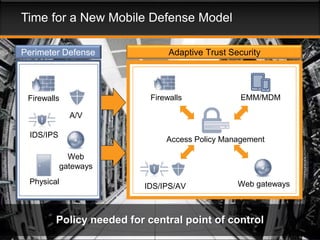
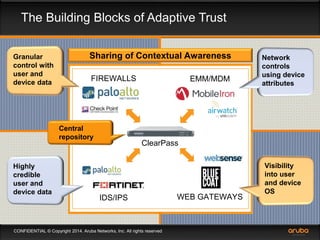
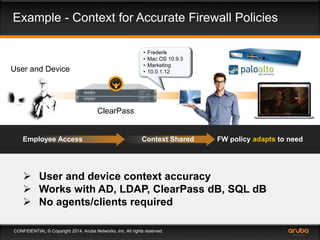
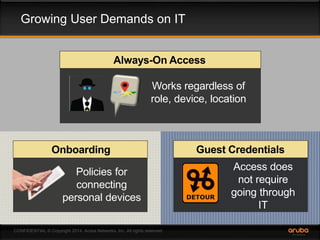
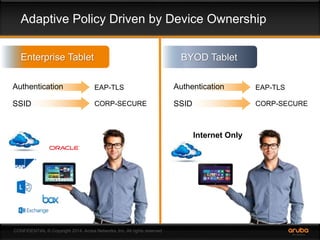
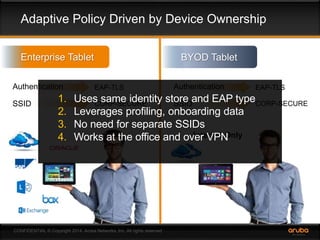
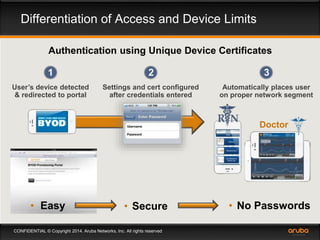
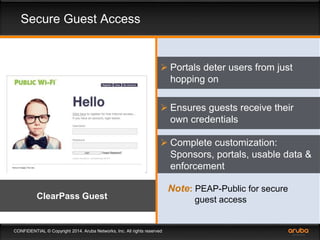
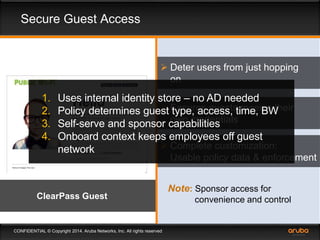
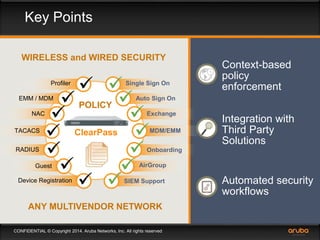
This document discusses the need for adaptive trust security policies to address challenges from increased enterprise mobility and BYOD trends. It promotes the Aruba ClearPass policy management platform as a solution. ClearPass provides centralized identity management, device profiling, and context-aware access policies. It can integrate with firewalls, MDM solutions, and other security tools to enable adaptive, risk-based access control based on user, device, app, and location attributes. ClearPass supports a range of use cases including secure BYOD access, differentiated guest access, and migration from AAA to context-based policy models.