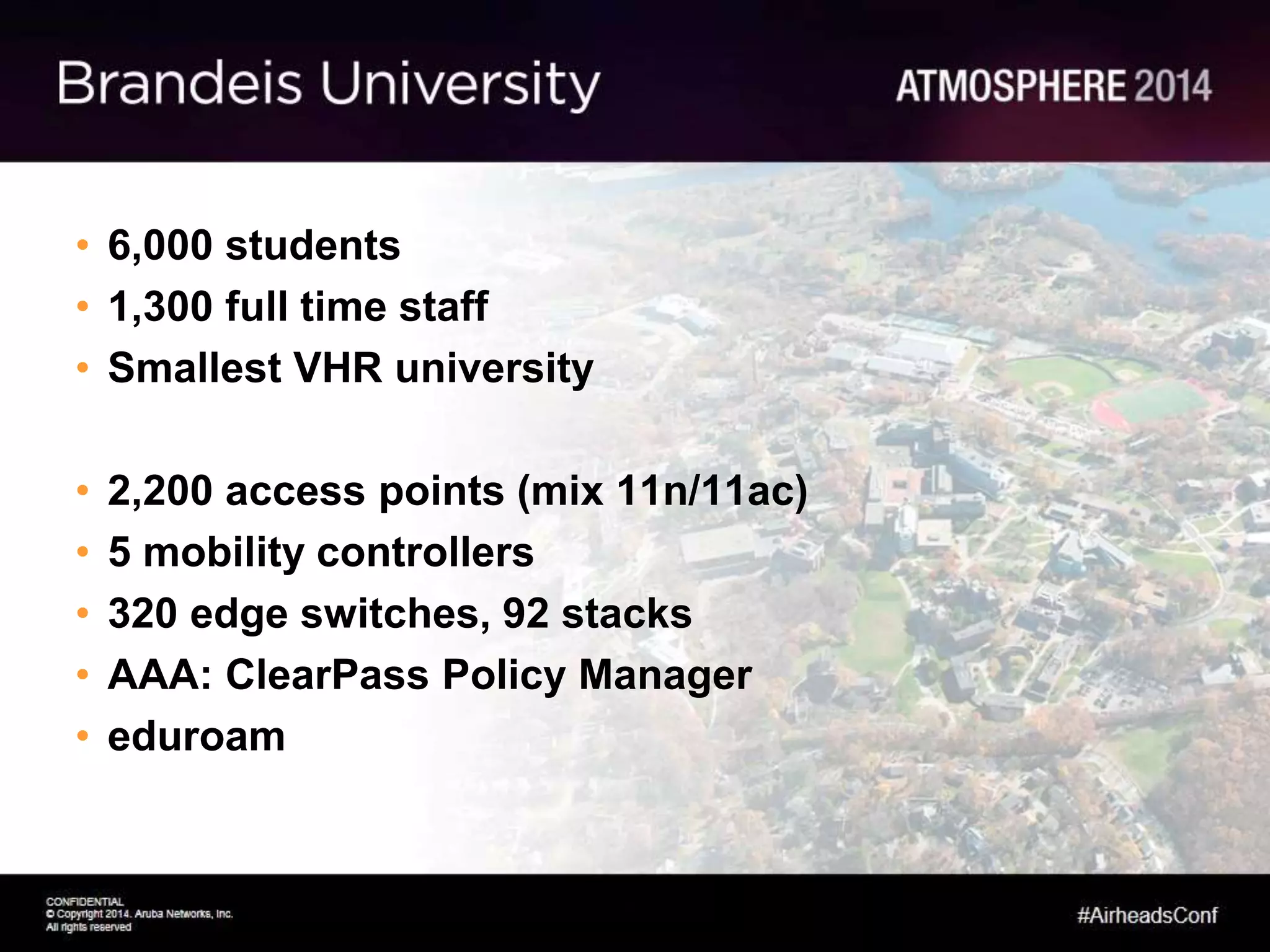
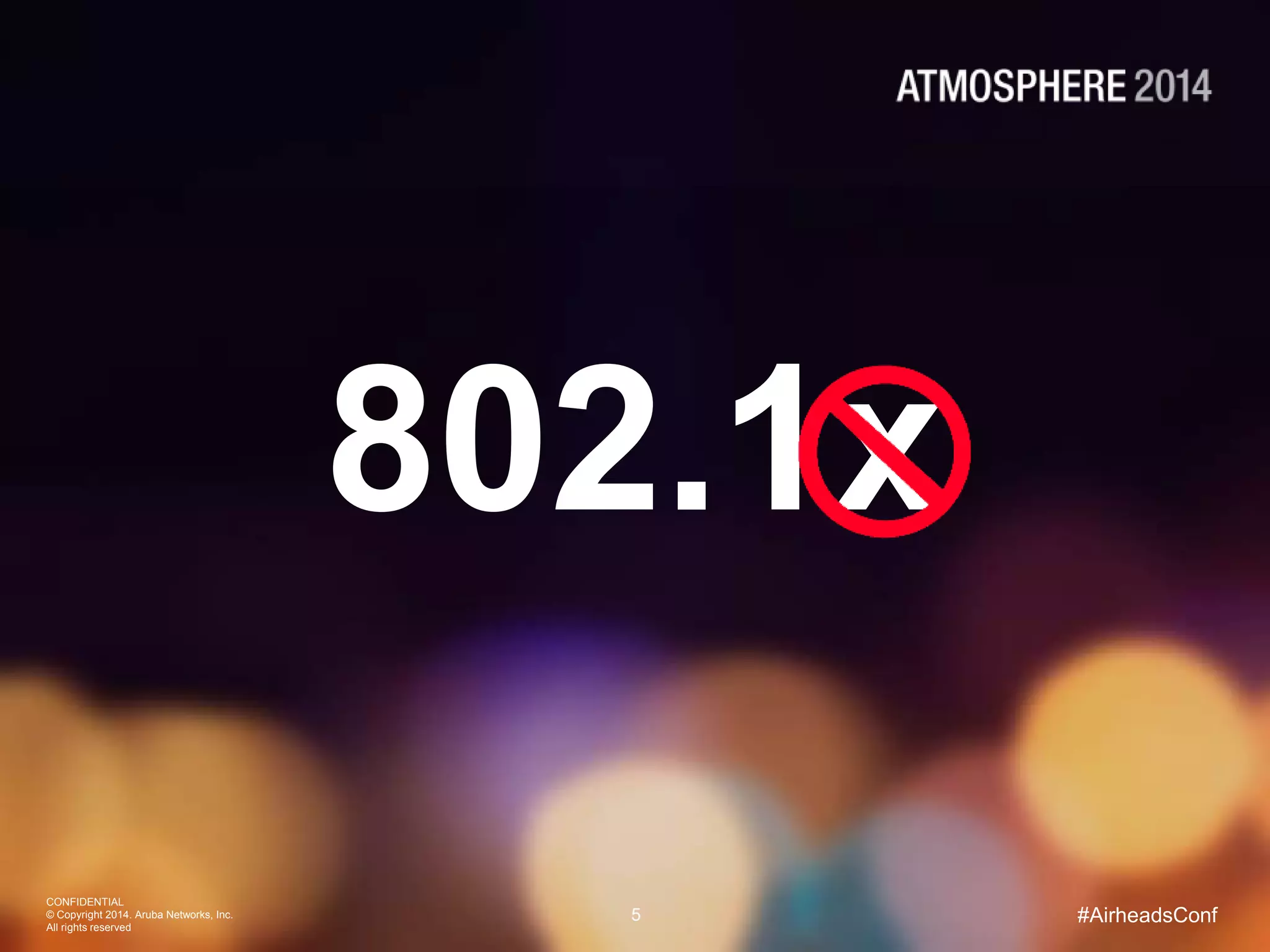
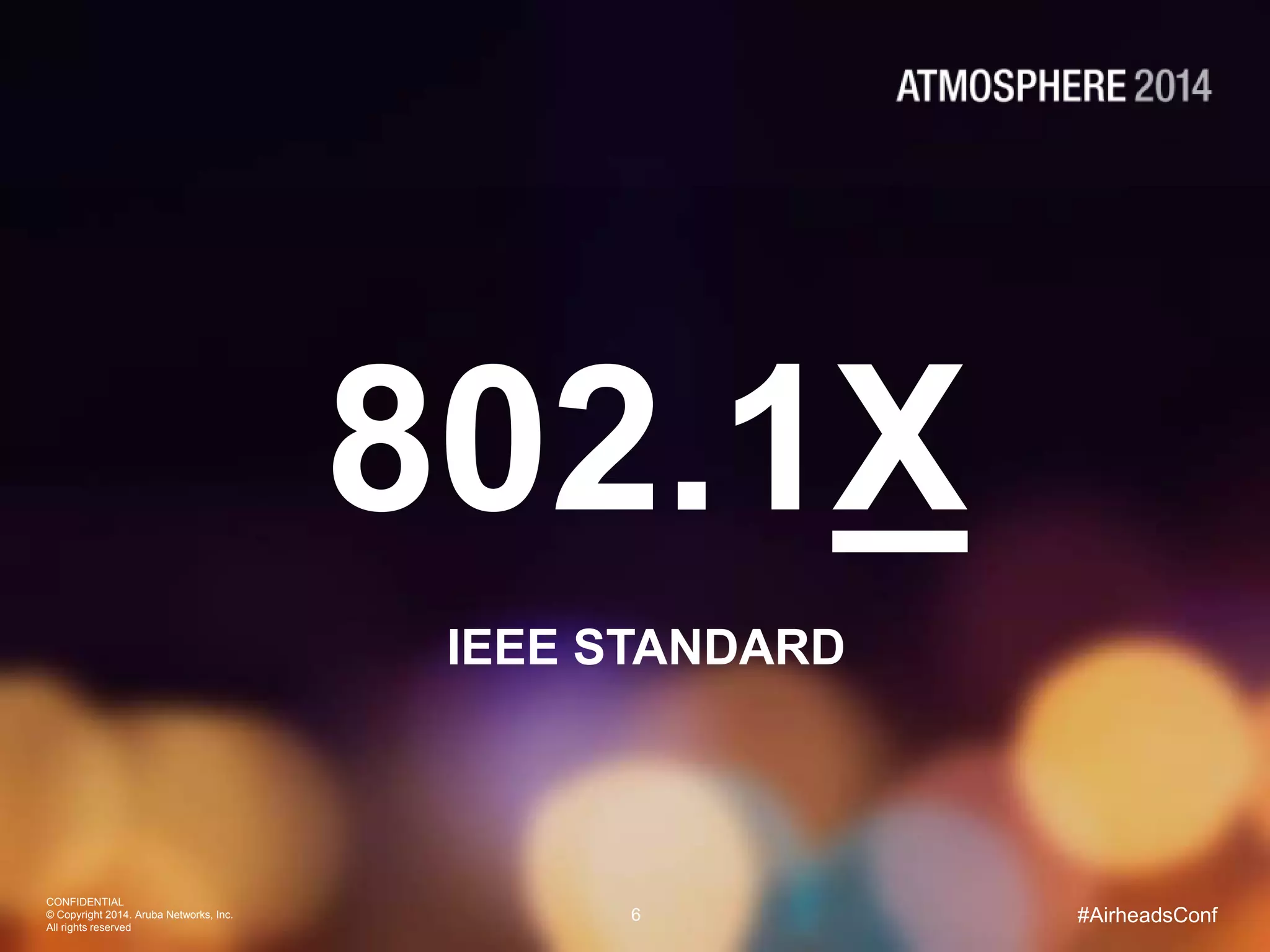
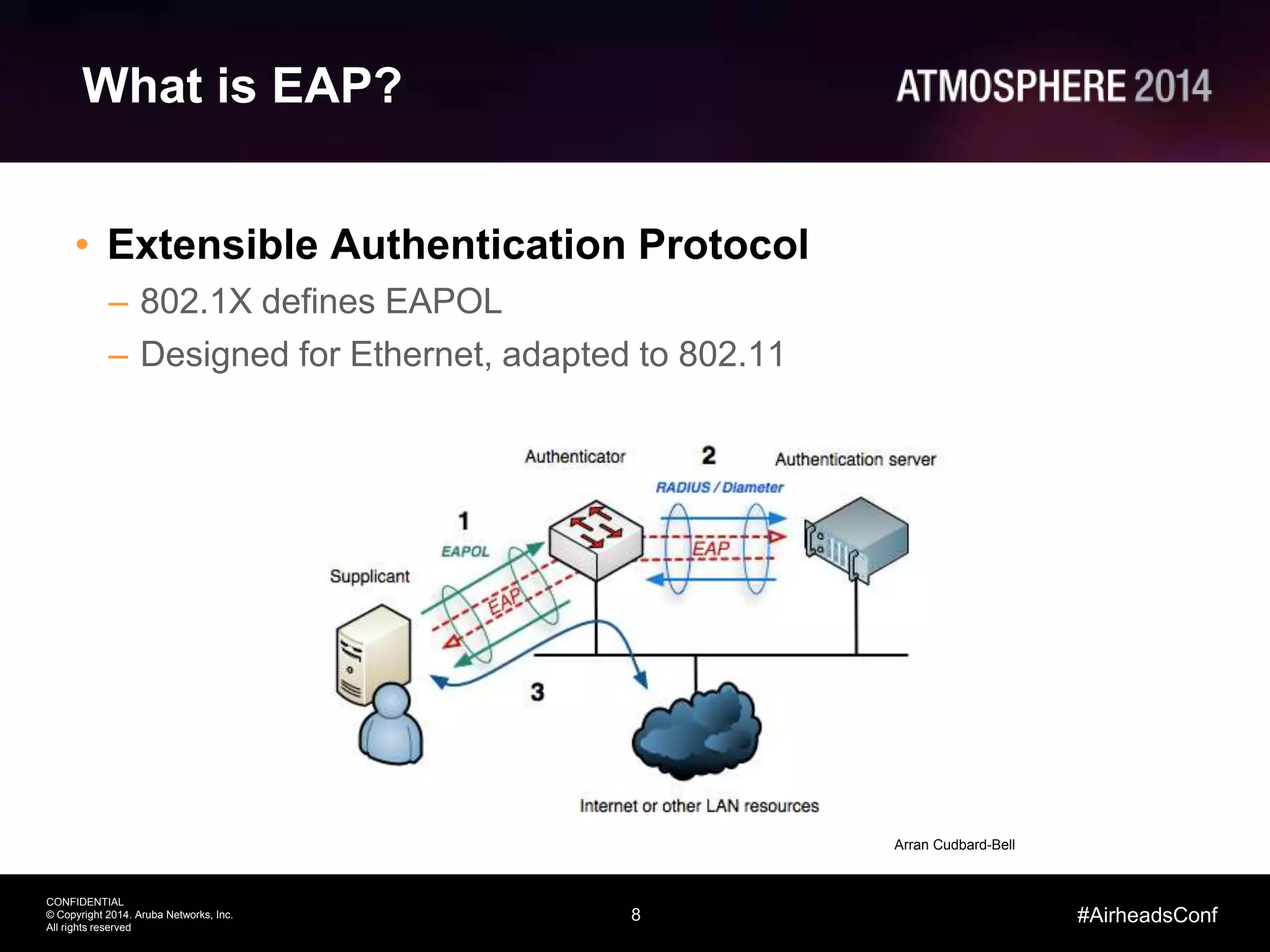
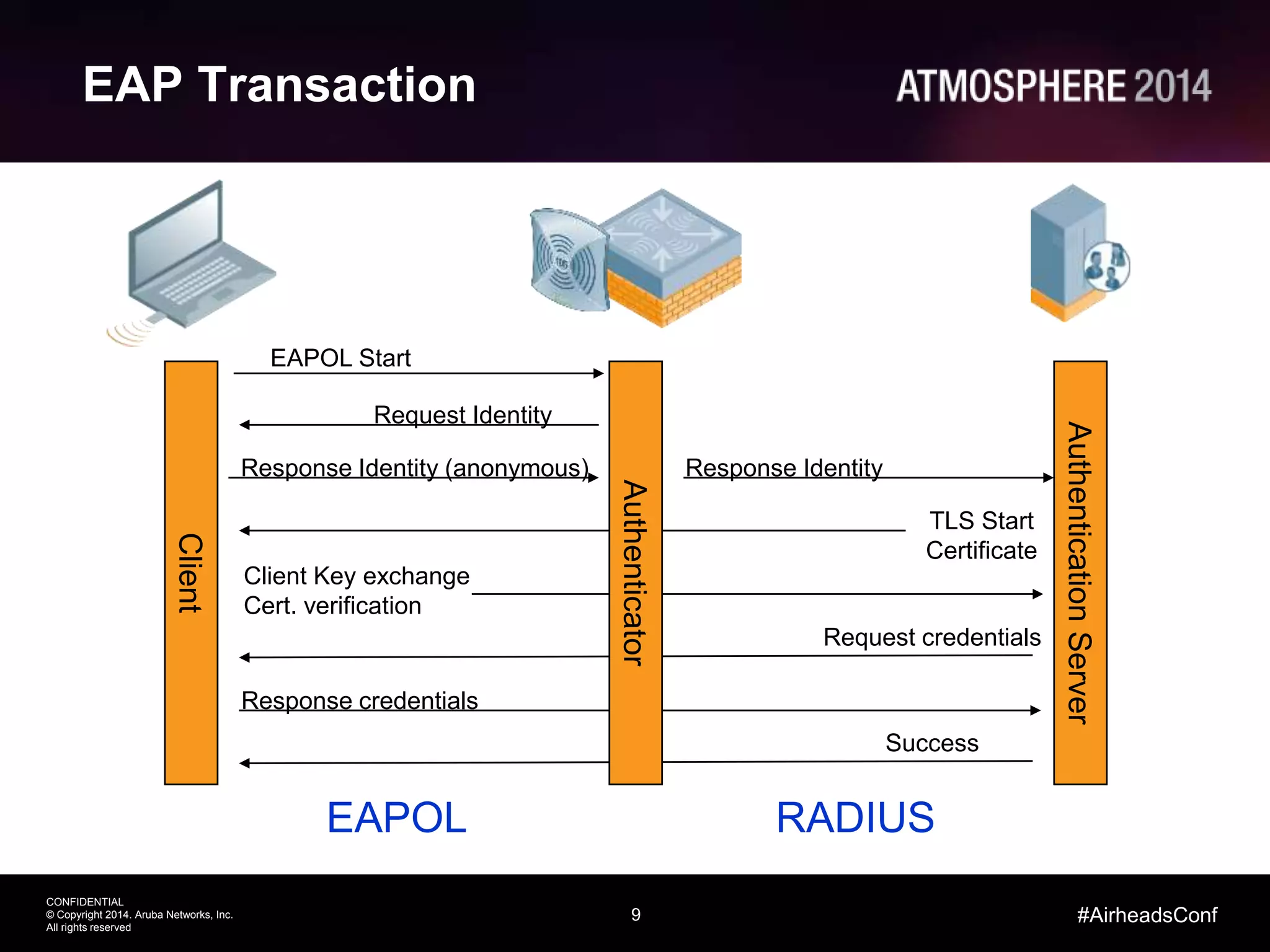
