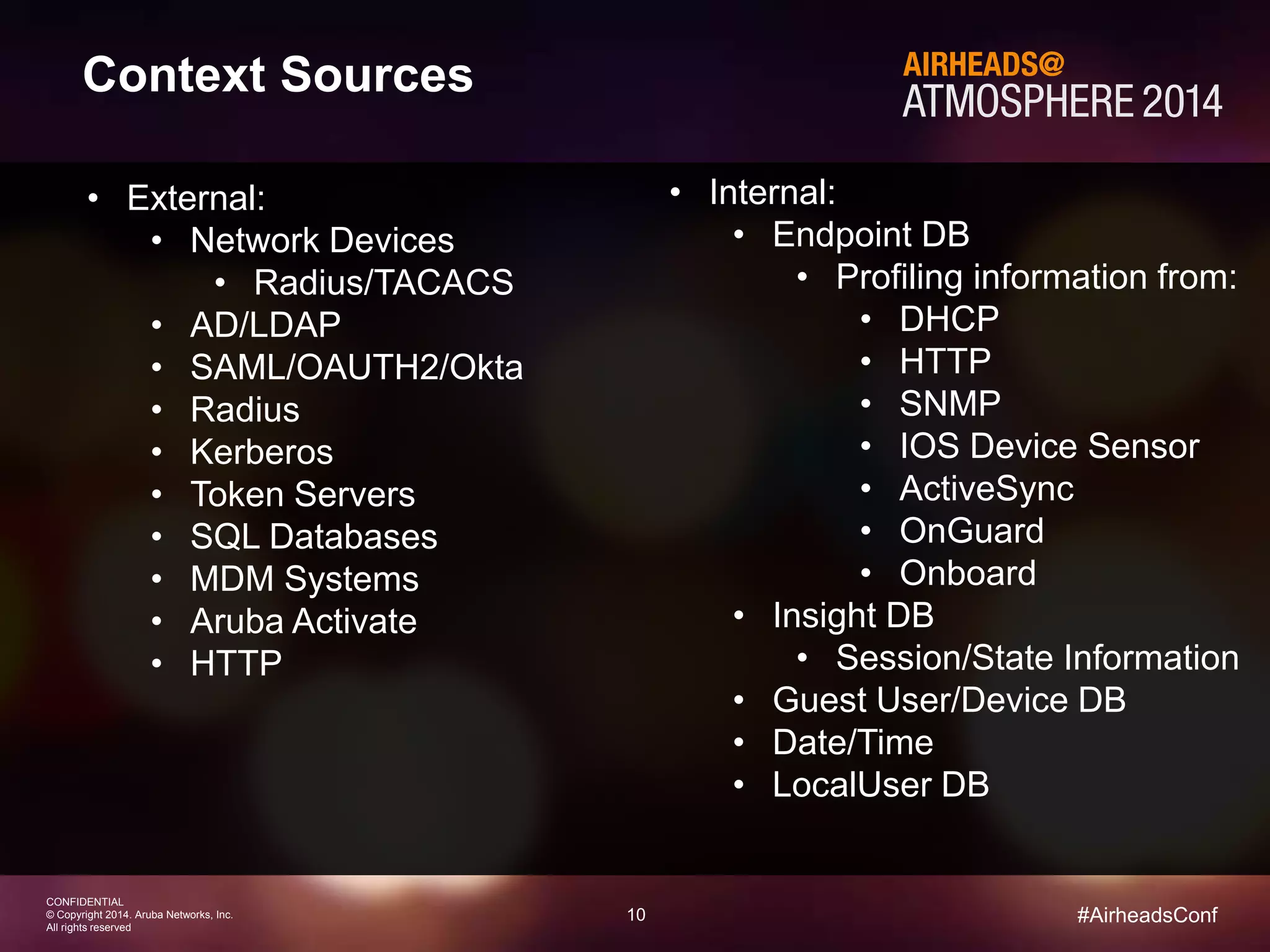
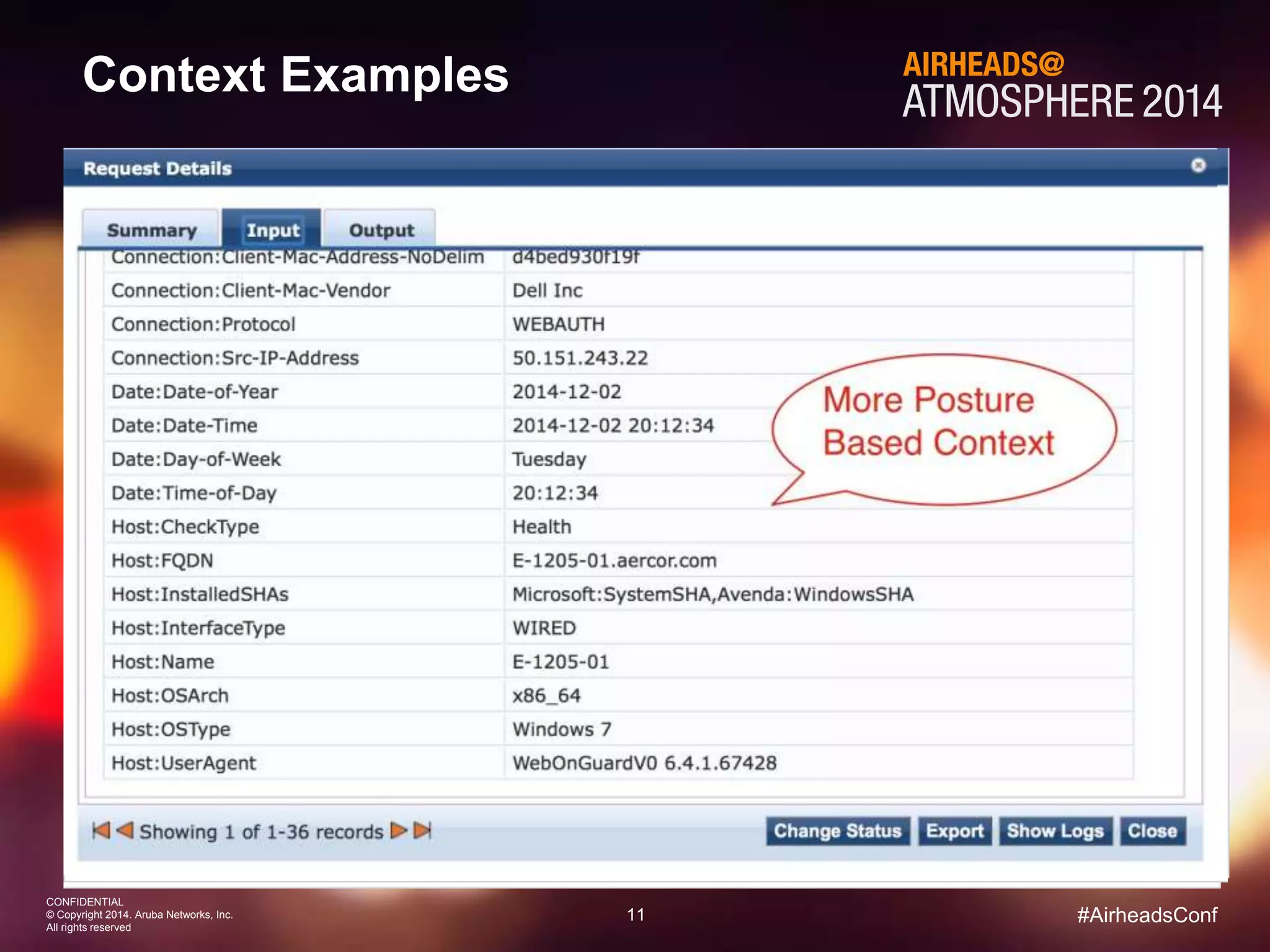
