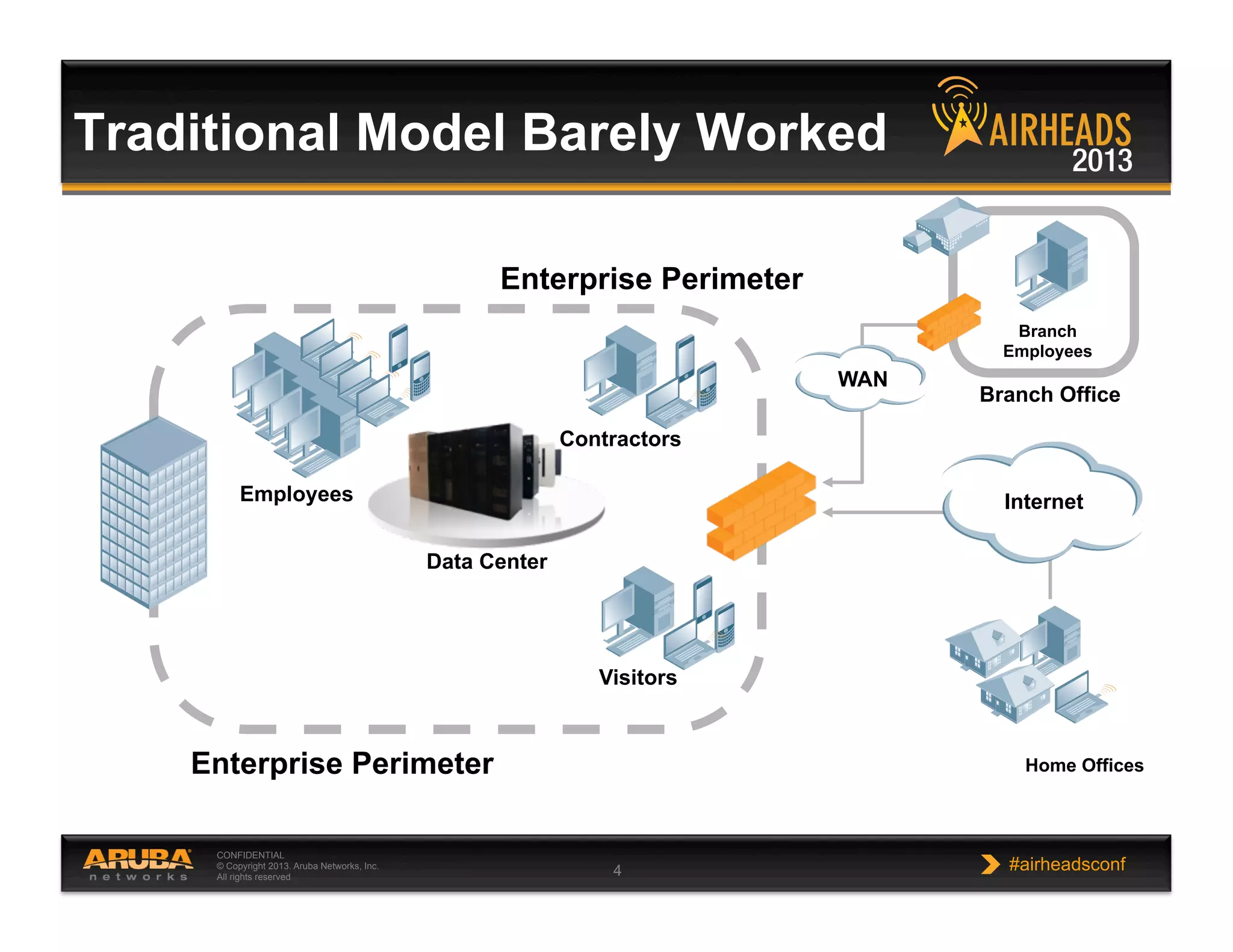
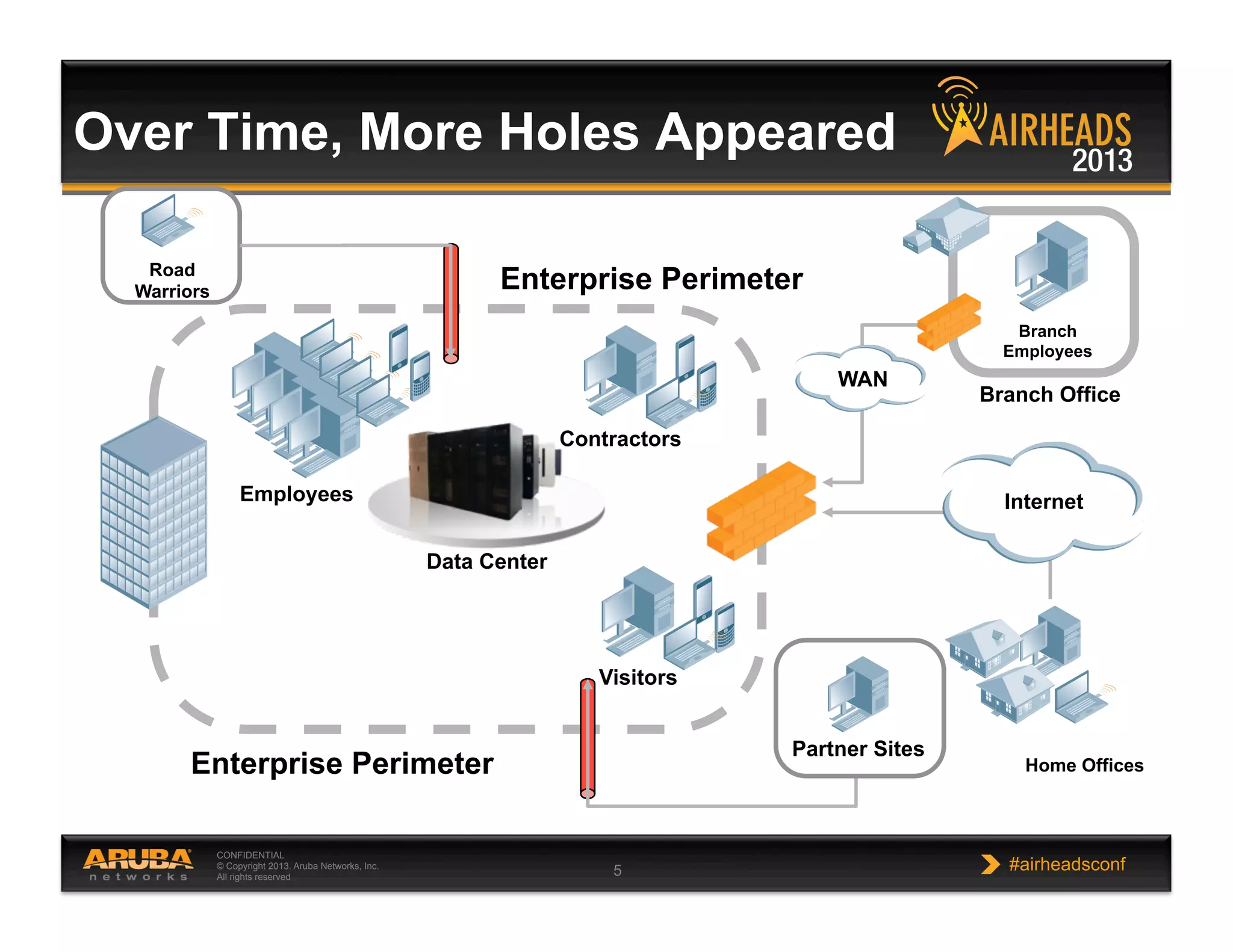
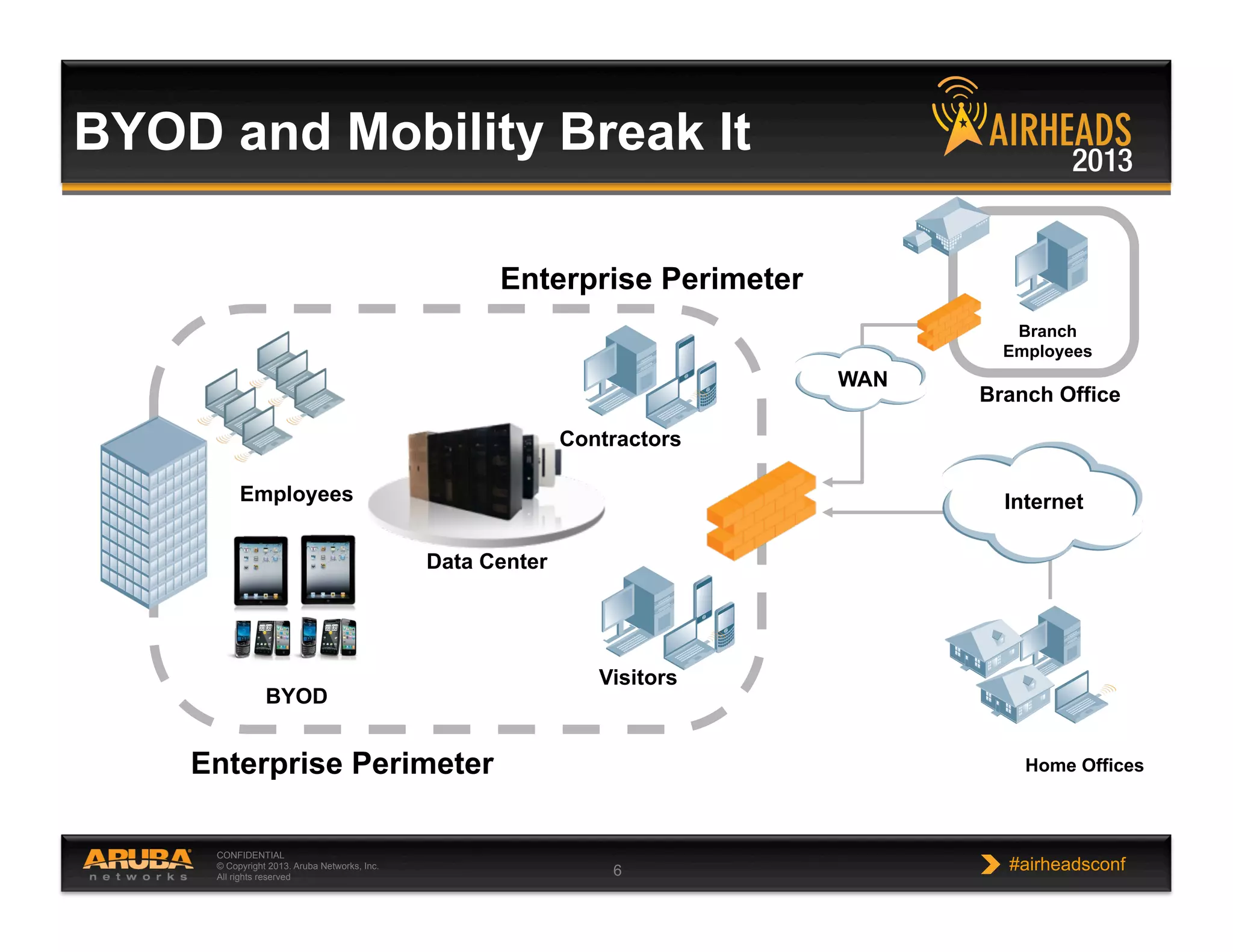
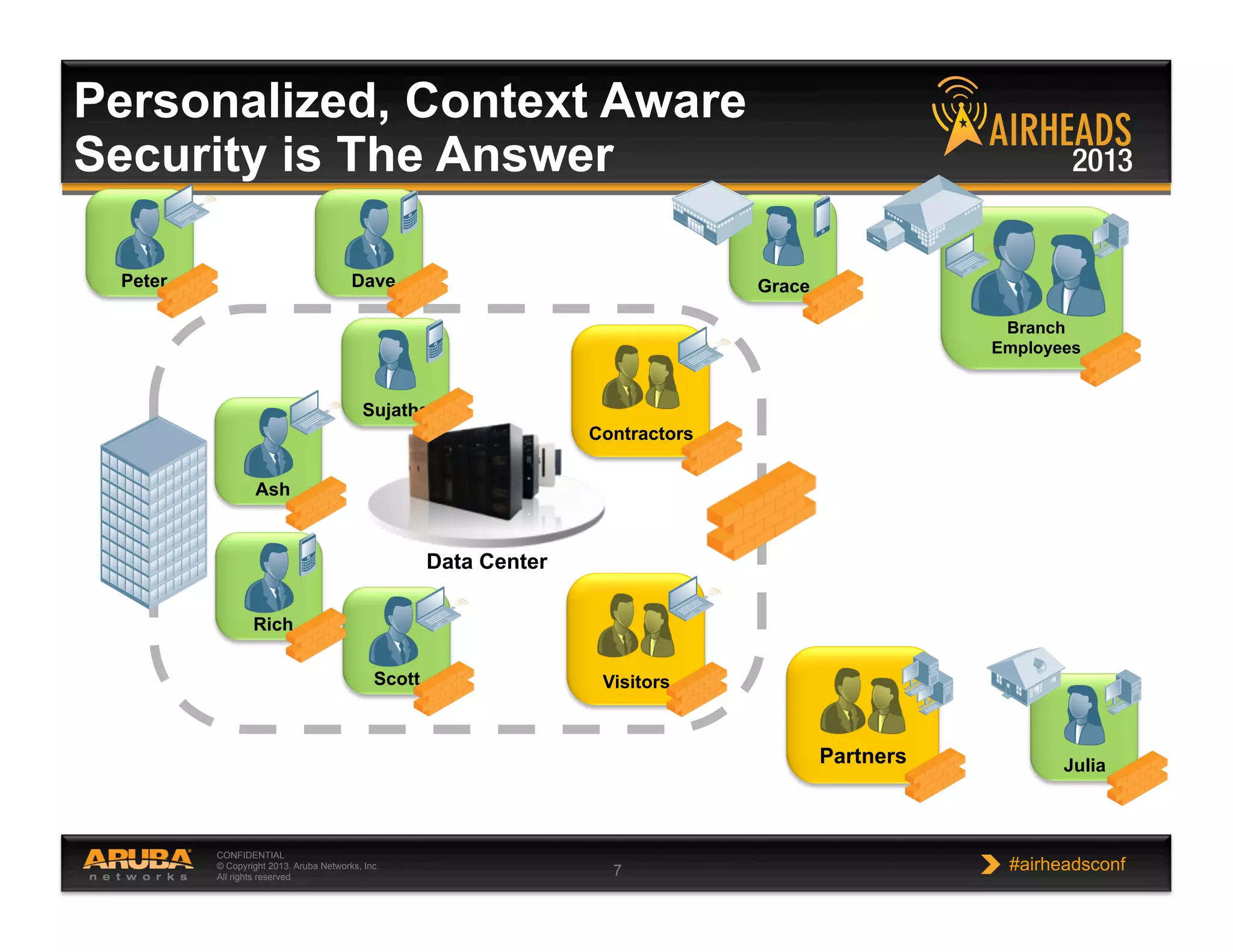
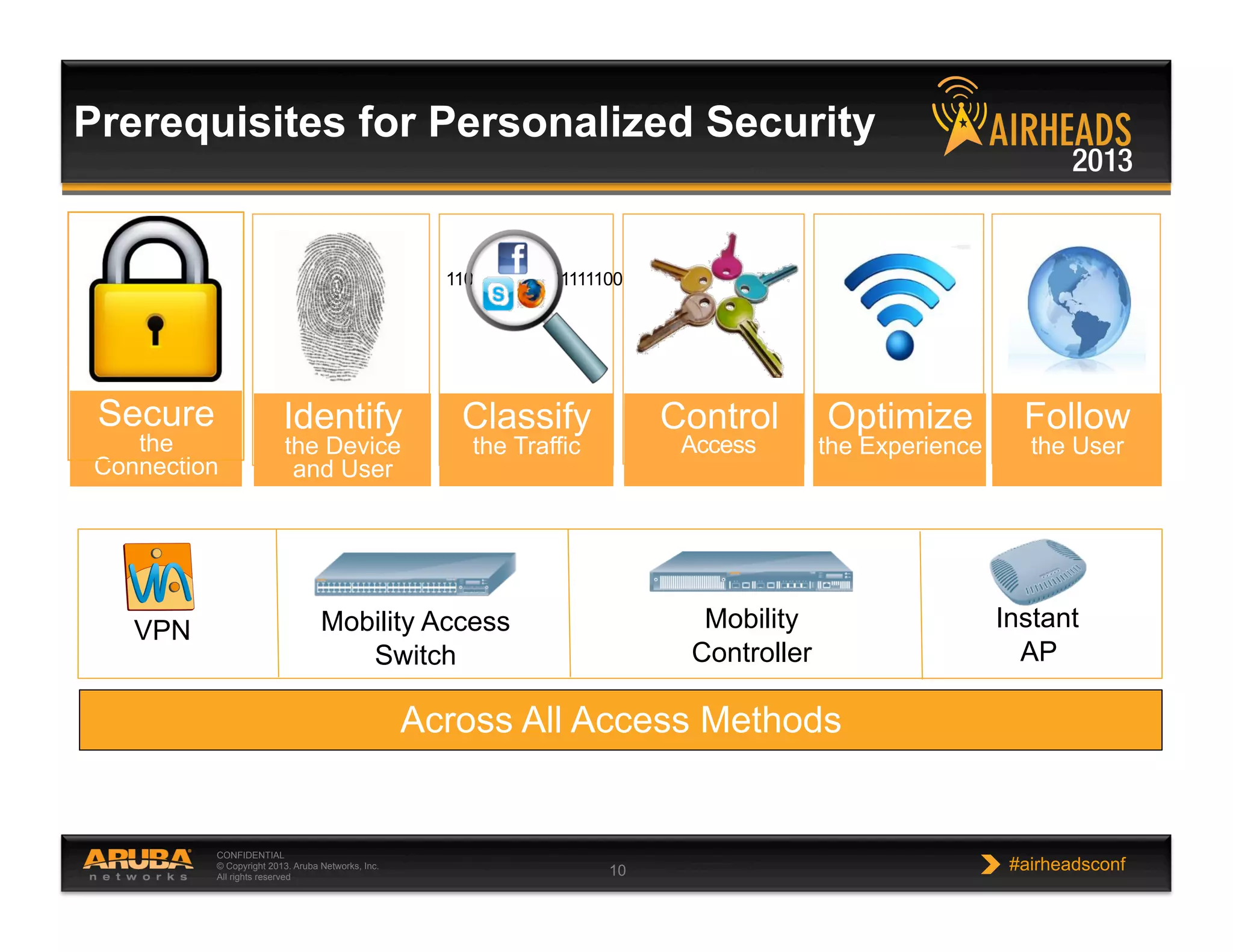
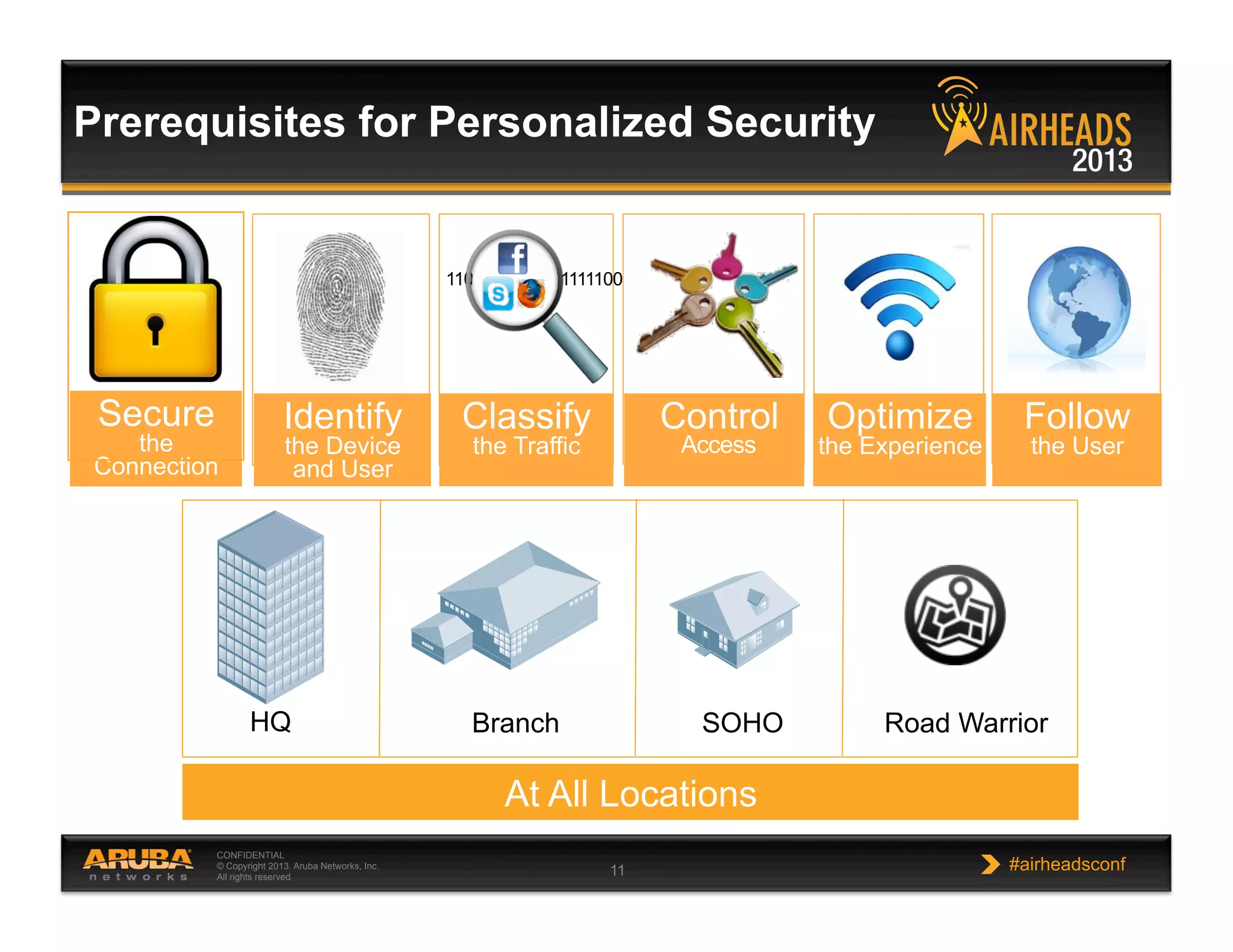
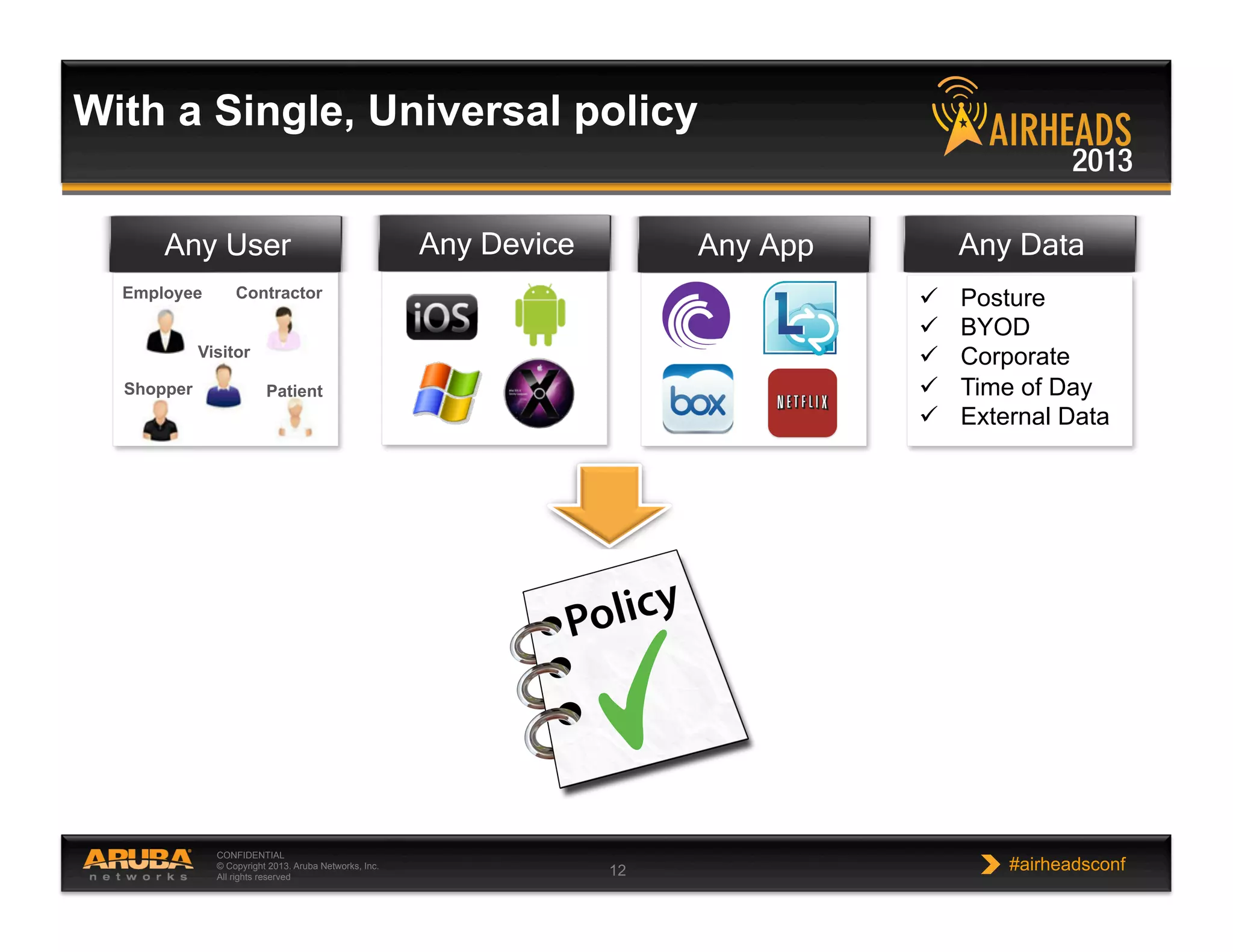
