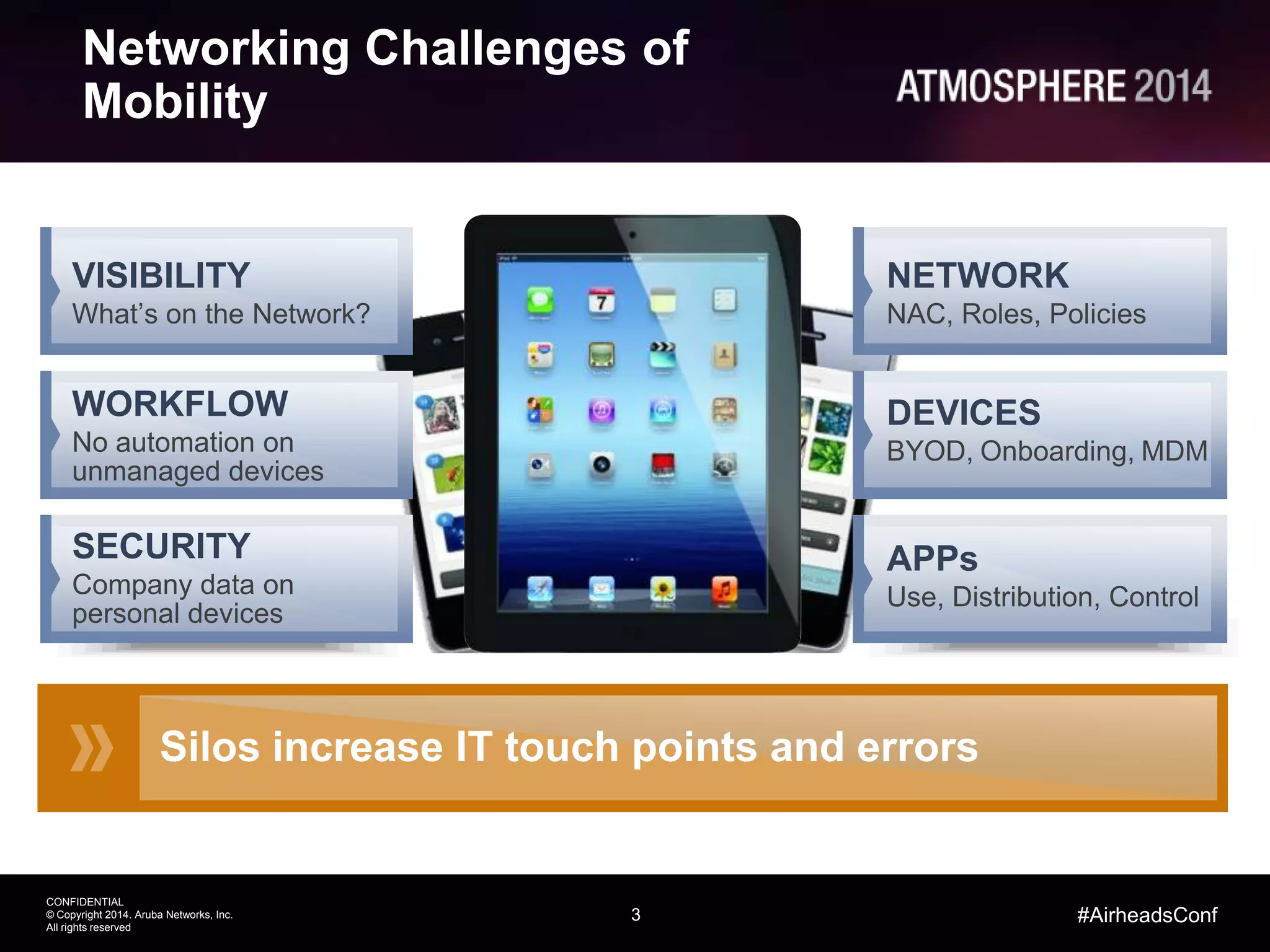
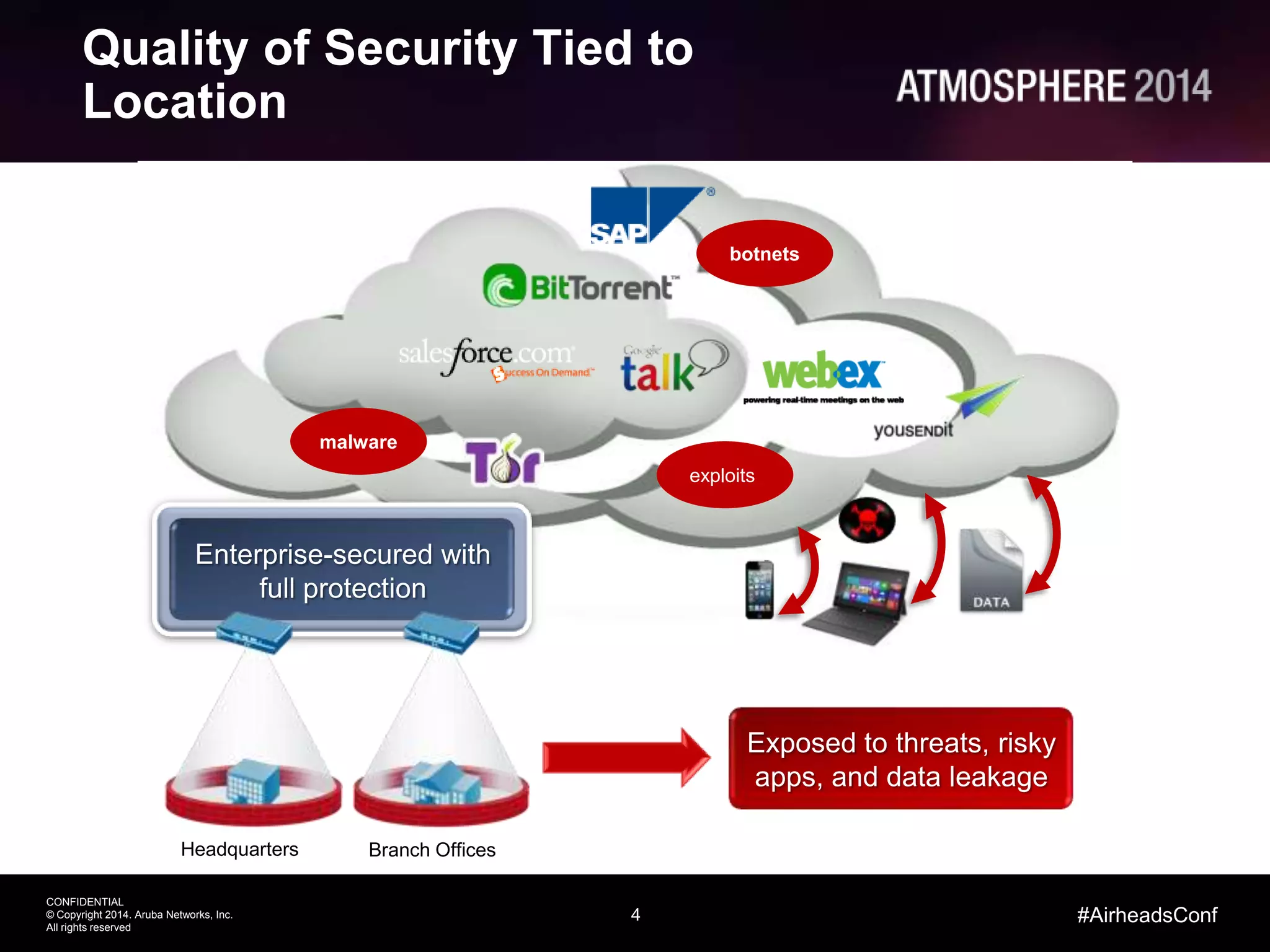
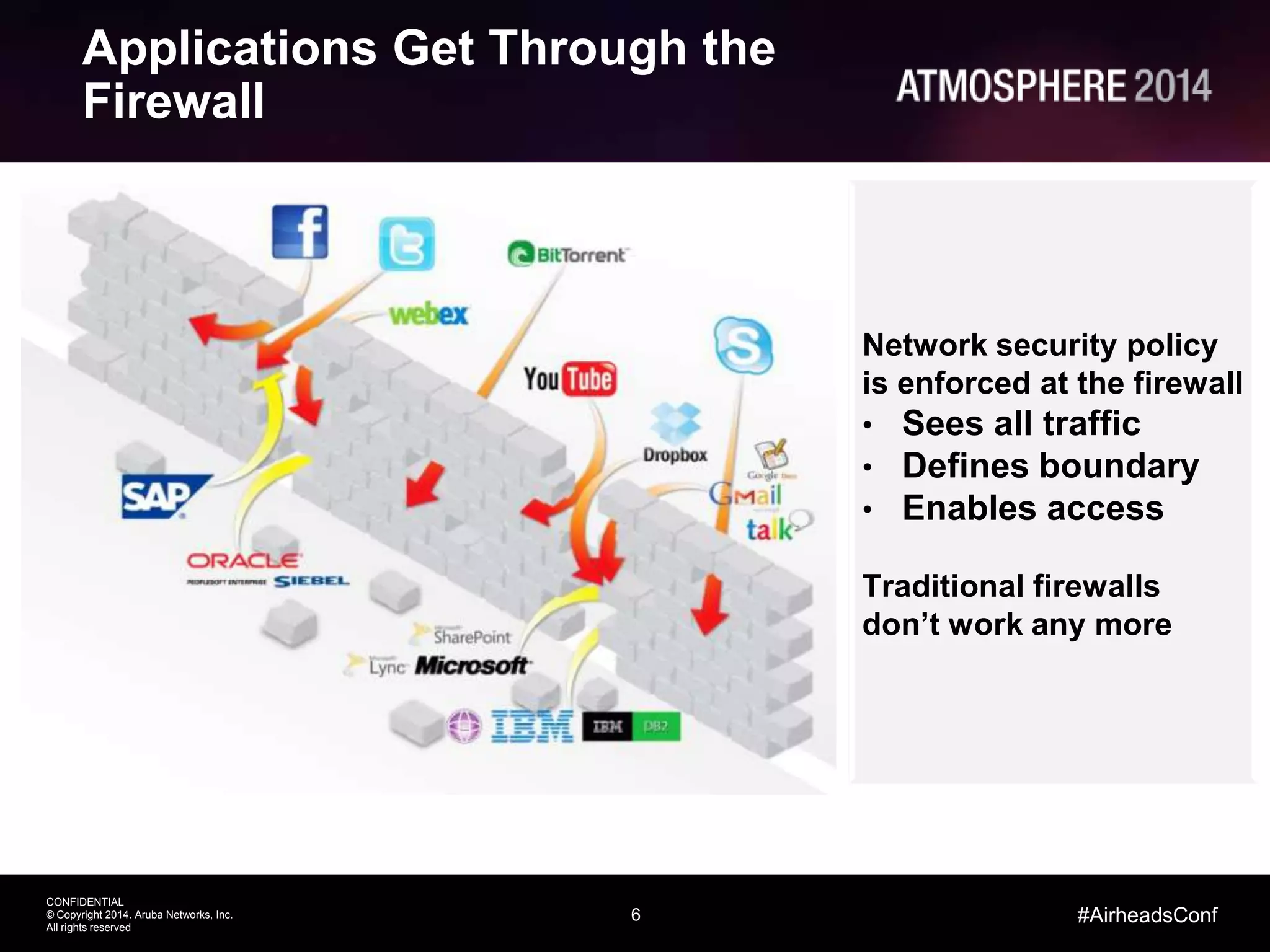