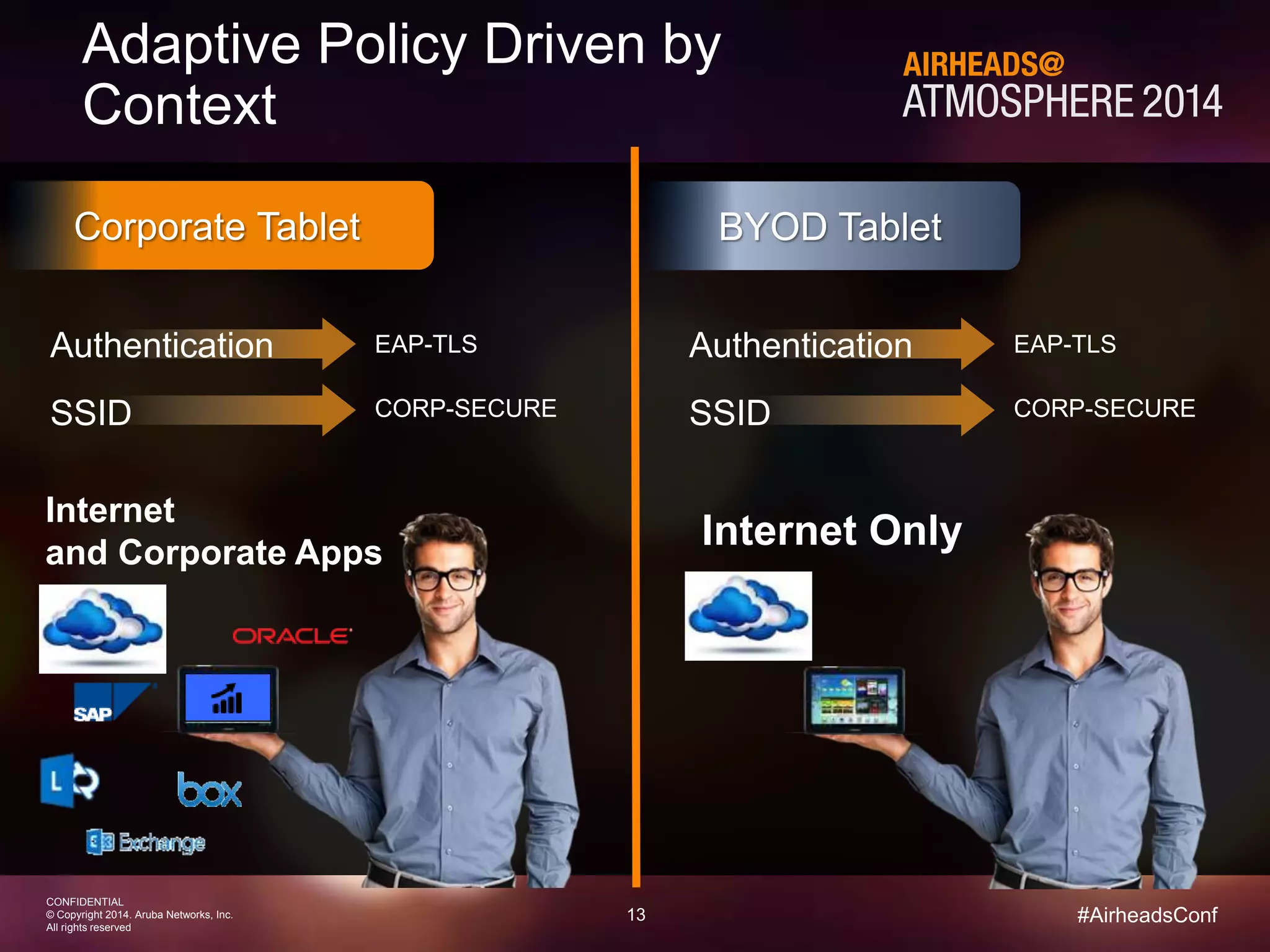
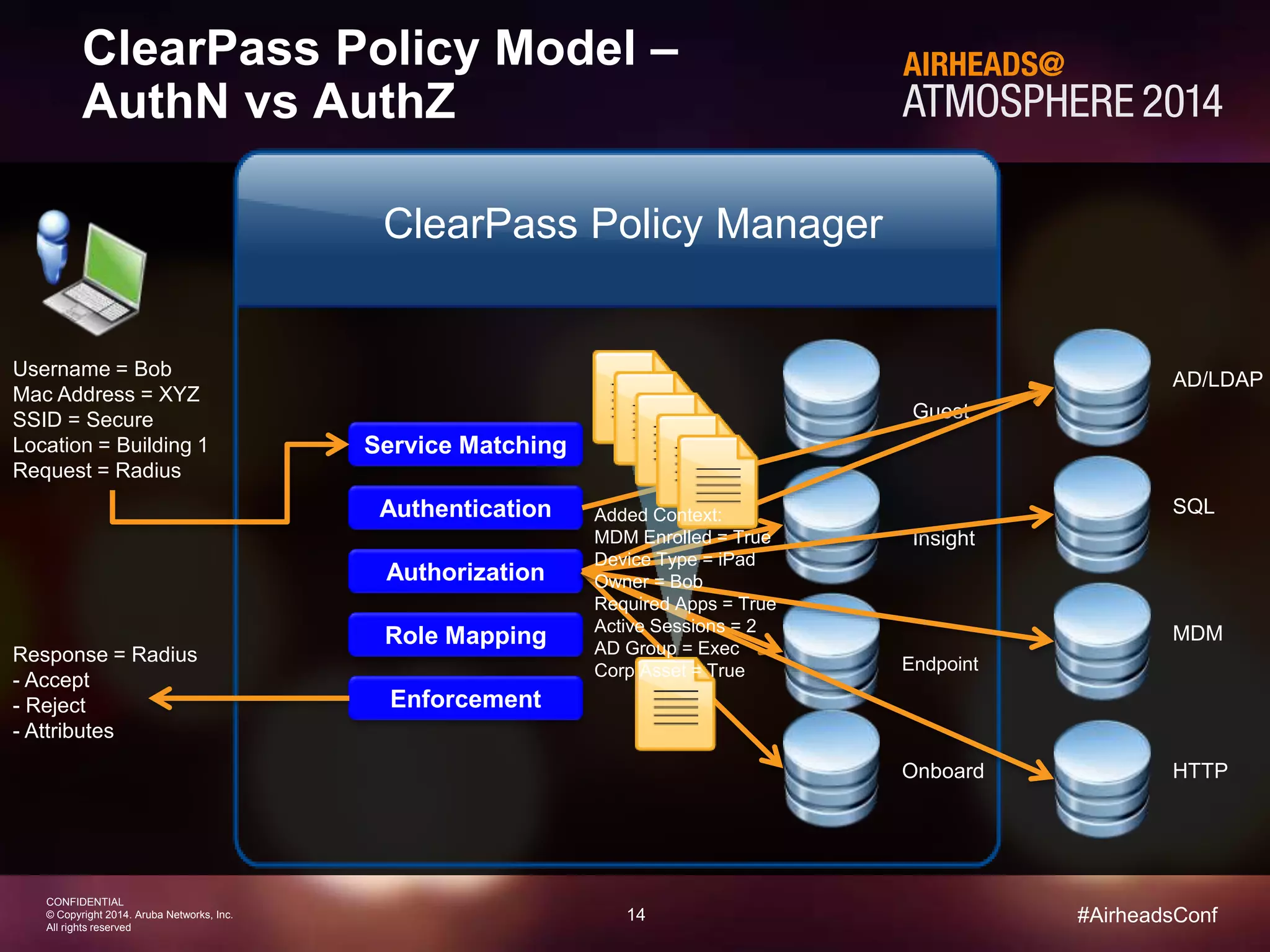
