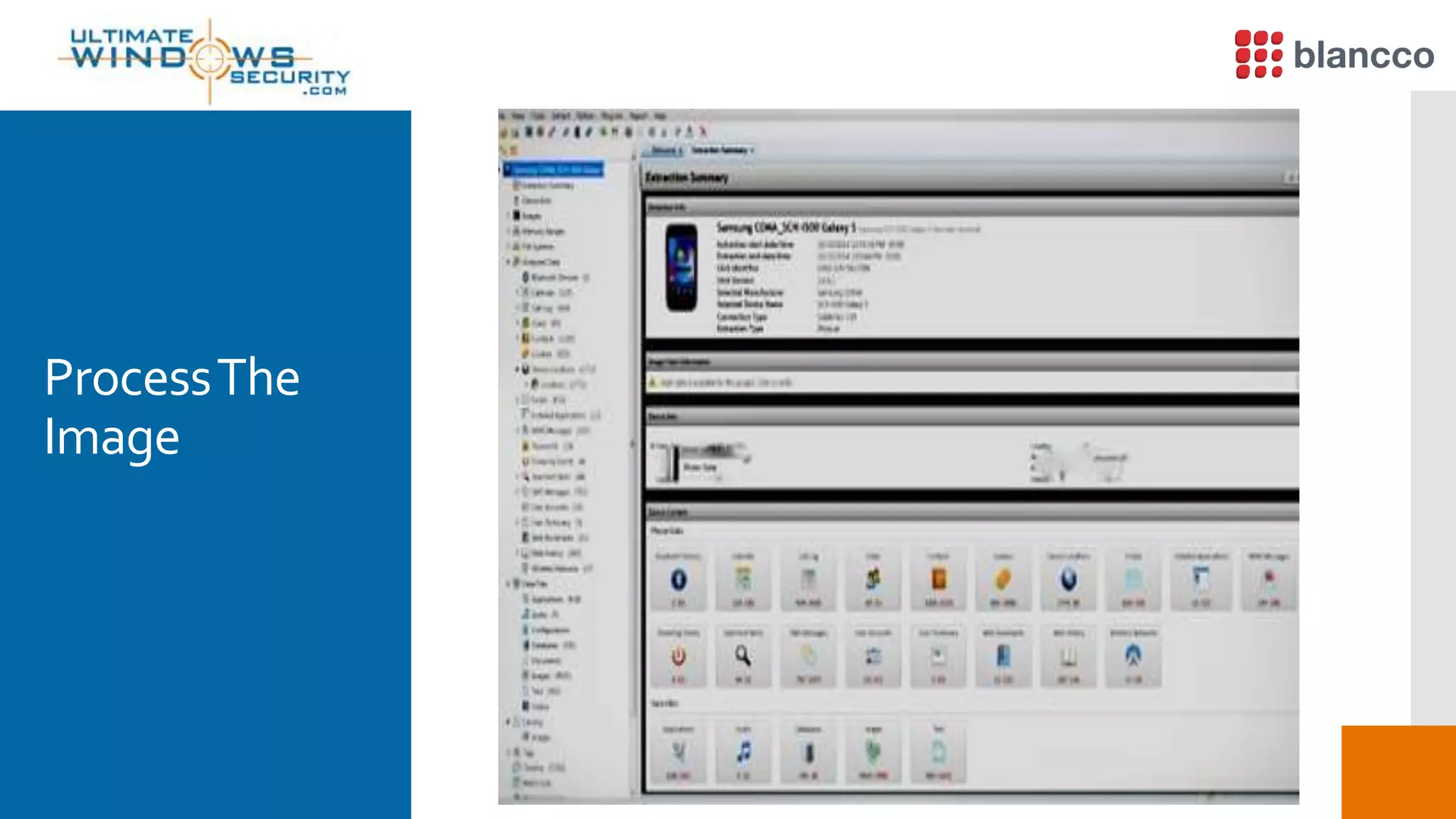
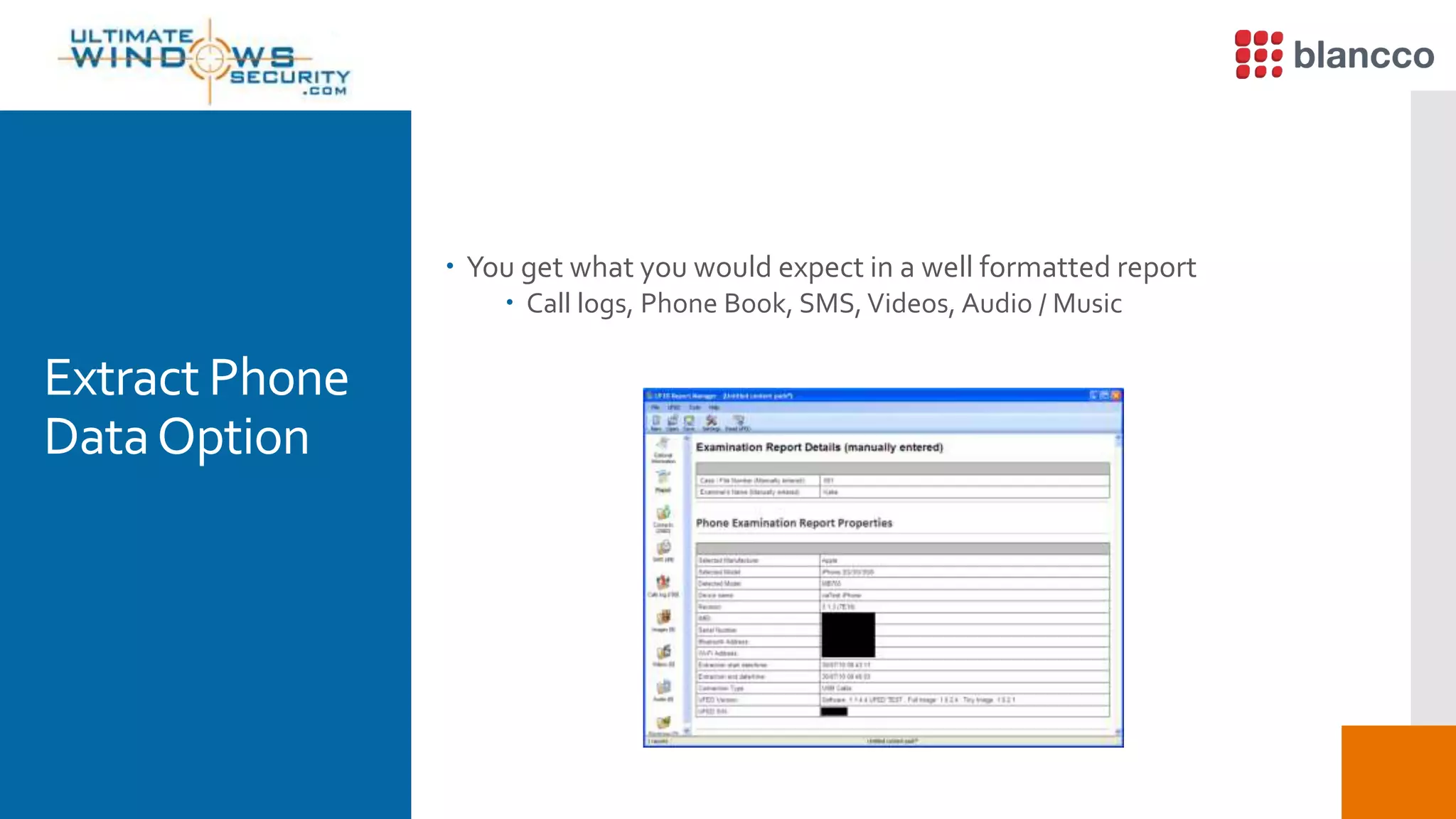
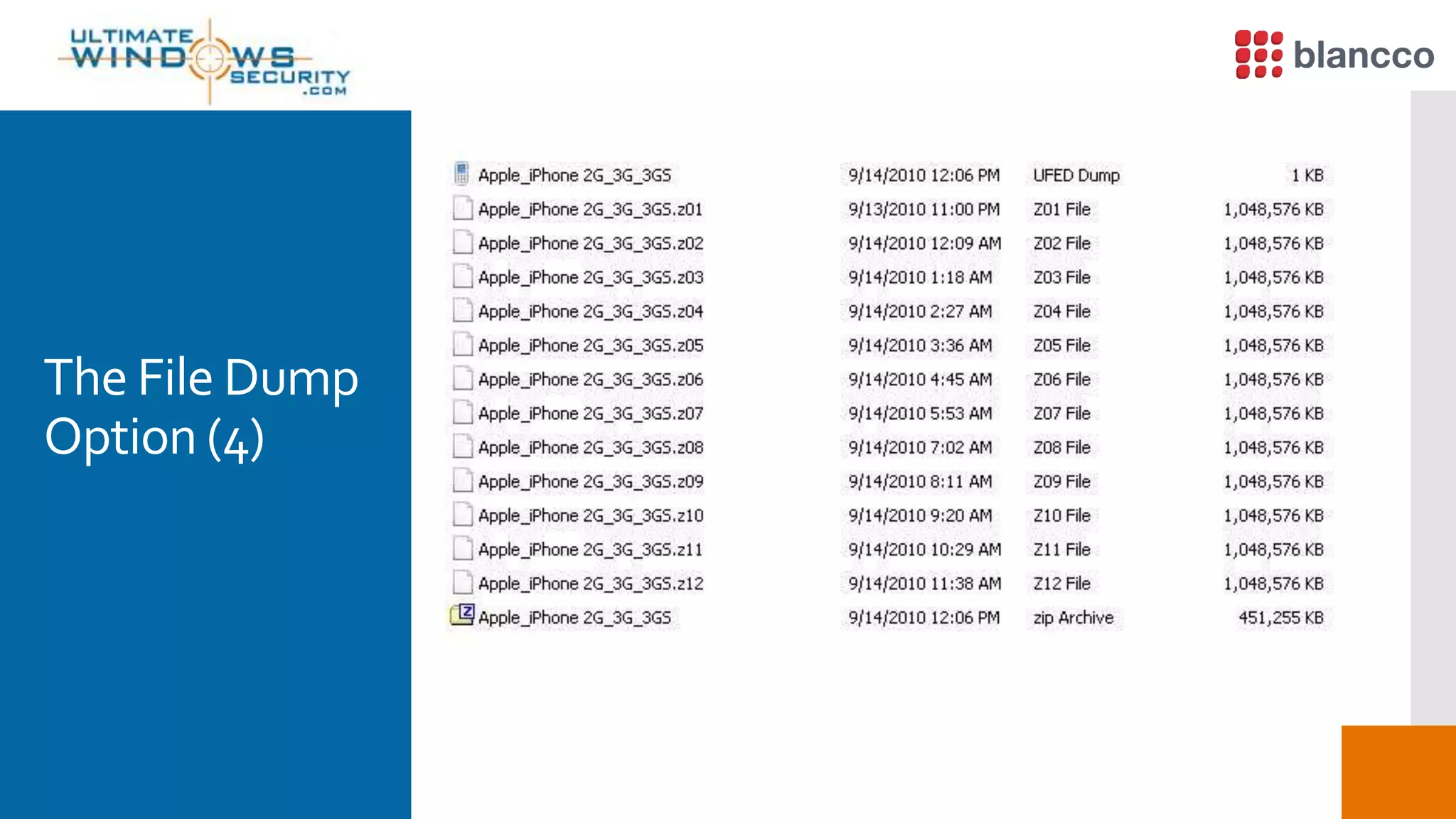
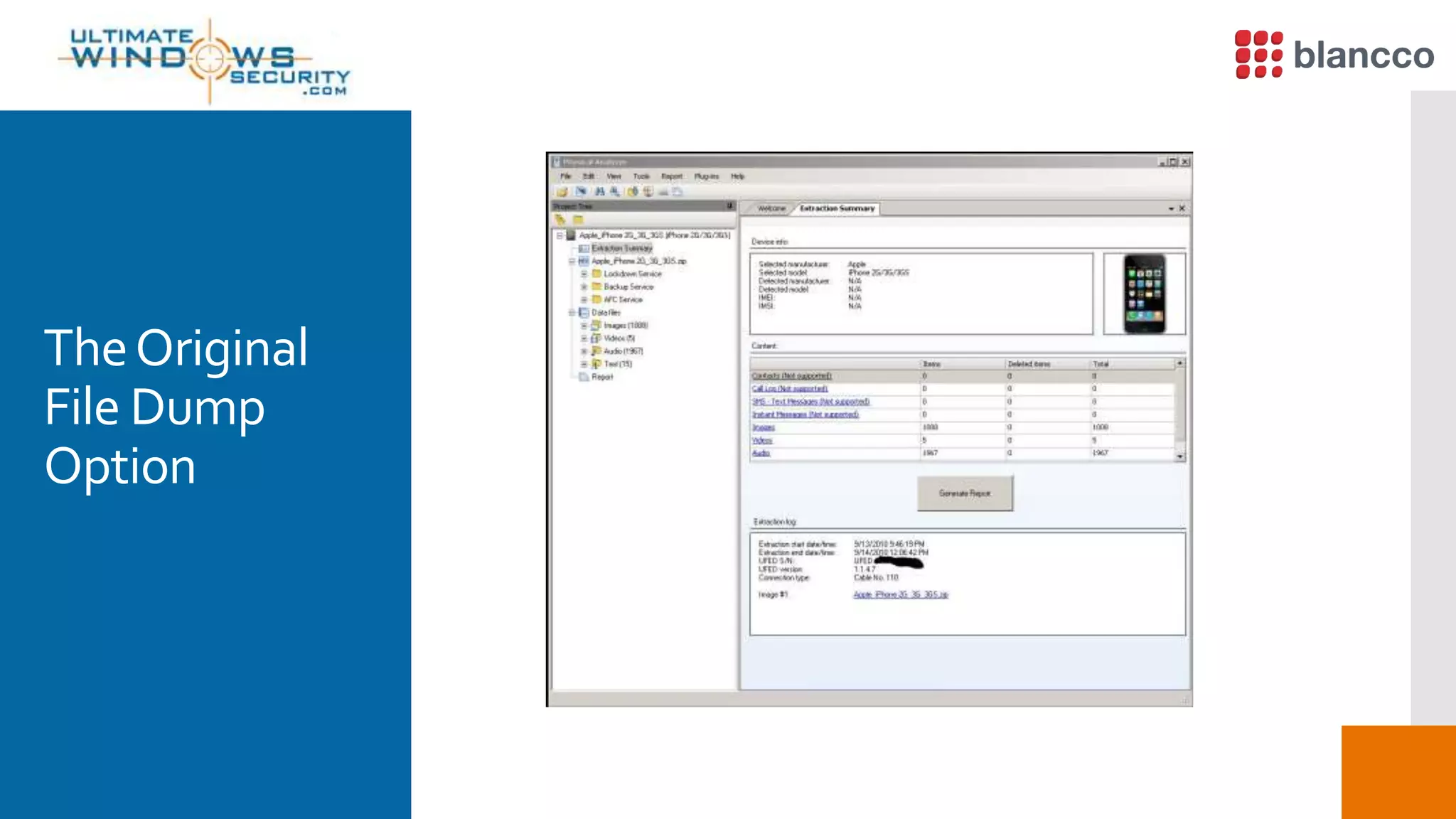