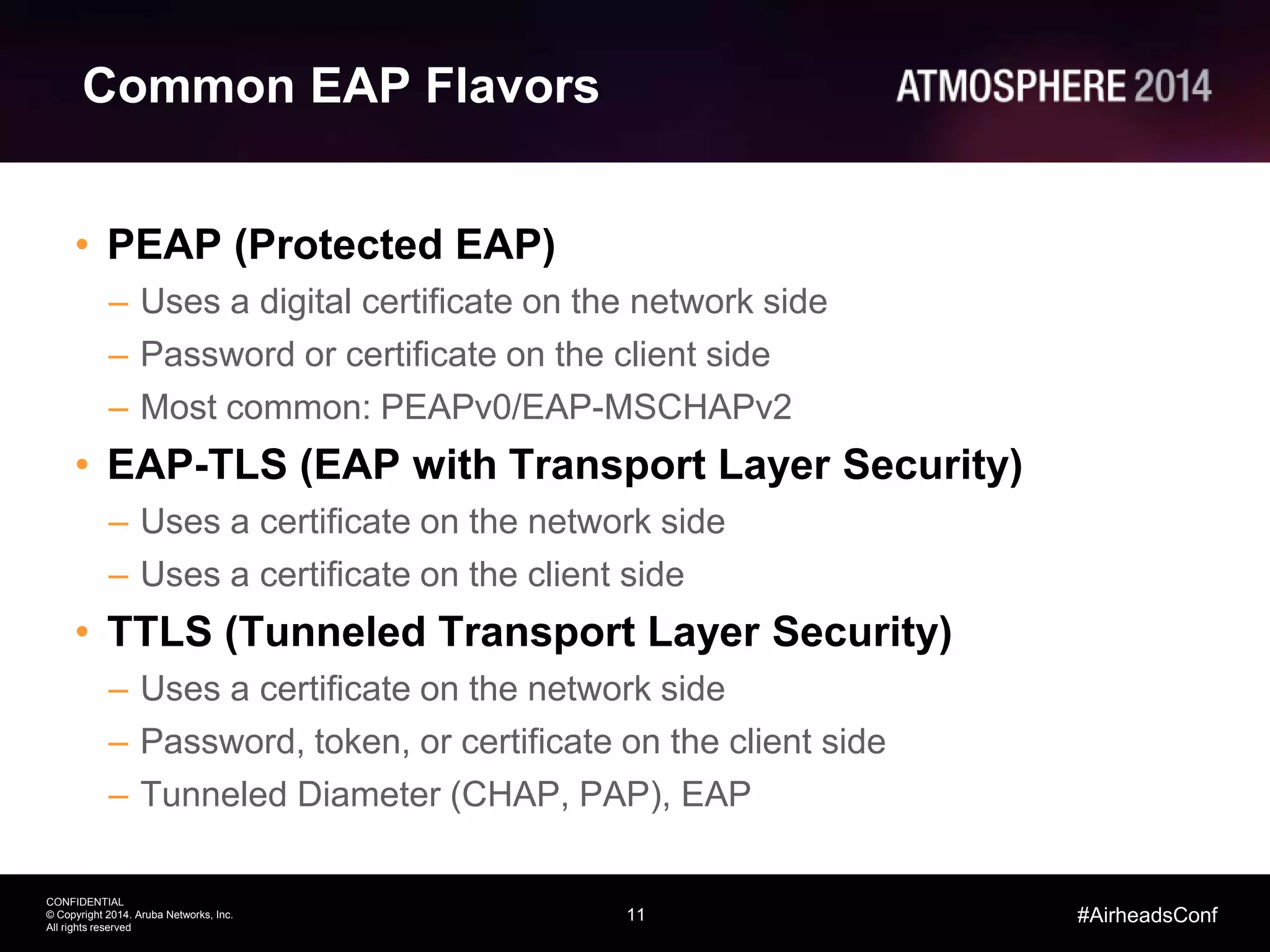
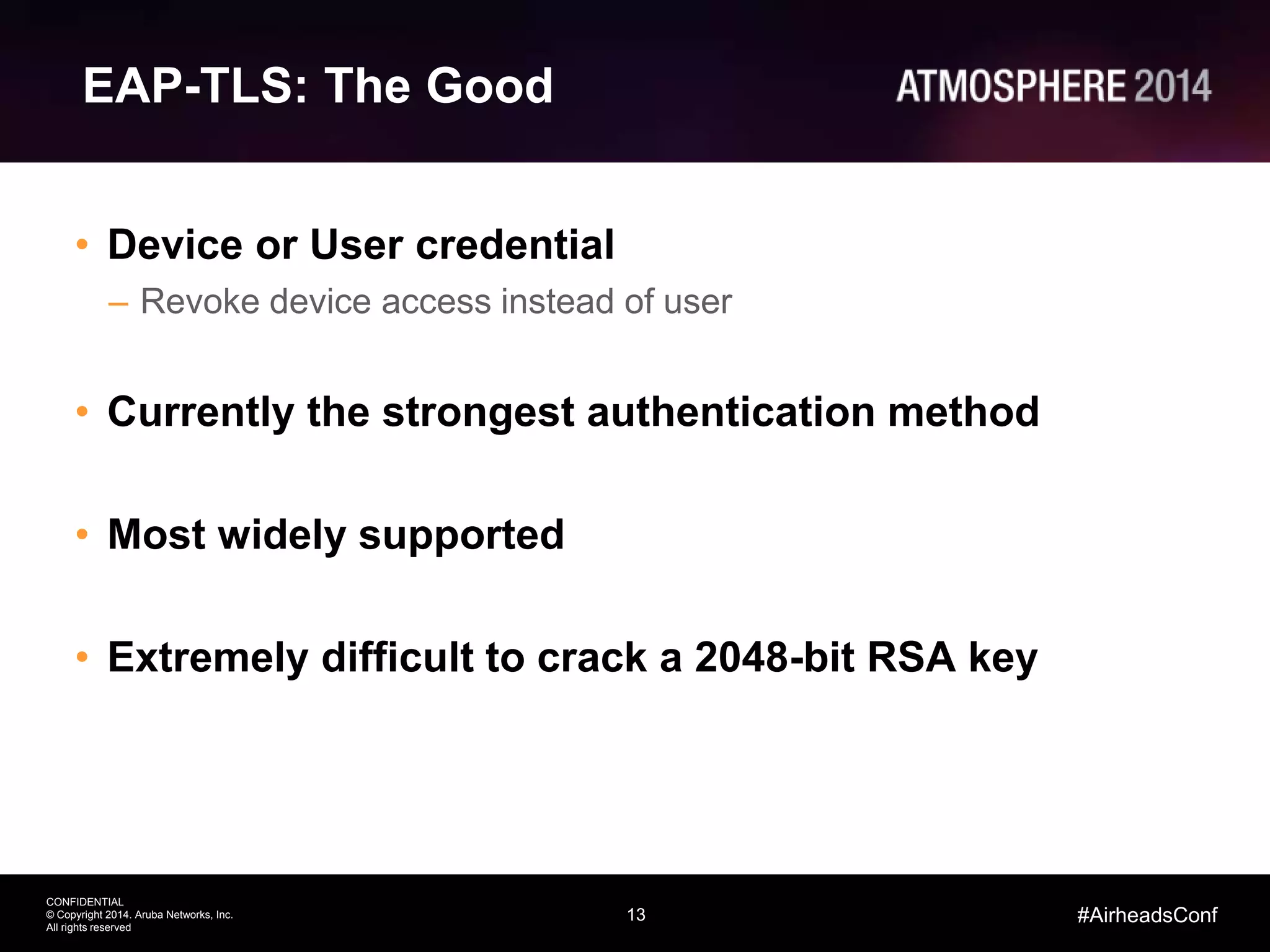
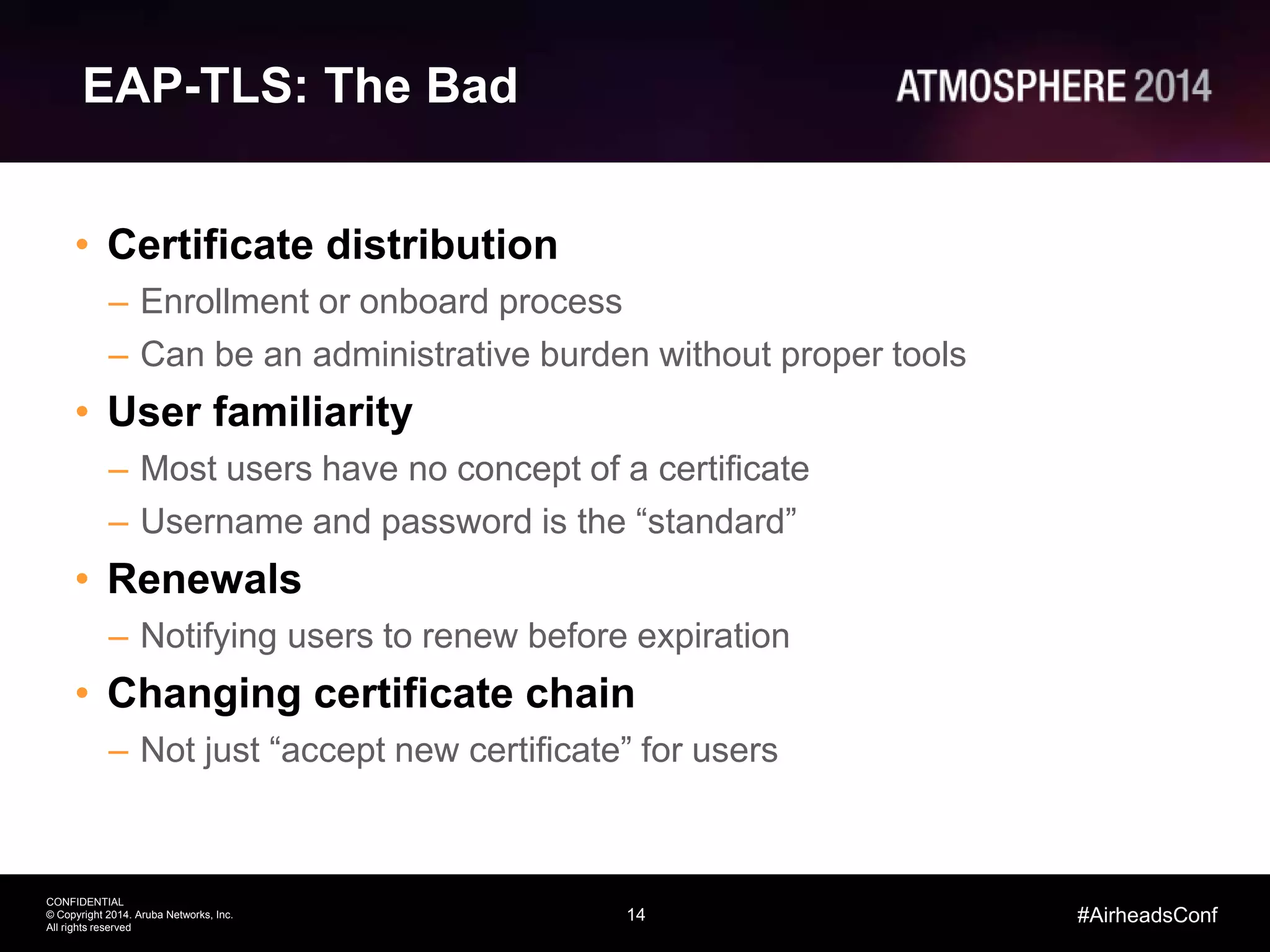
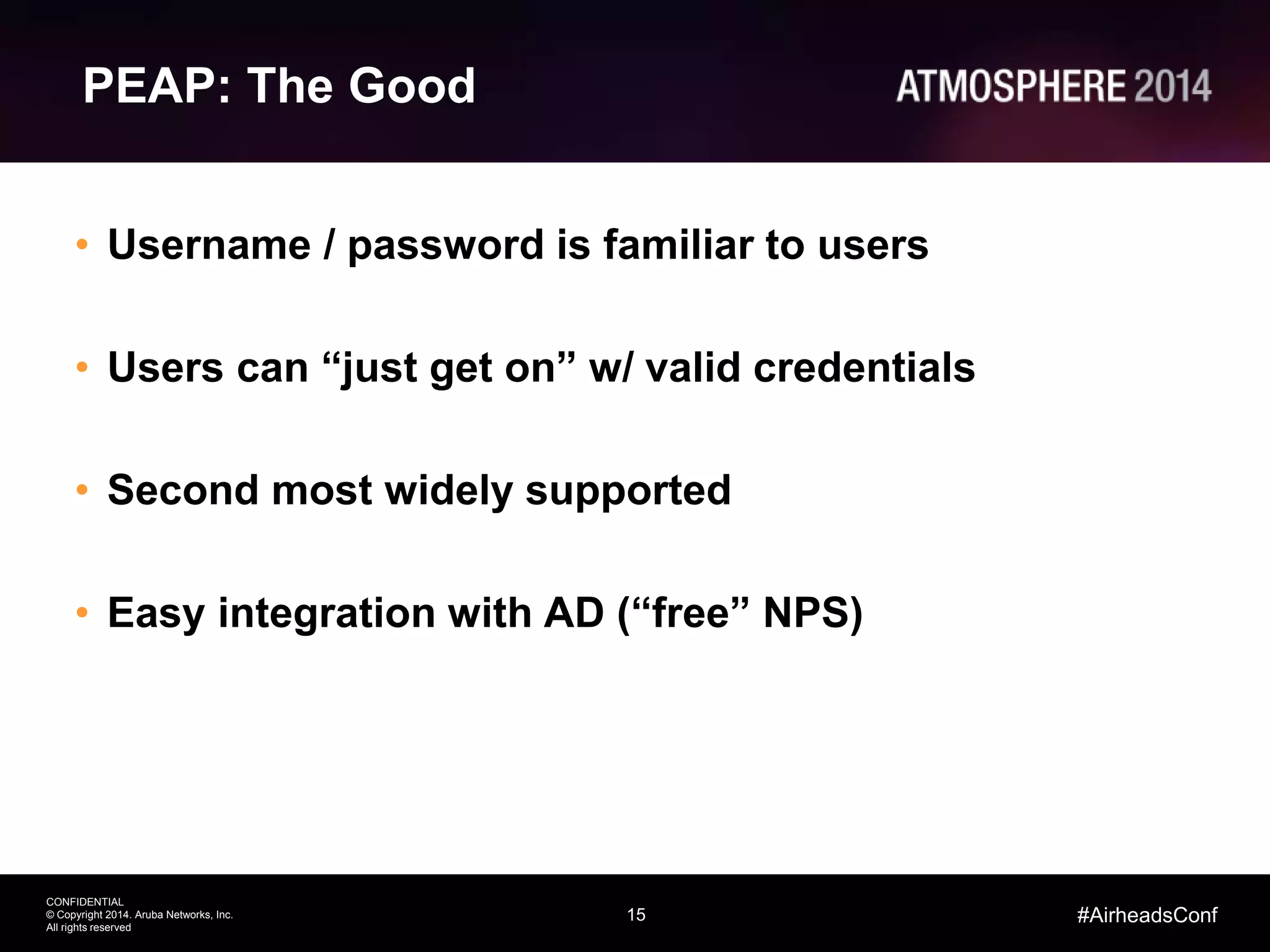
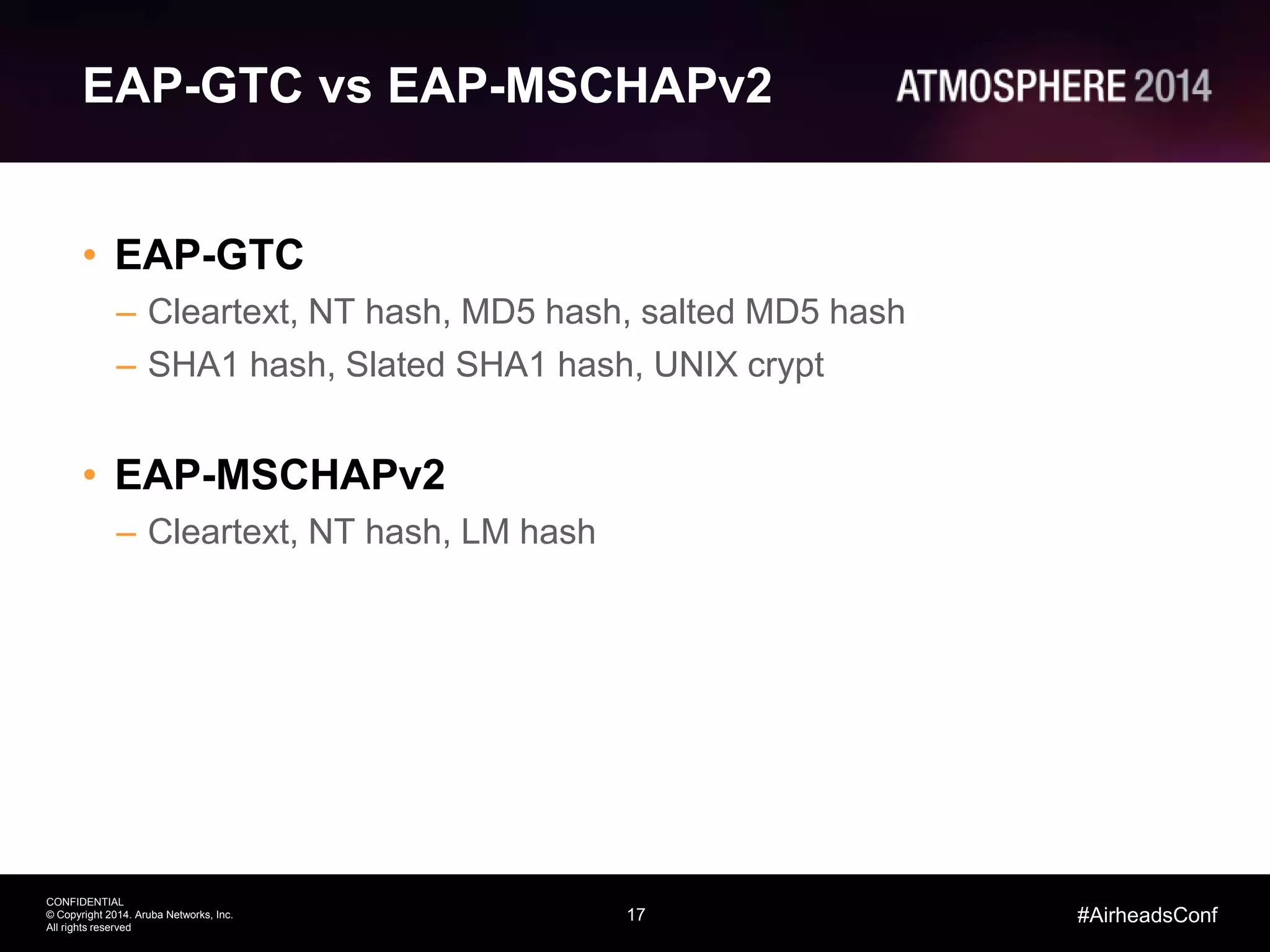
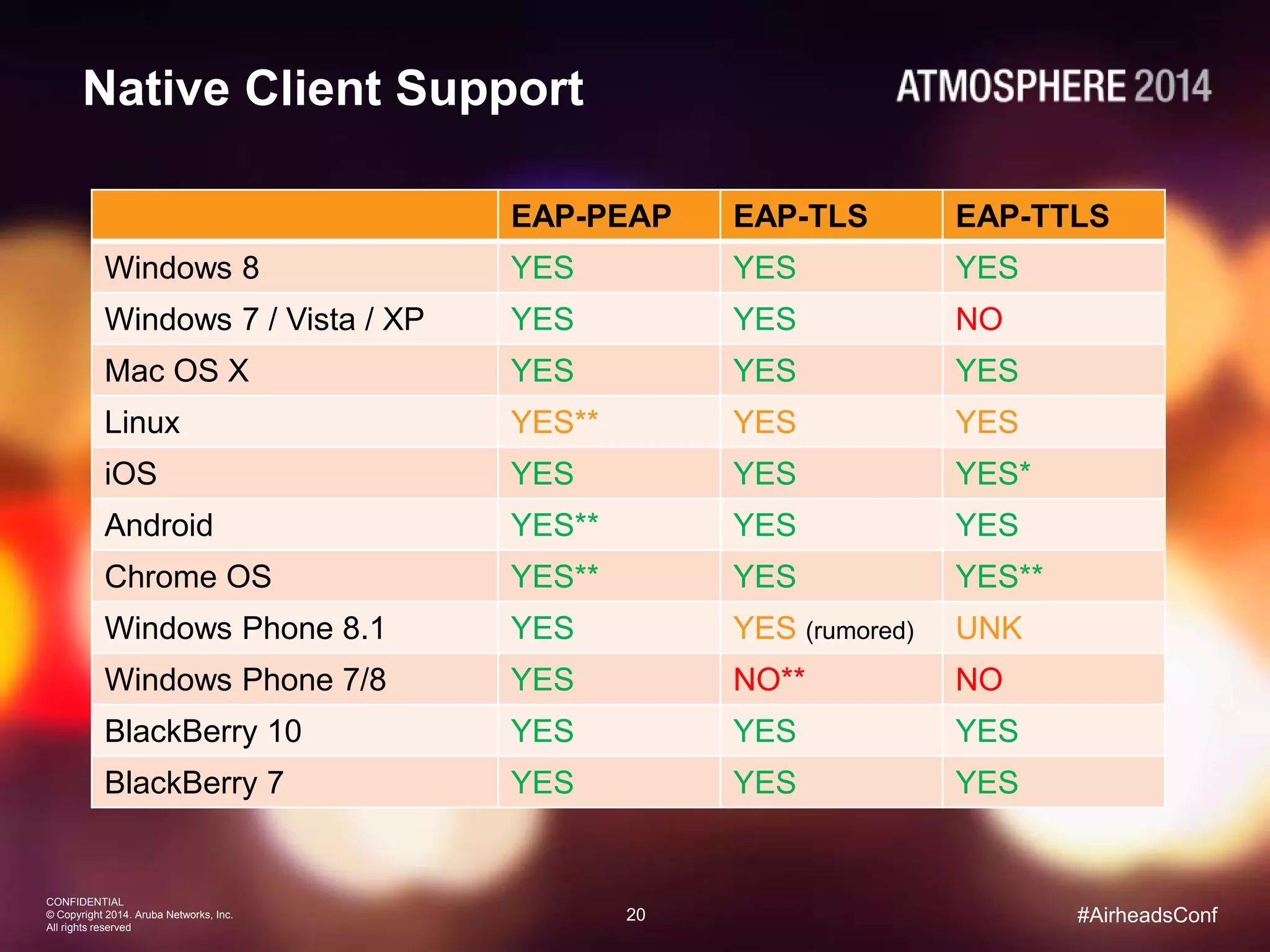