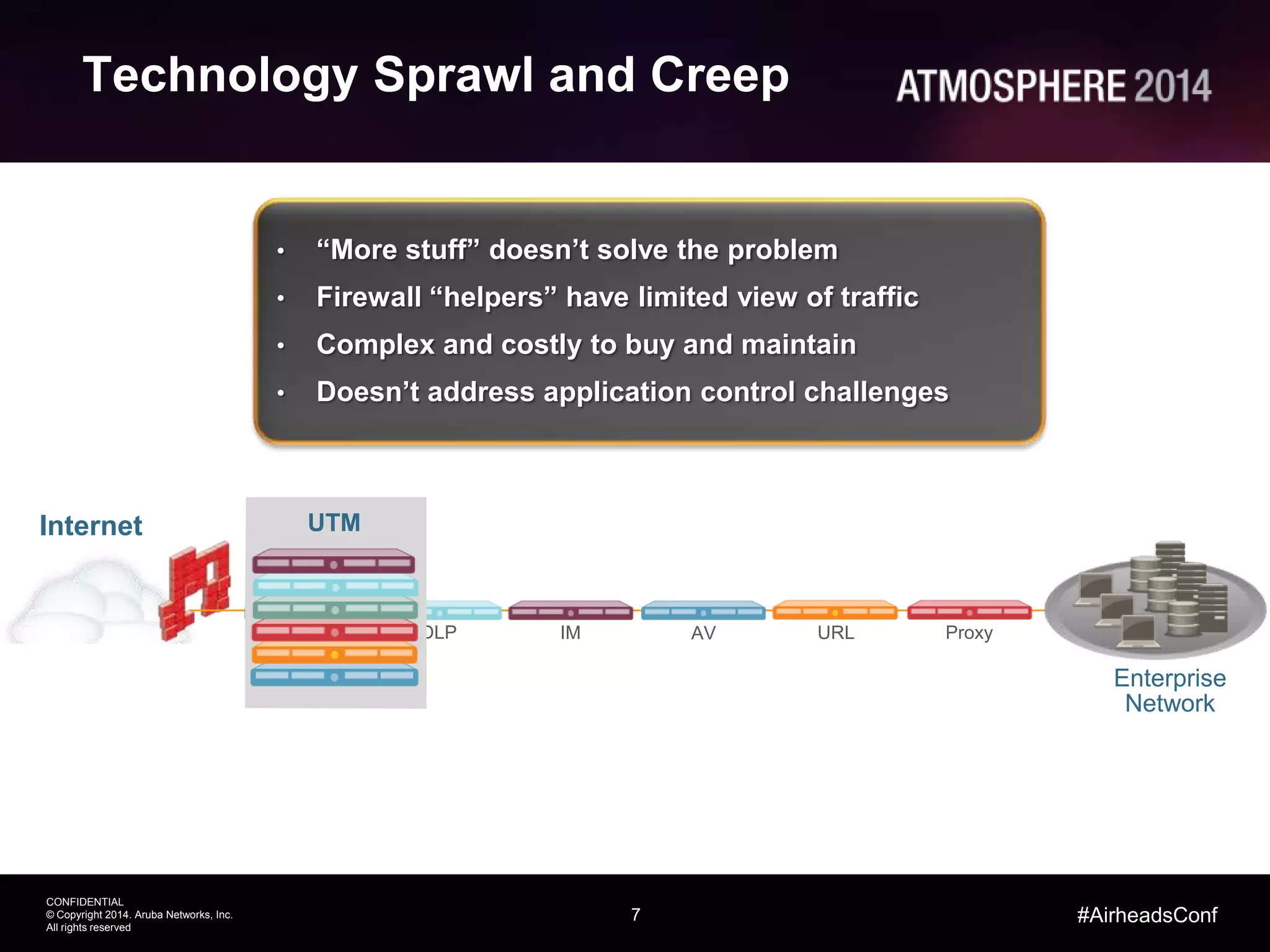
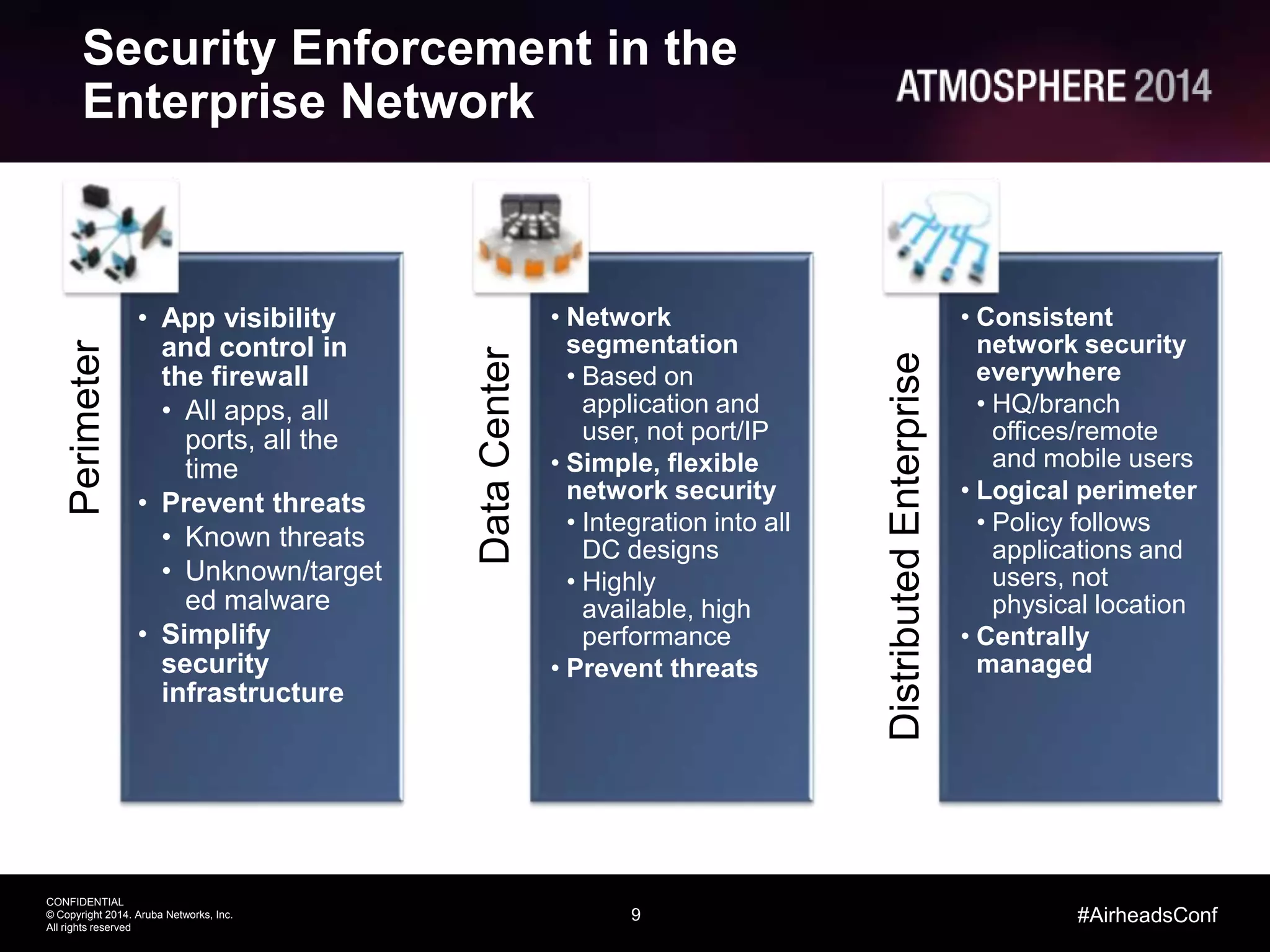
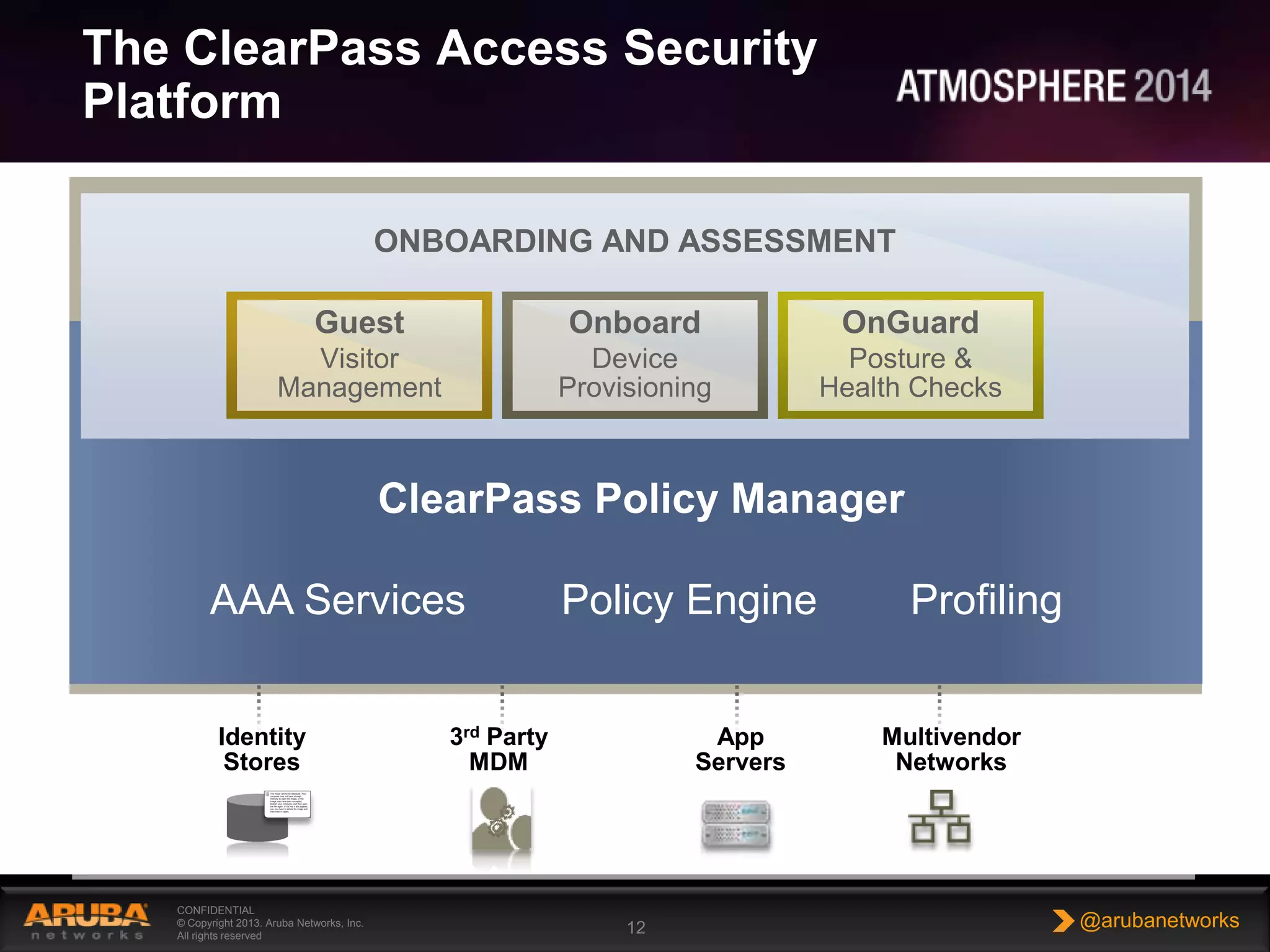