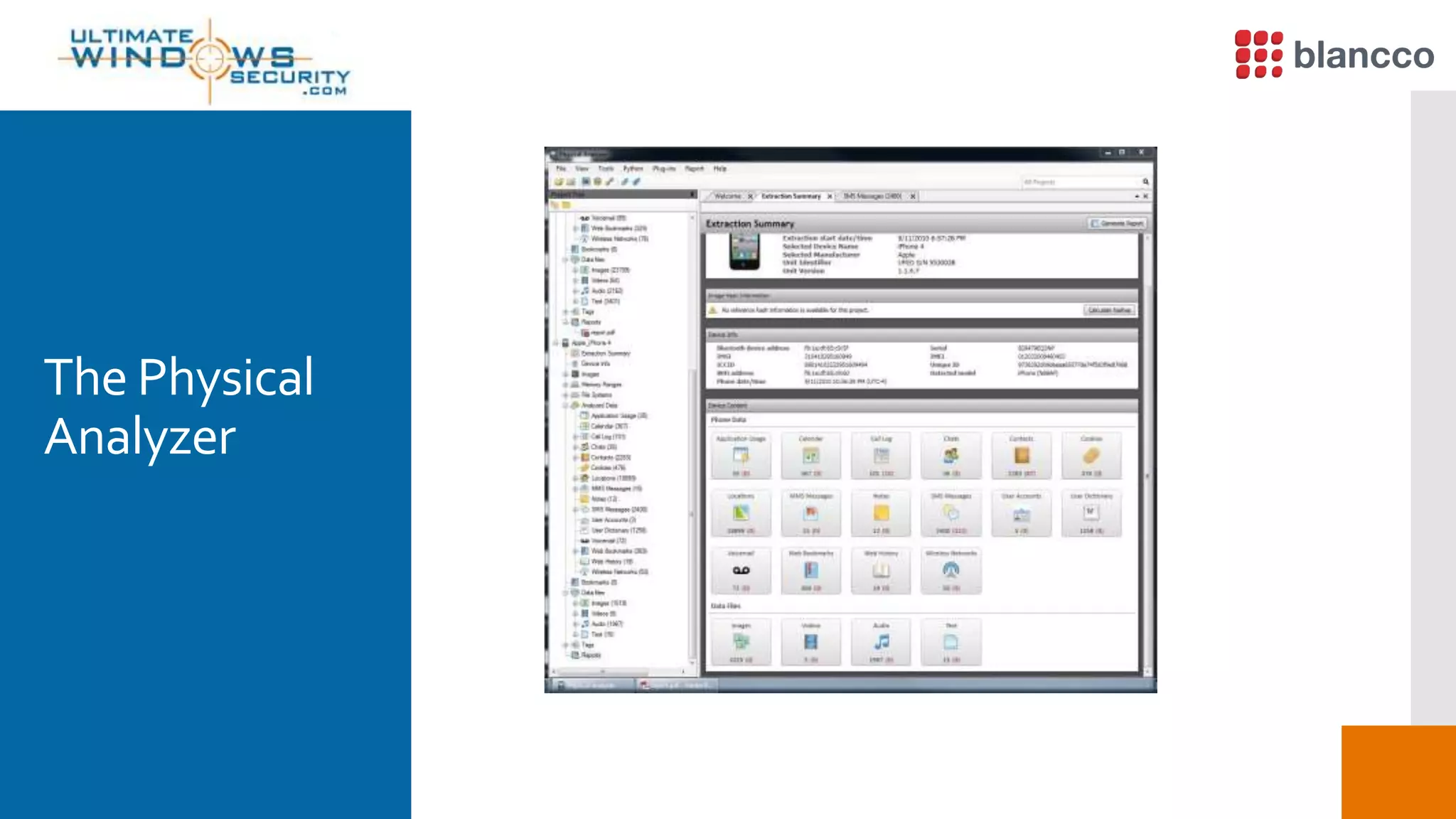
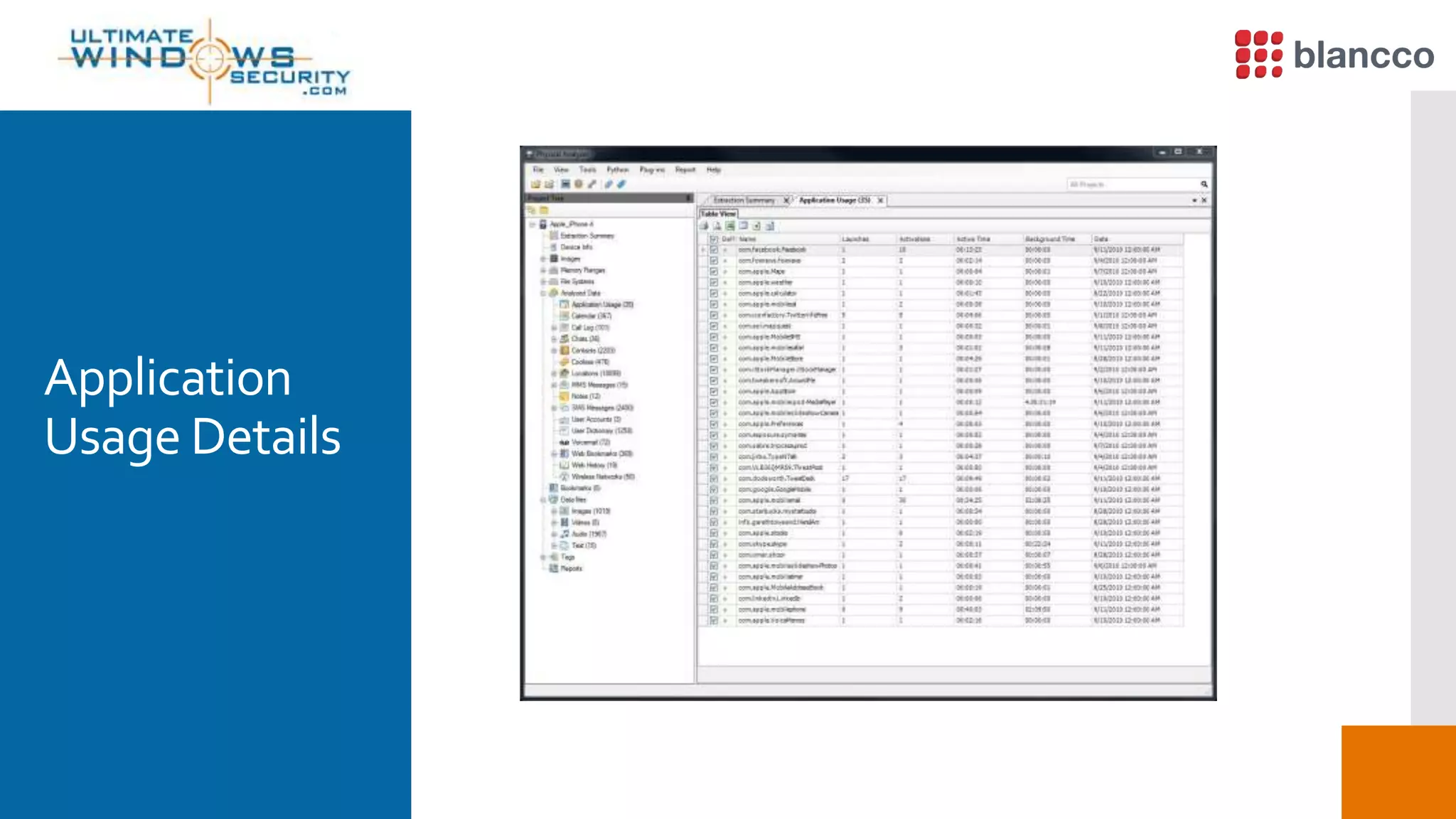
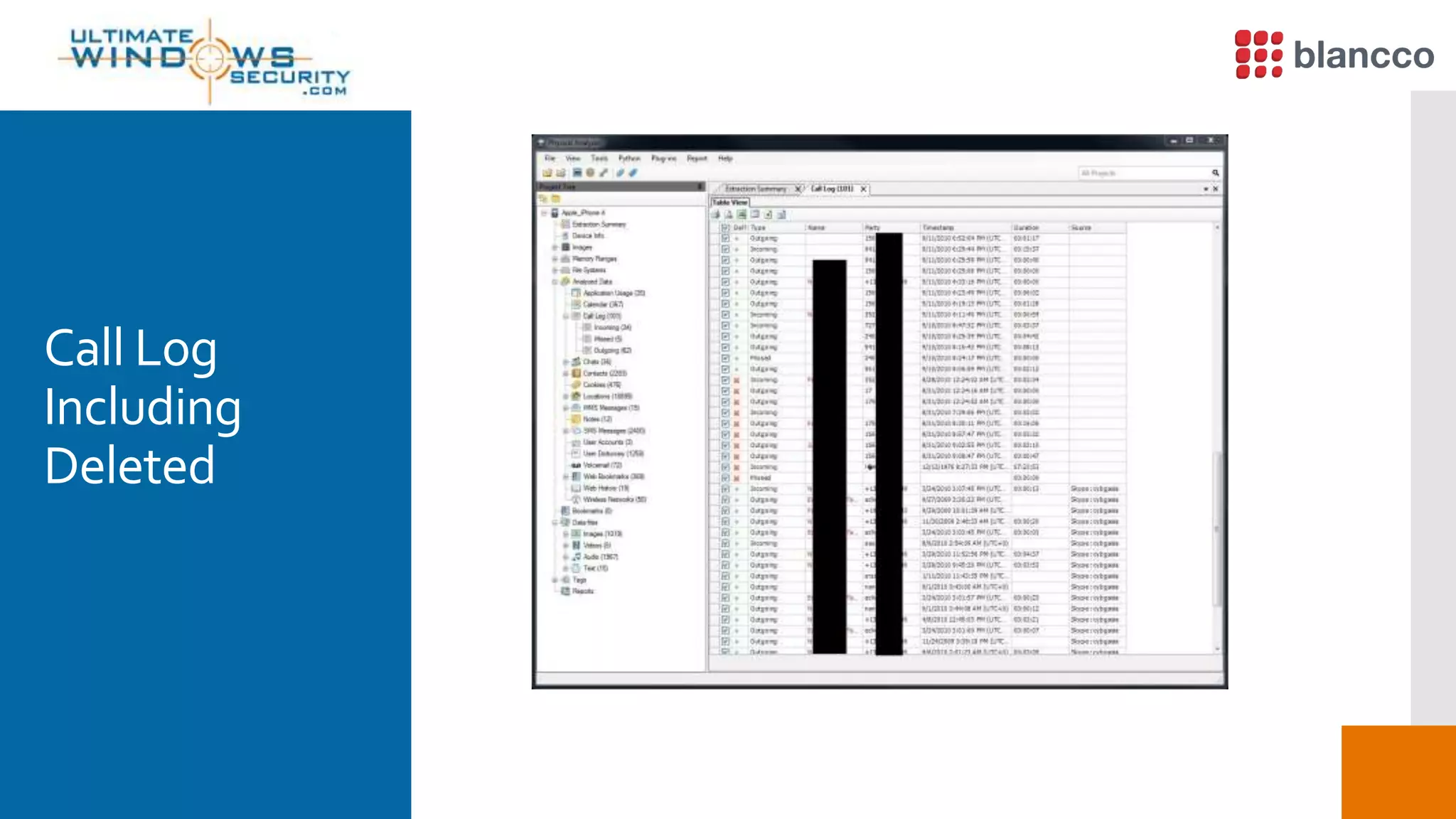