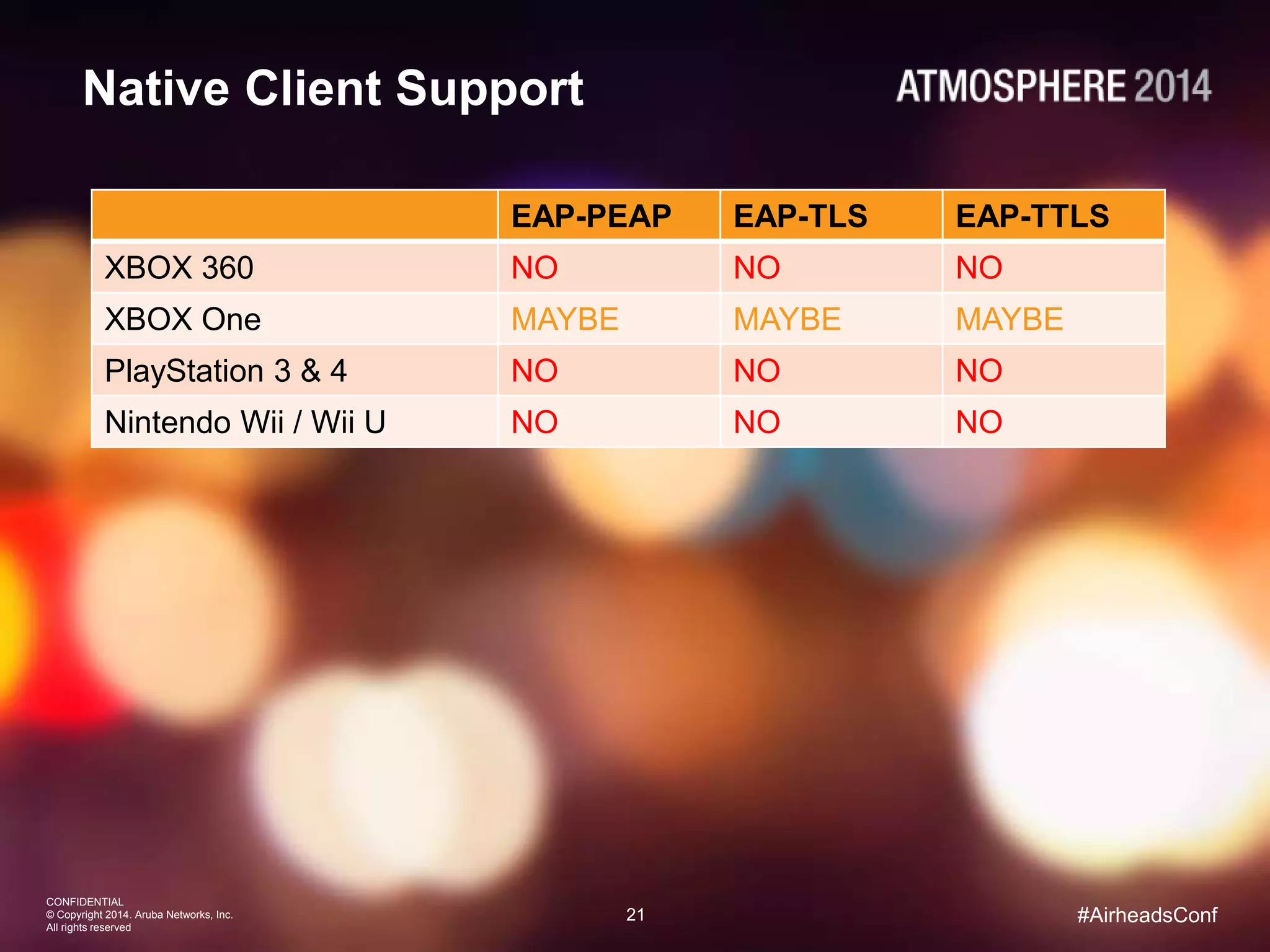
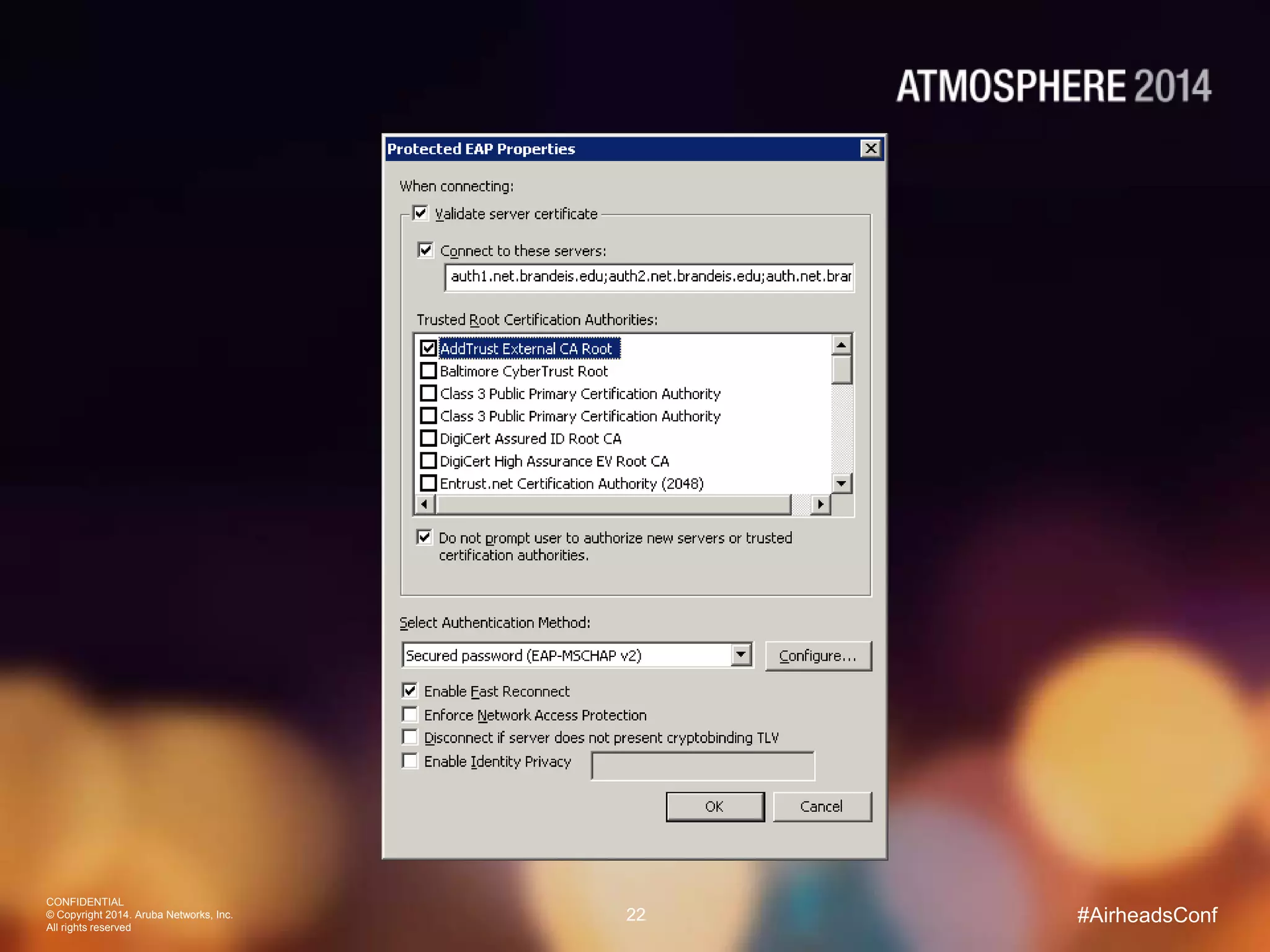
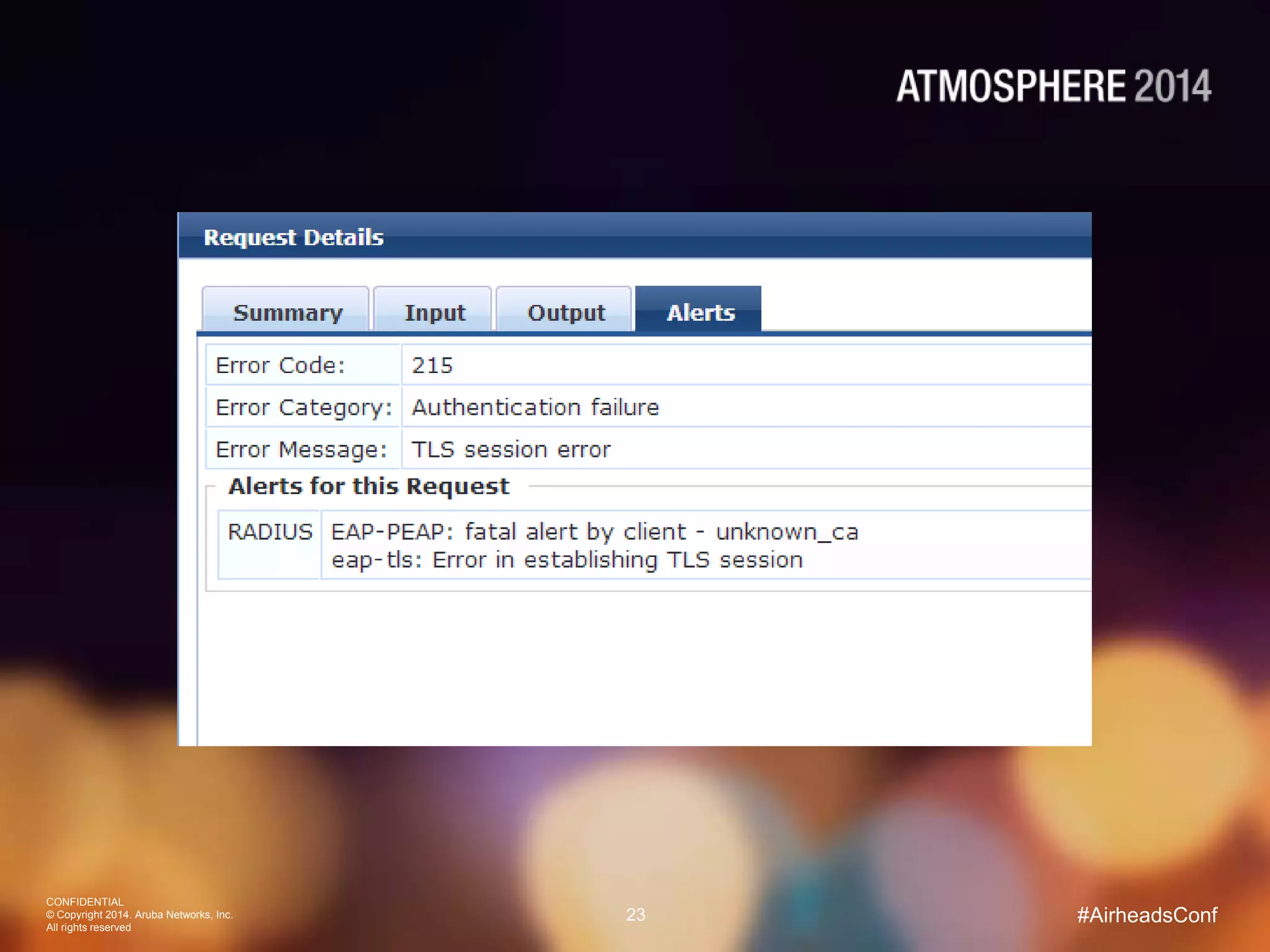
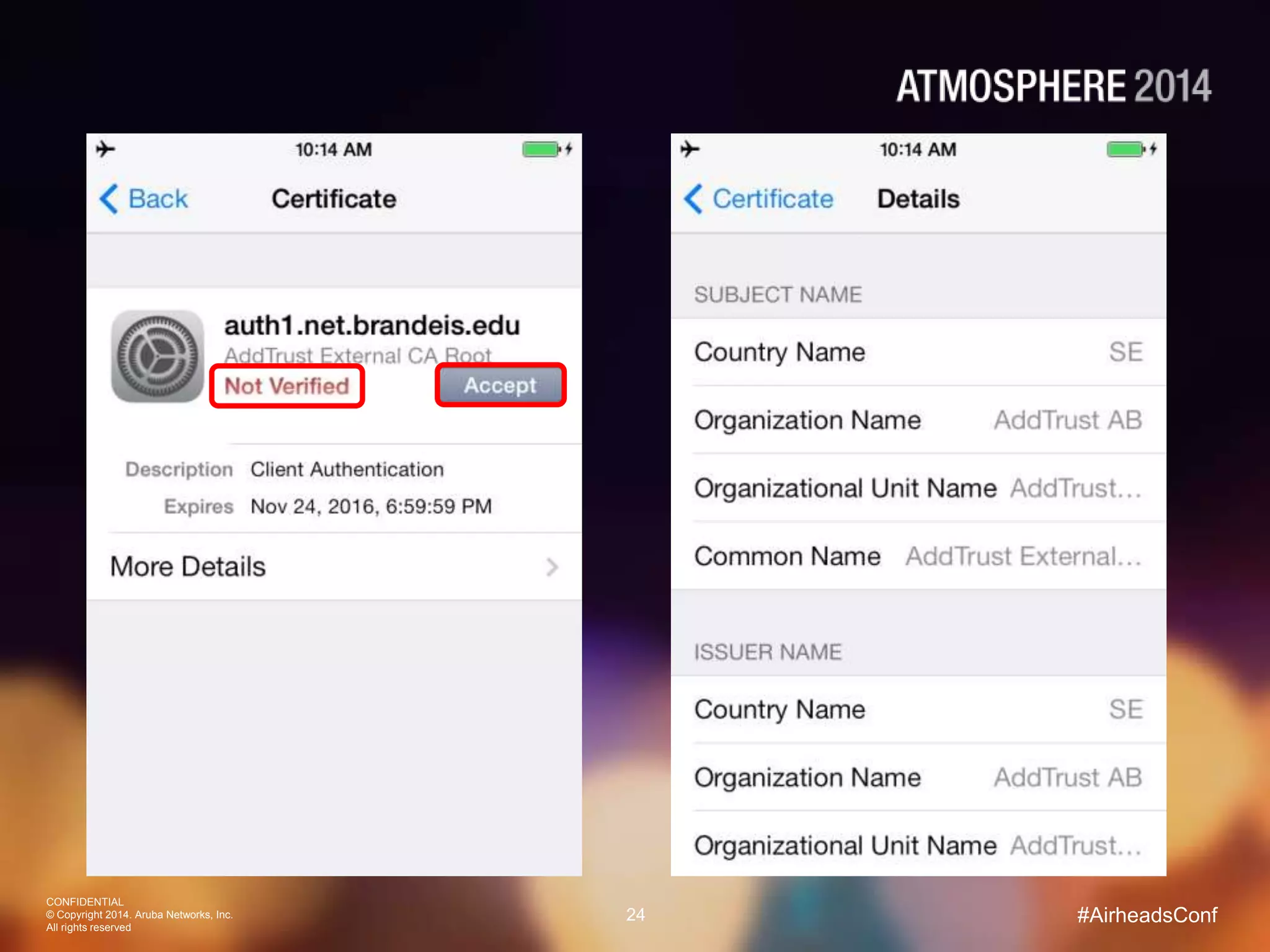
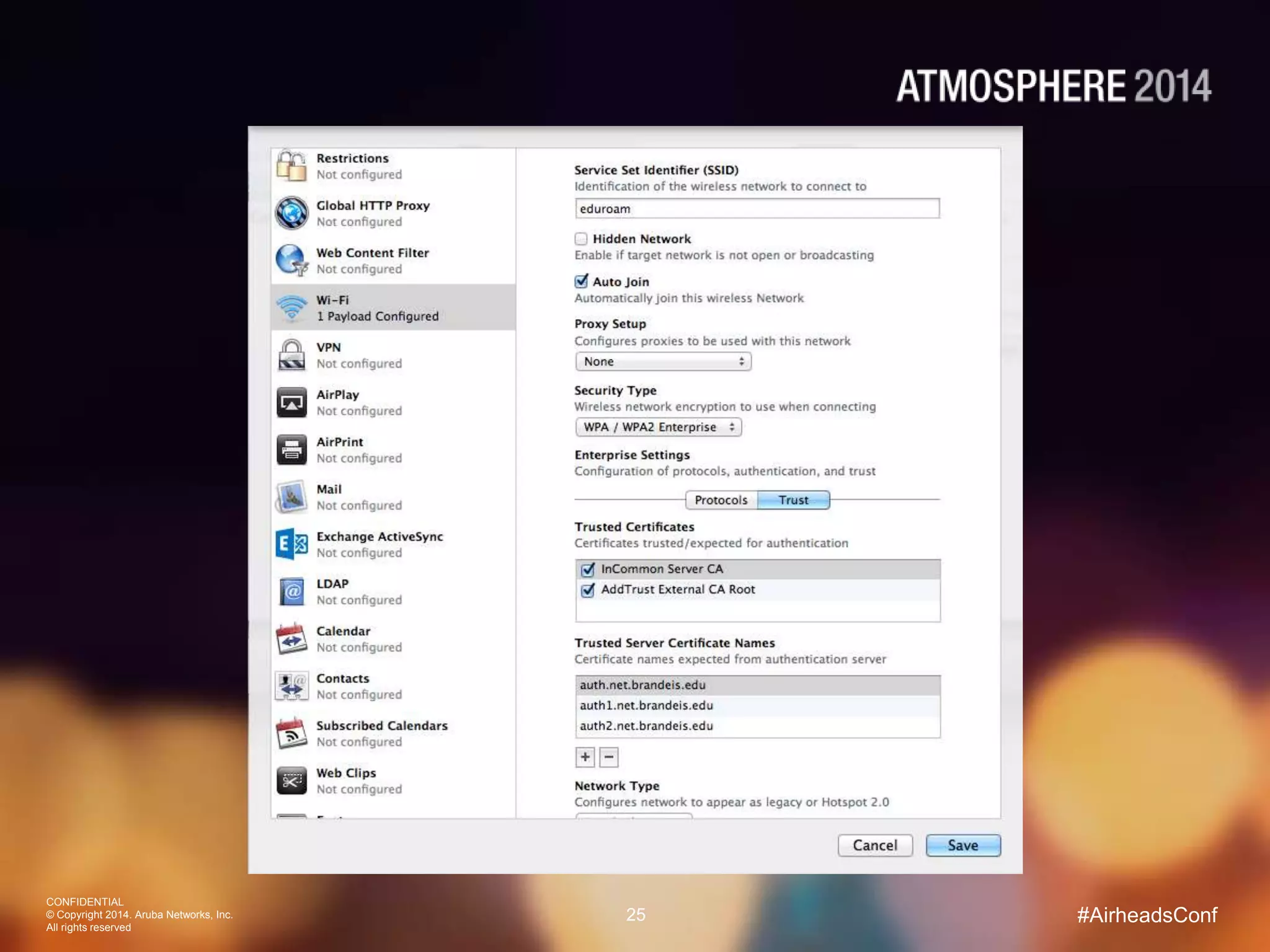