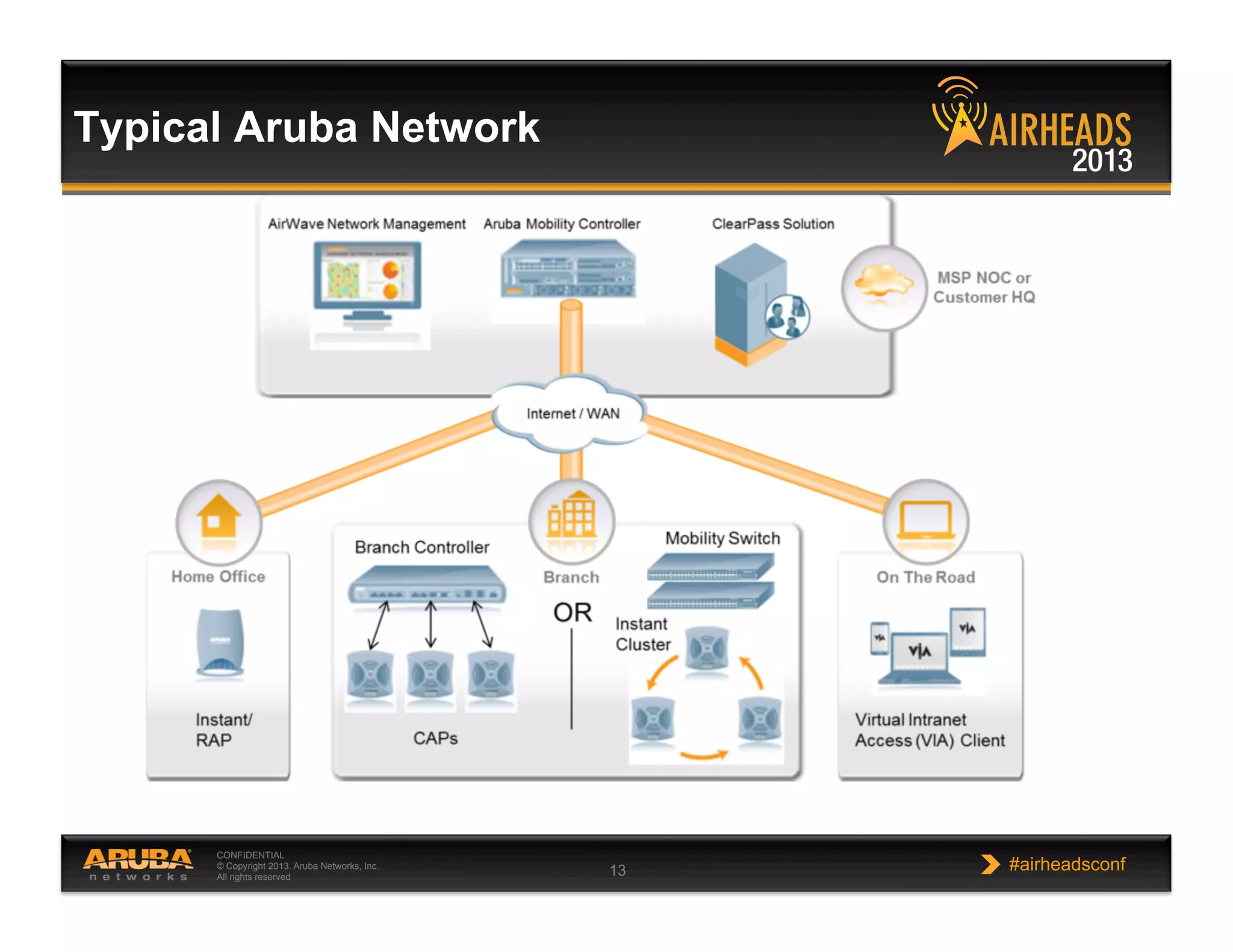
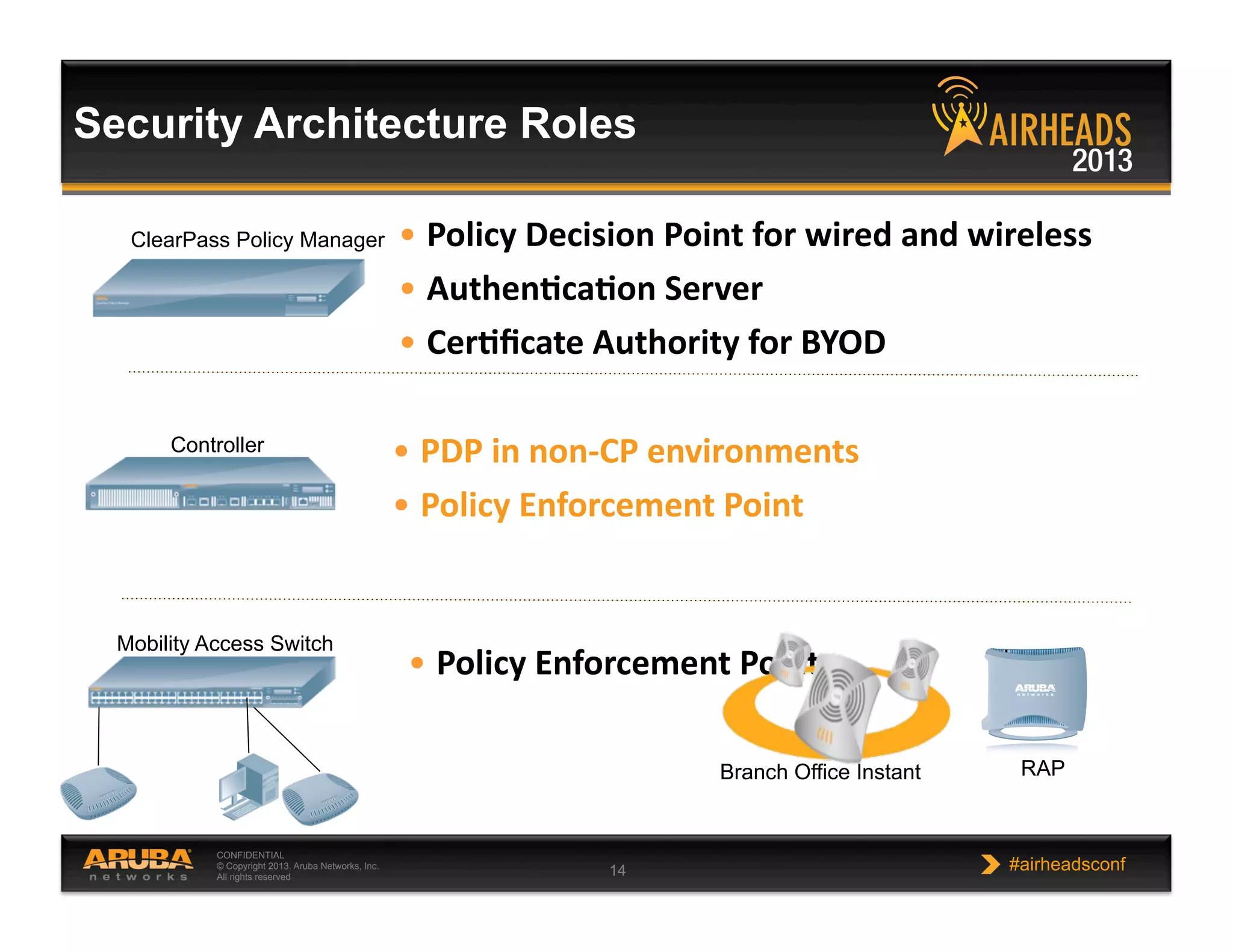
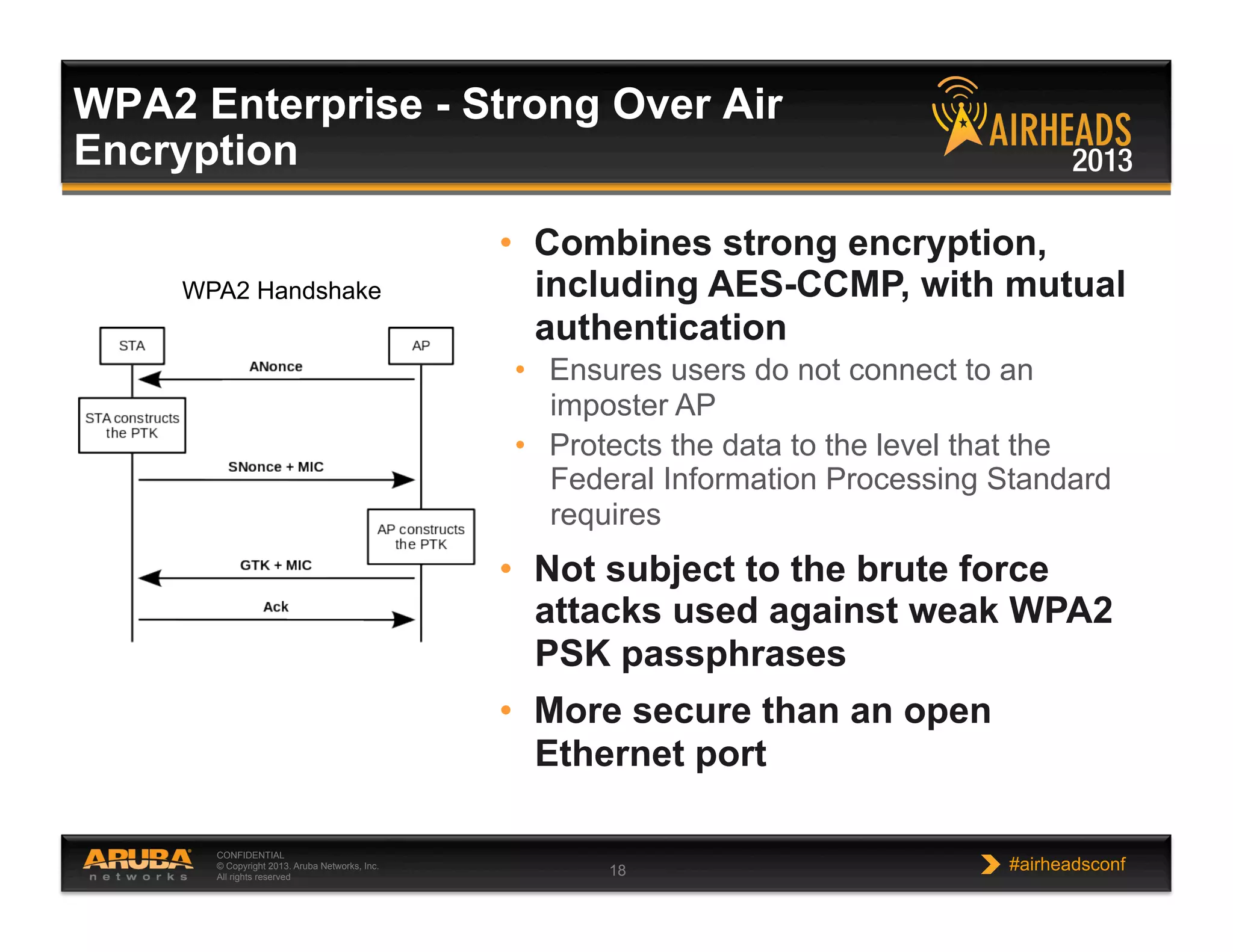
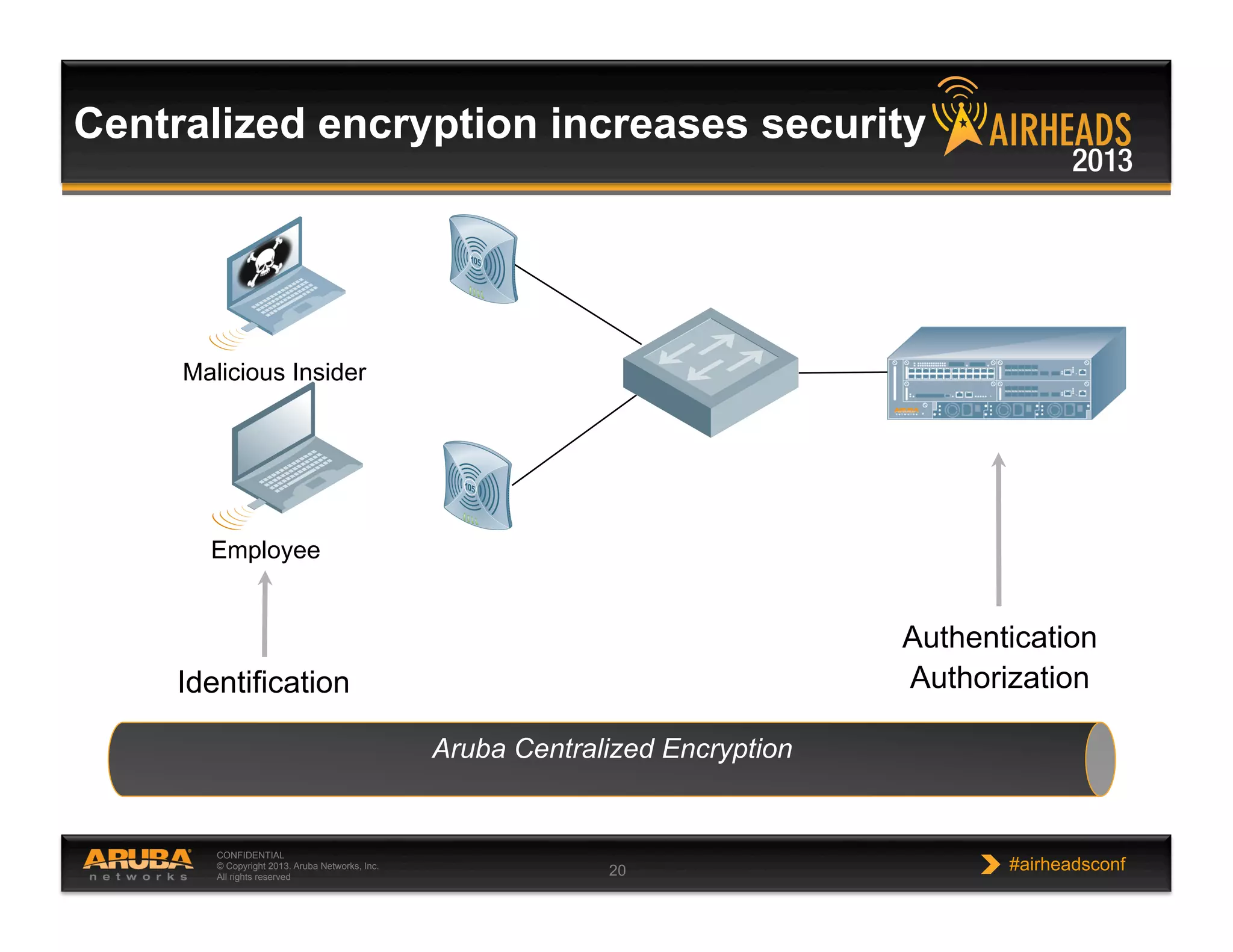
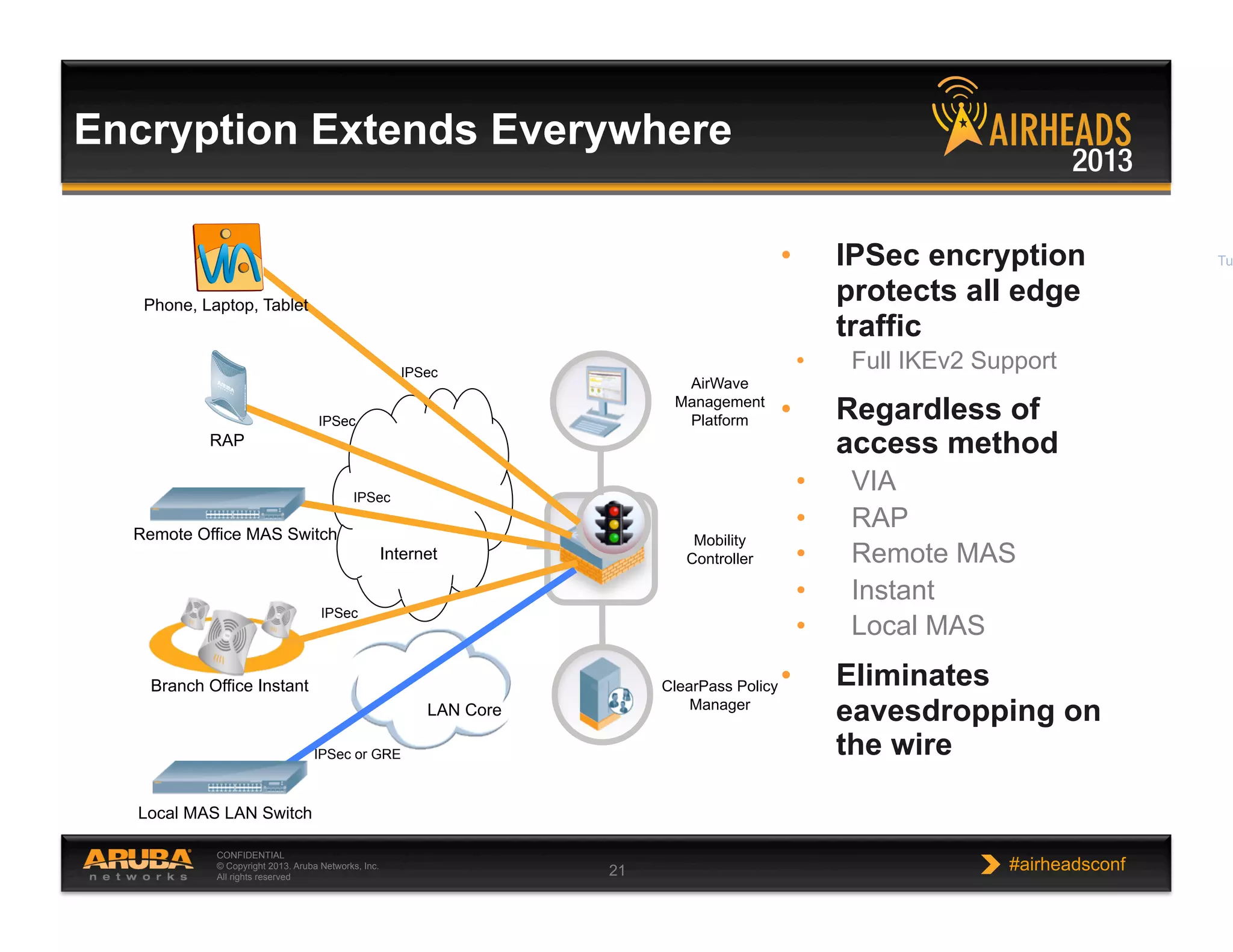
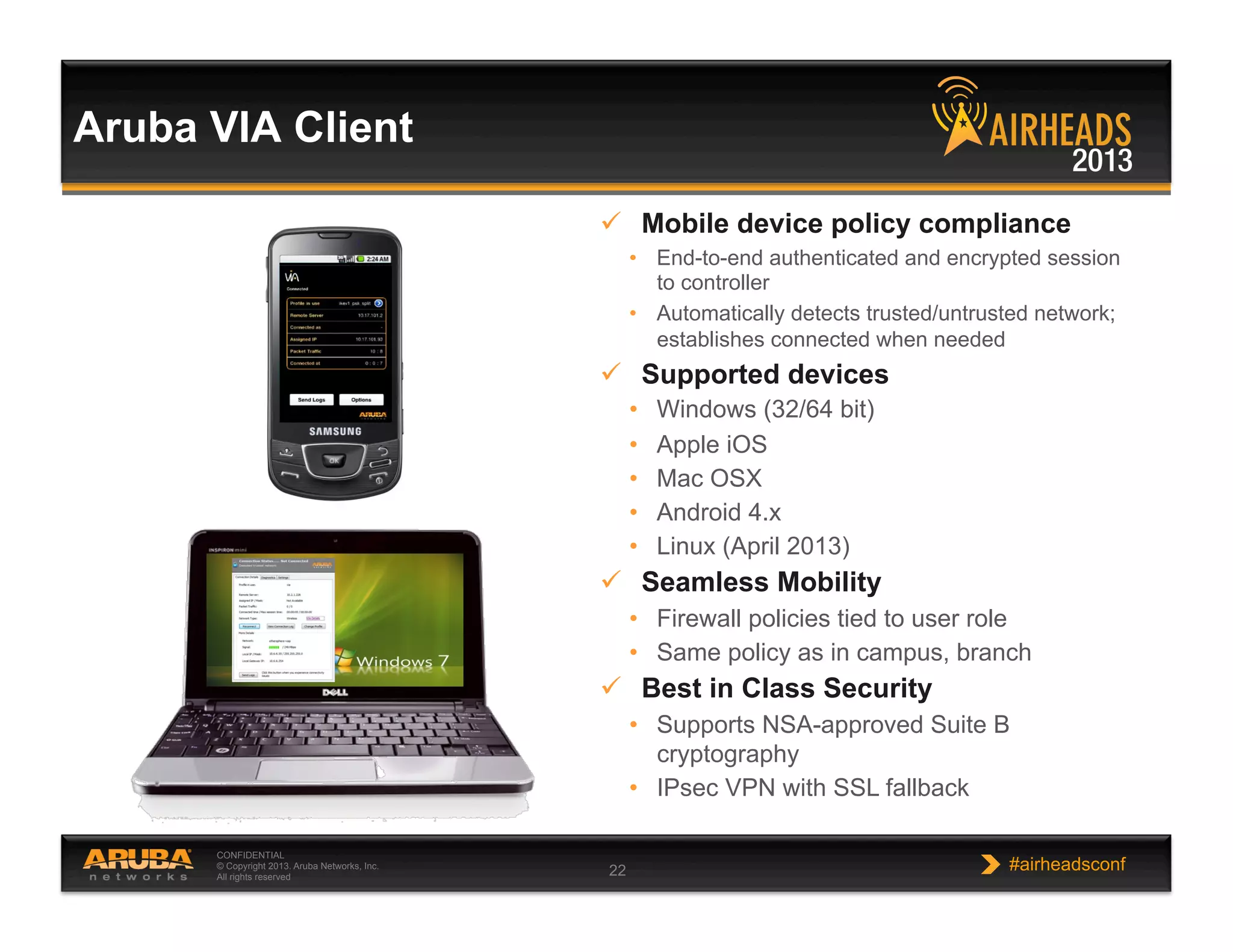
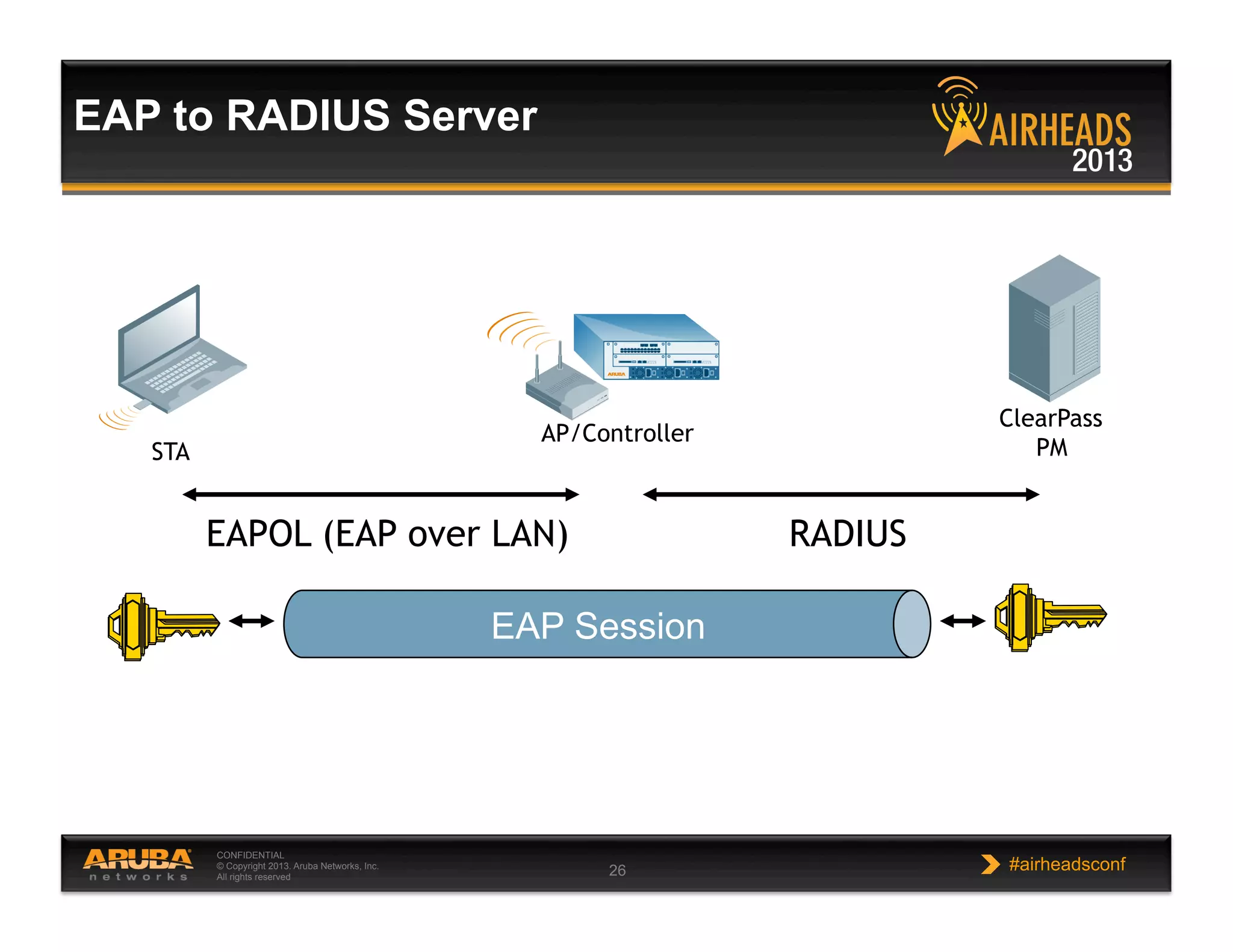