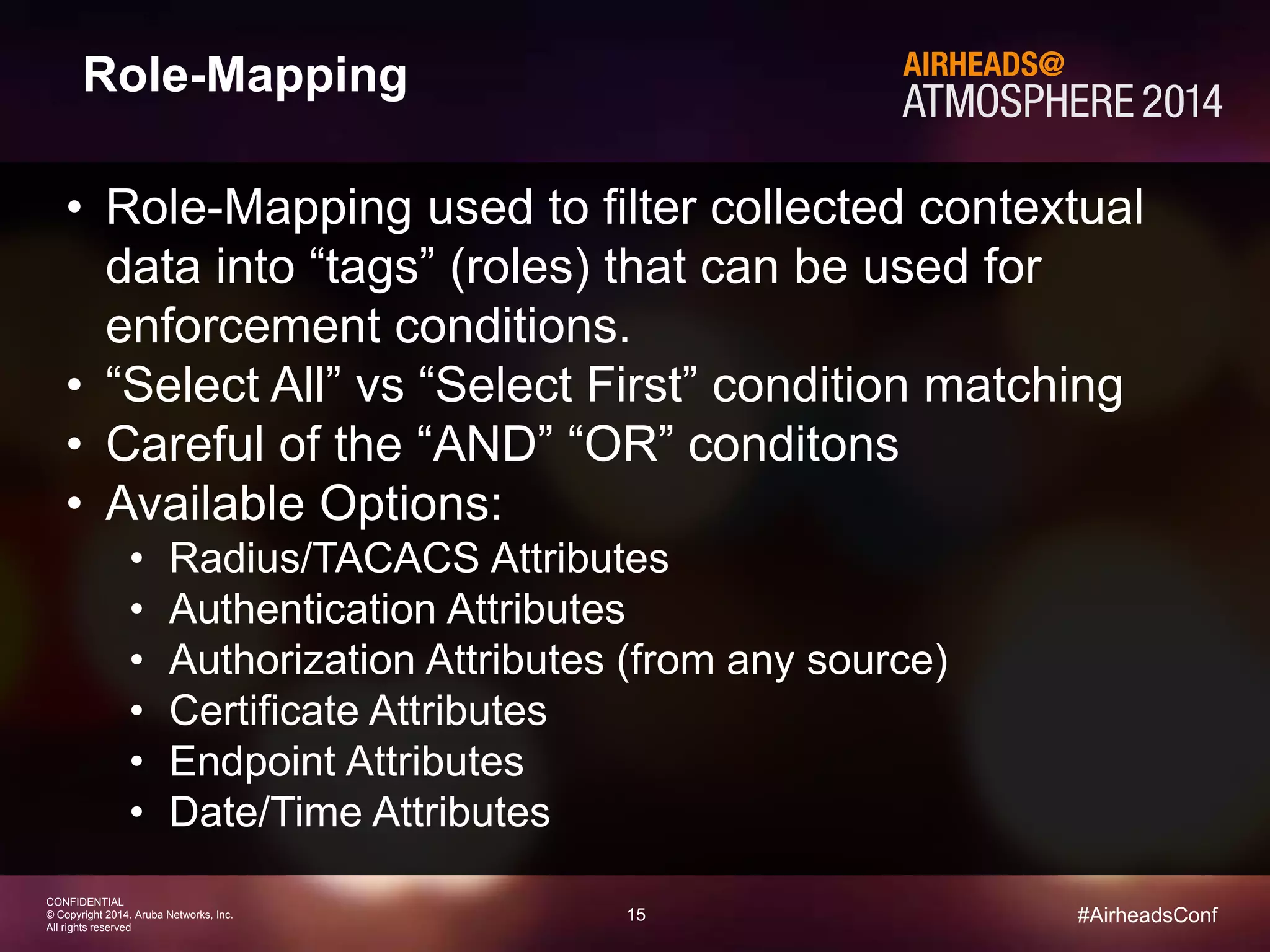