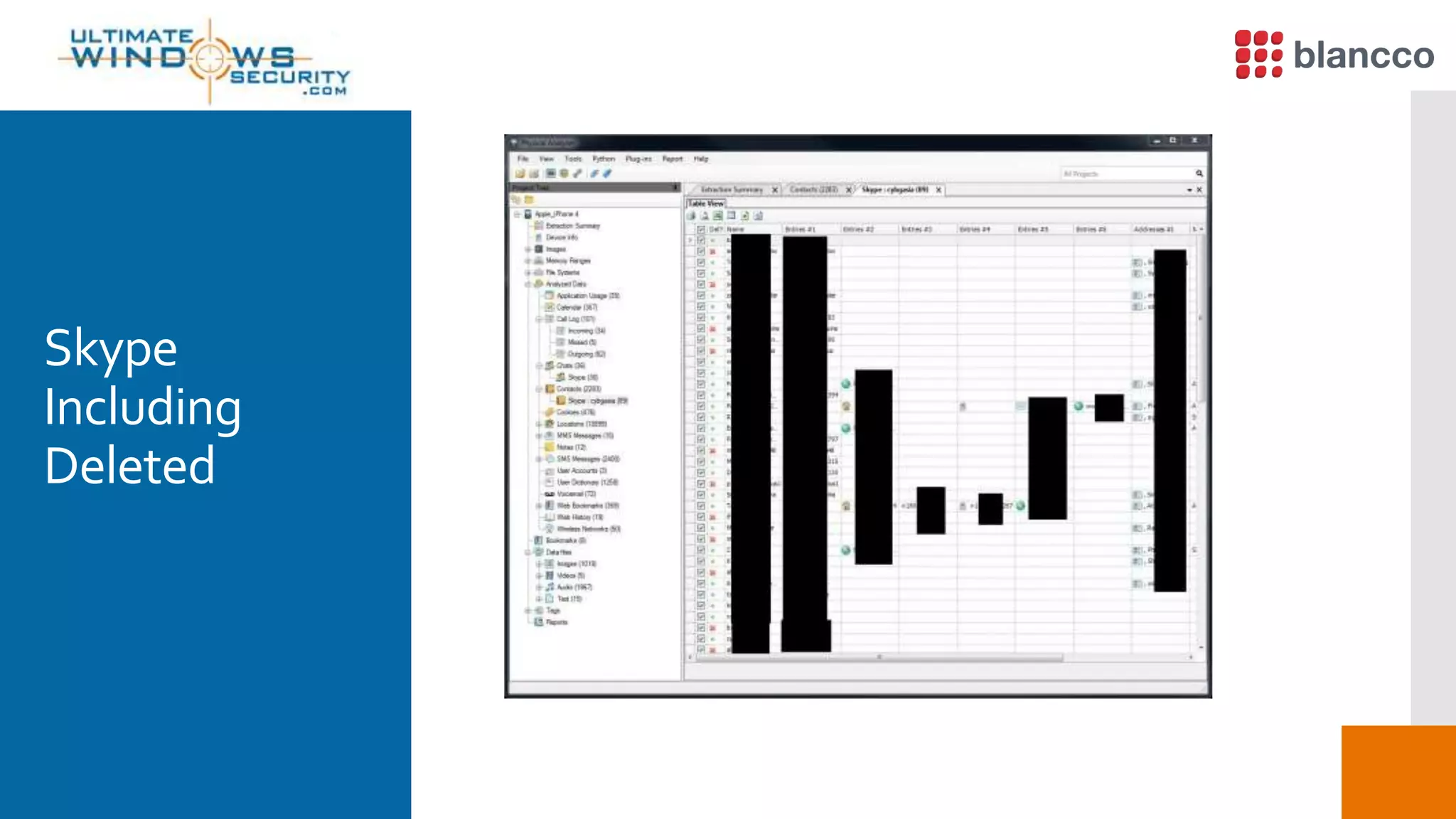
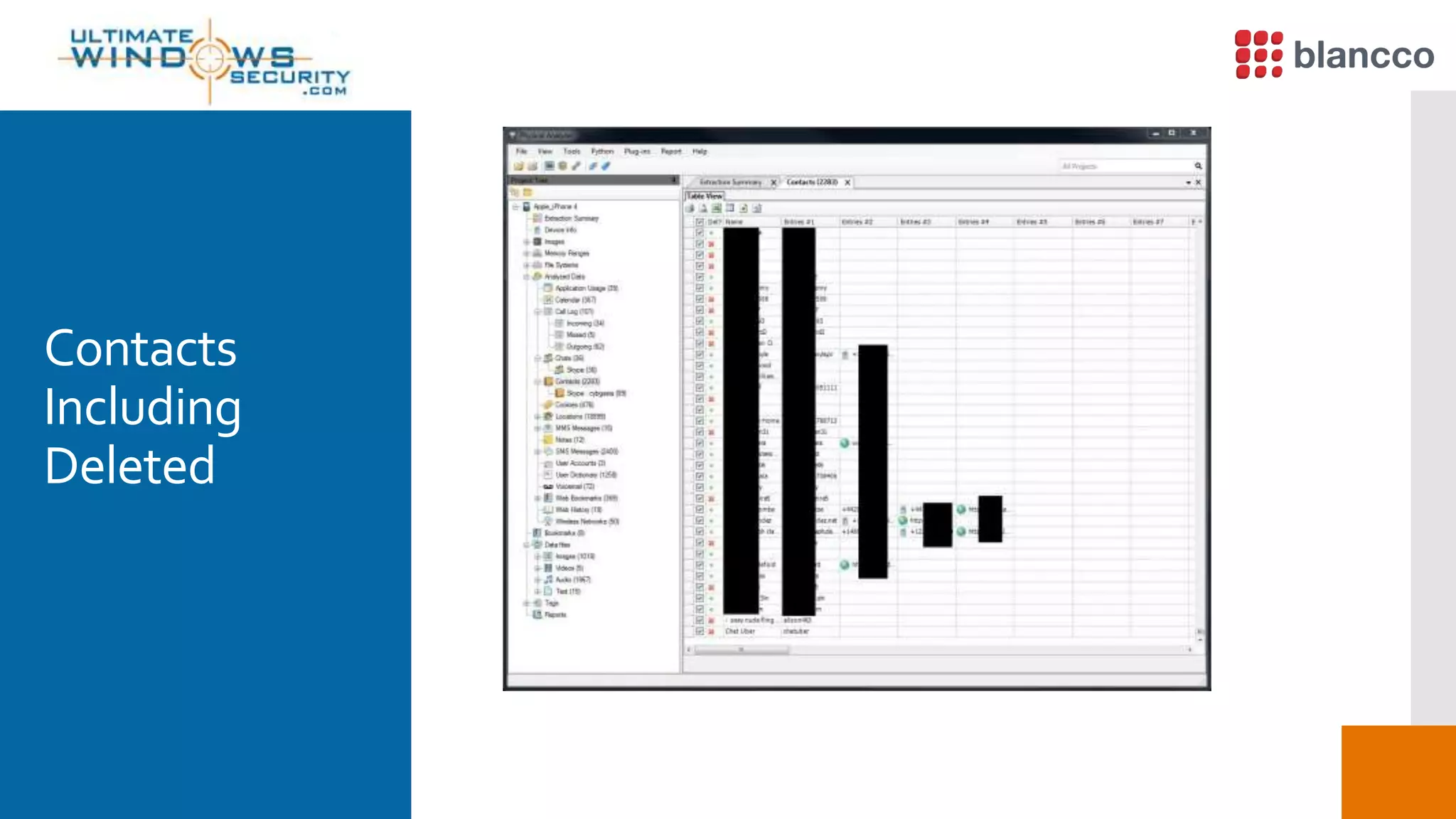
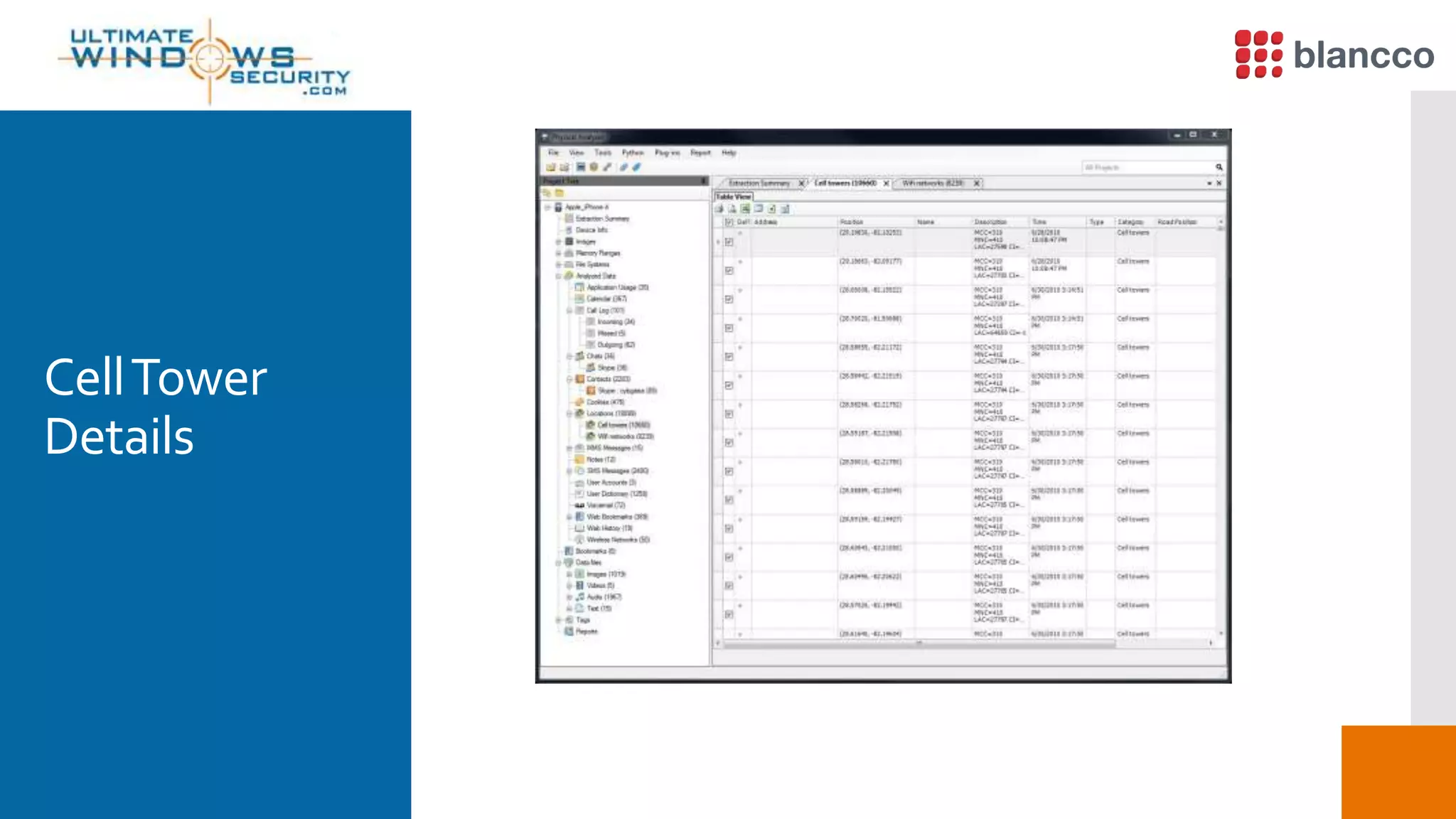
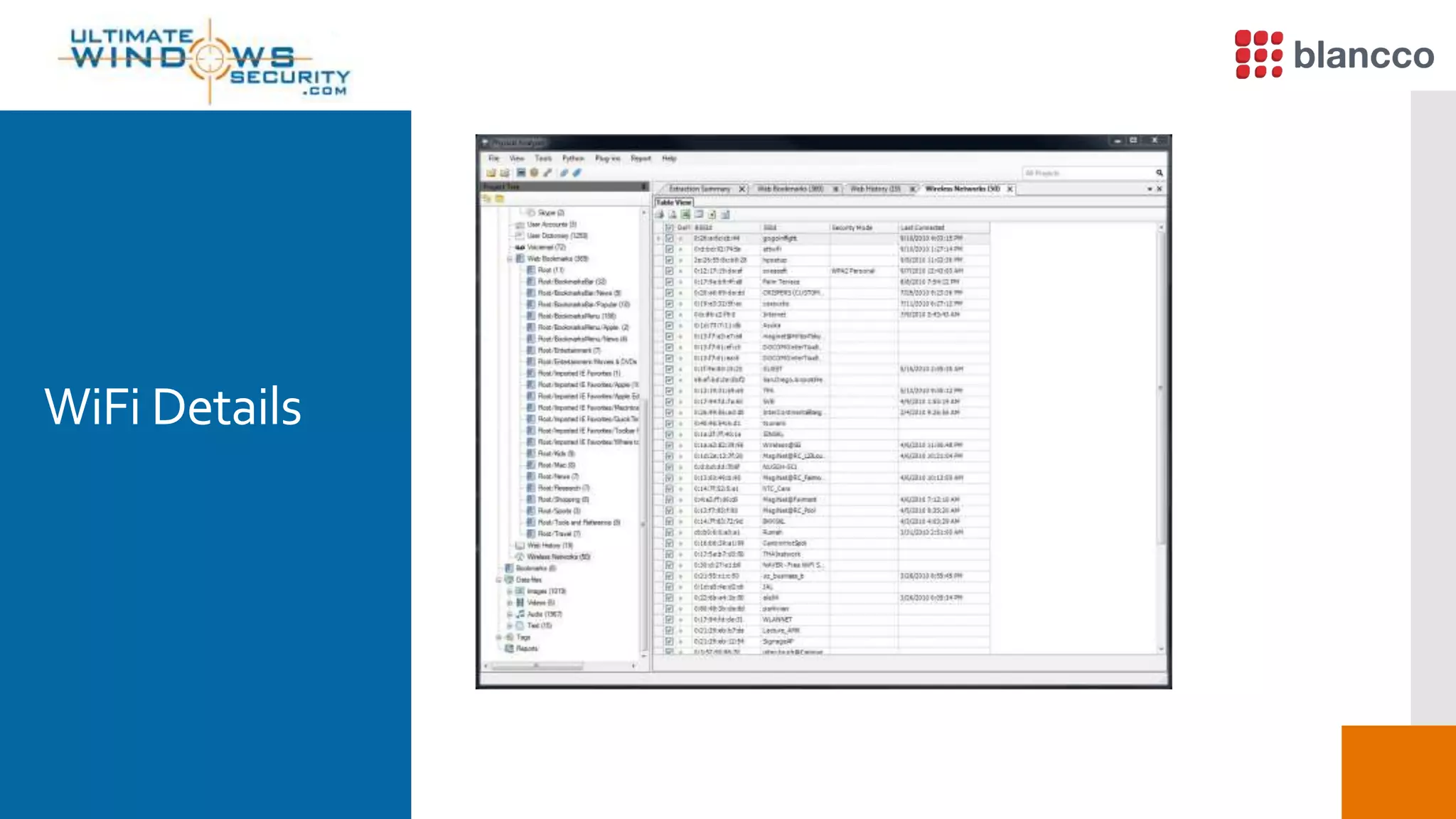