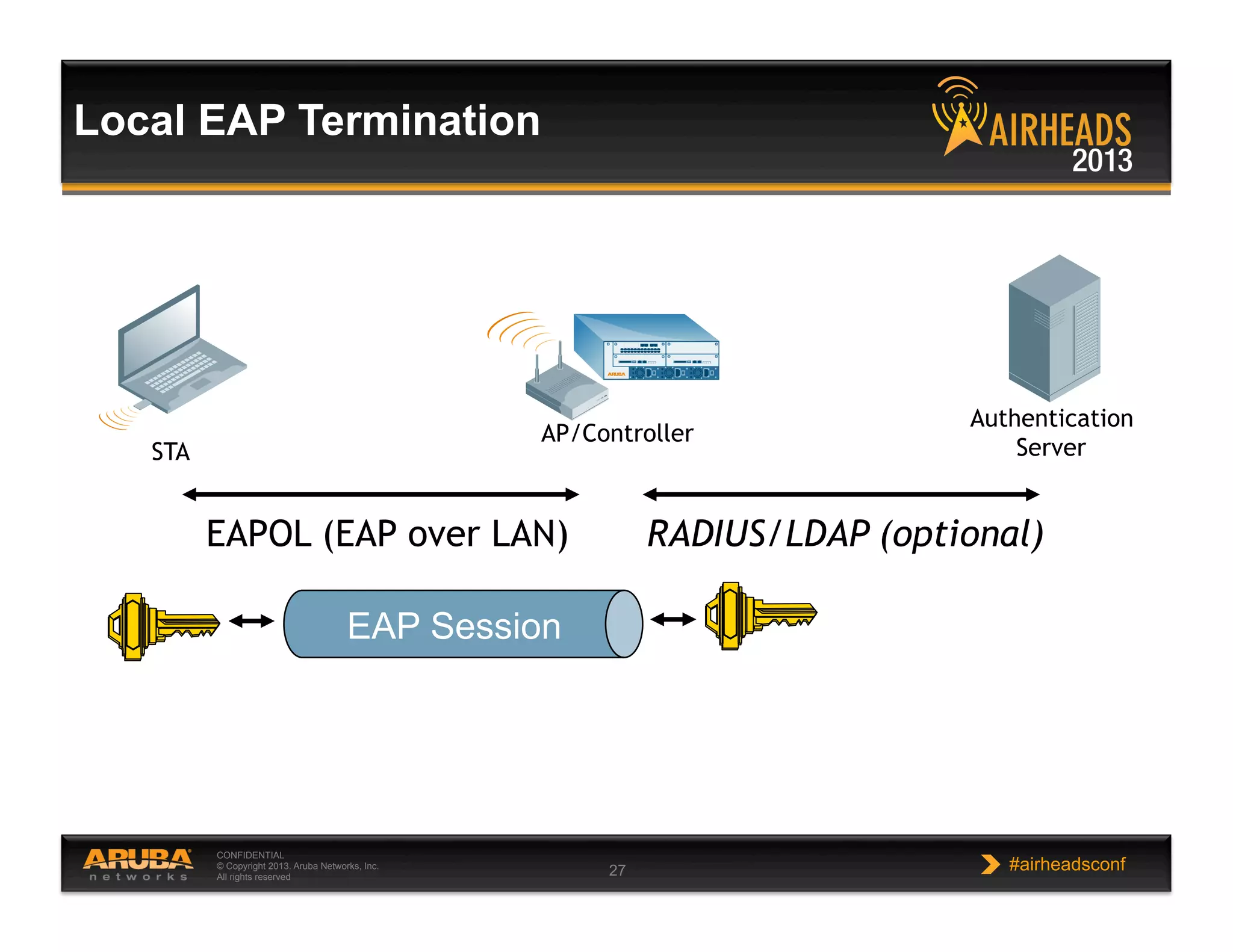
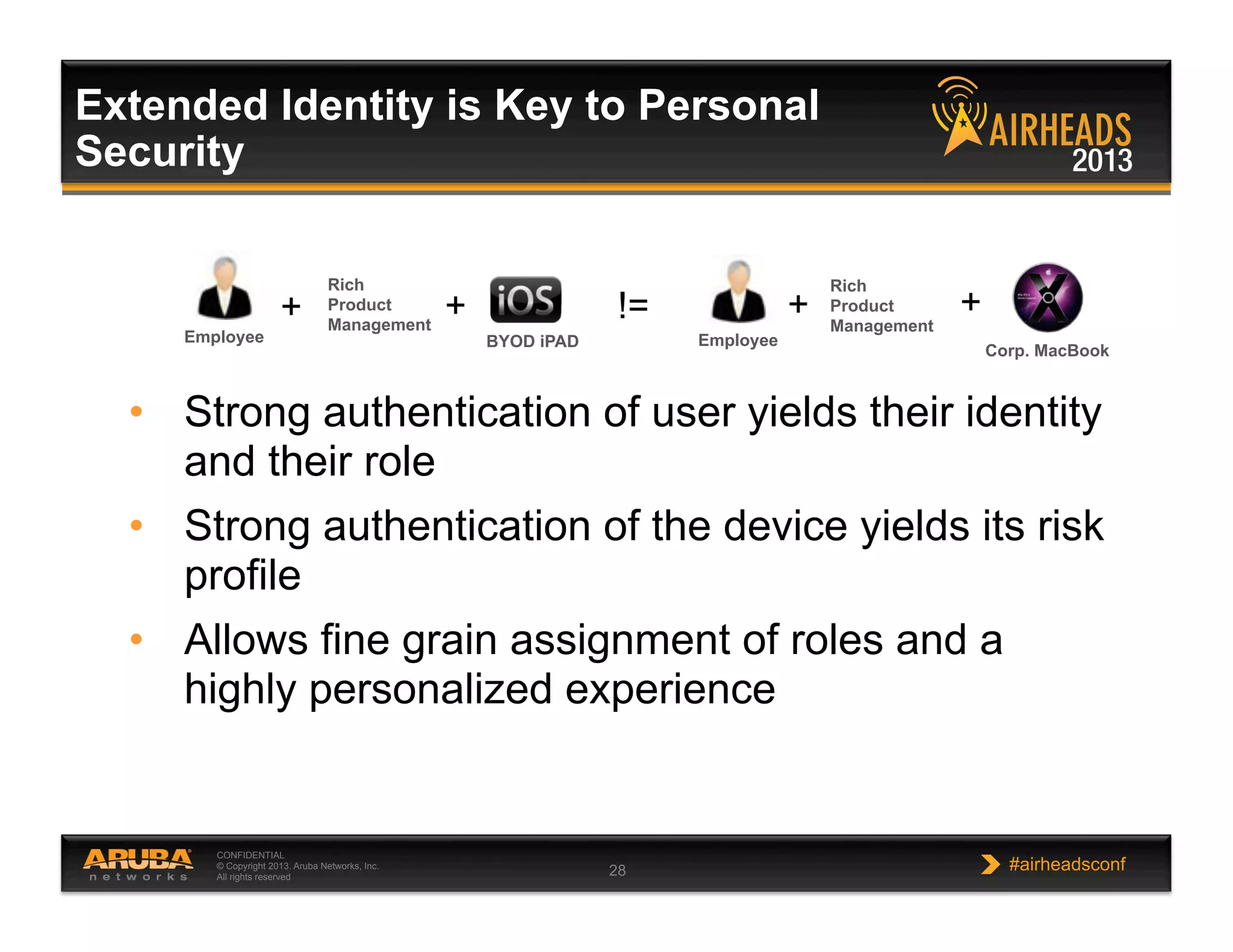
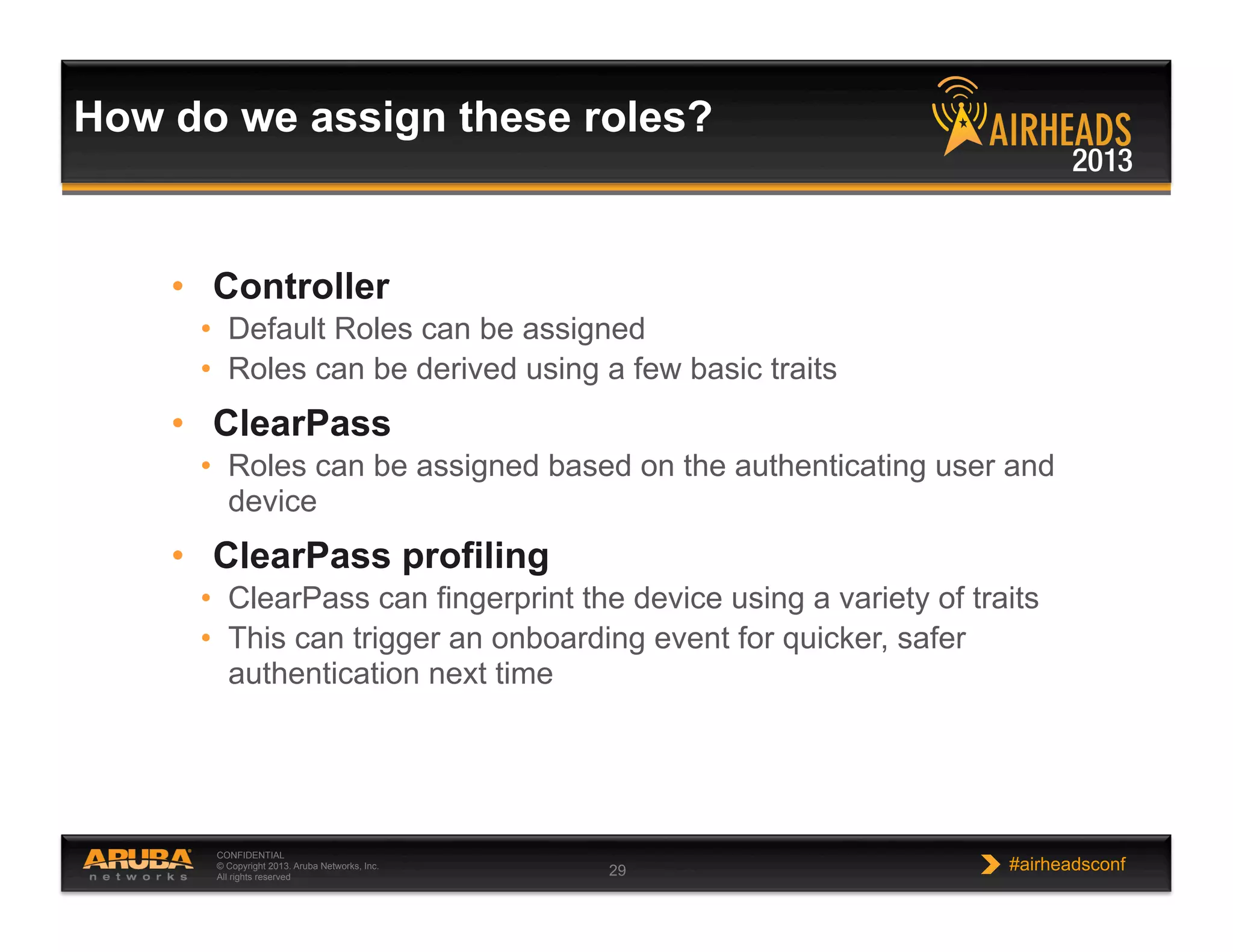
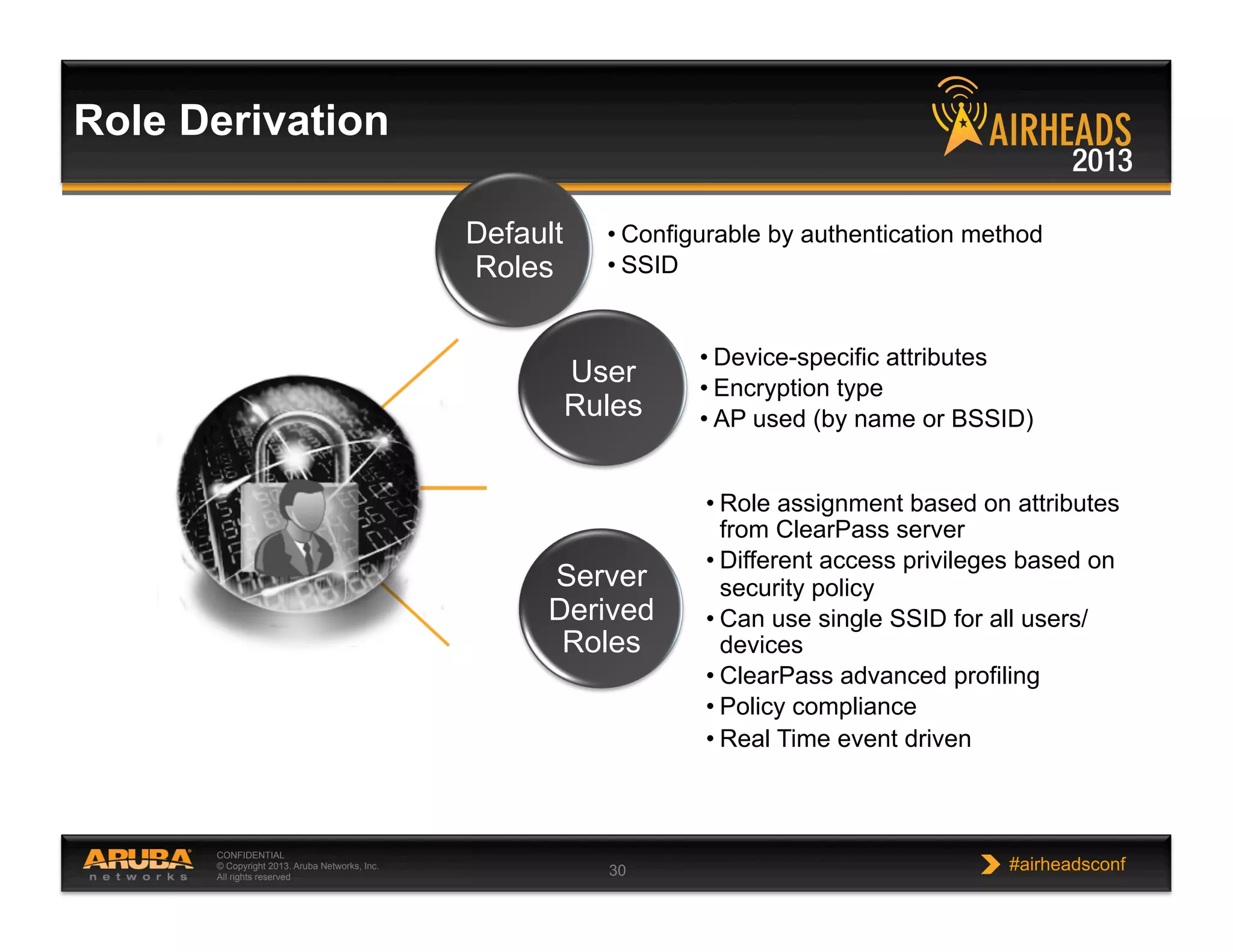
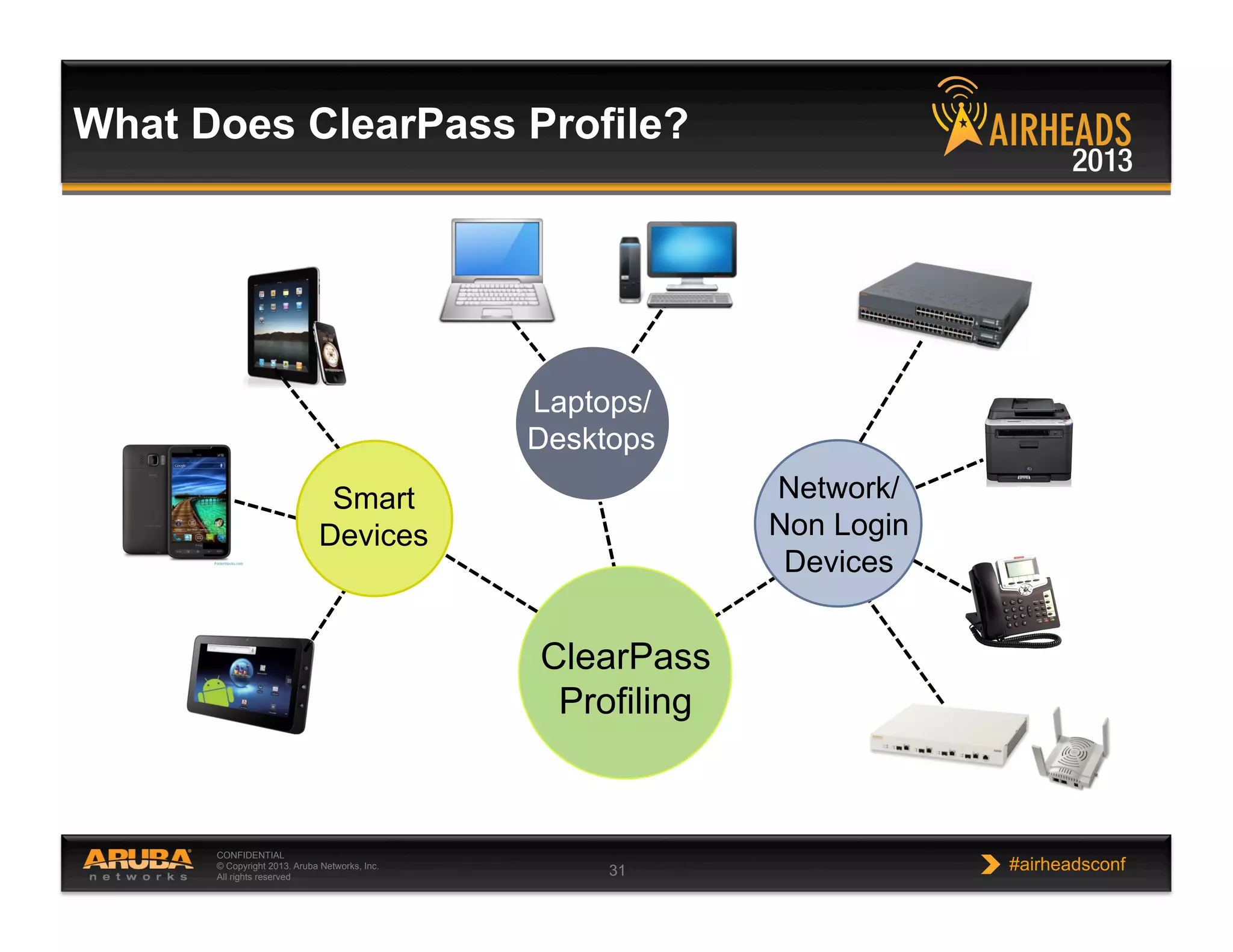
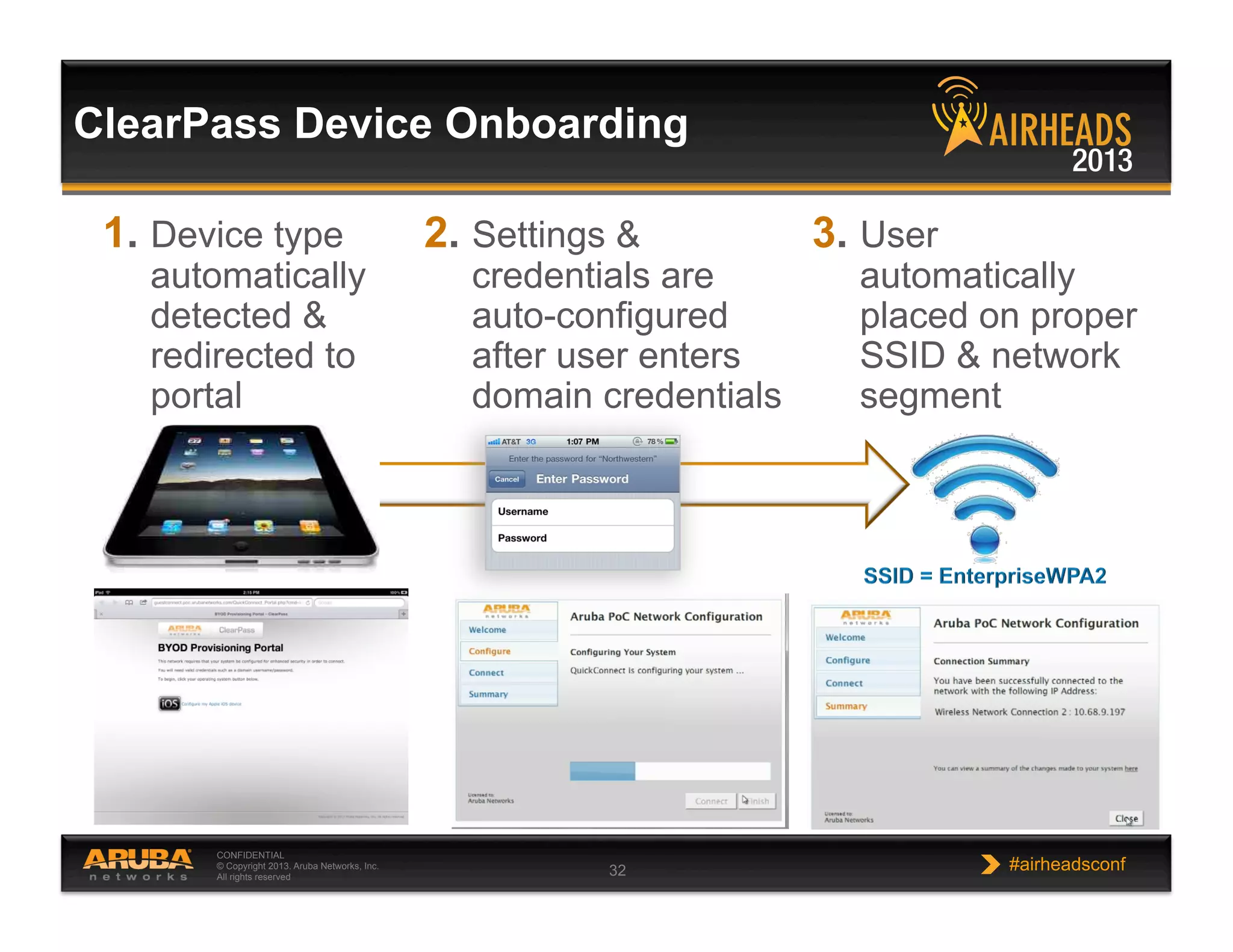
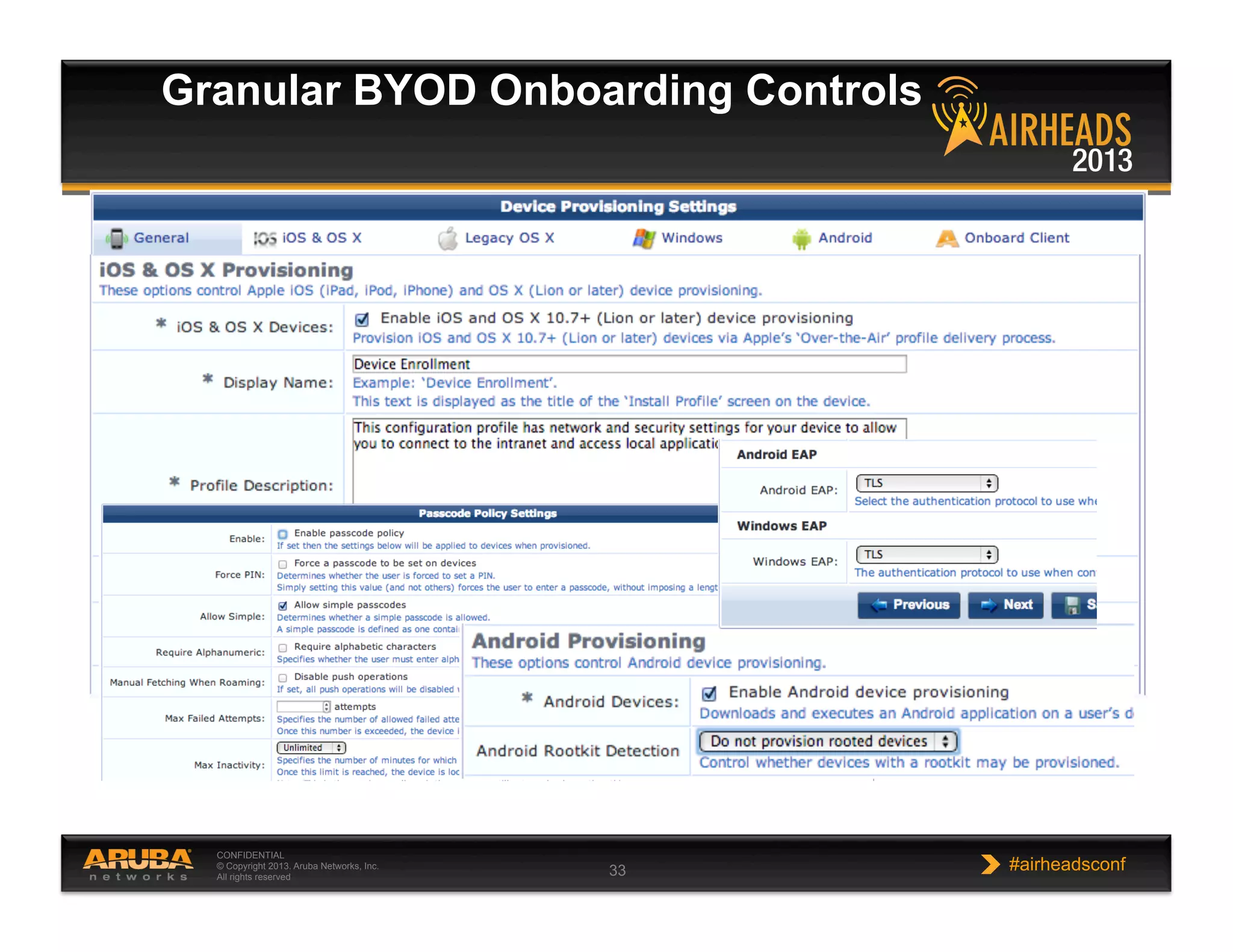