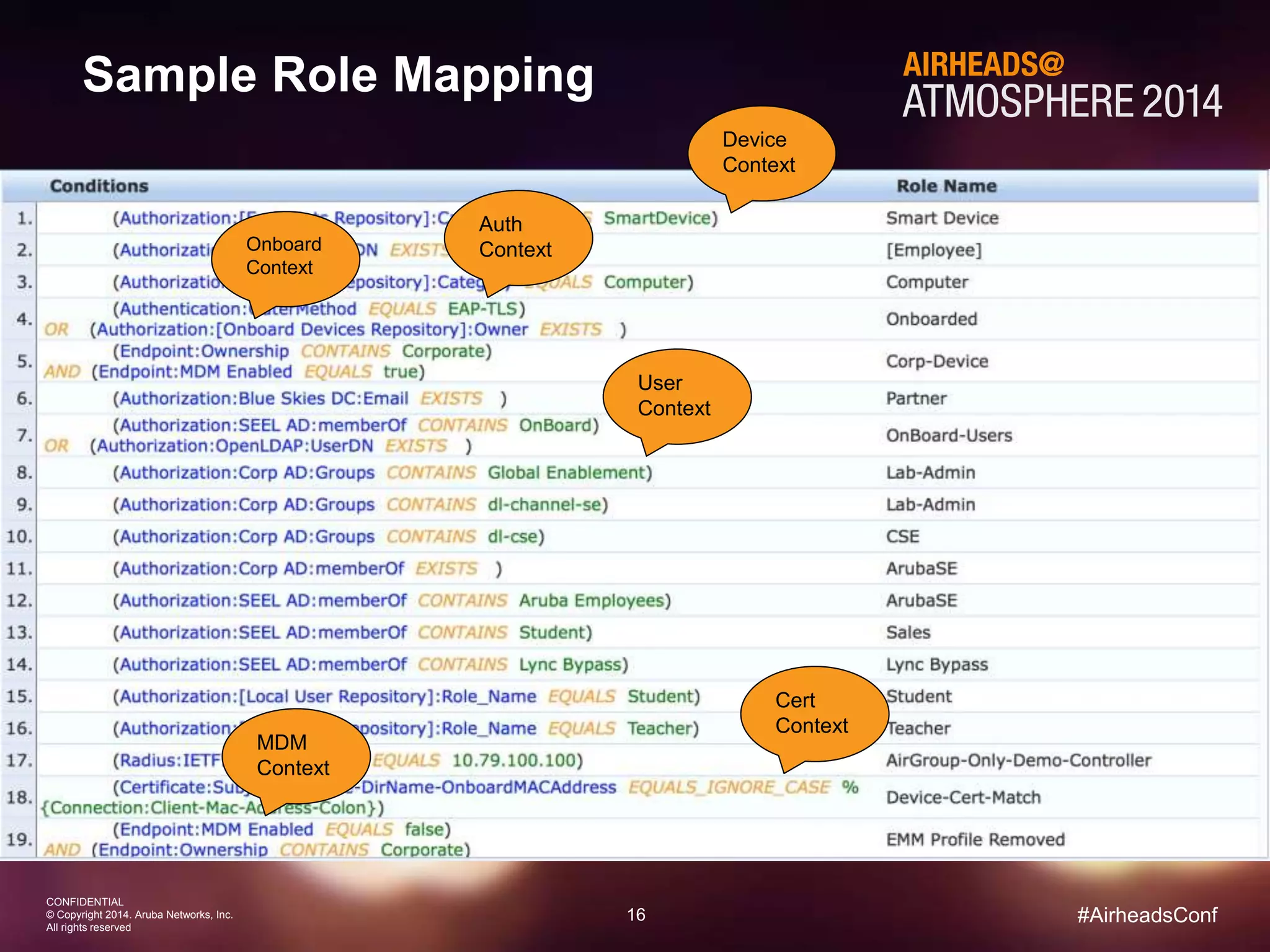
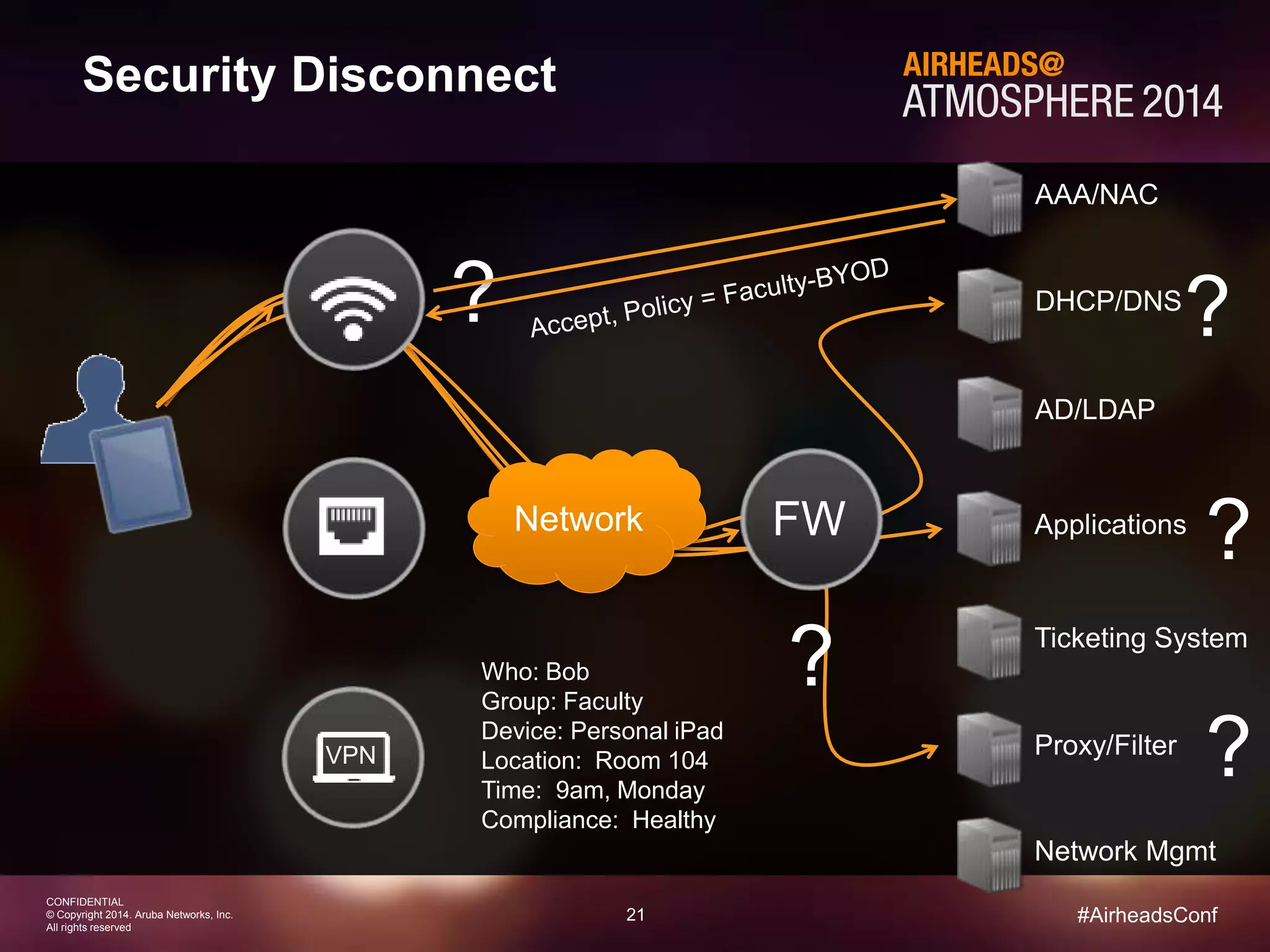