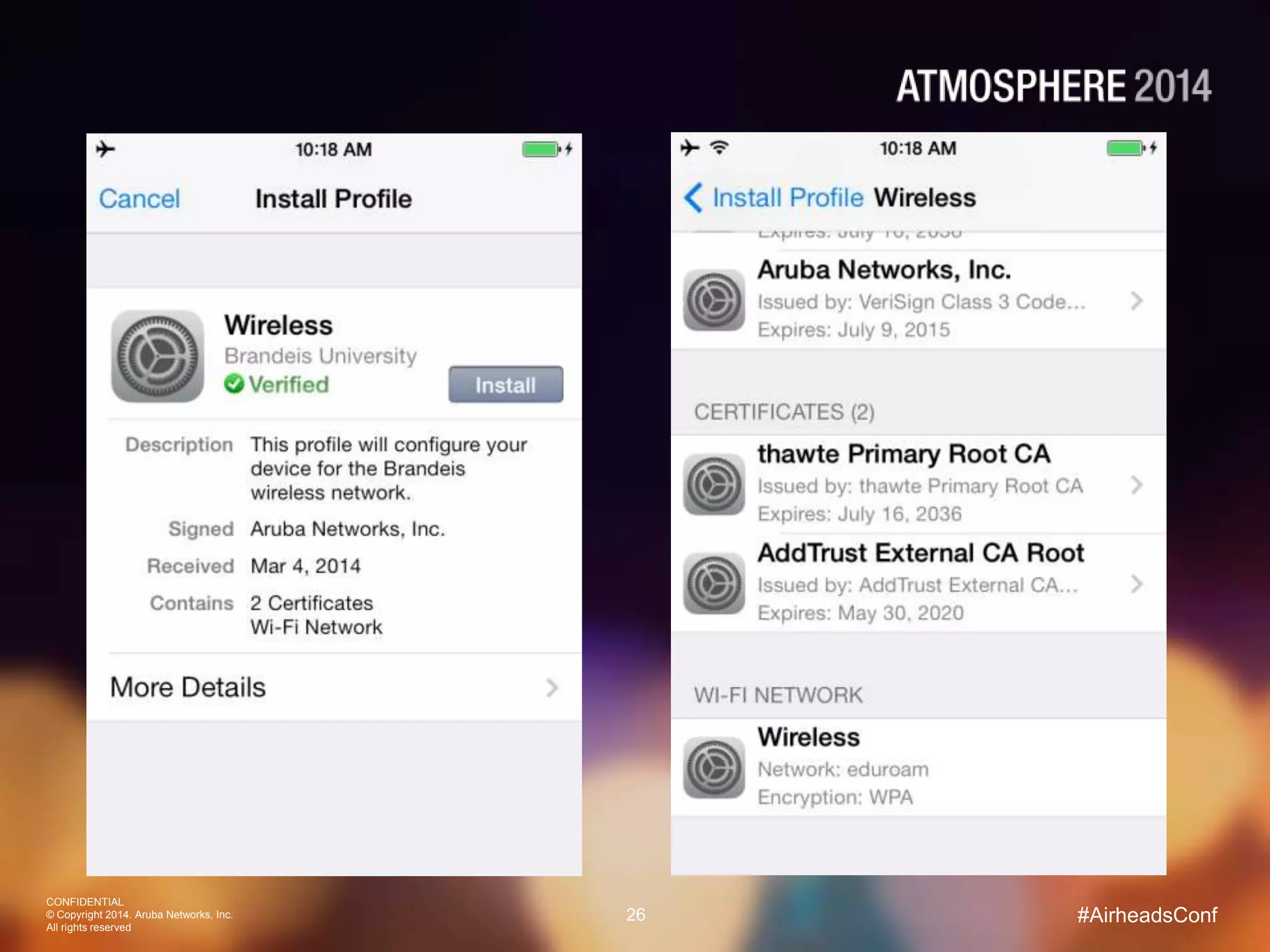
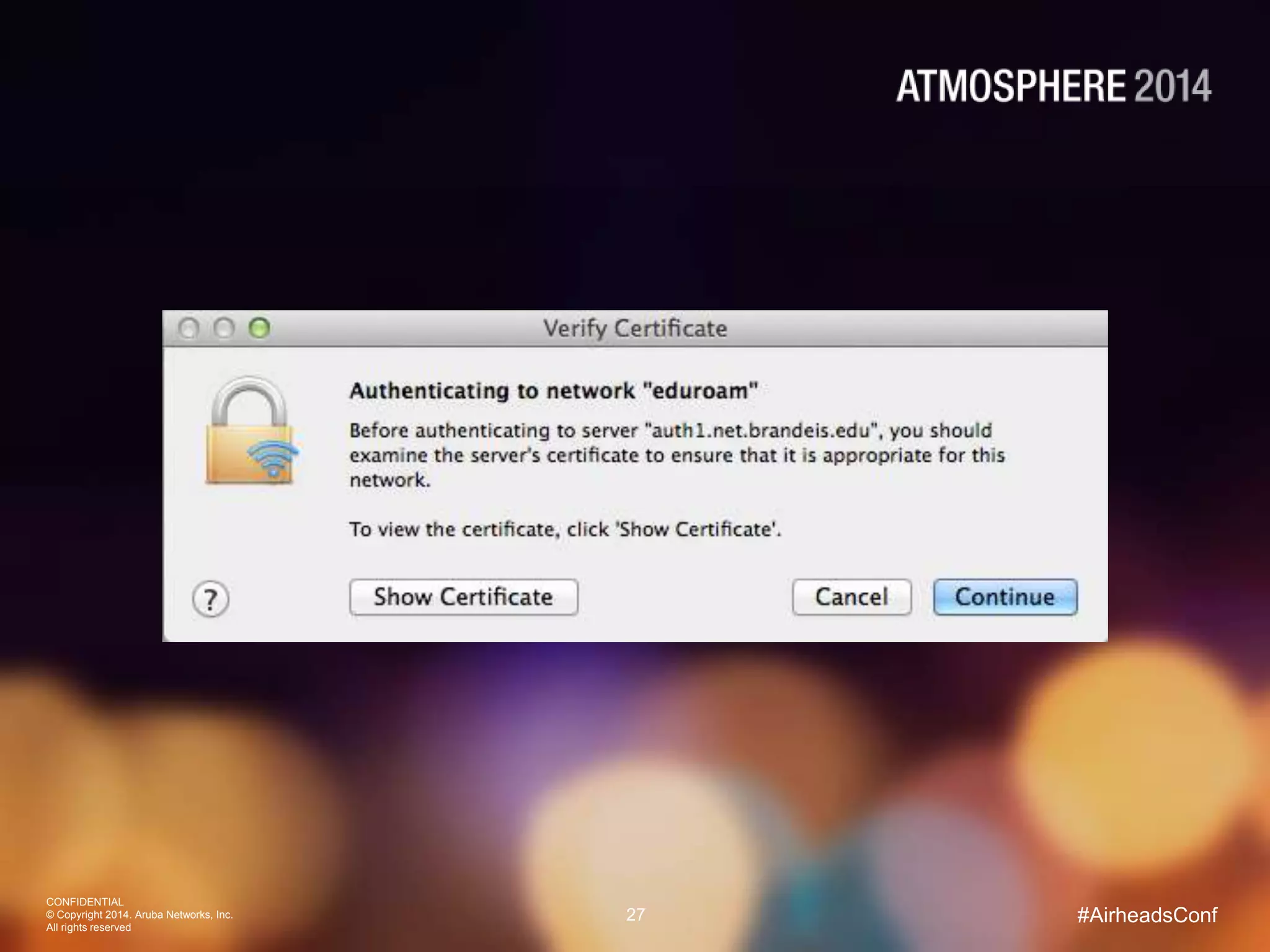
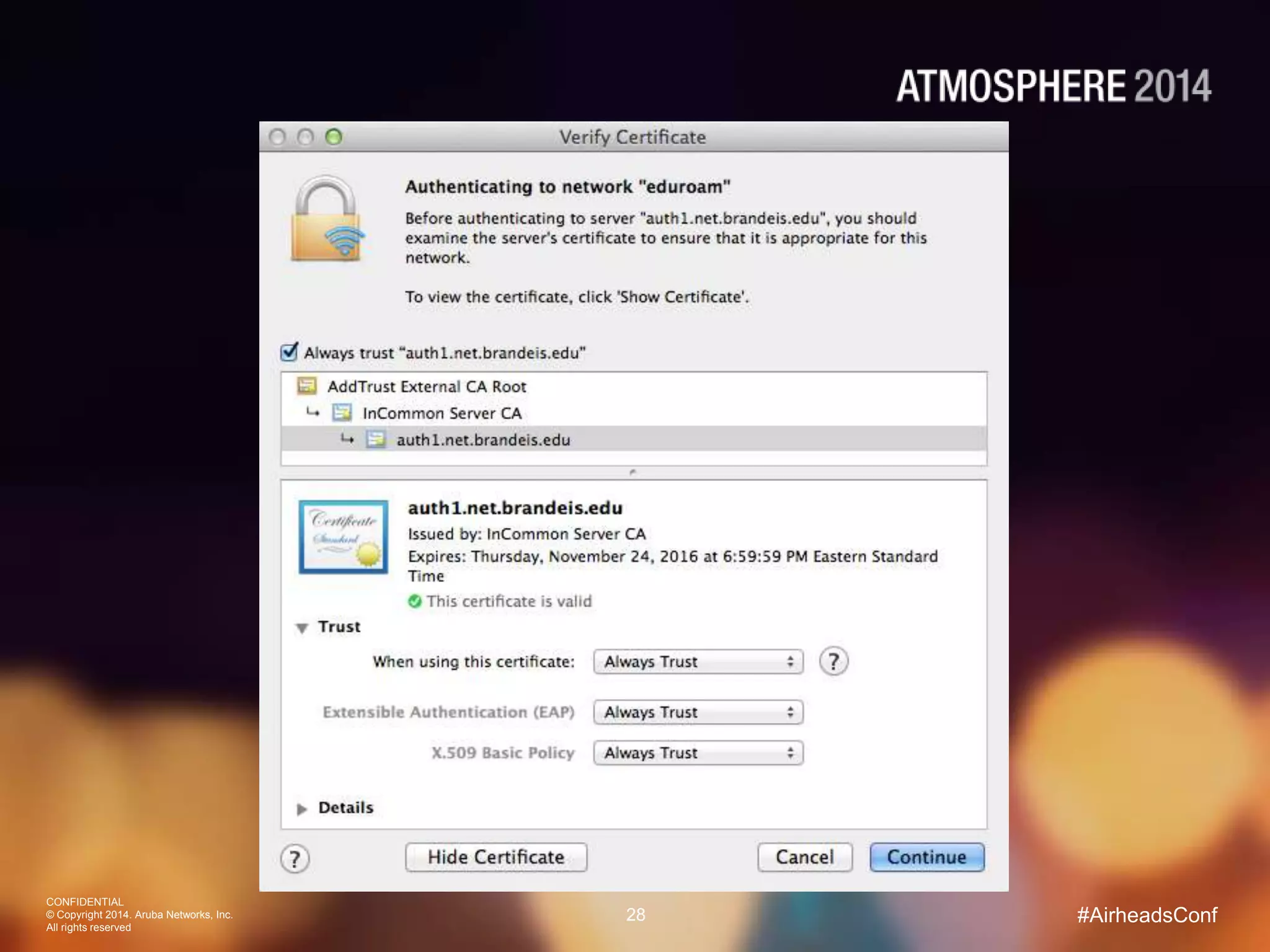
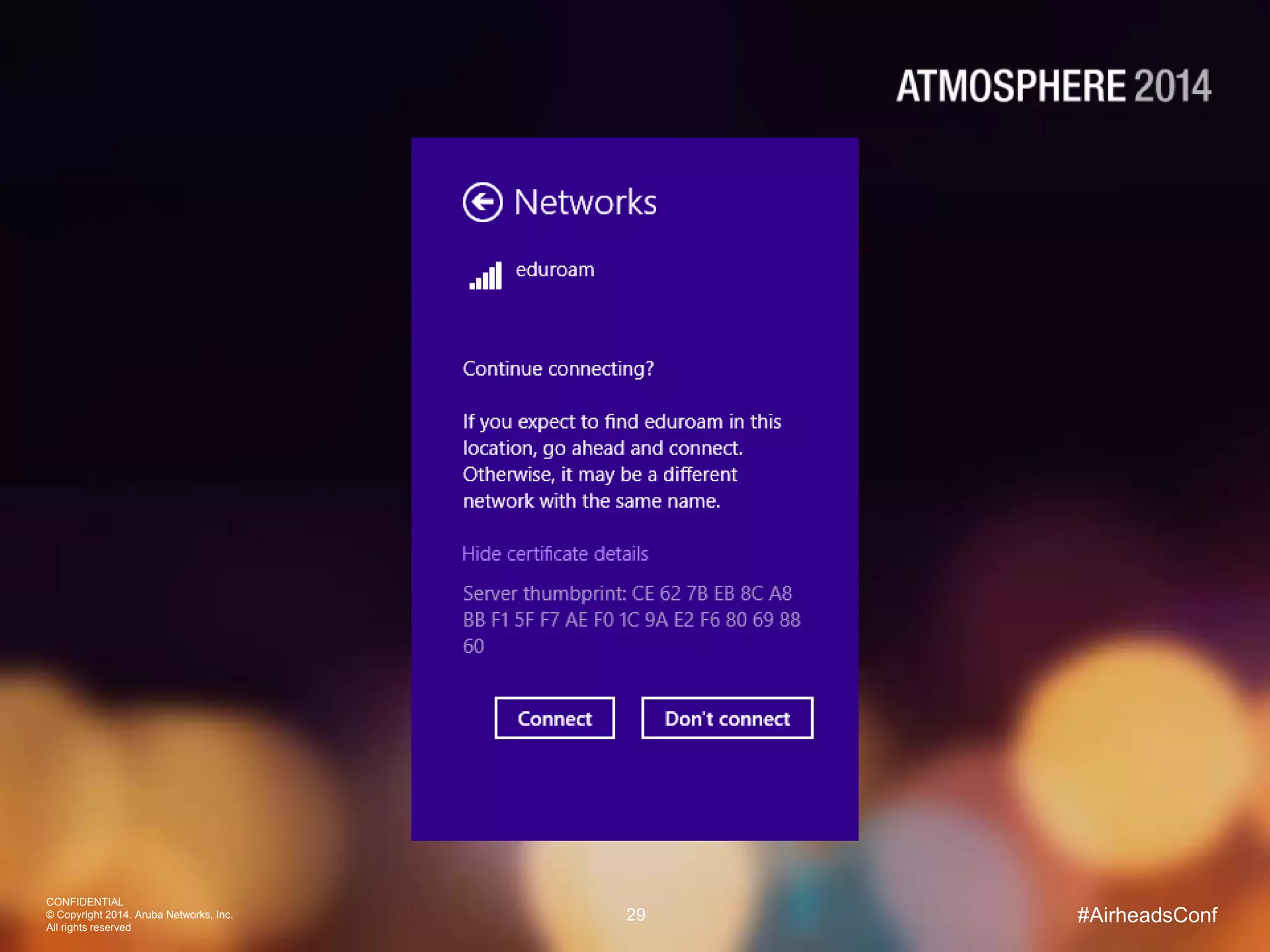
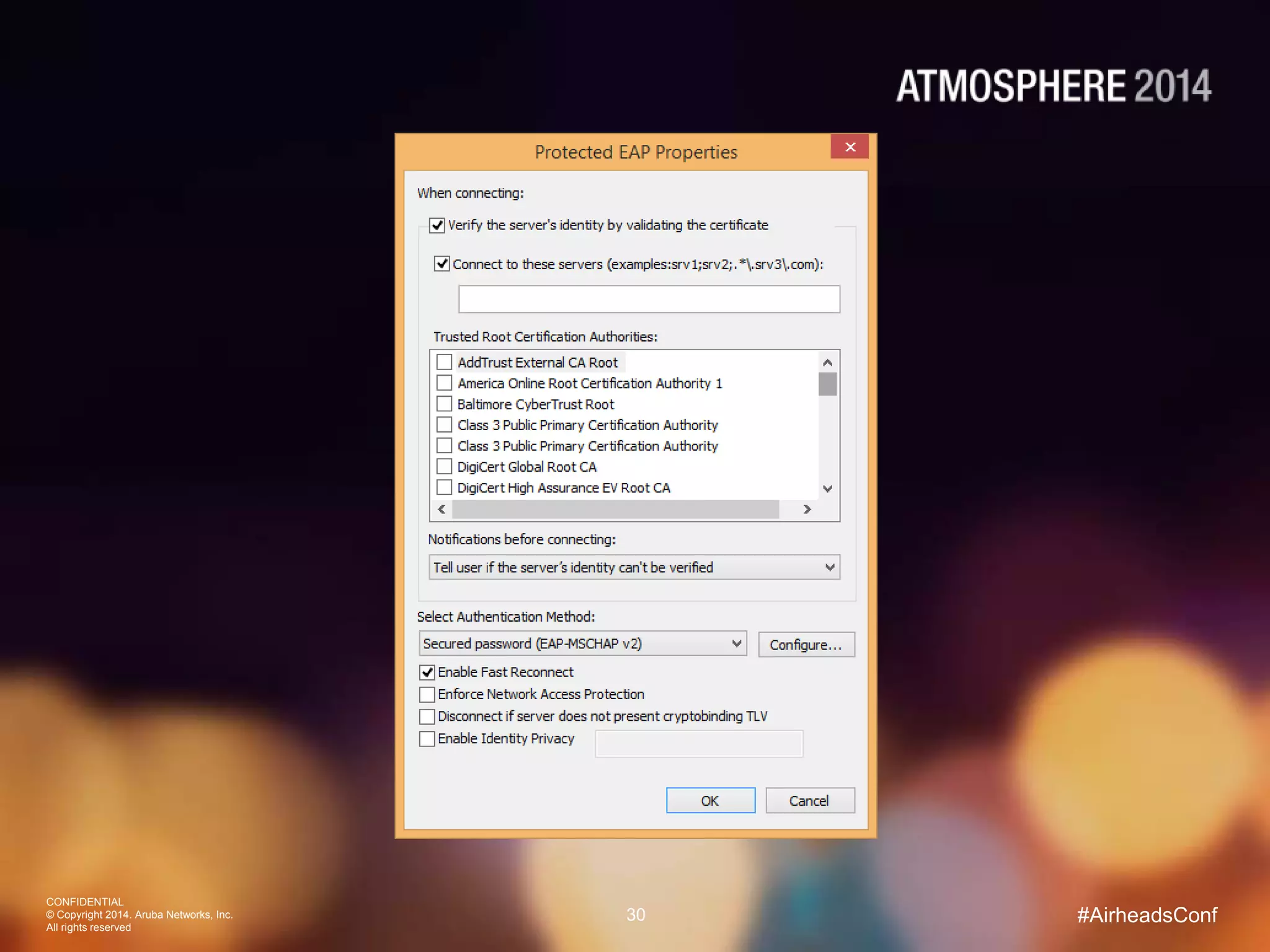
