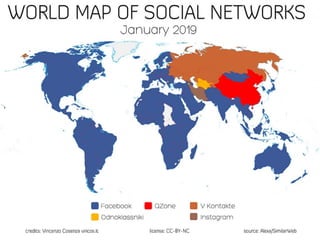
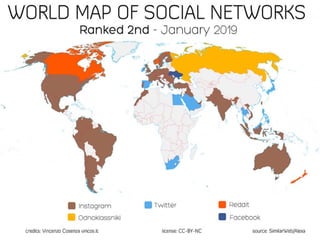
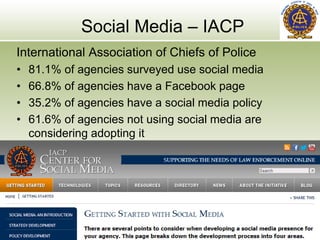
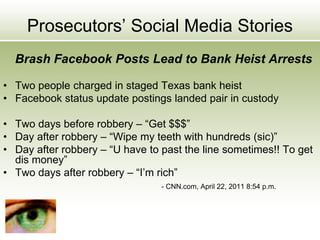
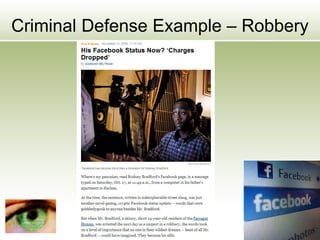
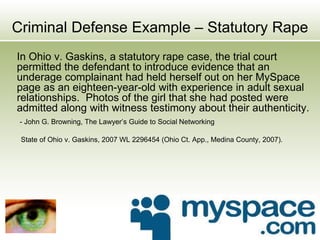
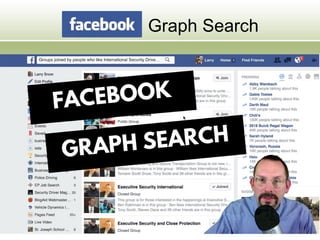
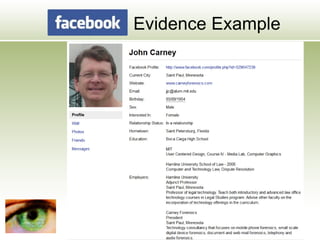
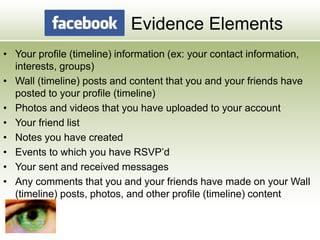
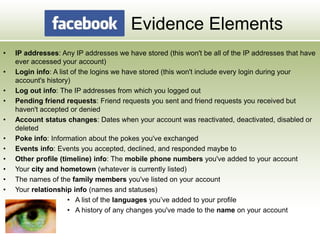
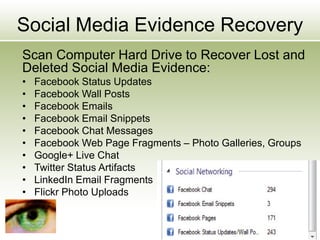
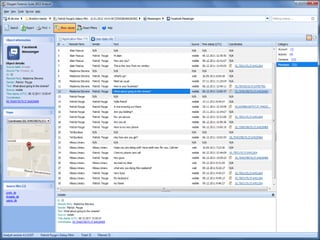
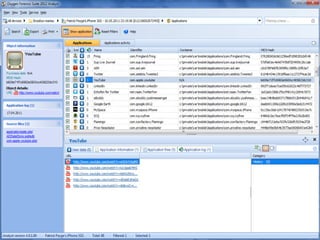
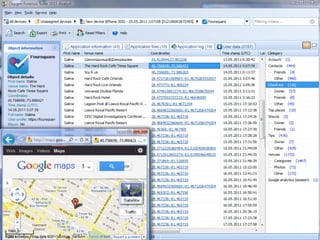
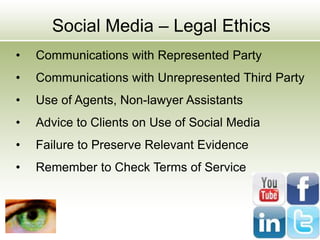
The document discusses the impact of social media as a crucial source of evidence in legal proceedings, highlighting its role in investigations and how it serves as a 'new confessional' for individuals. It covers various social media platforms, the types of evidence they provide, and the legal implications surrounding the discovery and admissibility of social media evidence. Additionally, it addresses the ethical considerations attorneys must navigate when dealing with social media in the context of legal representation.