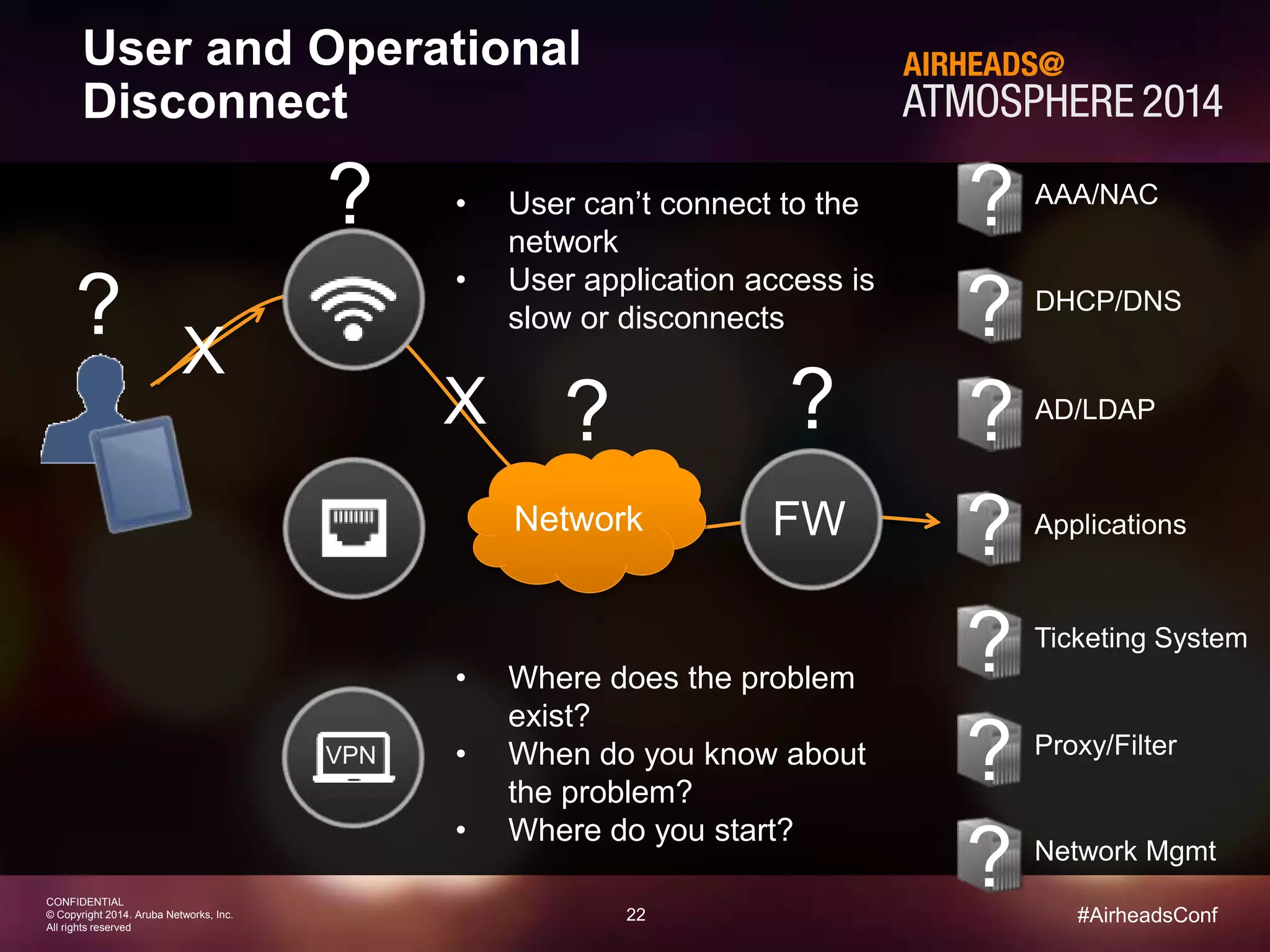
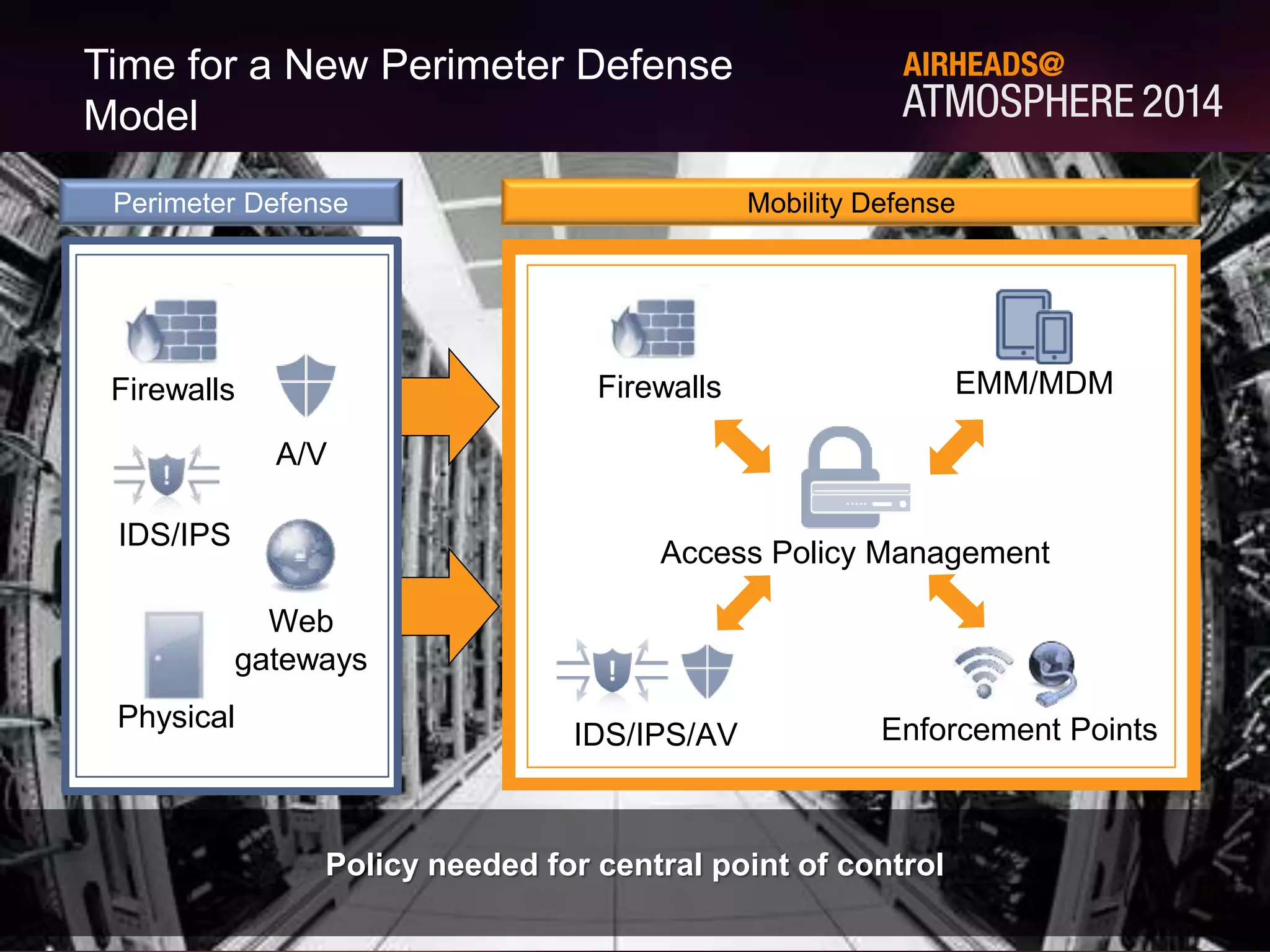