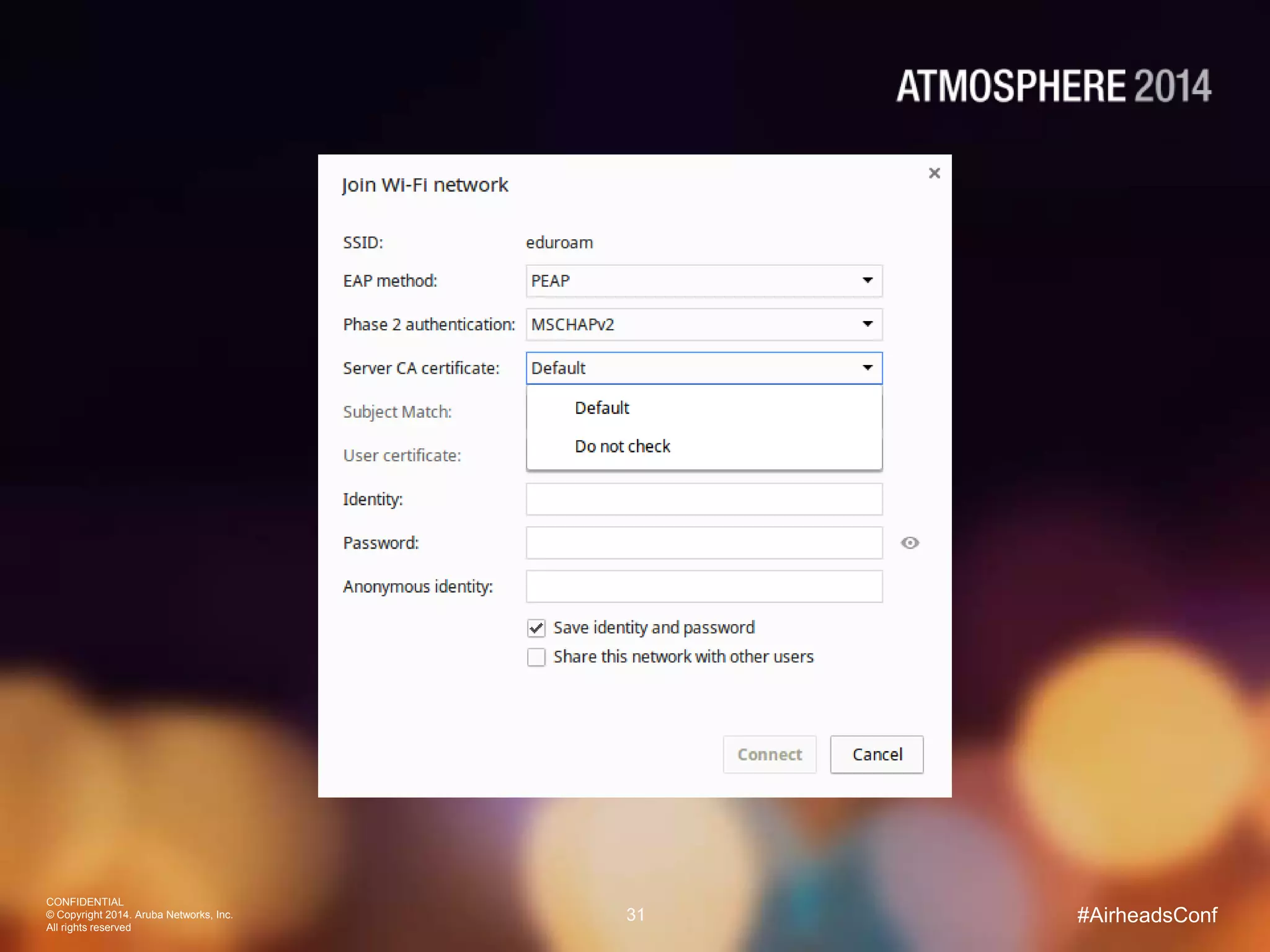
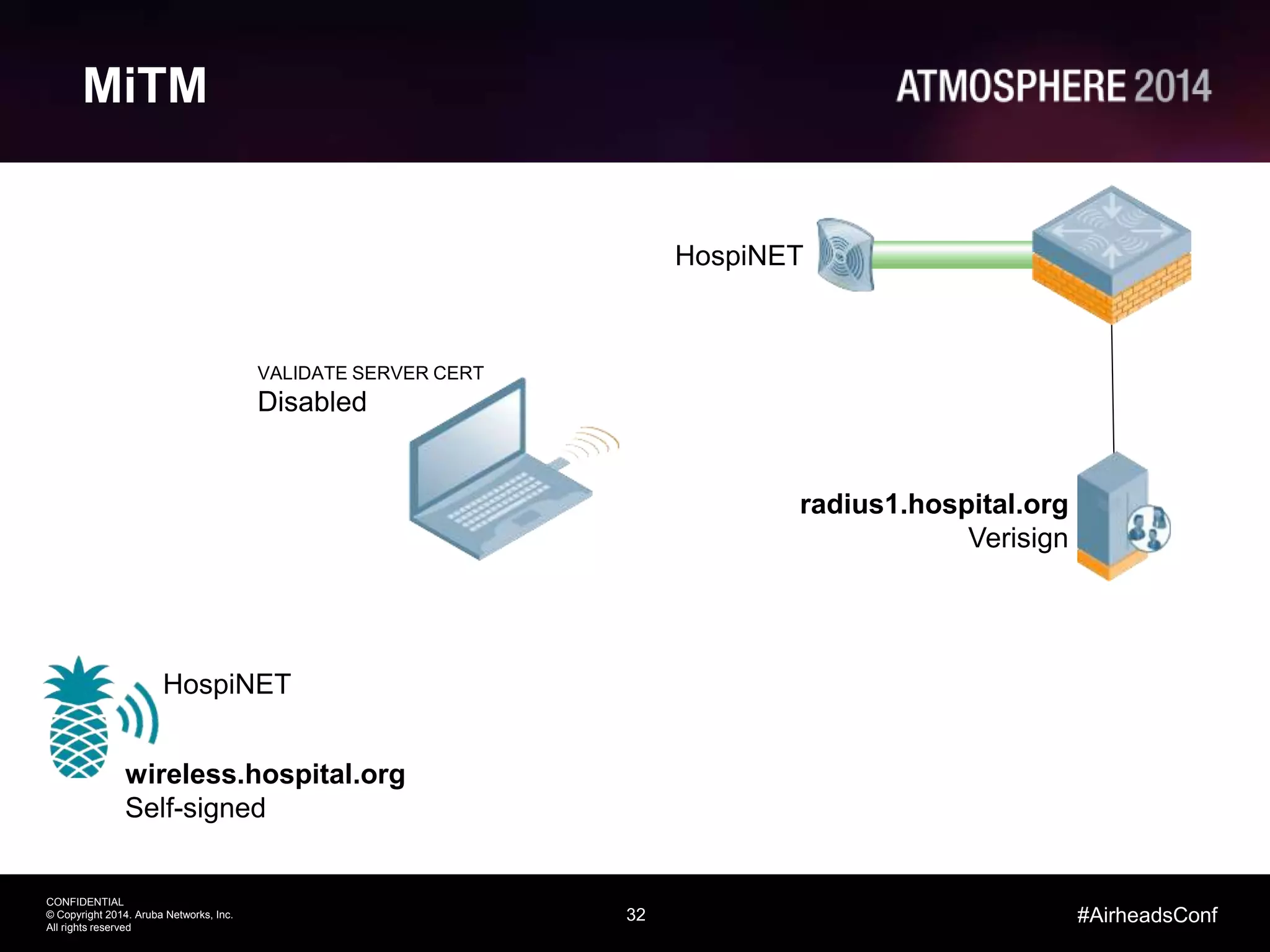
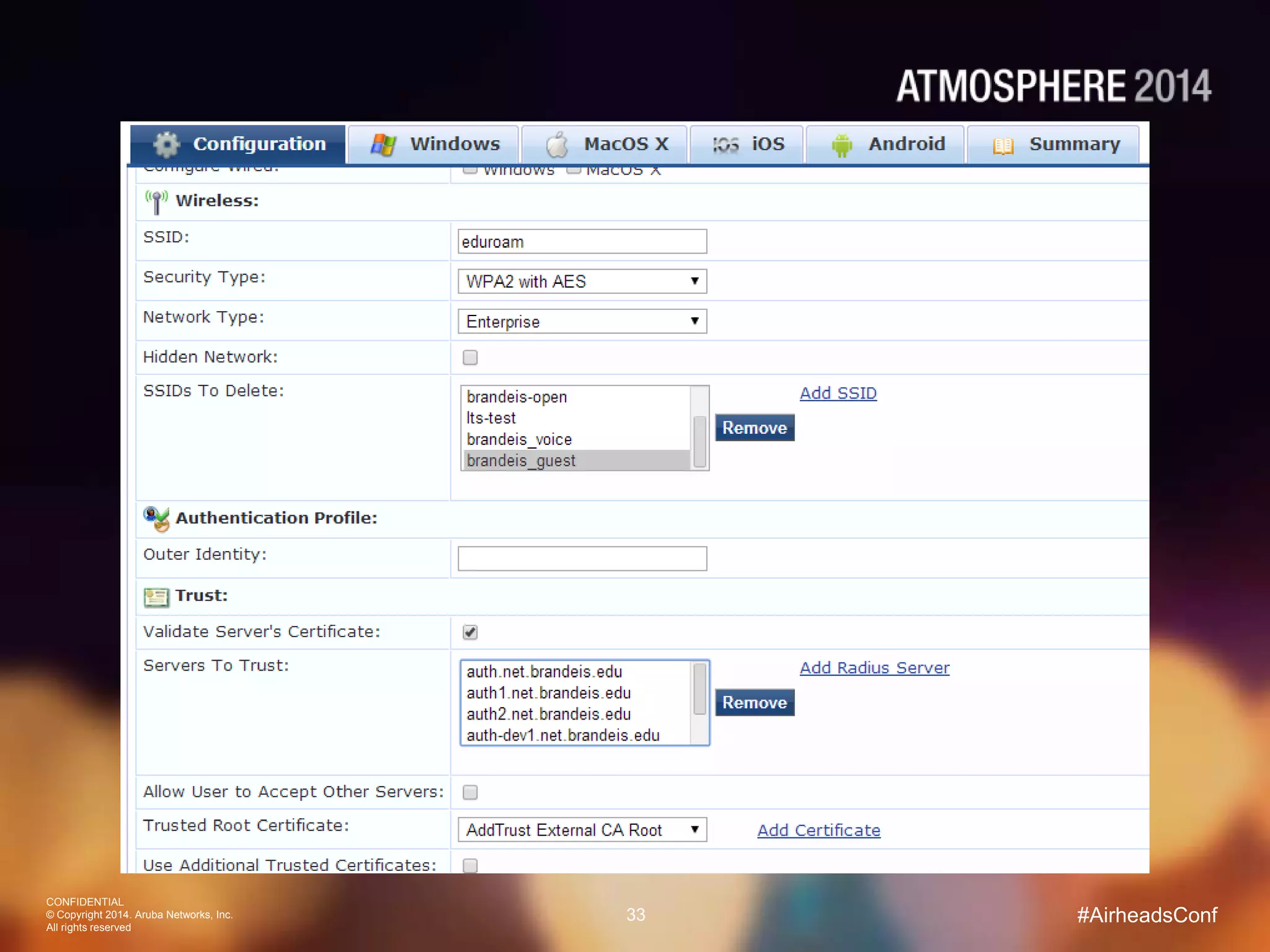
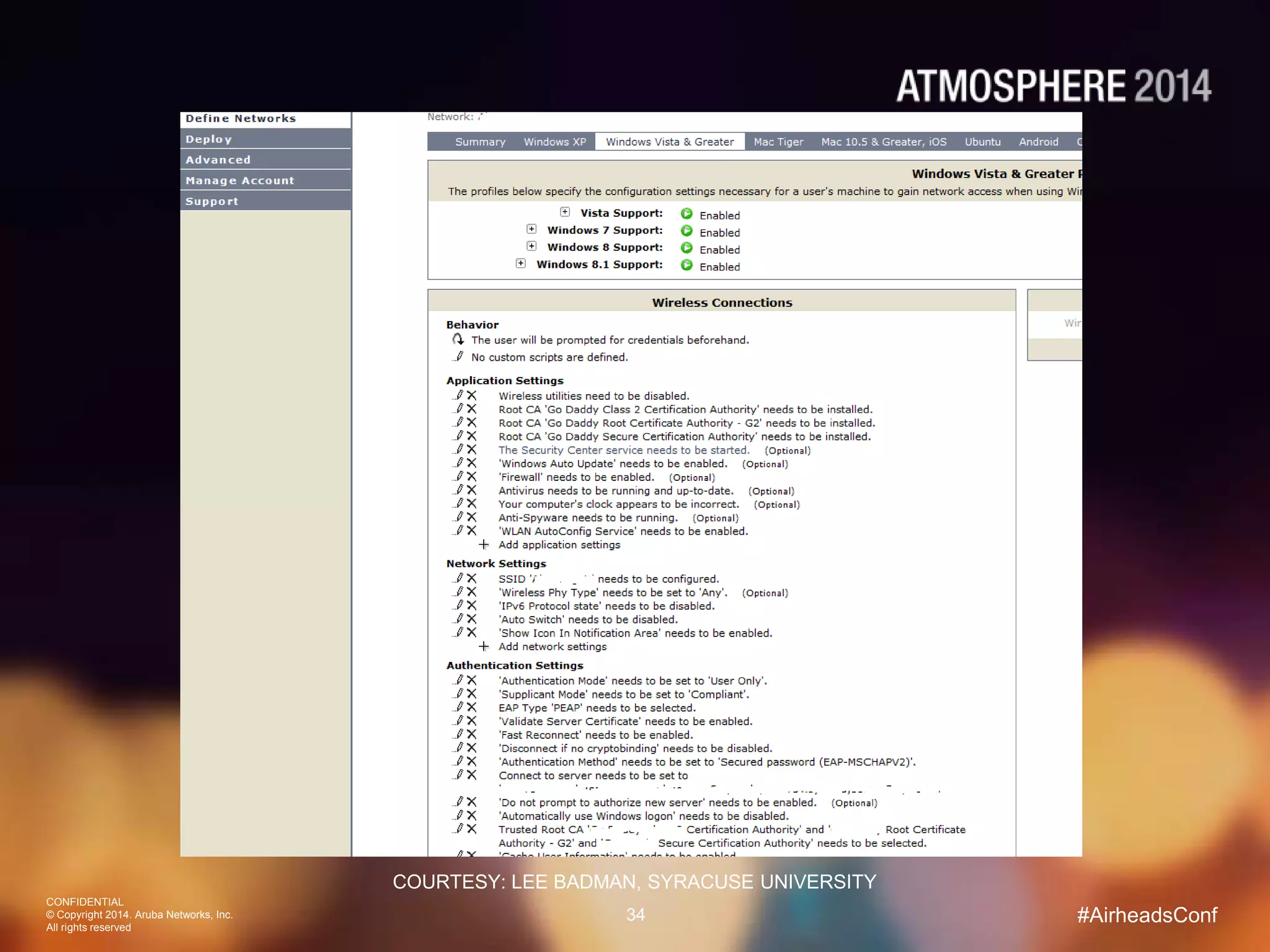
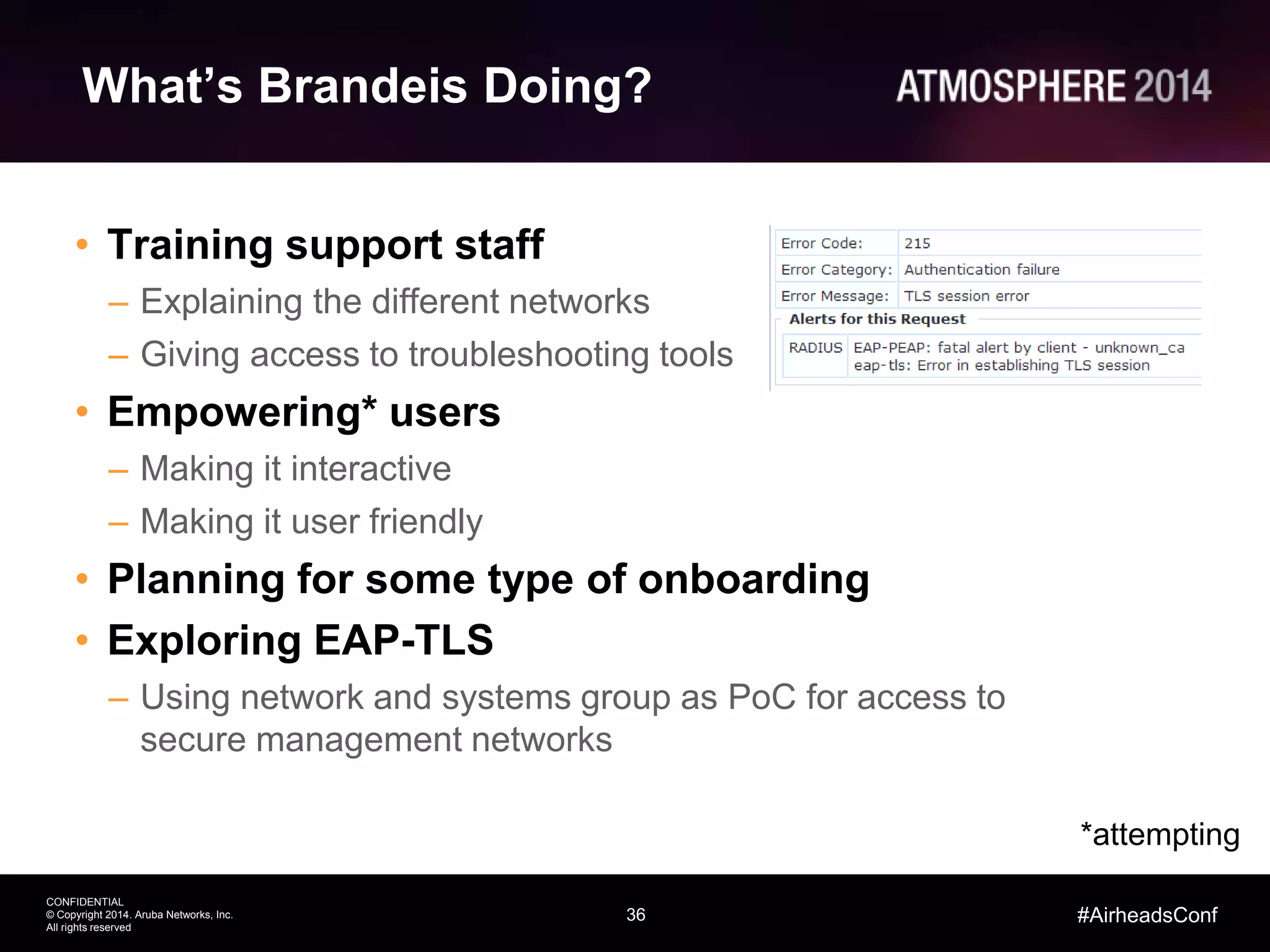
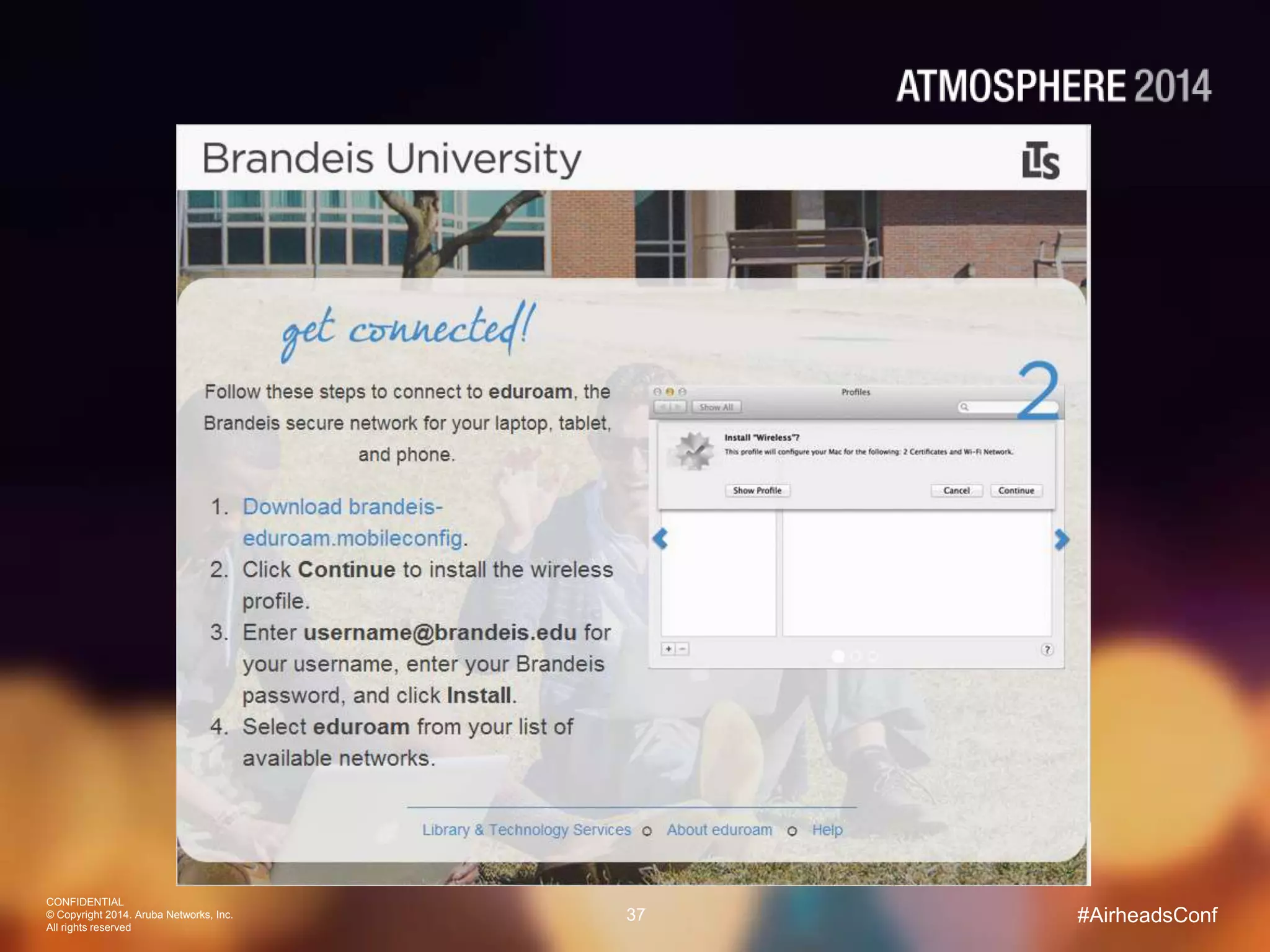