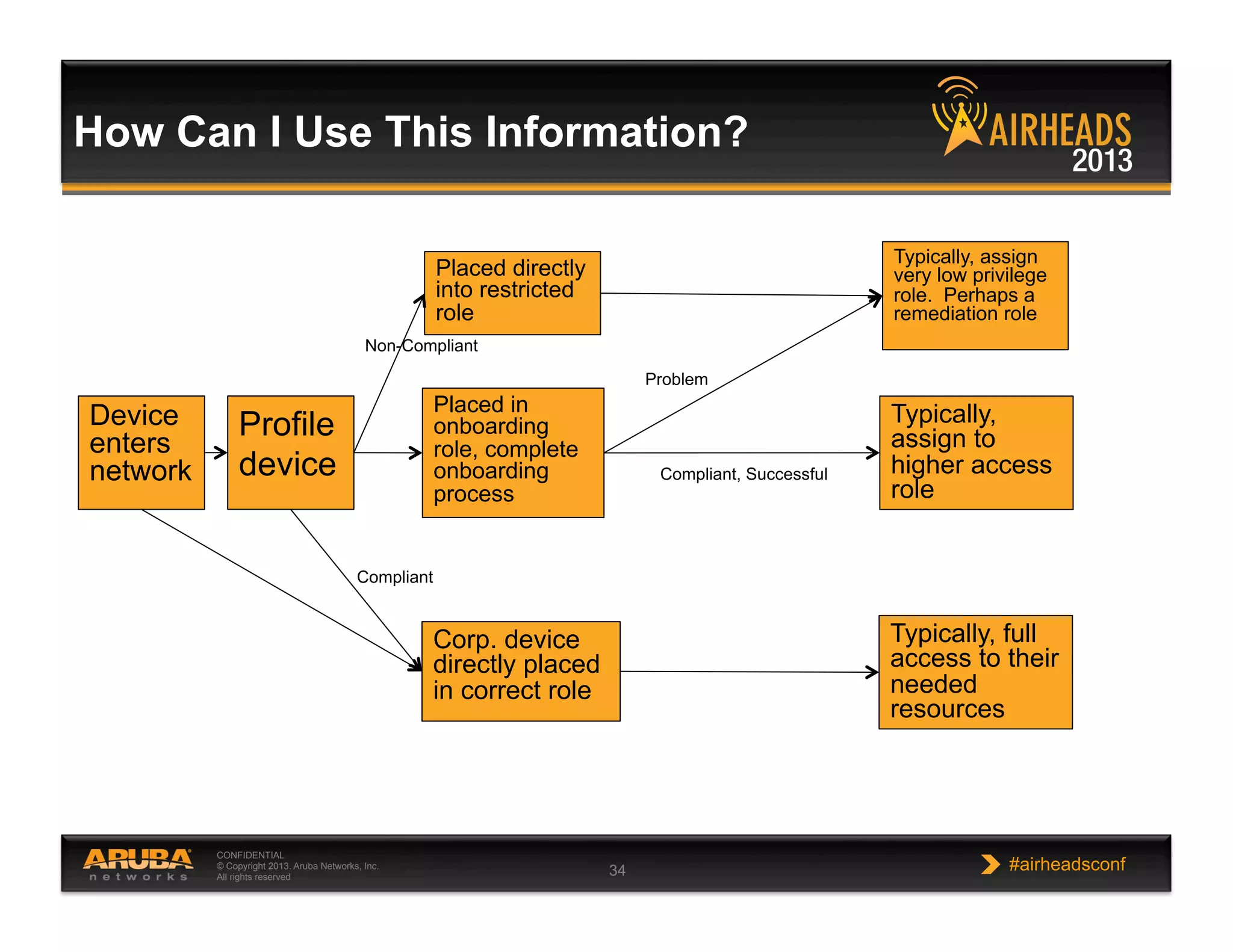
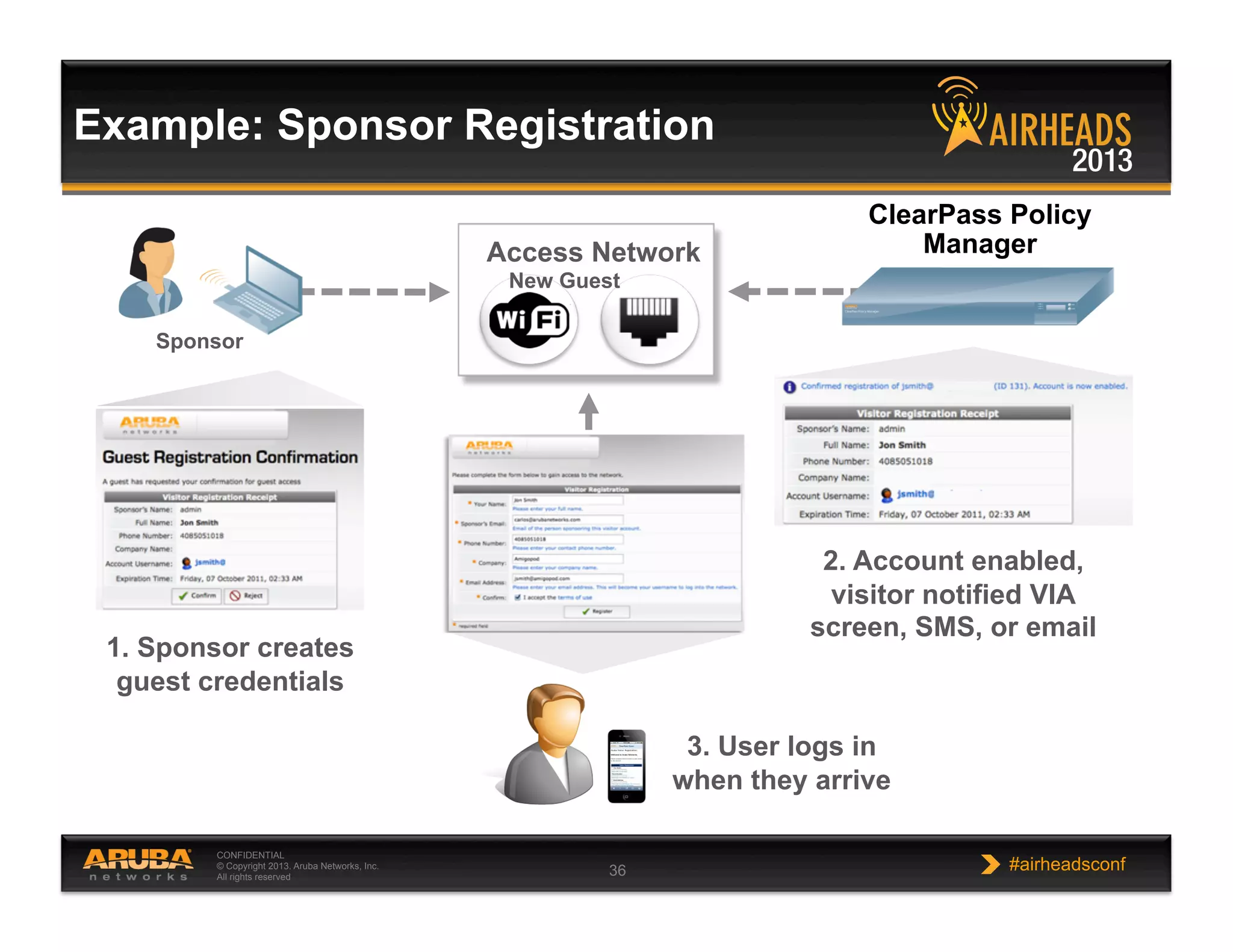
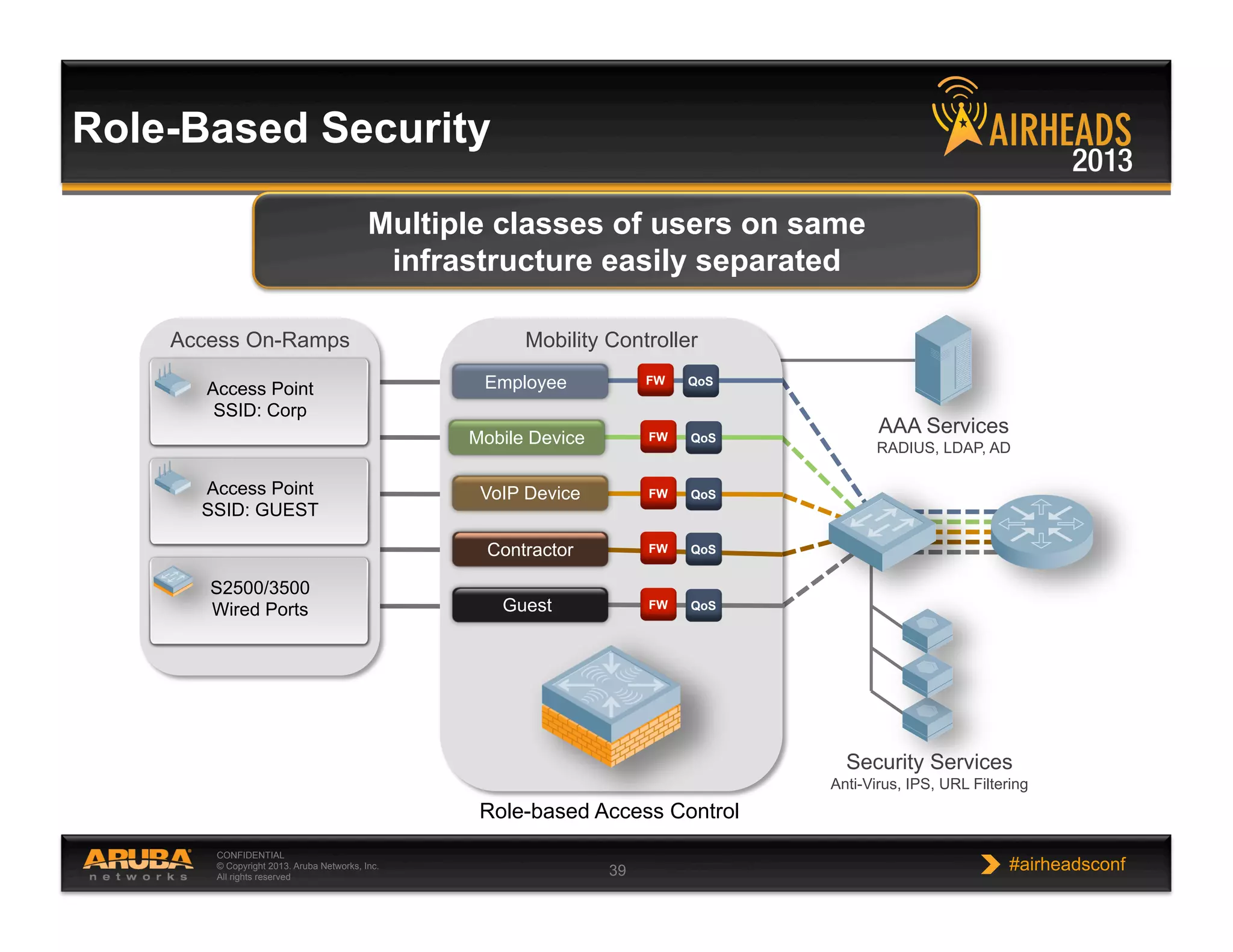
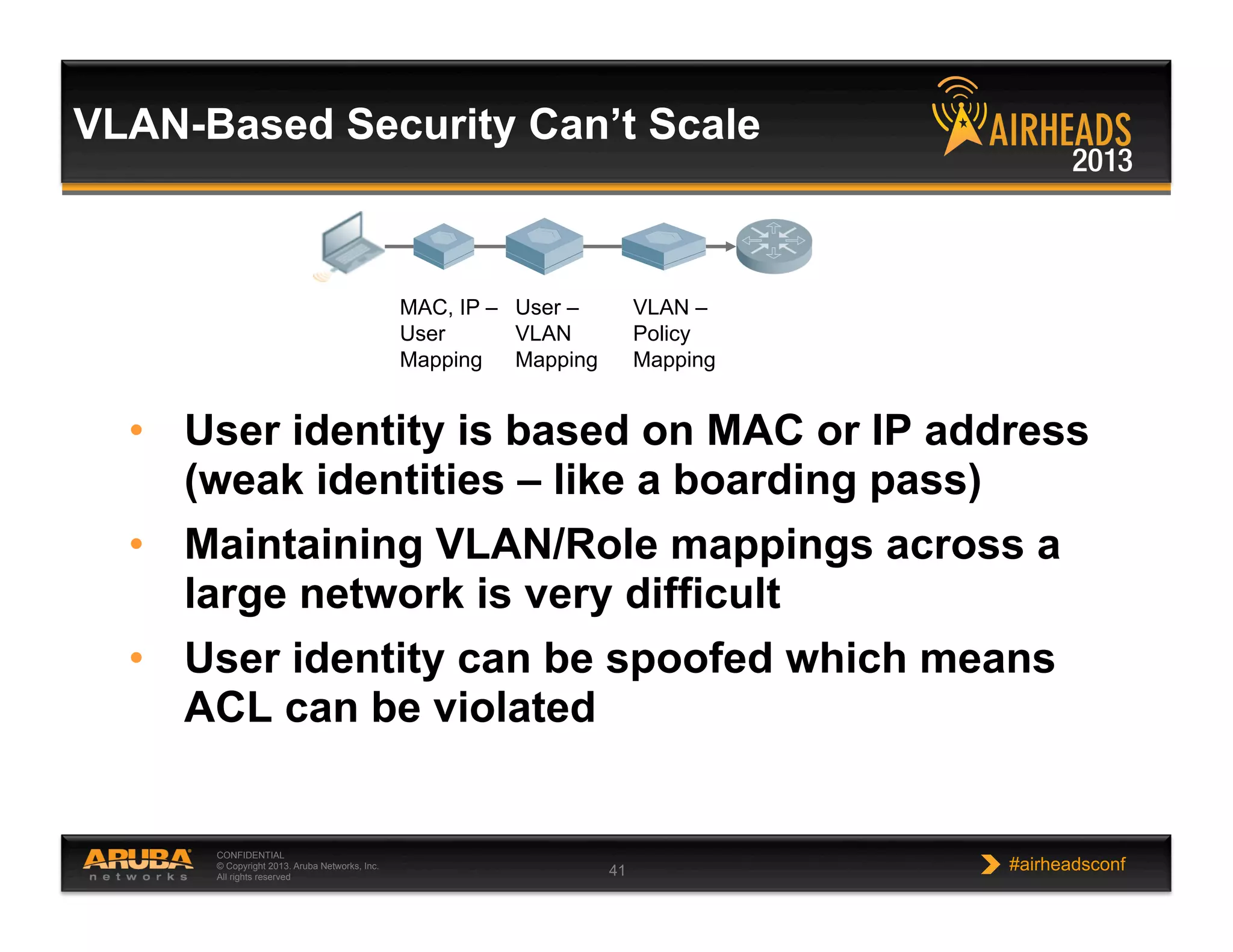
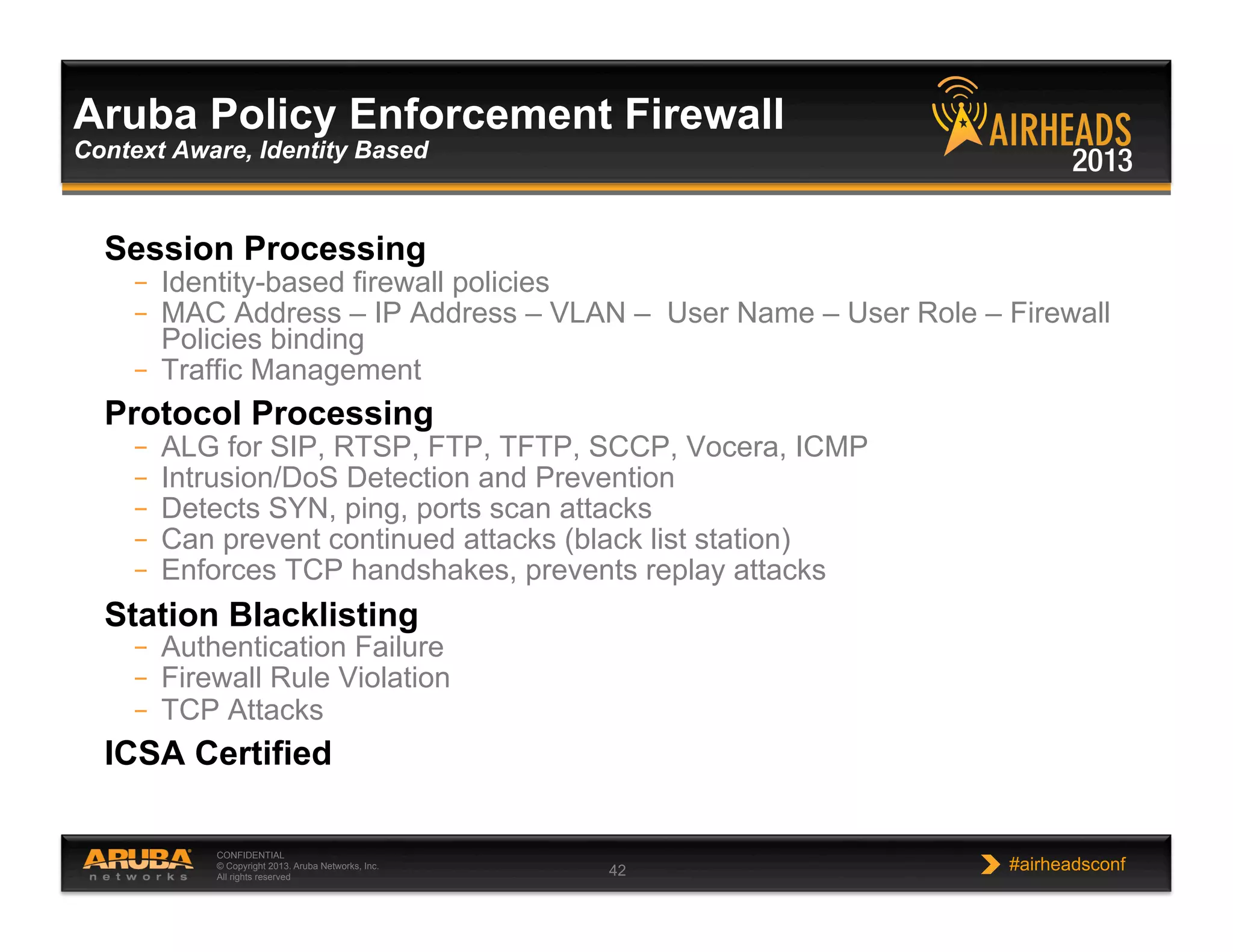
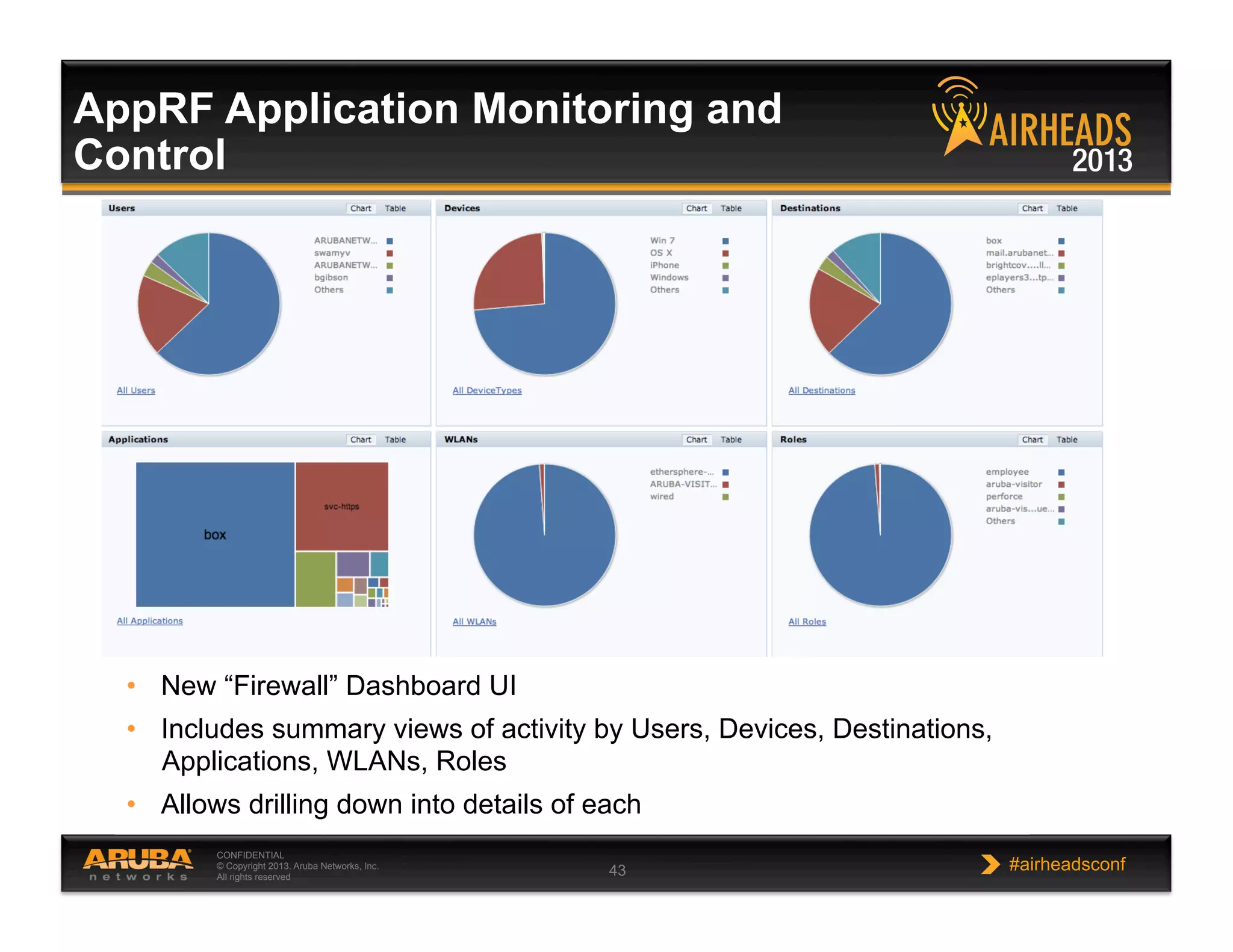