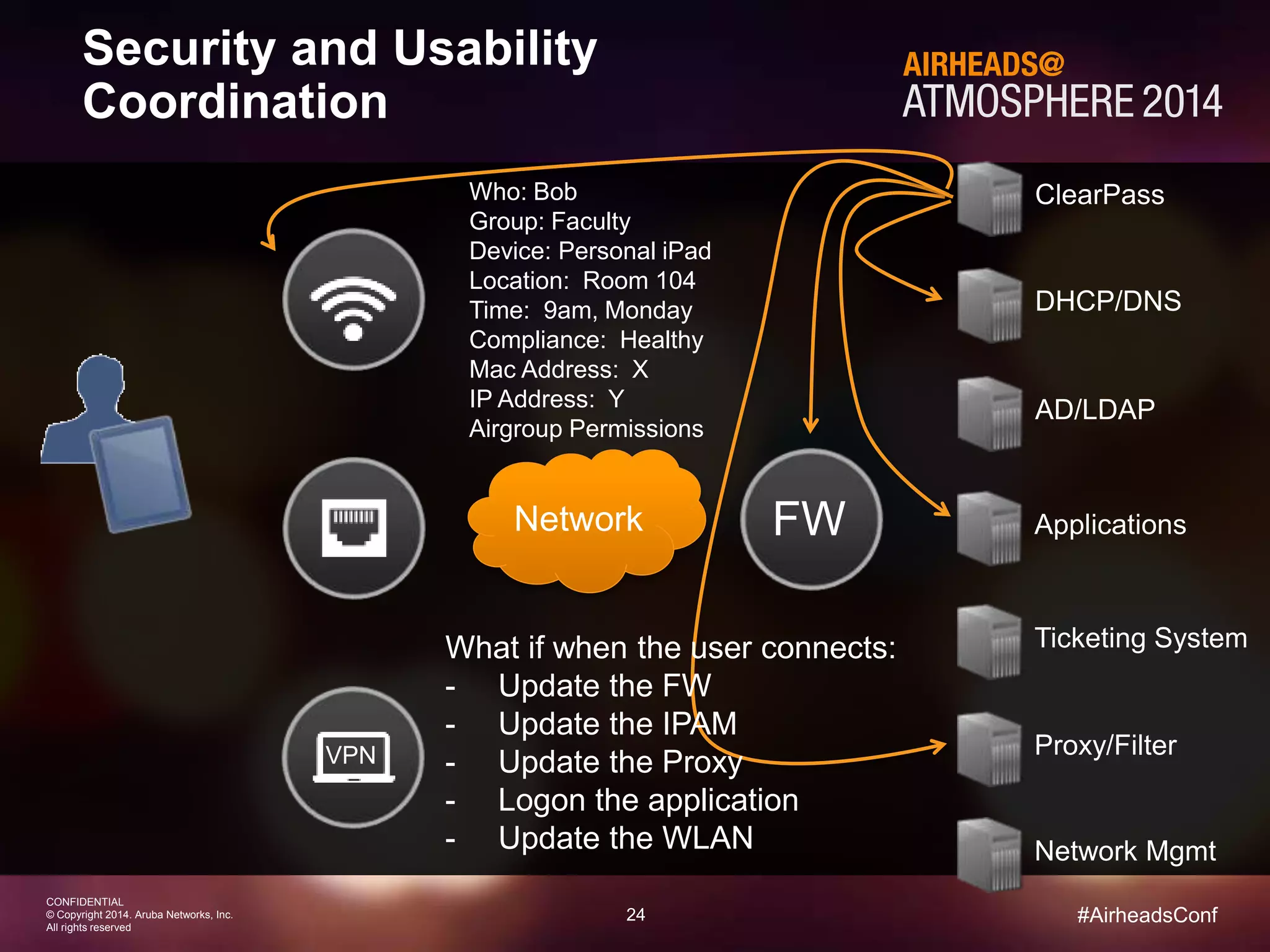