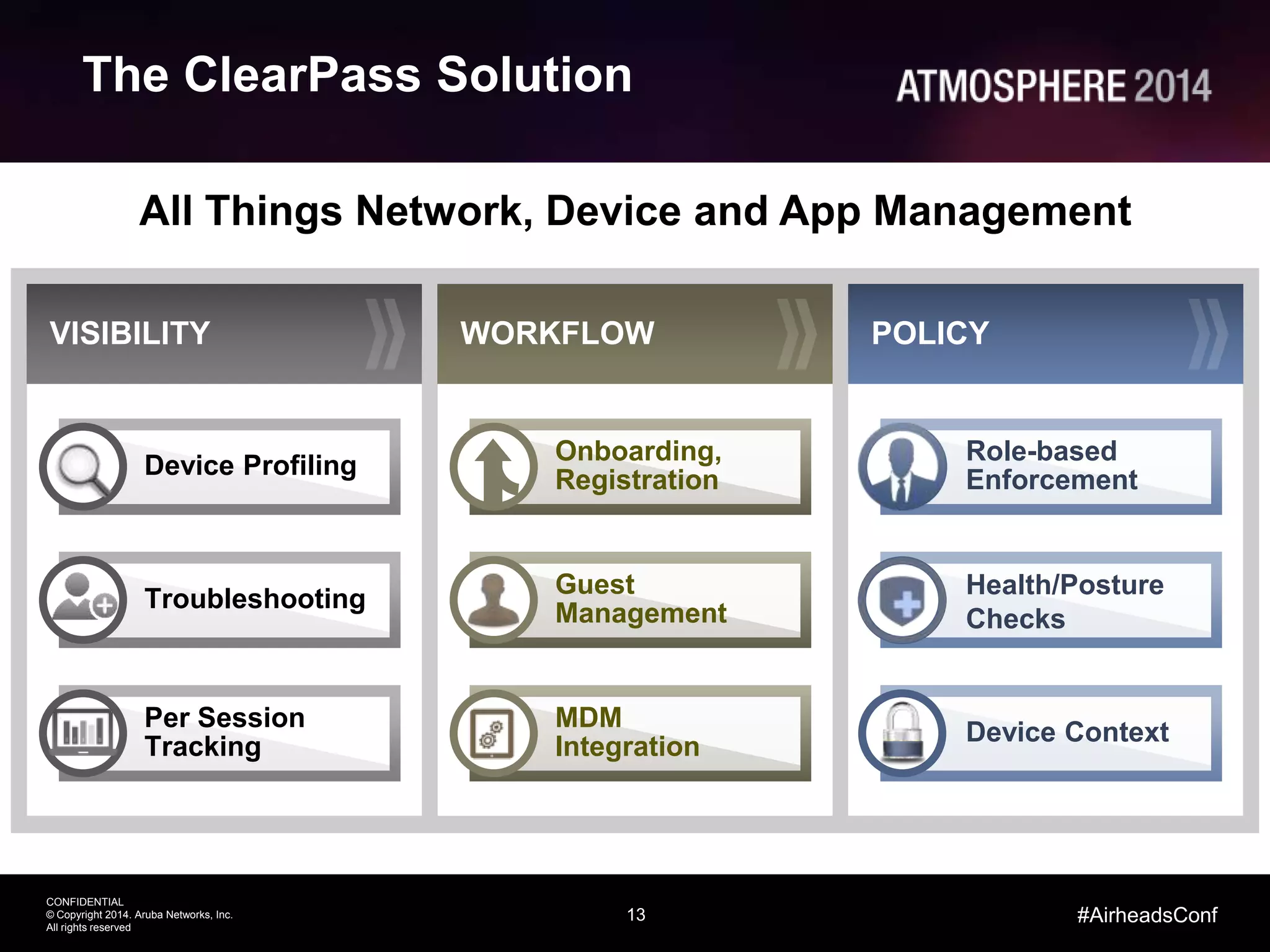
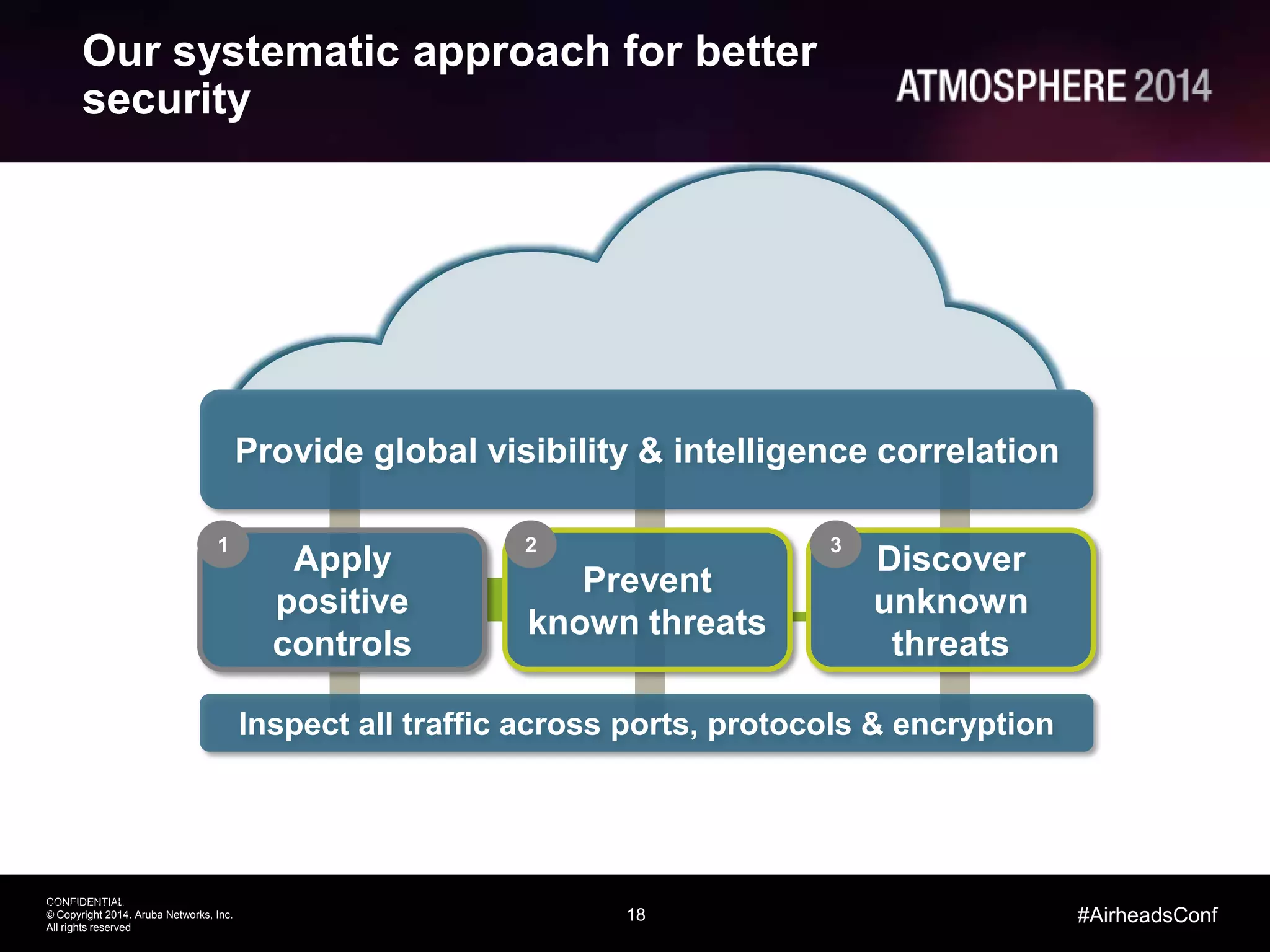
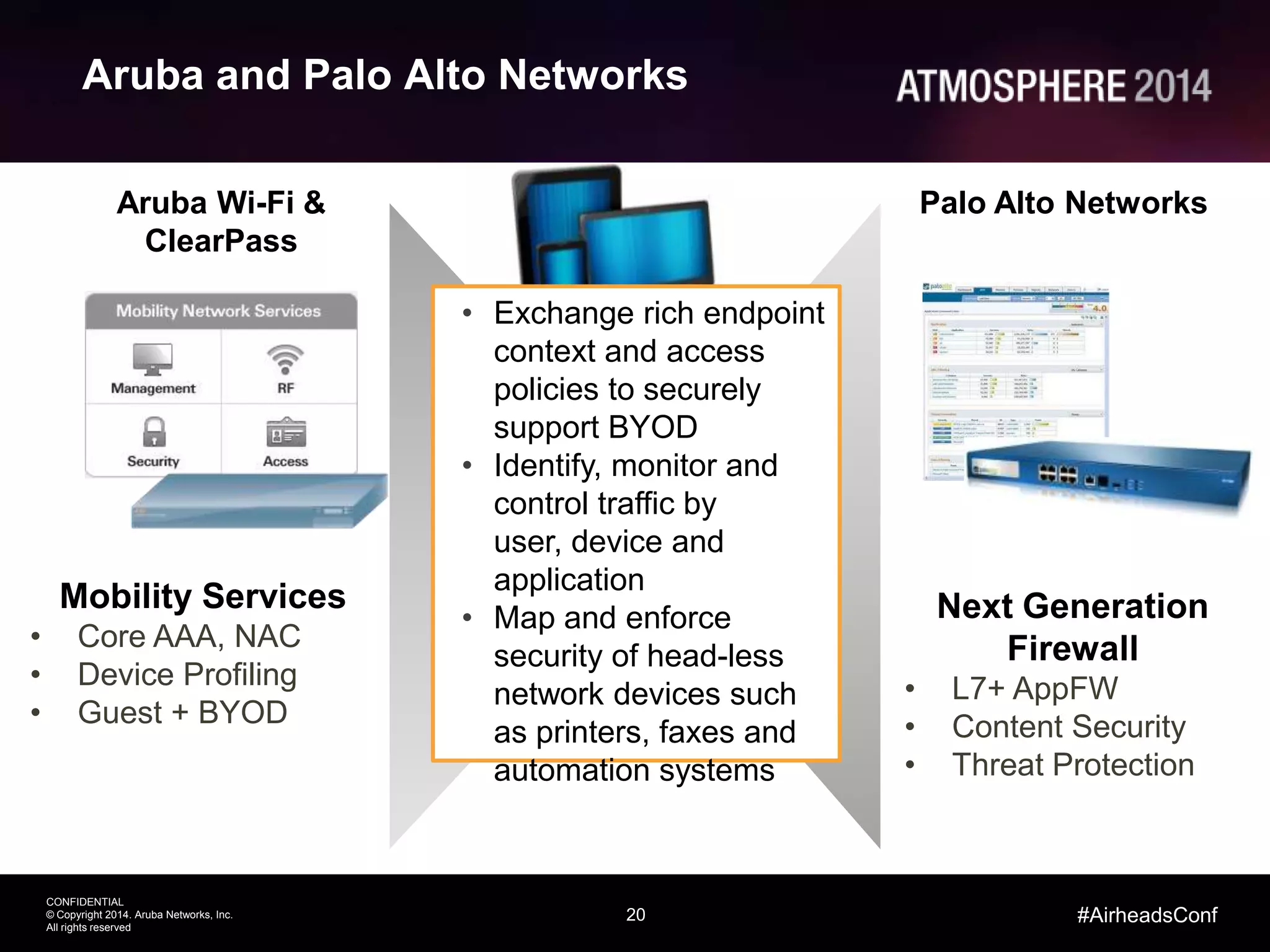
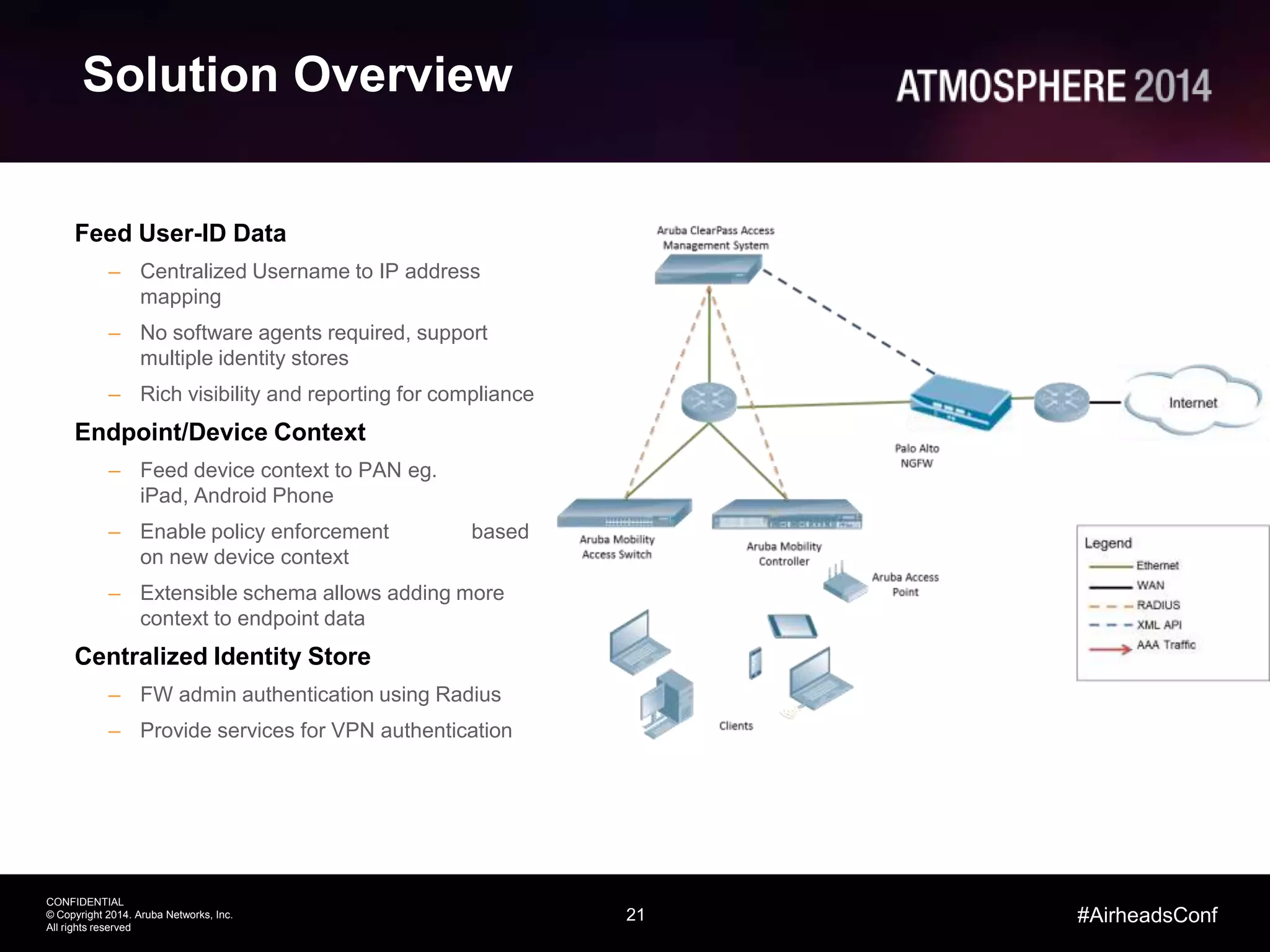