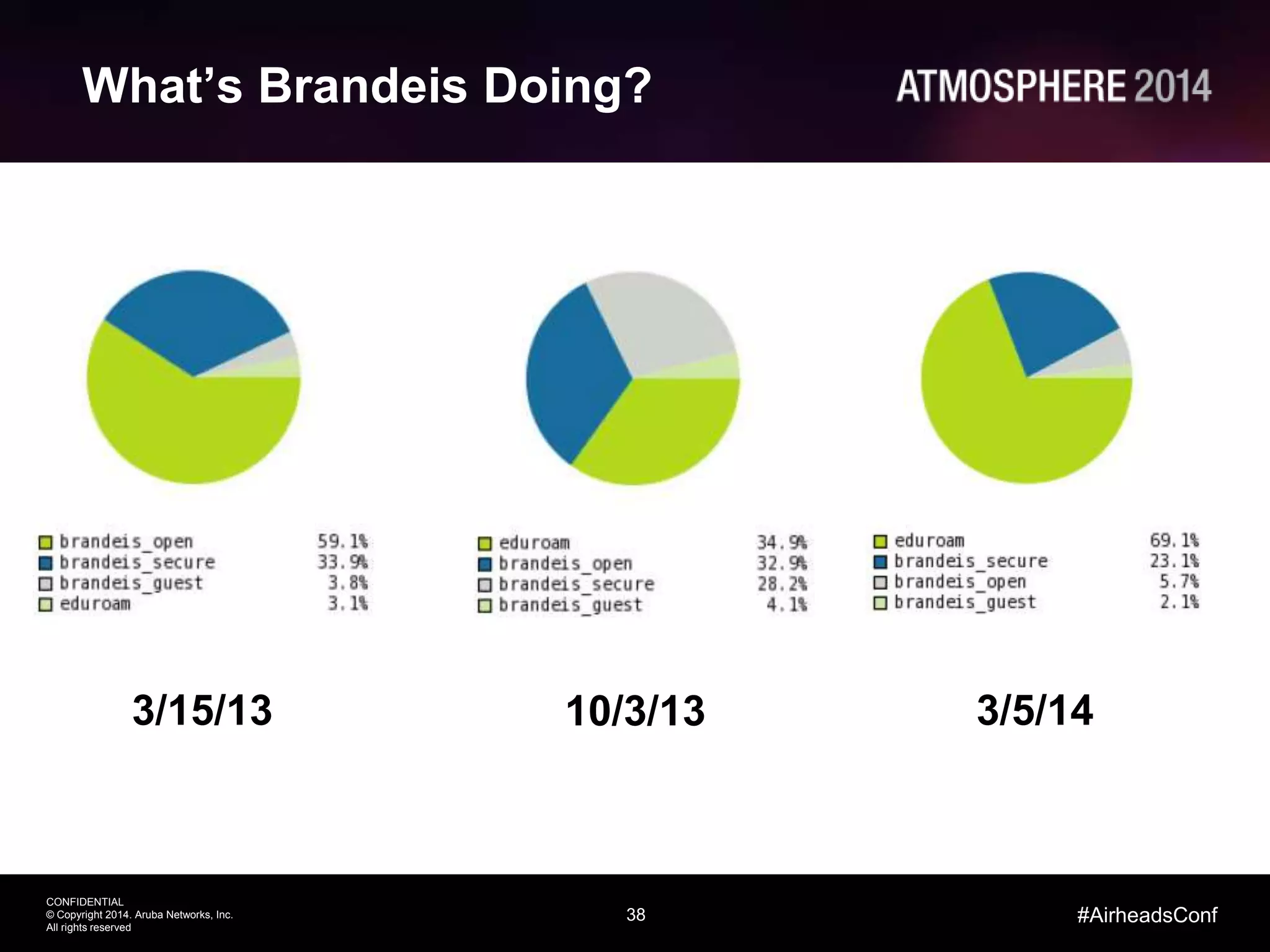
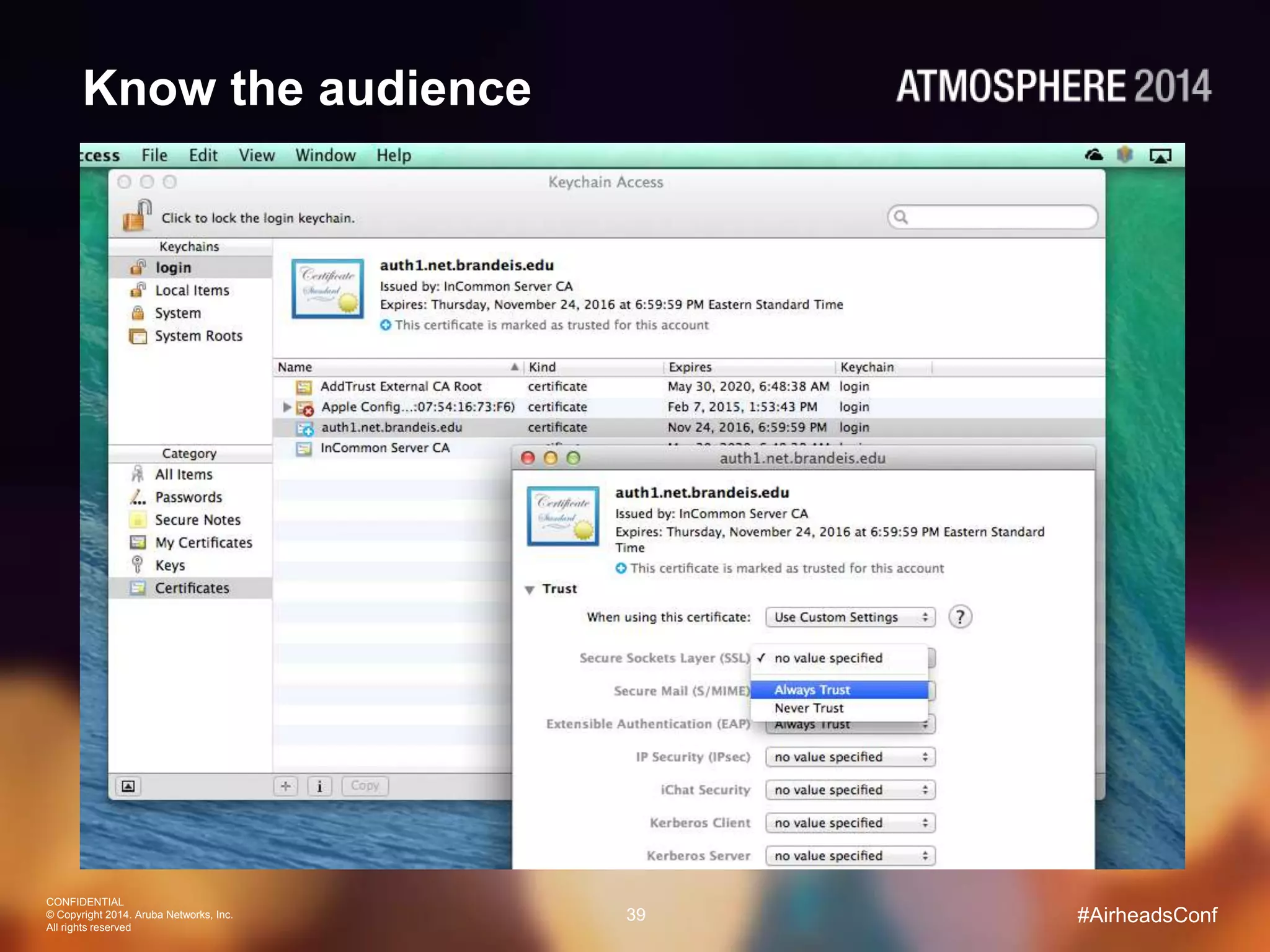
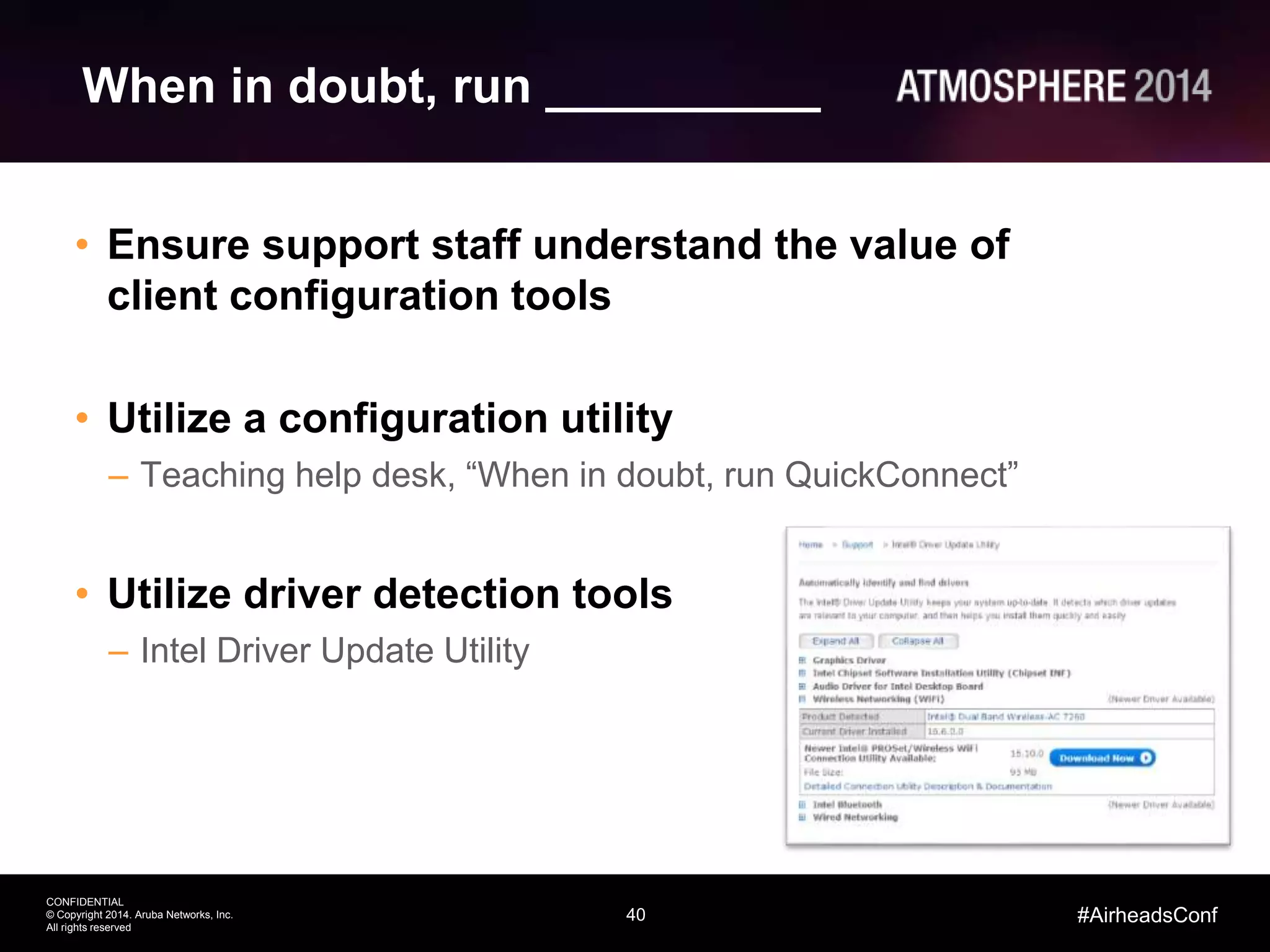
Tim Cappalli of Brandeis University presented on real-world challenges of deploying 802.1X authentication across wired and wireless networks. He discussed common EAP authentication methods like PEAP, EAP-TLS, and TTLS, noting their advantages and disadvantages. Cappalli also outlined challenges Brandeis faces including training support staff, empowering users, and planning for device onboarding. He explained steps Brandeis is taking like exploring EAP-TLS and utilizing client configuration tools to address these challenges.