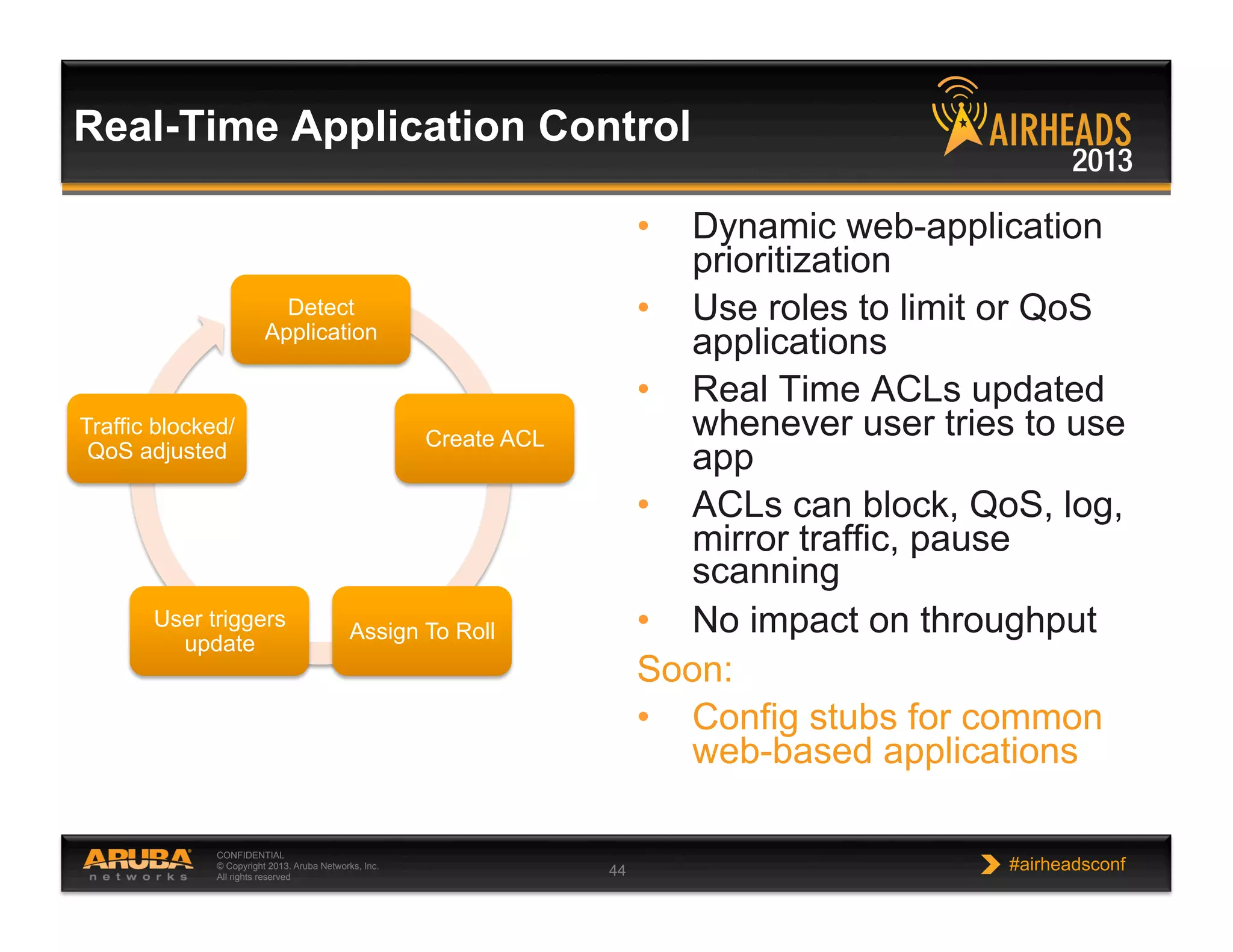
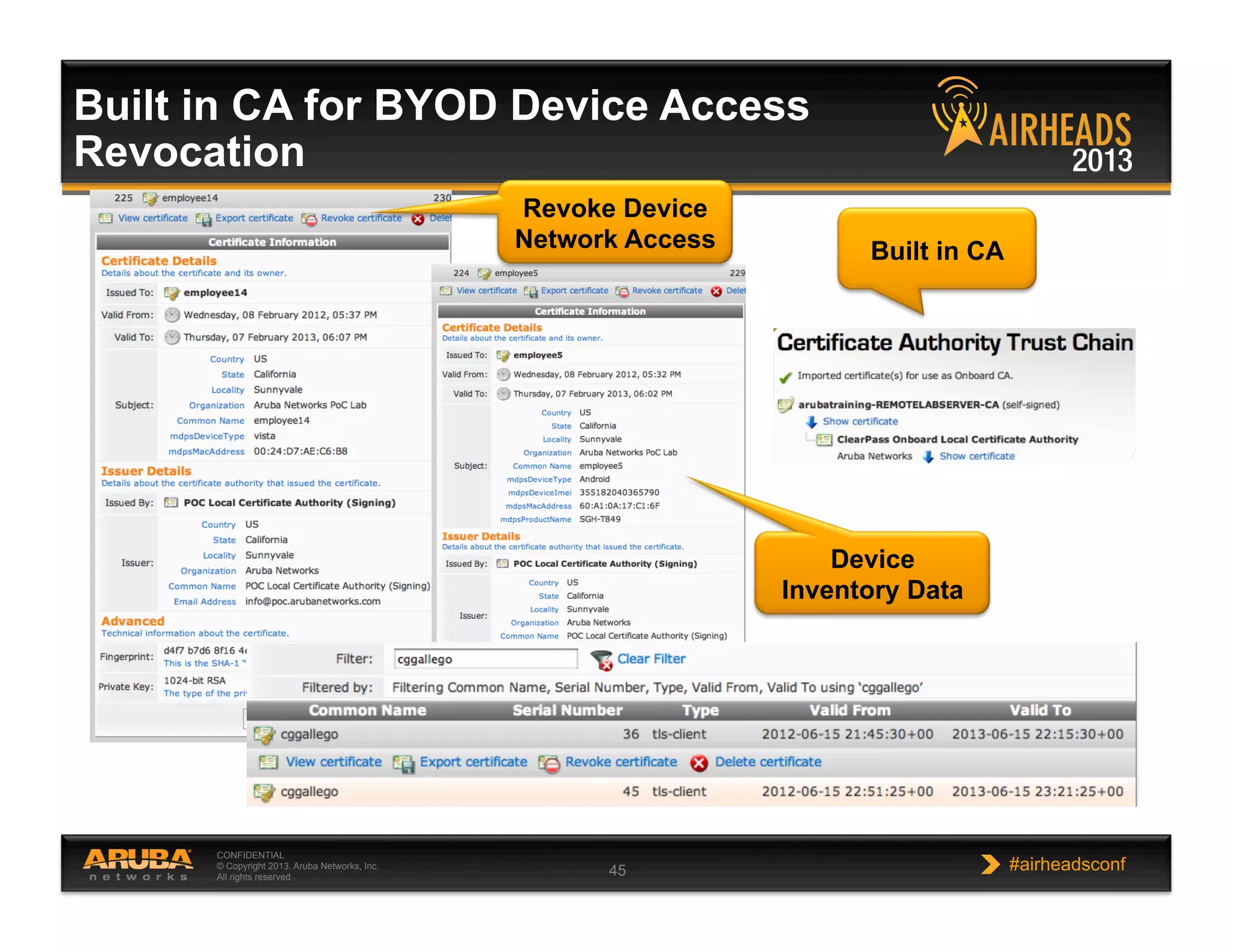
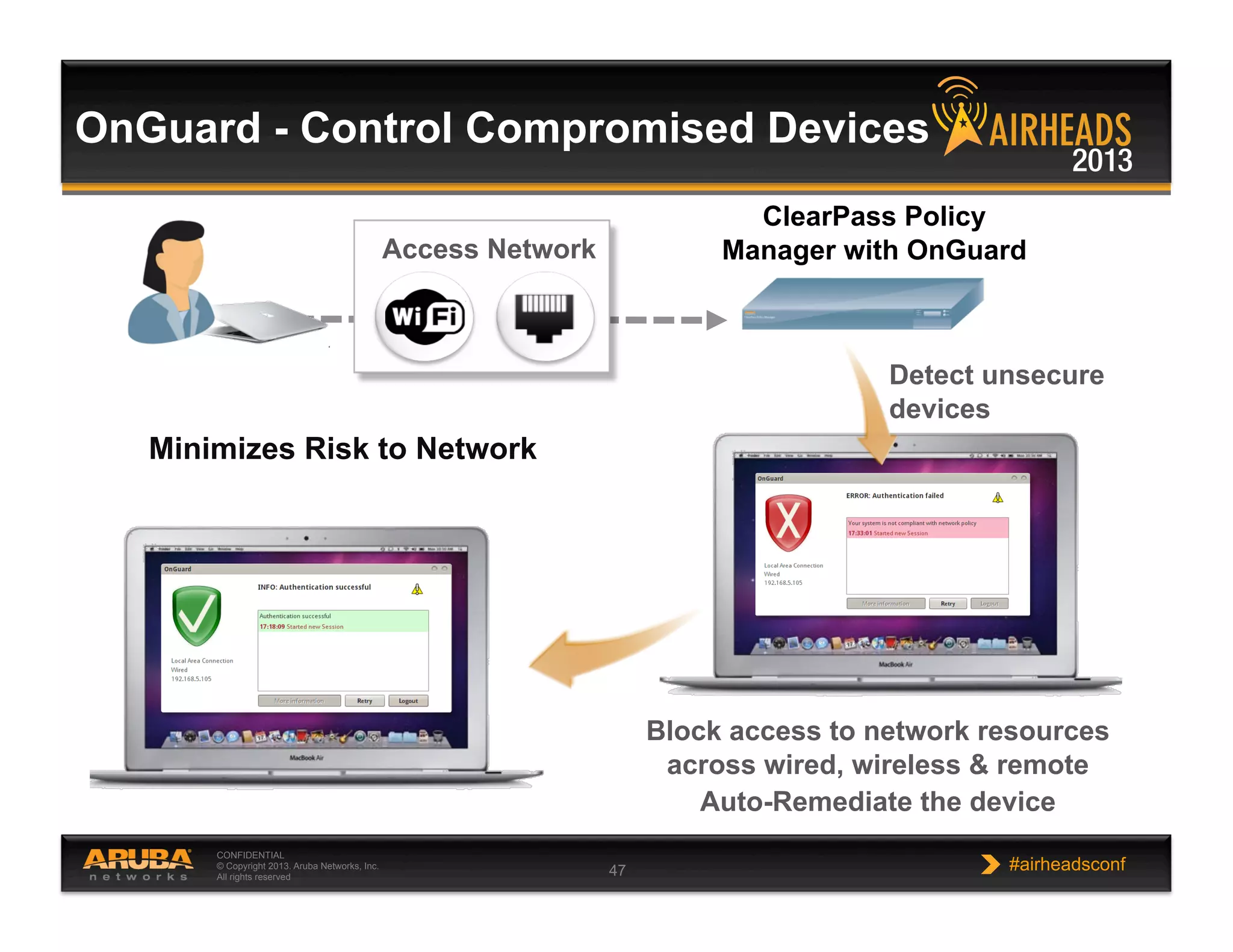
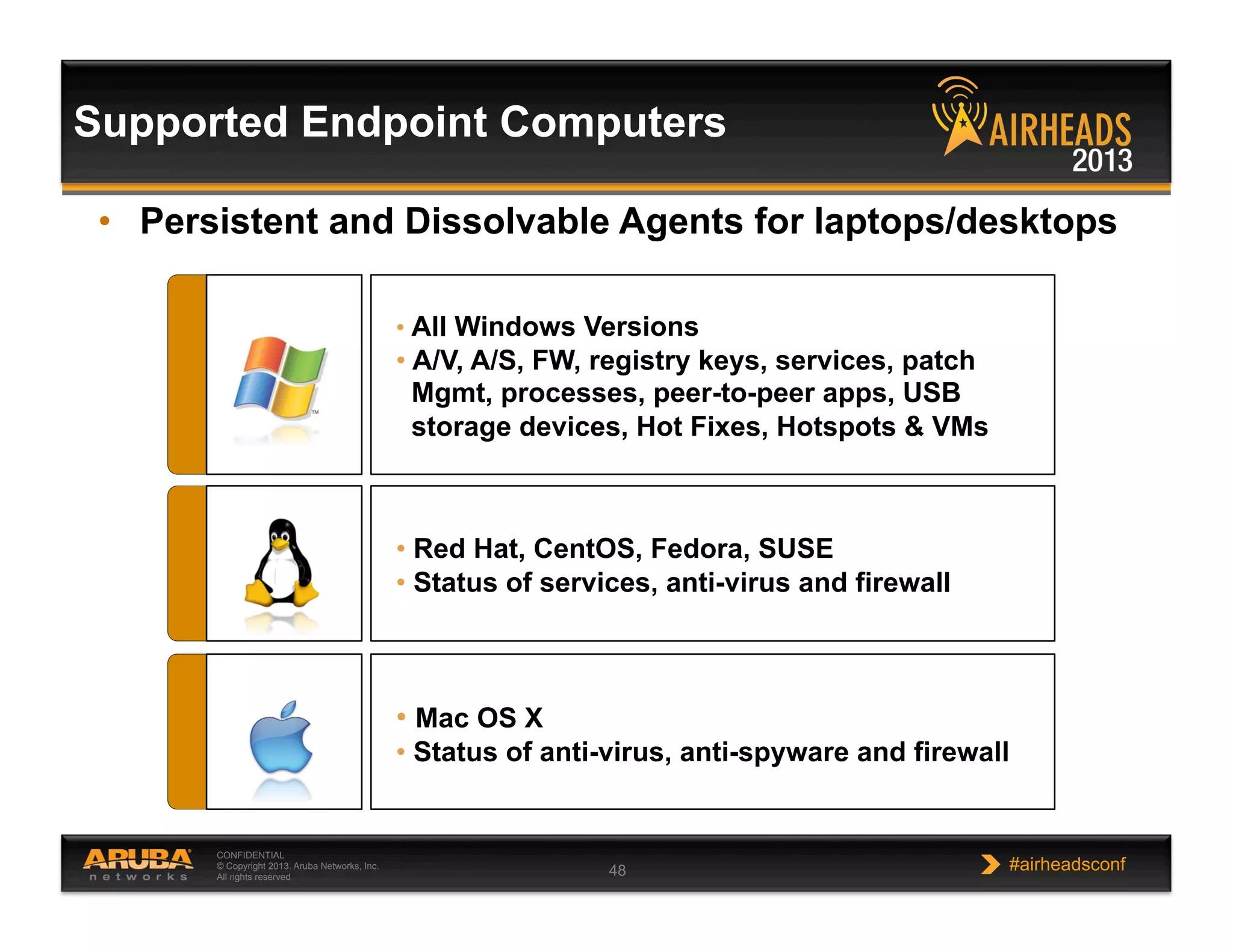
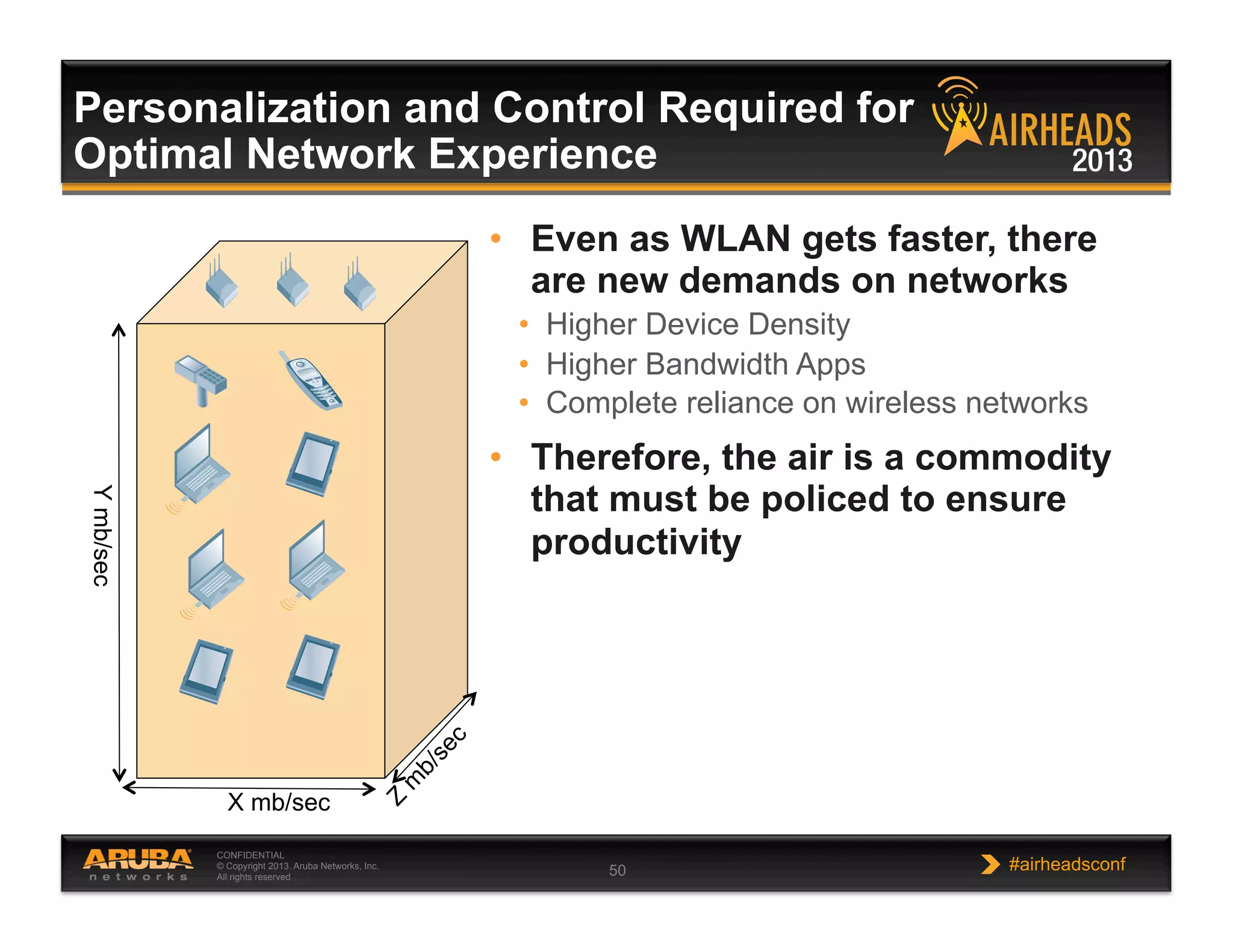
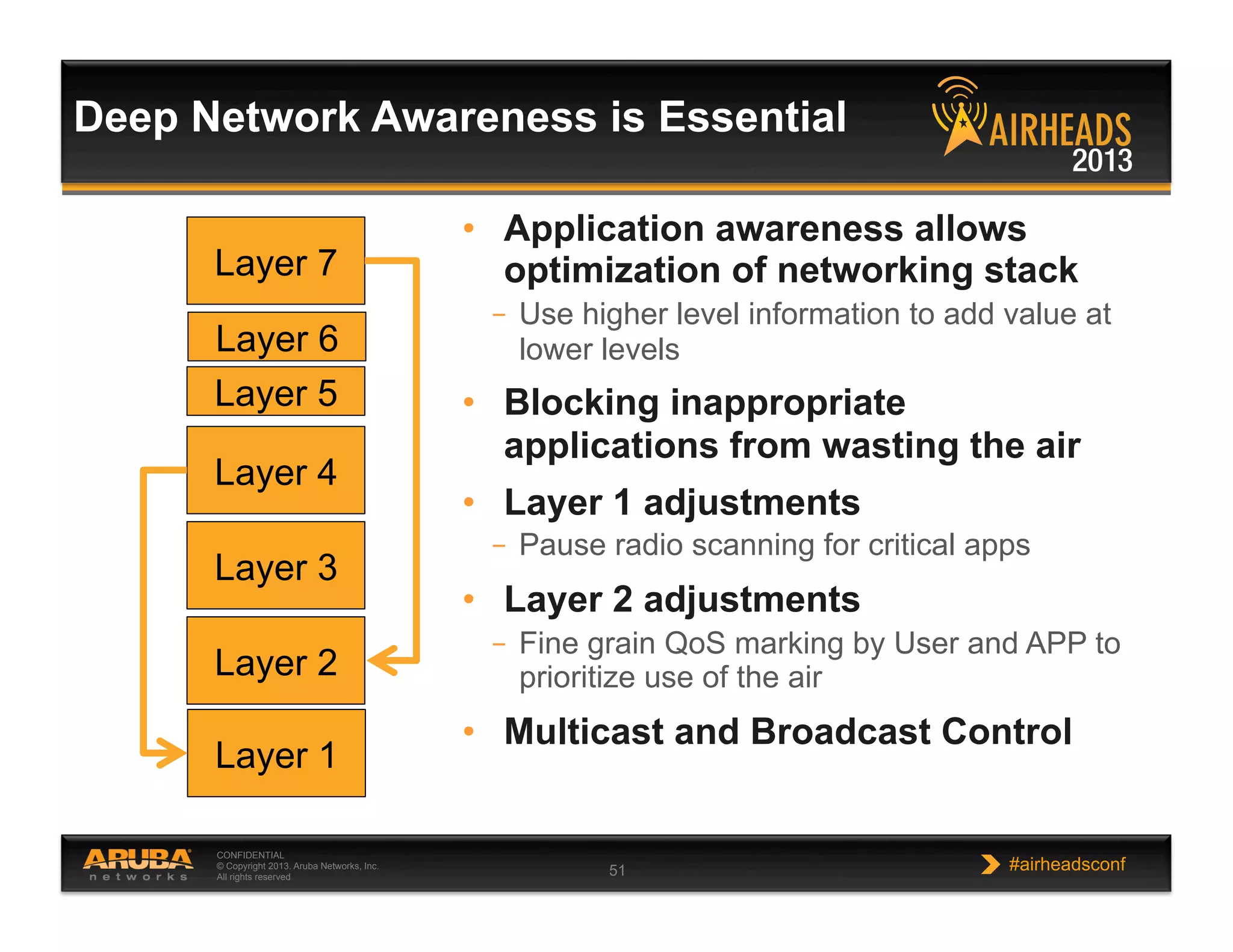
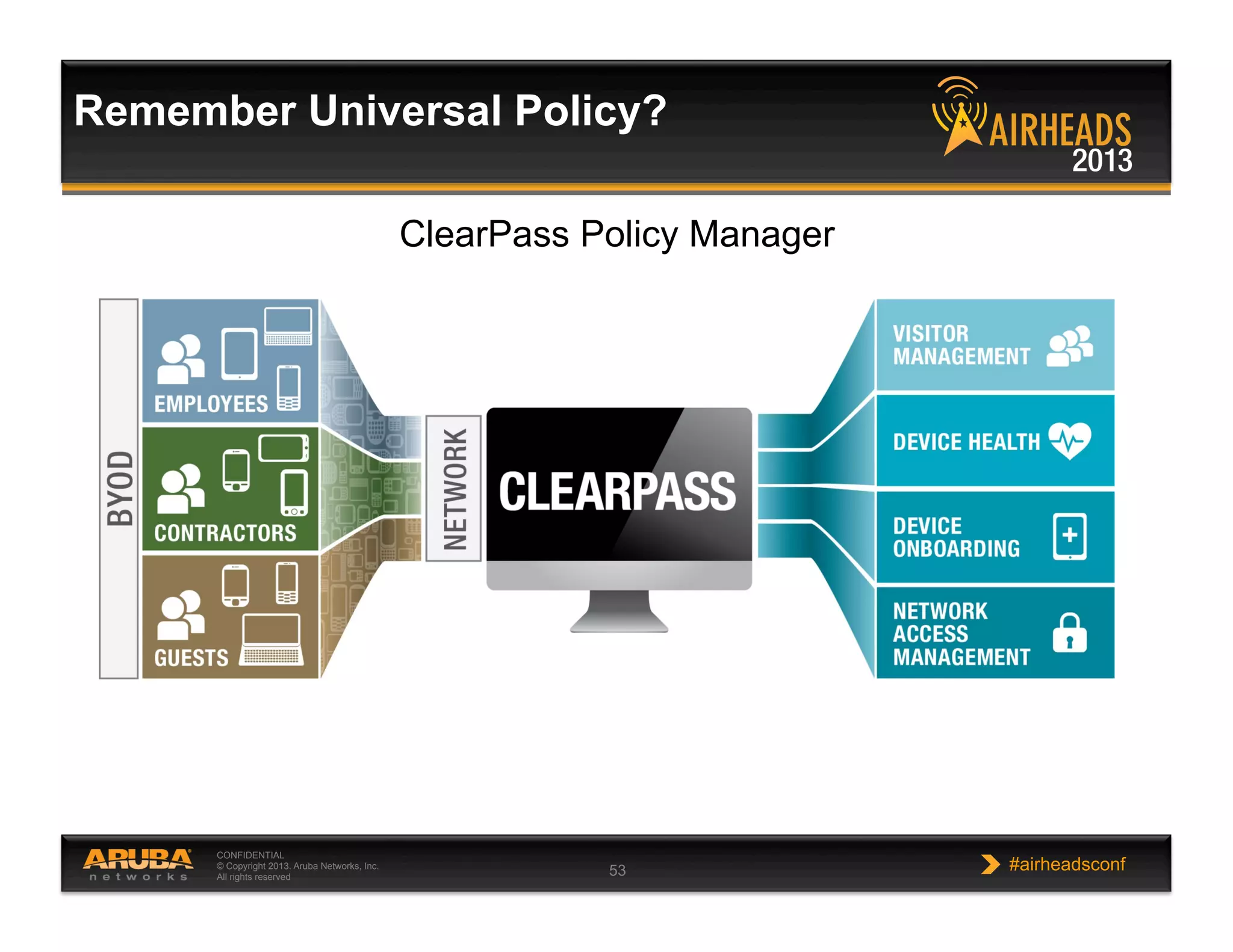