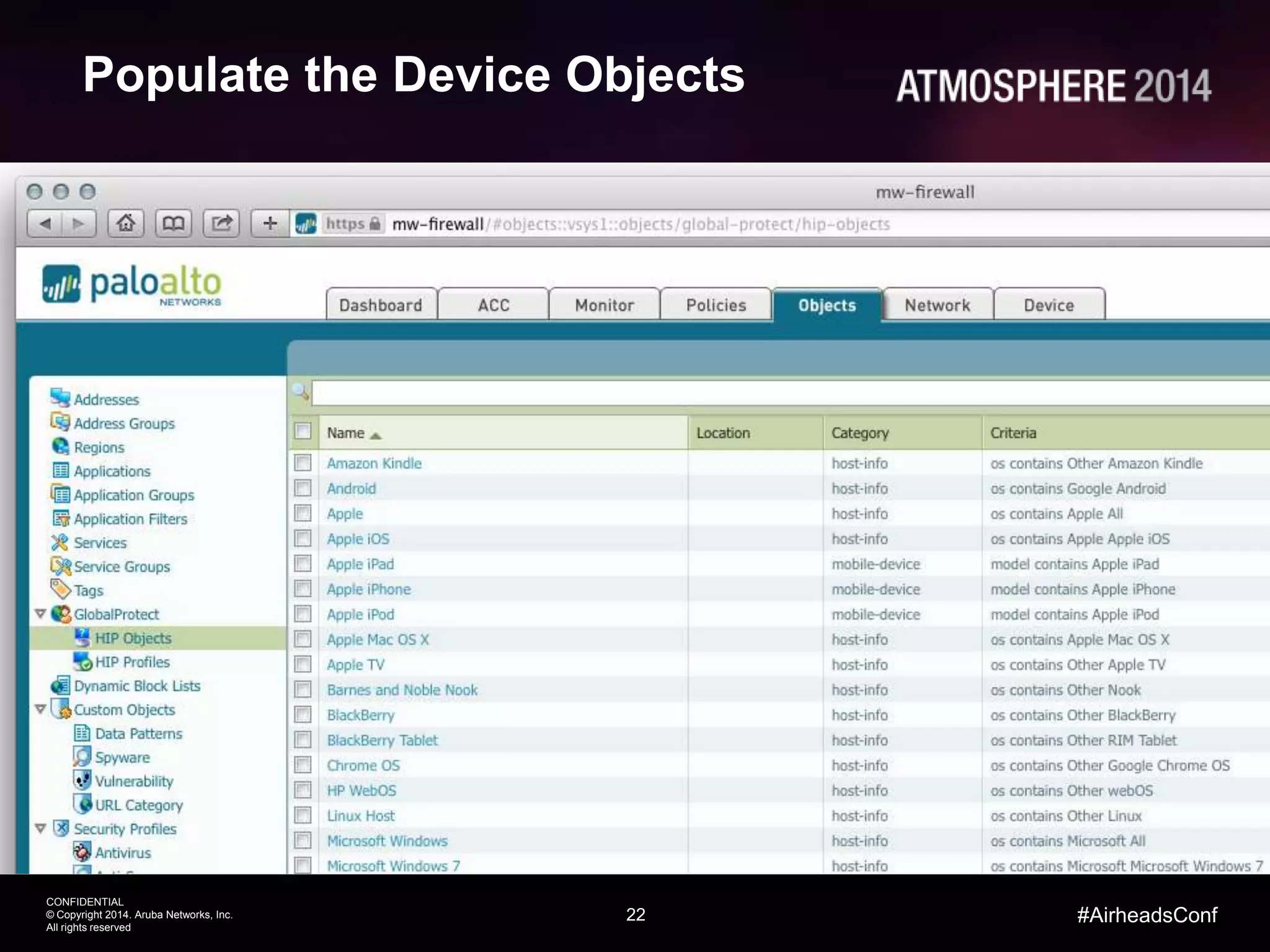
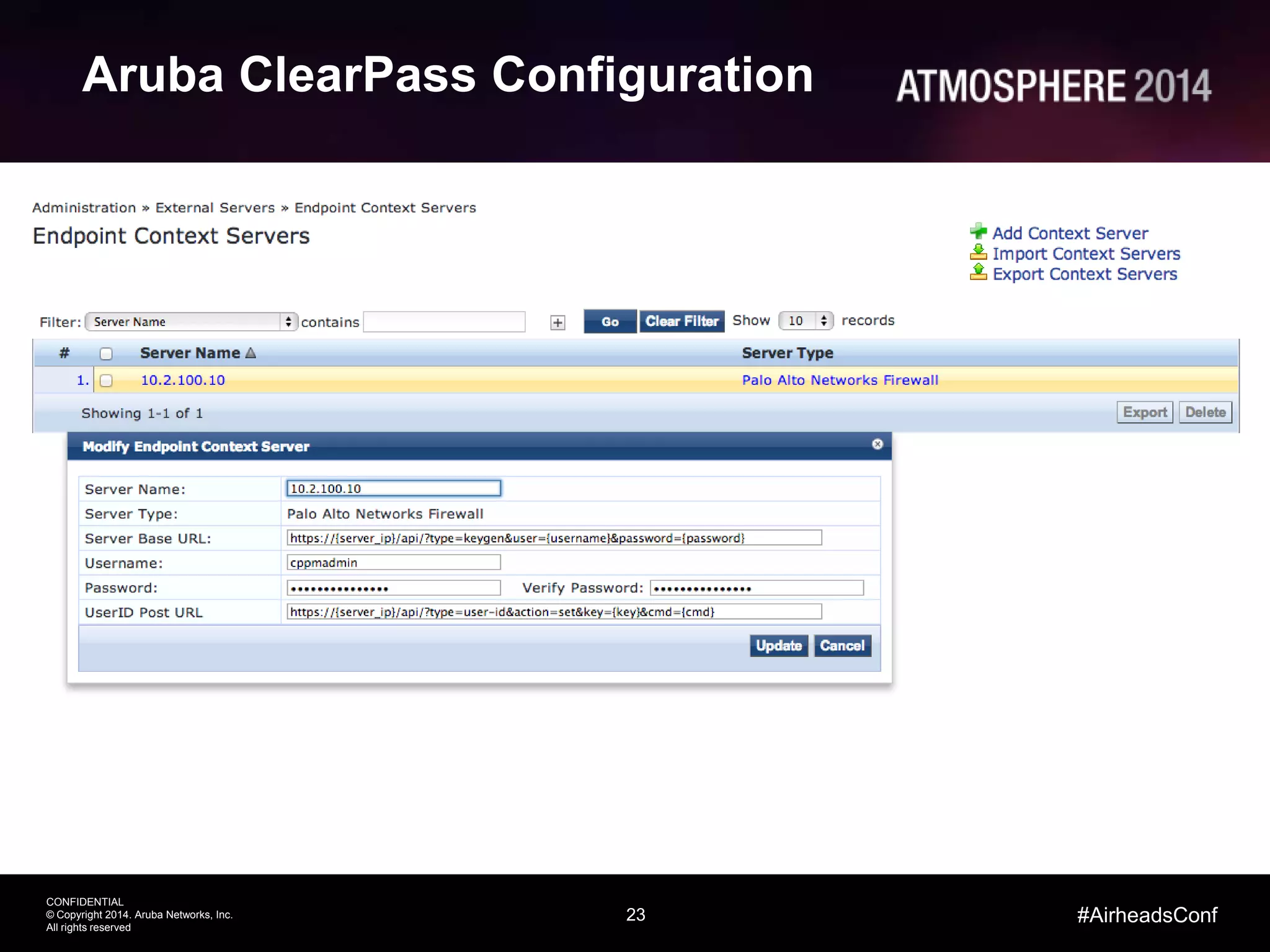
This document outlines the challenges and solutions associated with secure enterprise mobility, specifically focusing on BYOD and the evolving threat landscape. It discusses the limitations of traditional firewalls and presents a systematic approach to network security that emphasizes visibility, control, and threat prevention through advanced tools like the ClearPass platform and Palo Alto Networks next-generation firewalls. Additionally, it highlights the benefits of enhanced visibility, security, and performance in network management for a mobile workforce.