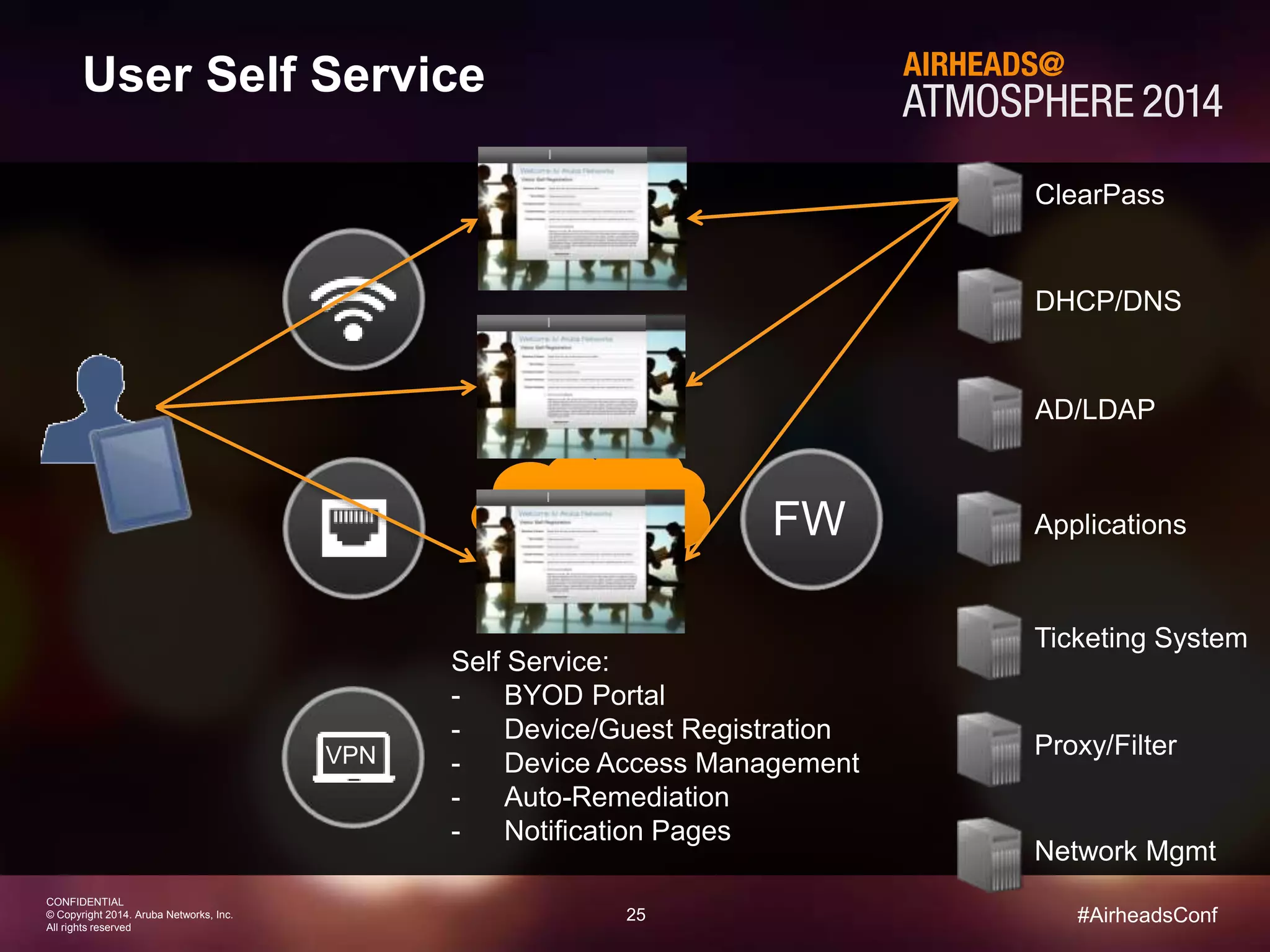
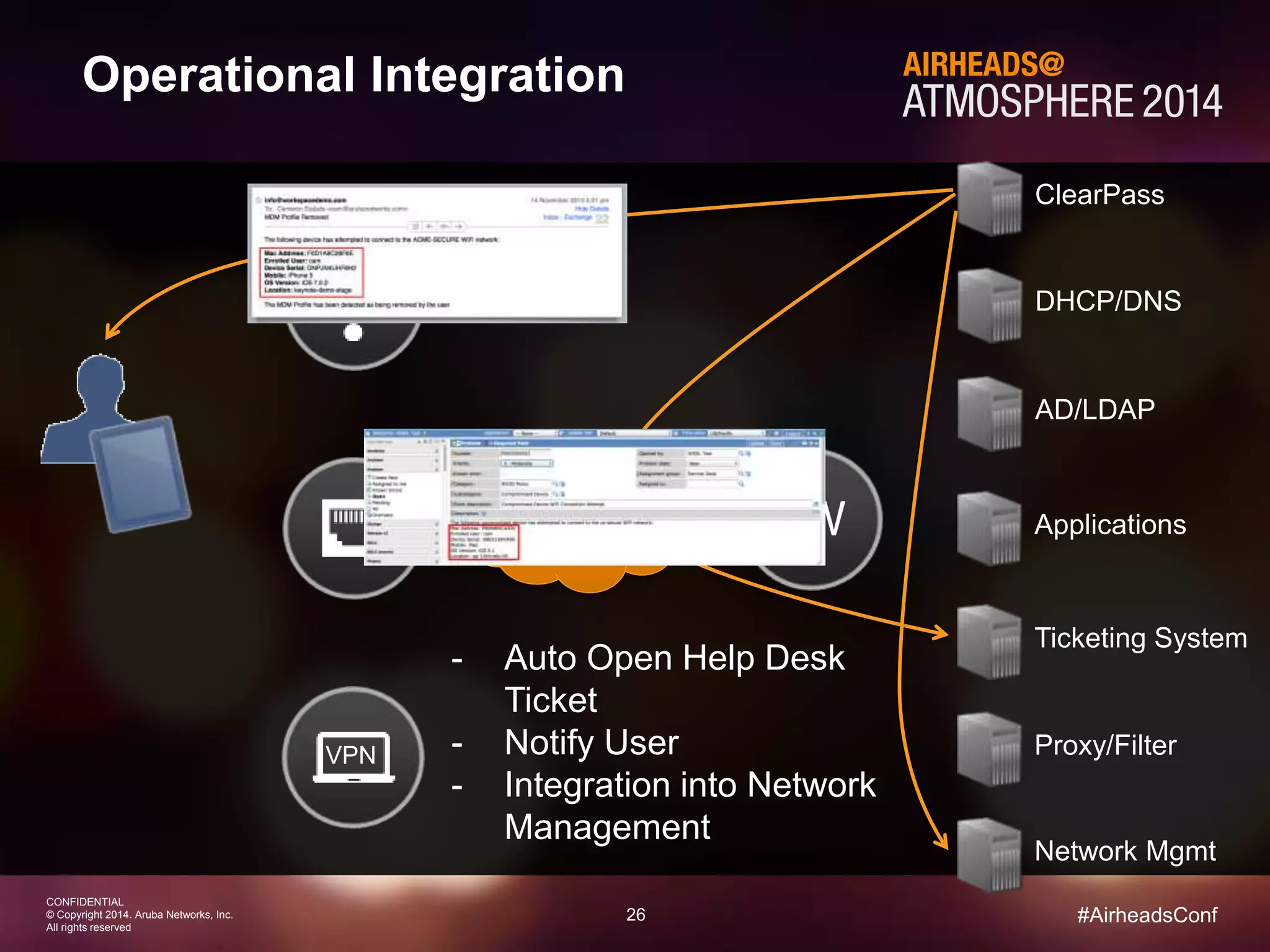