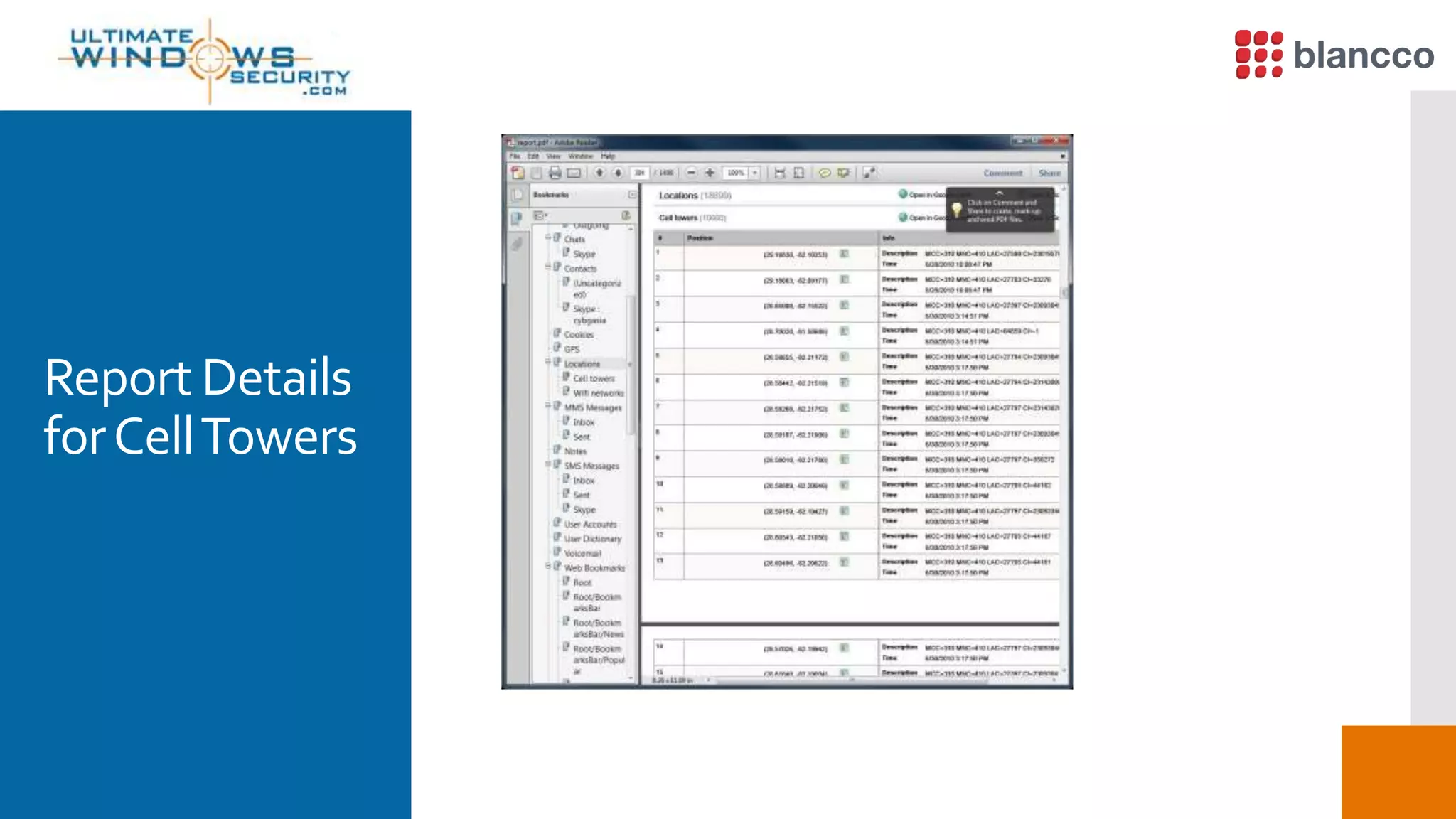
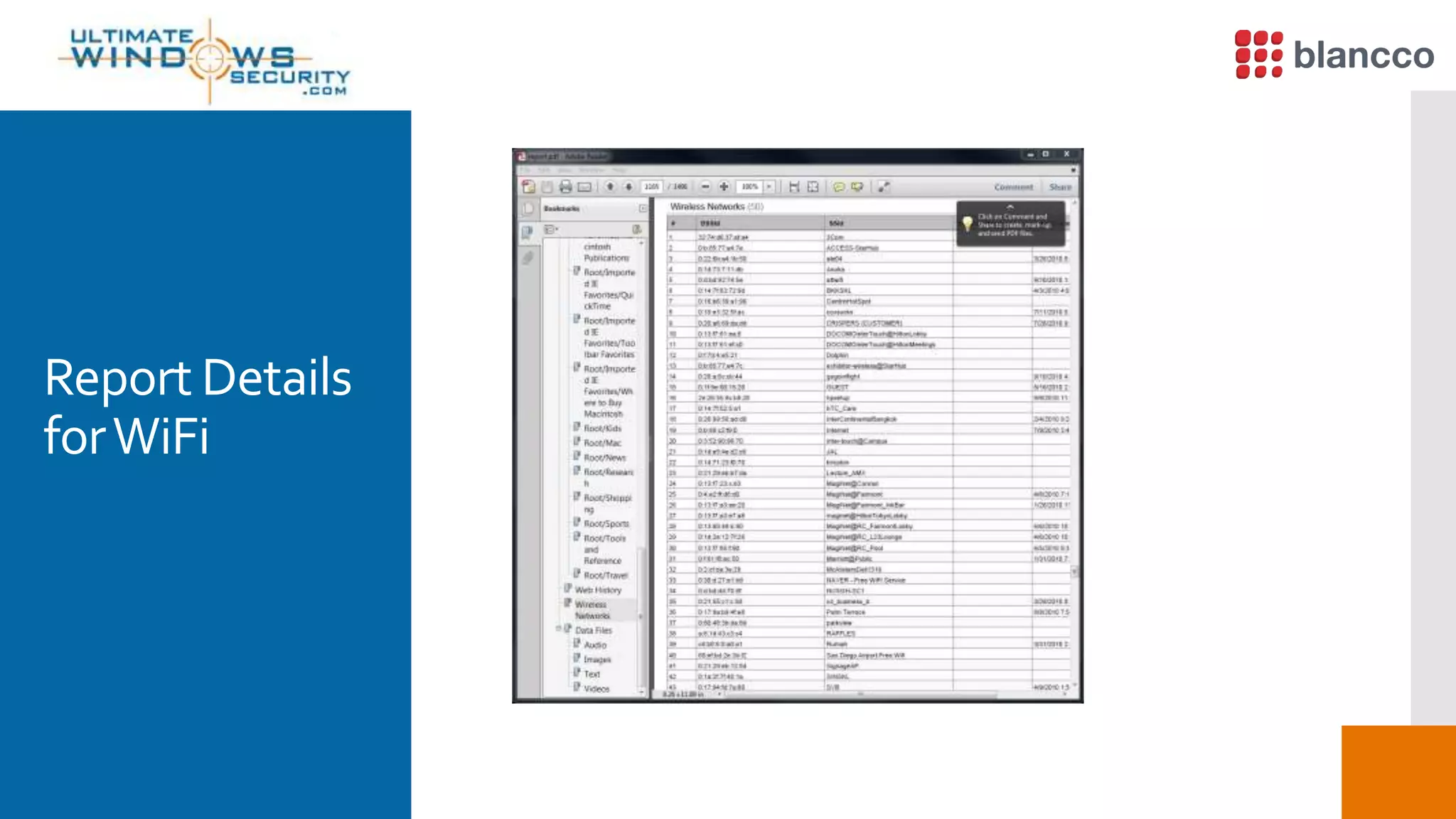
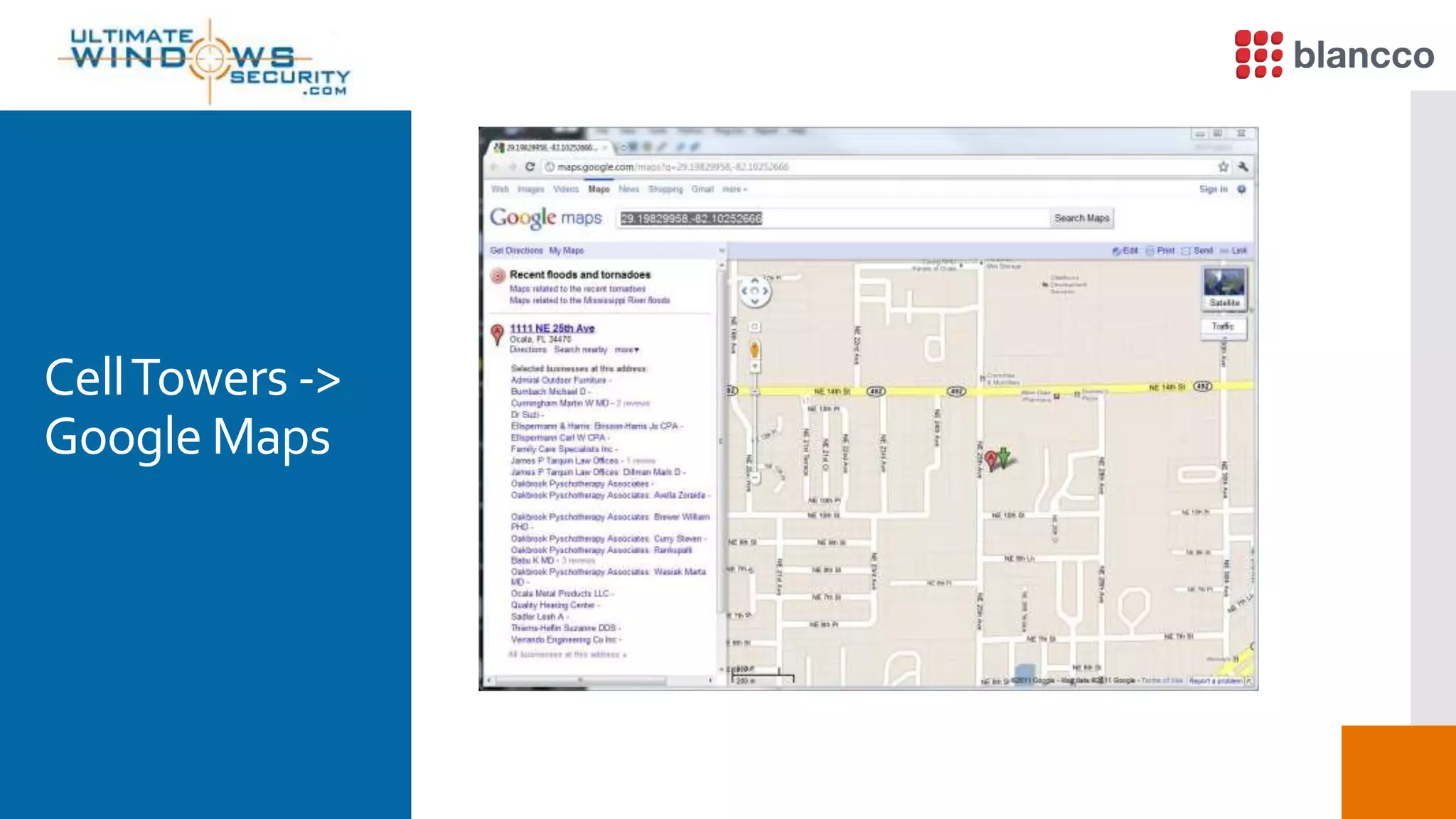