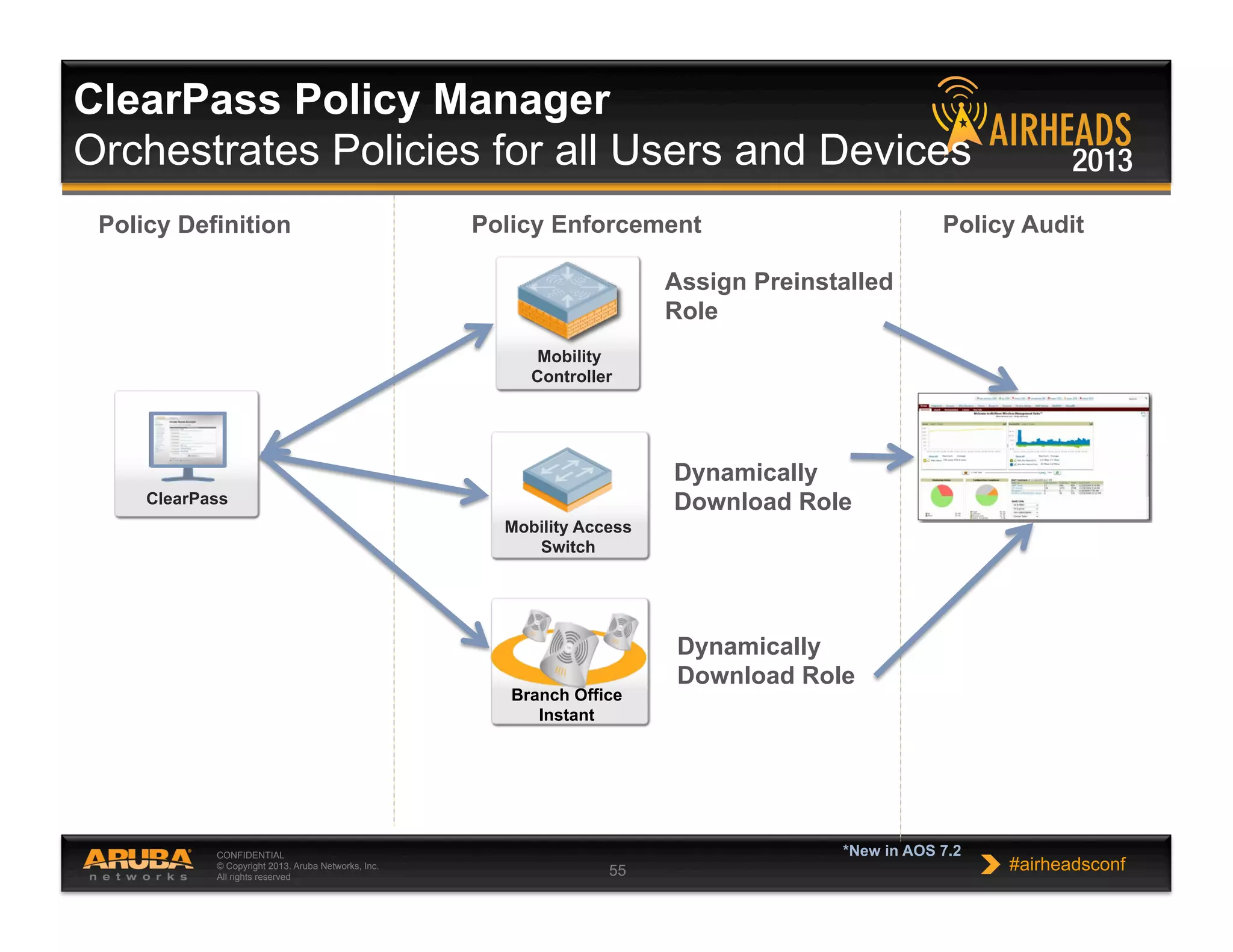
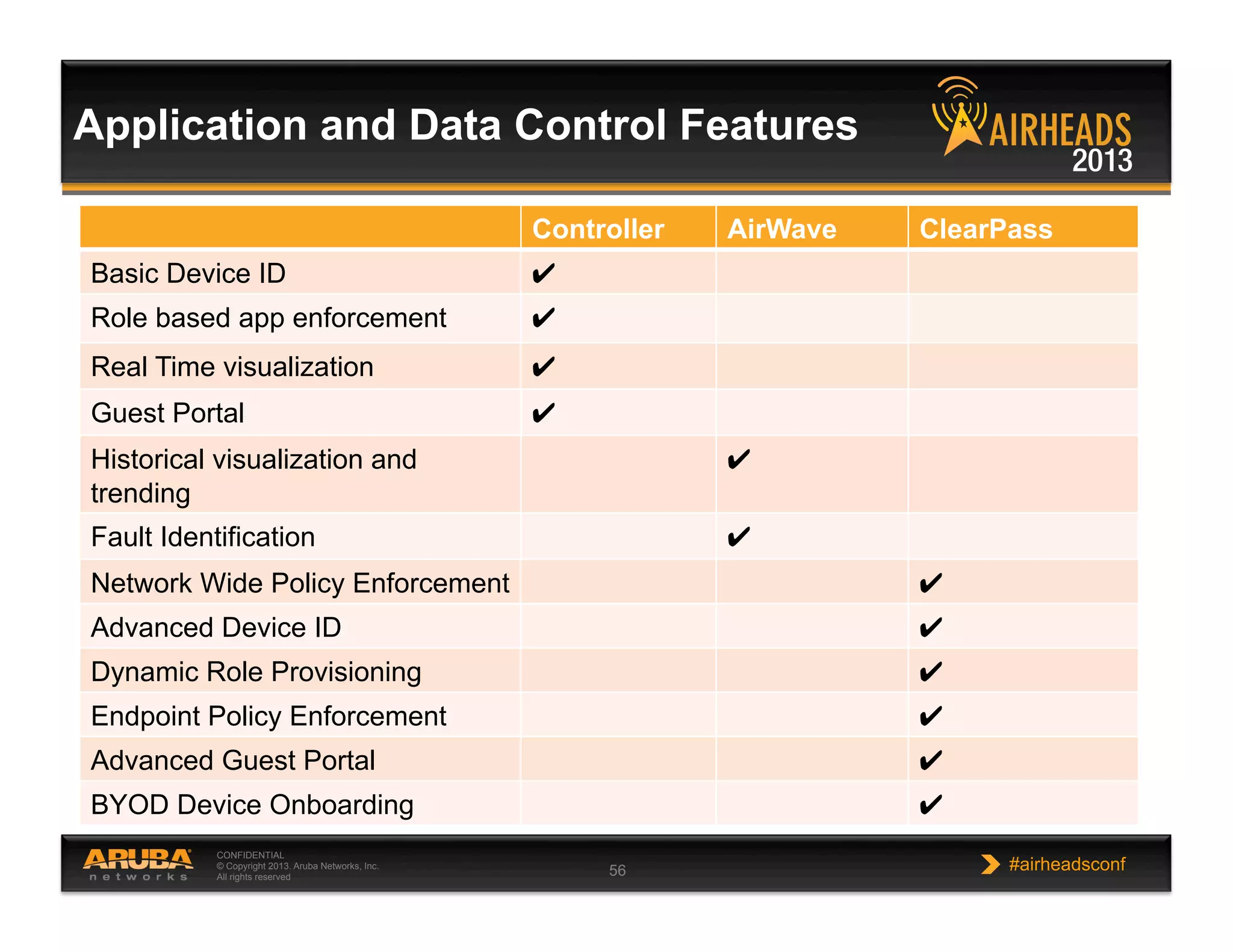
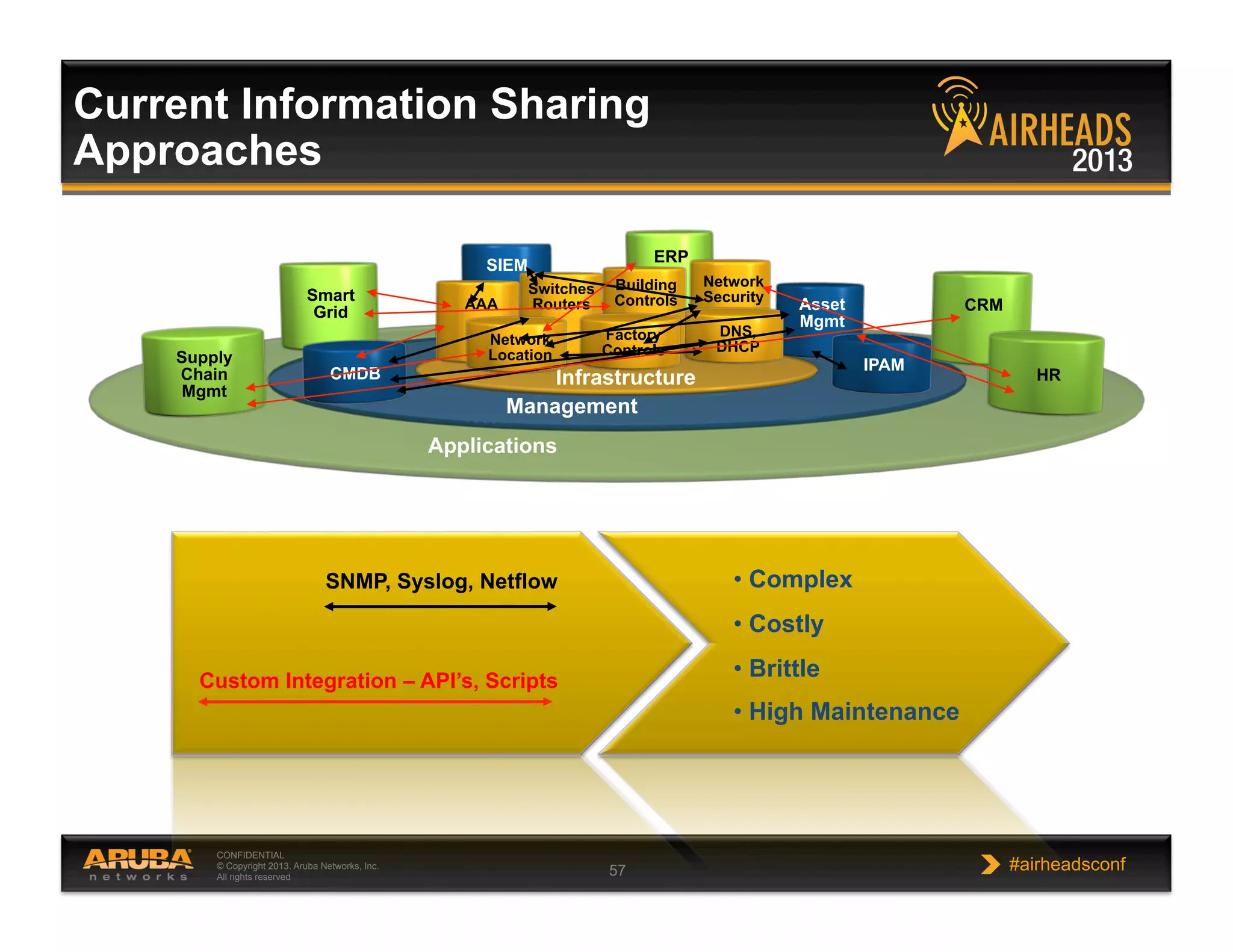
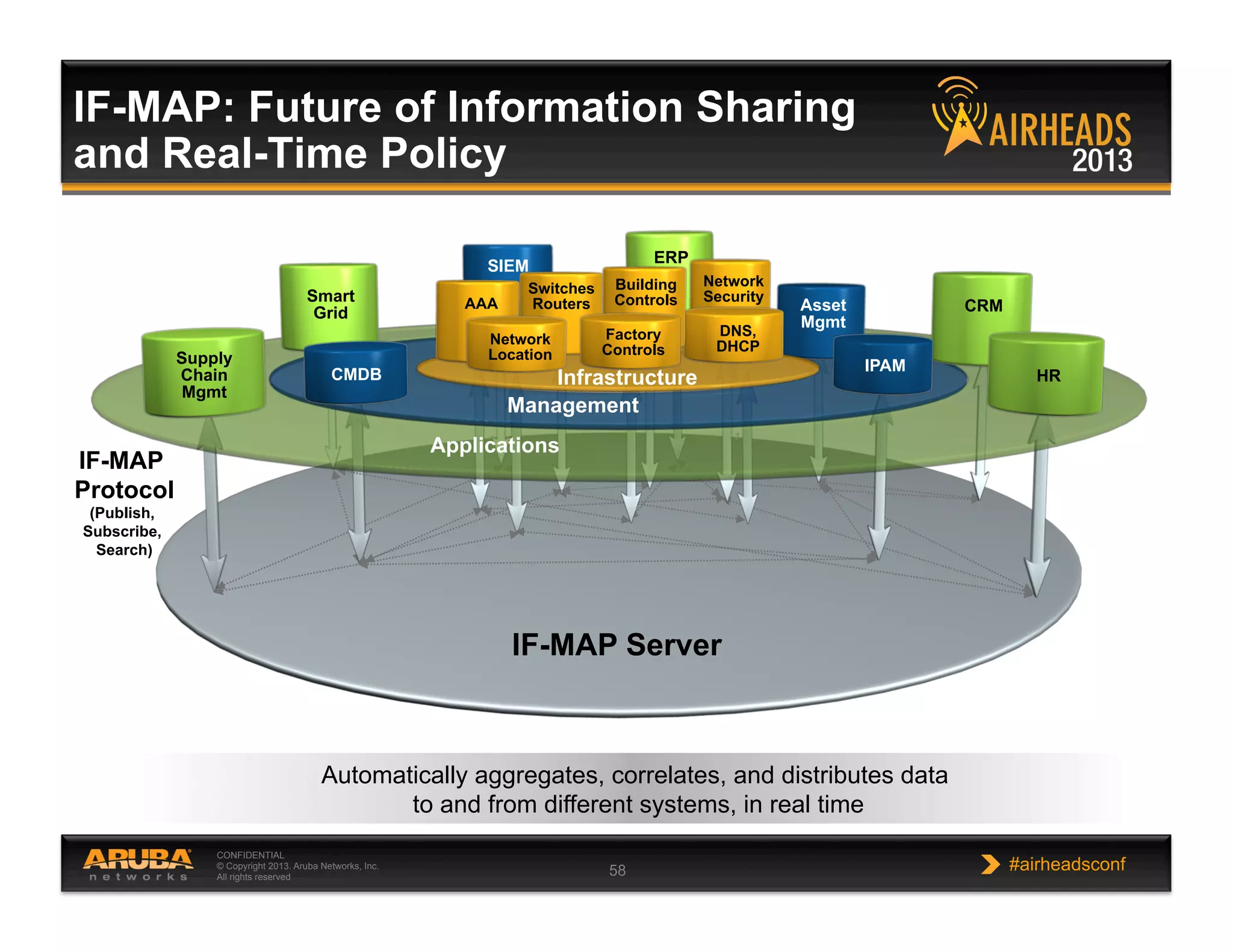
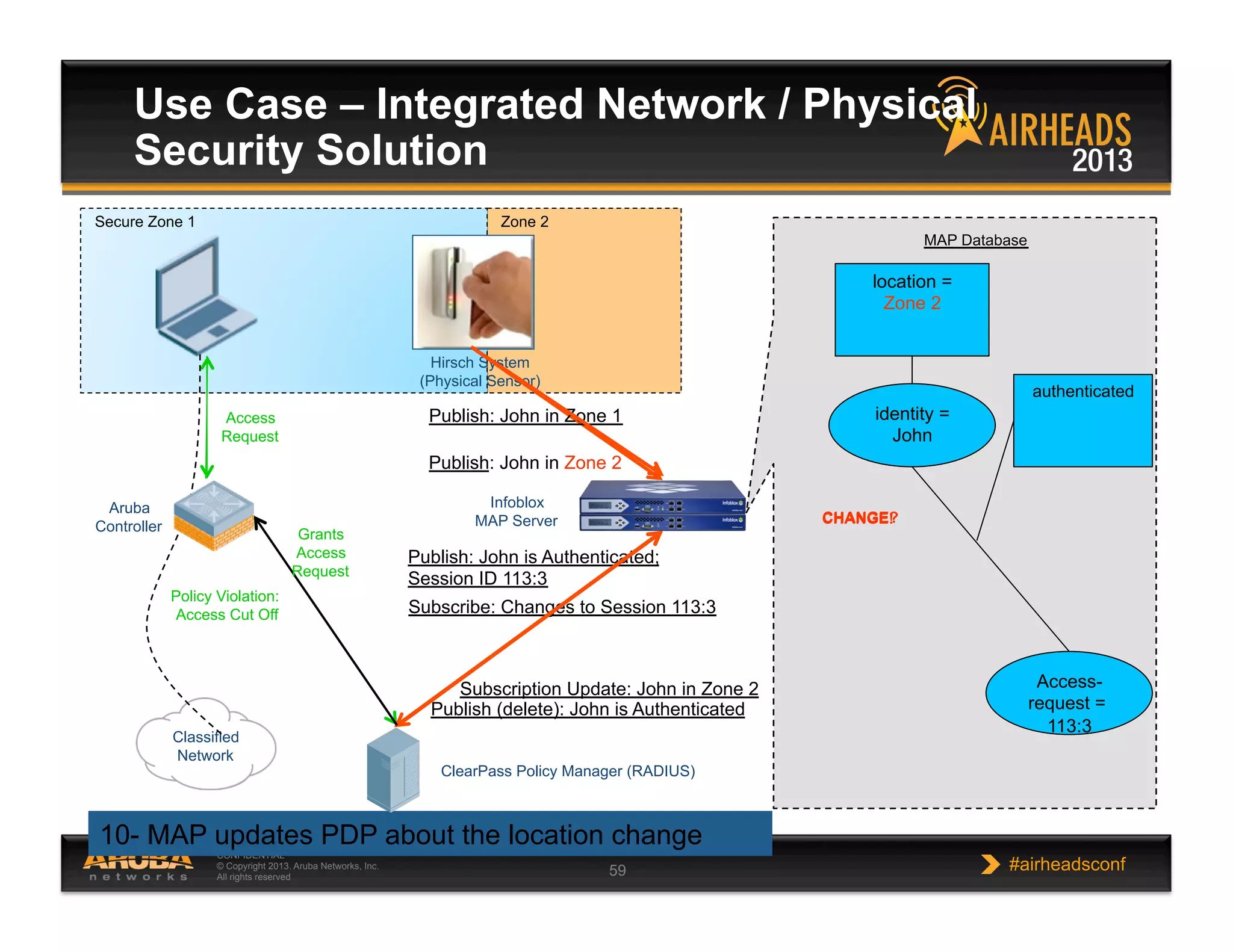
The document discusses implementing personalized network security using Aruba Networks products. It describes how traditional network security models are no longer effective due to factors like mobility and BYOD. Personalized, context-aware security which identifies users, devices, applications and locations is presented as a better approach. The Aruba security architecture is described, which uses ClearPass for policy management and enforcement across wireless, wired and VPN connections. Methods for strong authentication, device profiling, role-based access controls and guest access are covered to implement personalized security network-wide.