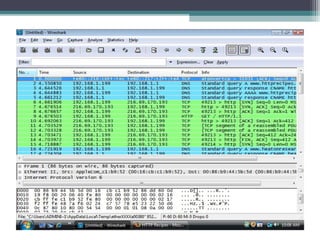
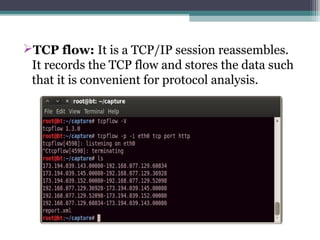
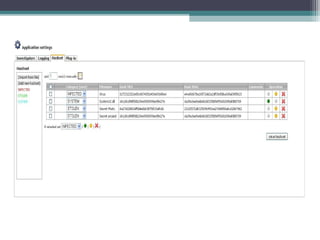
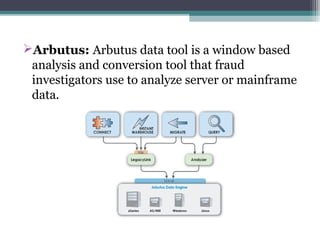
The document outlines the field of computer forensics, which involves the investigation and analysis of digital evidence to support legal proceedings. It covers its history, timeline, the need for computer forensics, types of digital crimes, the methodology employed by forensic experts, and rules for evidence collection. Additionally, it discusses various forensic tools used in the field and highlights an example of a high-profile case solved through computer forensics.