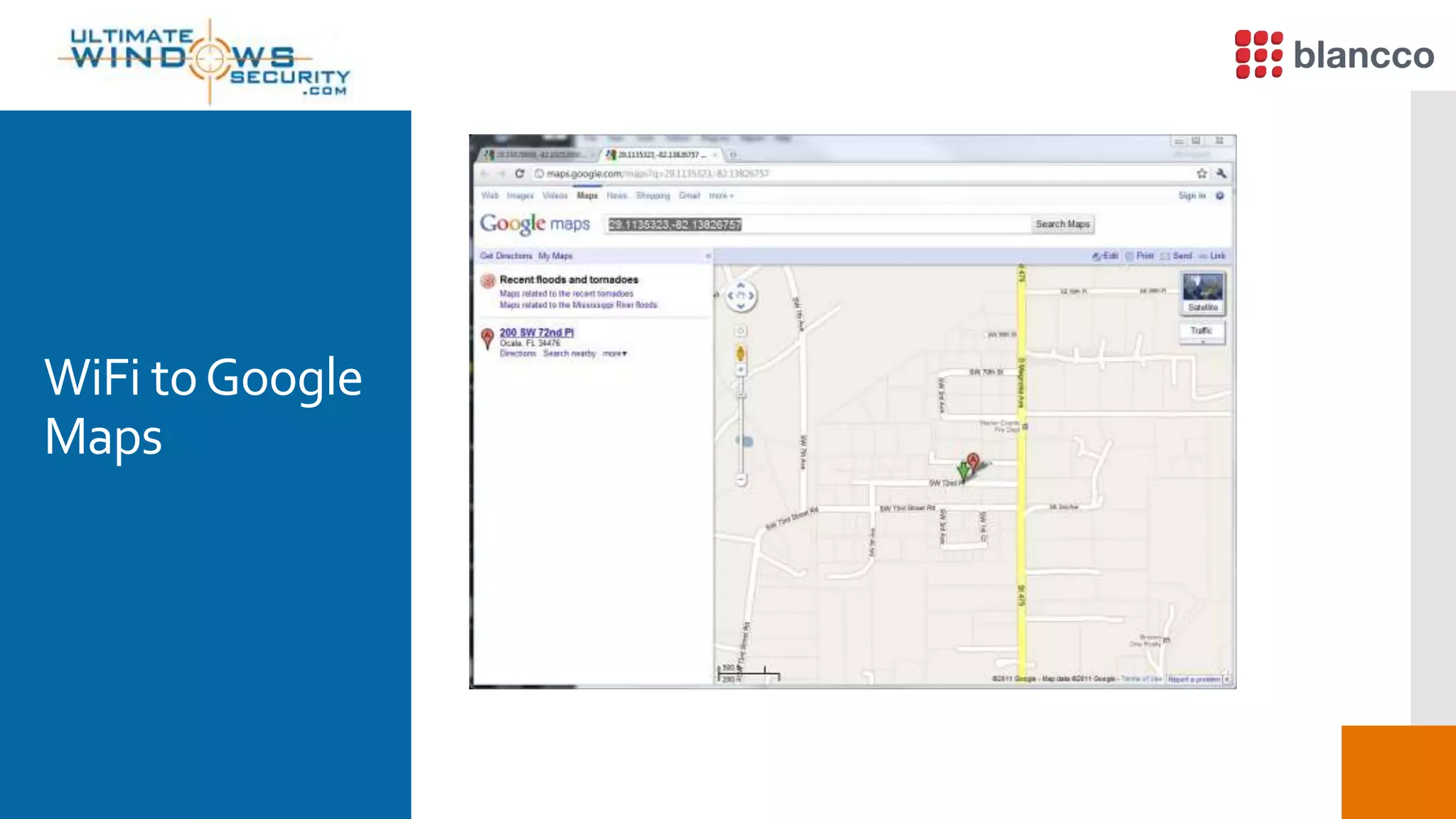
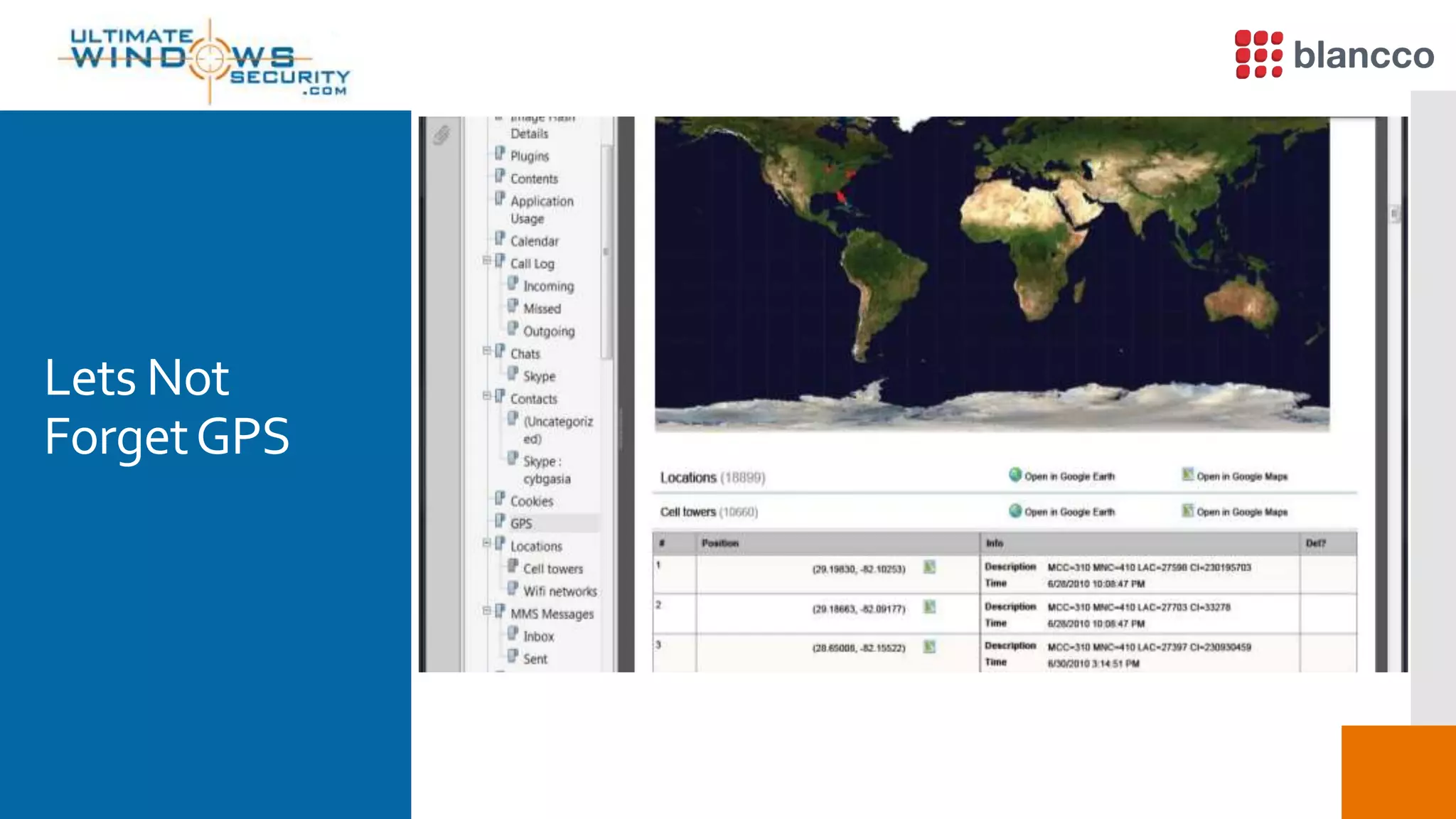
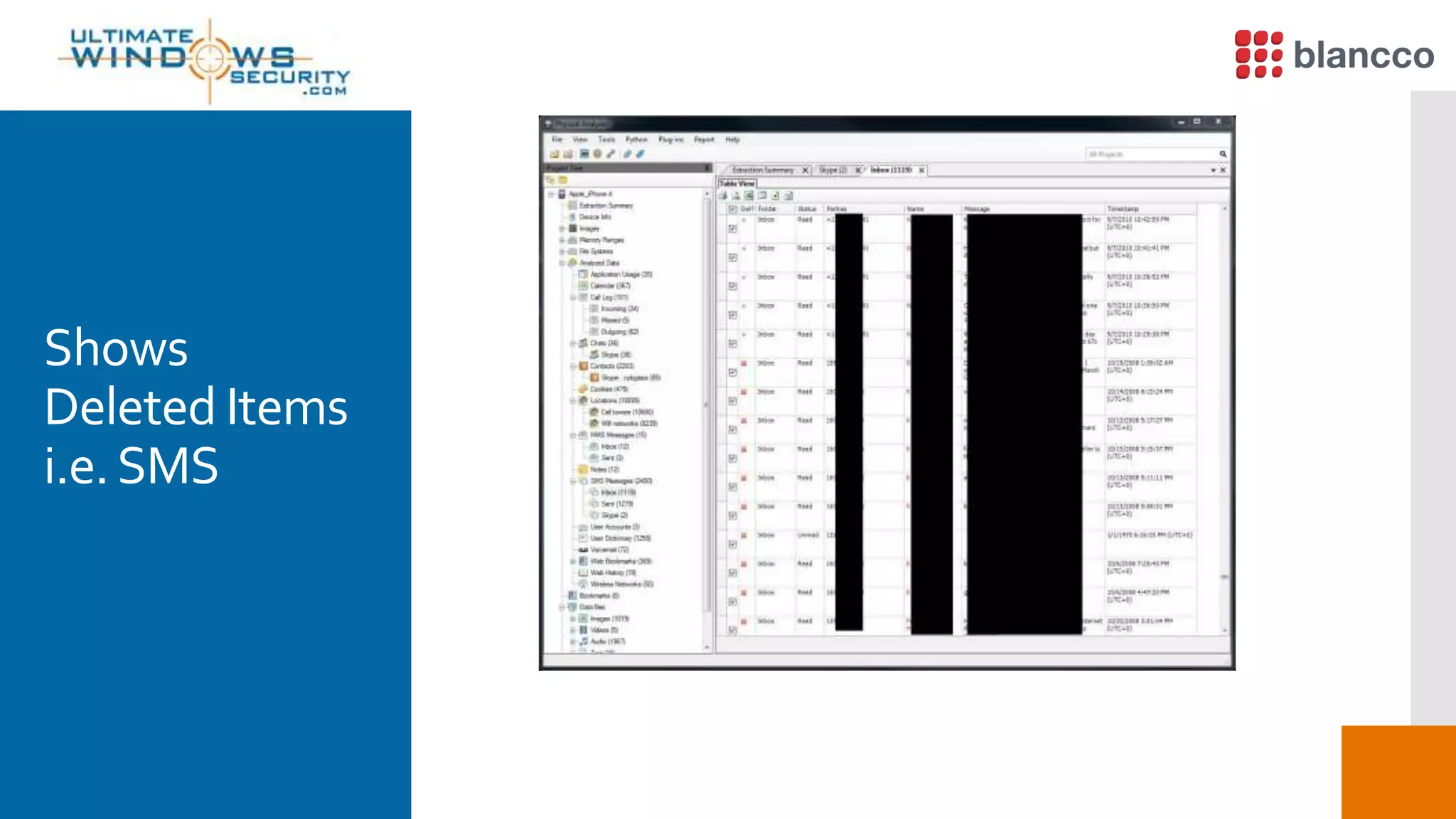
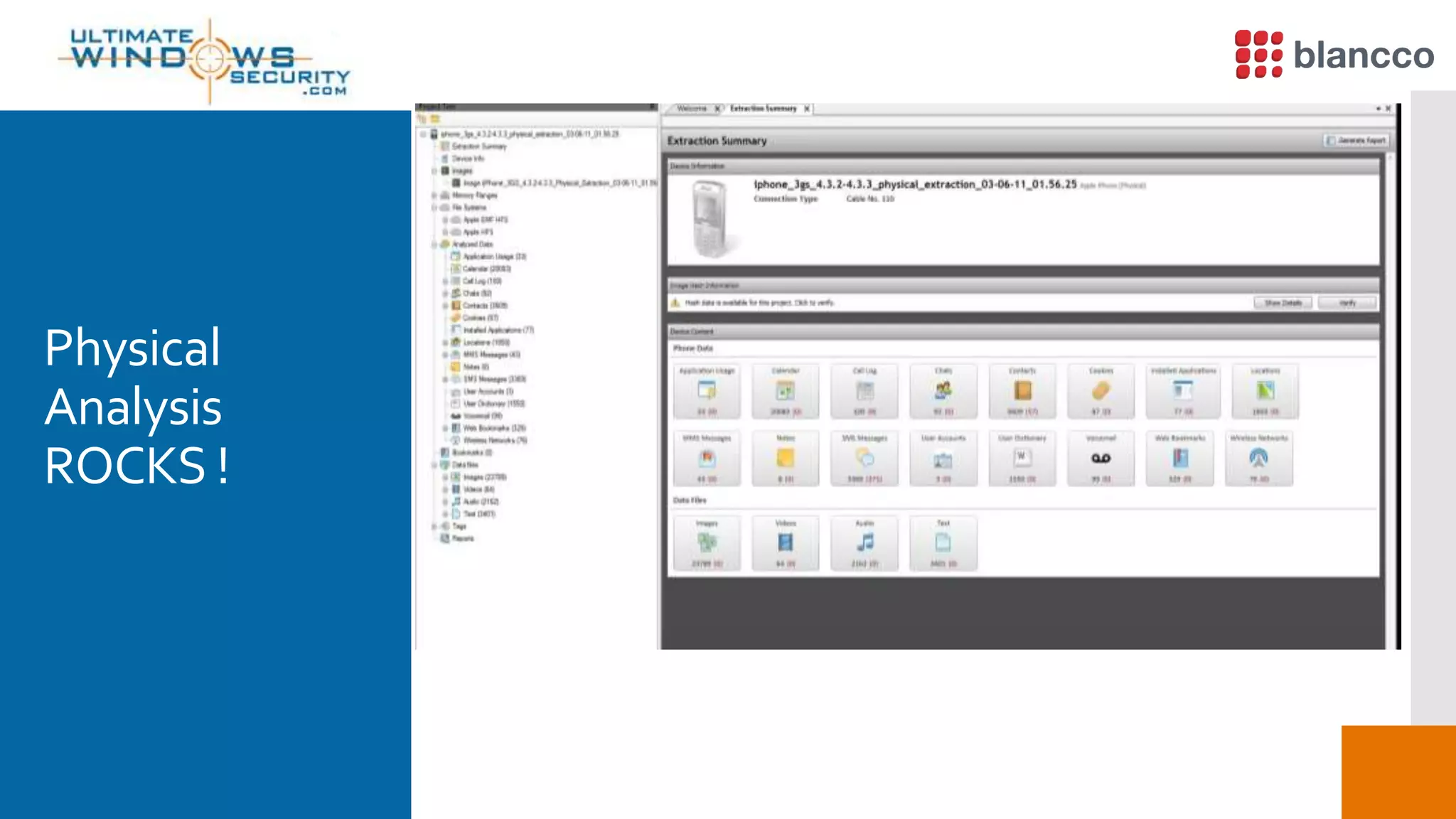
The document discusses data retrieval methods from various devices, such as hard drives, Android, and iPhones, emphasizing potential recovery of deleted files. It highlights the inadequacies of data wiping methods and the importance of physical analysis over logical analysis for comprehensive data recovery. Tools like FTK Imager, Blancco, and SANS SIFT Toolkit are recommended for efficient data recovery processes.