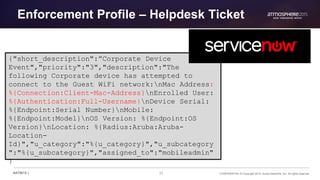
This document discusses ClearPass design scenarios for improving the user experience while maintaining security. It addresses allowing employees on the guest network, identifying corporate devices, and supporting "headless" wired and wireless devices that do not support 802.1x authentication. The document recommends using ClearPass policies to communicate with users, provide self-service options, dynamically update other systems, and proactively identify and resolve problems to balance usability and security. It also suggests profiling and registering devices to authorize network access for devices that cannot use 802.1x authentication.















![23 CONFIDENTIAL © Copyright 2015. Aruba Networks, Inc. All rights reserved#ATM15 |
Endpoint Attribute Tagging
ClearPass
AD/LDAP
Device
Authentication
SSID: Secure
WPA2-AES
[MACHINE AUTHENTICATED]
Certificate:Issuer-CN
Update Endpoint
Ownership:
Corporate
MAC | 11:22:33:44:55:66
Authorization](https://image.slidesharecdn.com/clearpassdesignscenariosfinal-150302154459-conversion-gate02/85/ClearPass-design-scenarios-that-solve-the-toughest-security-policy-requirements-19-320.jpg)