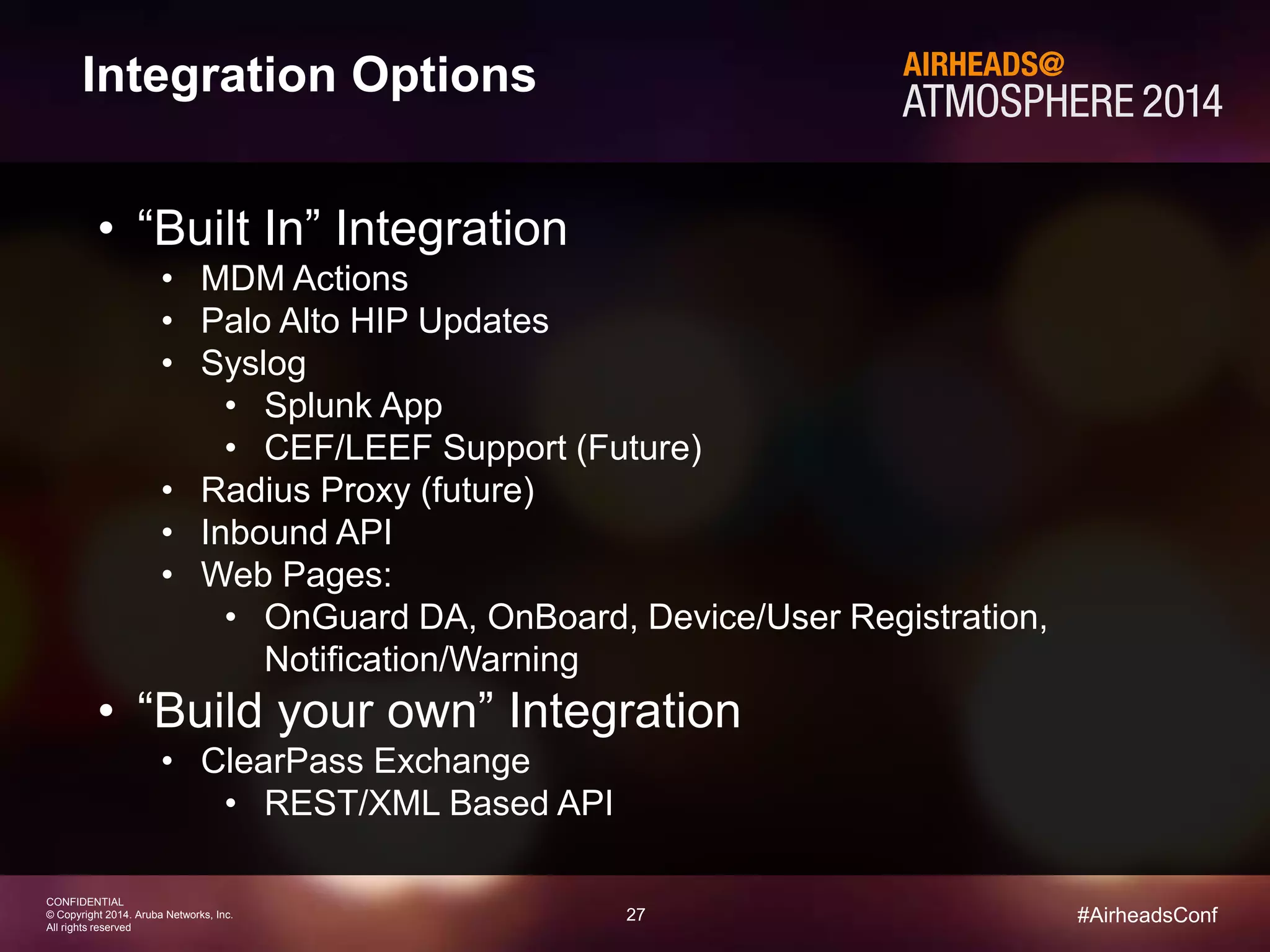
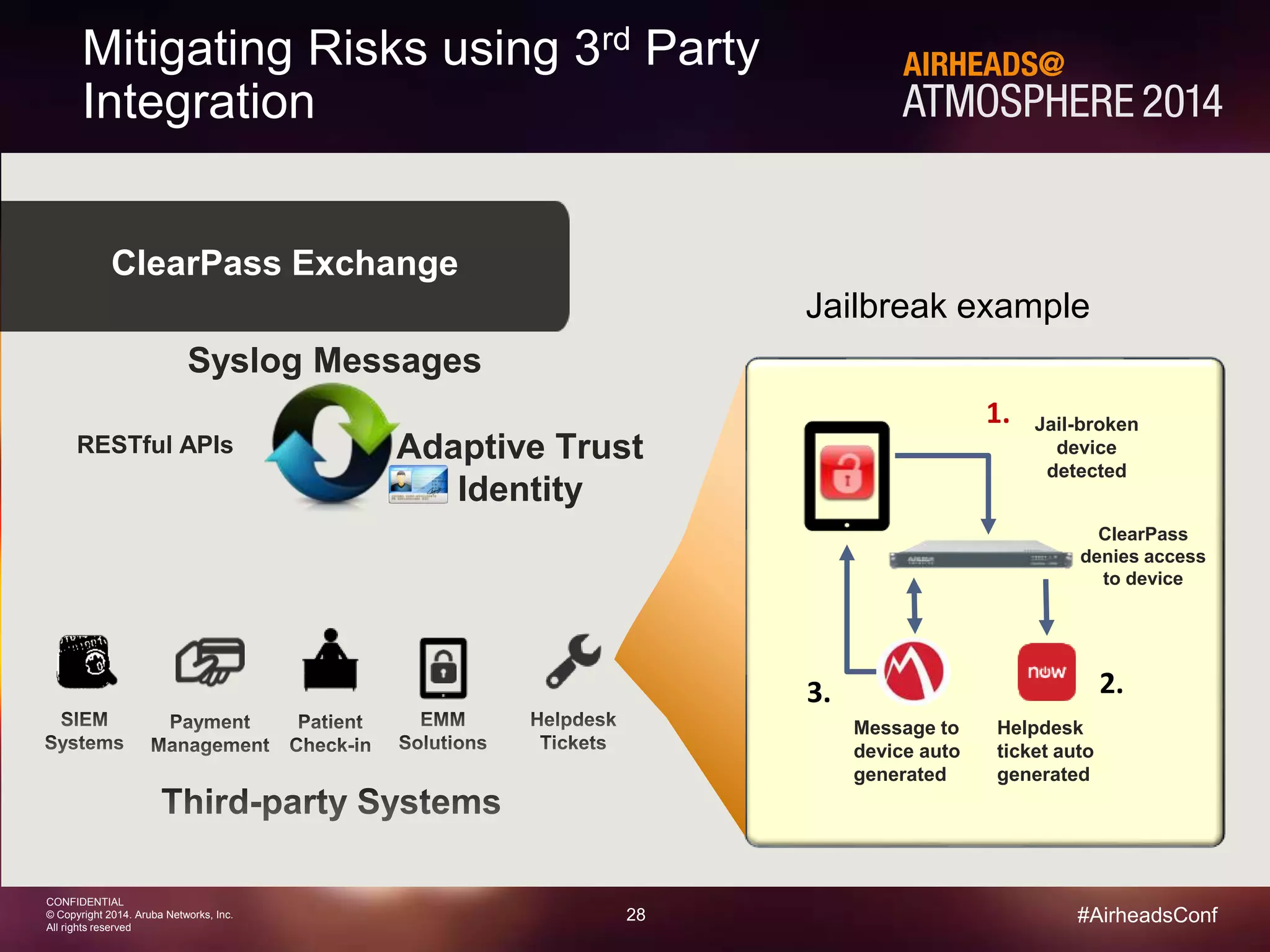
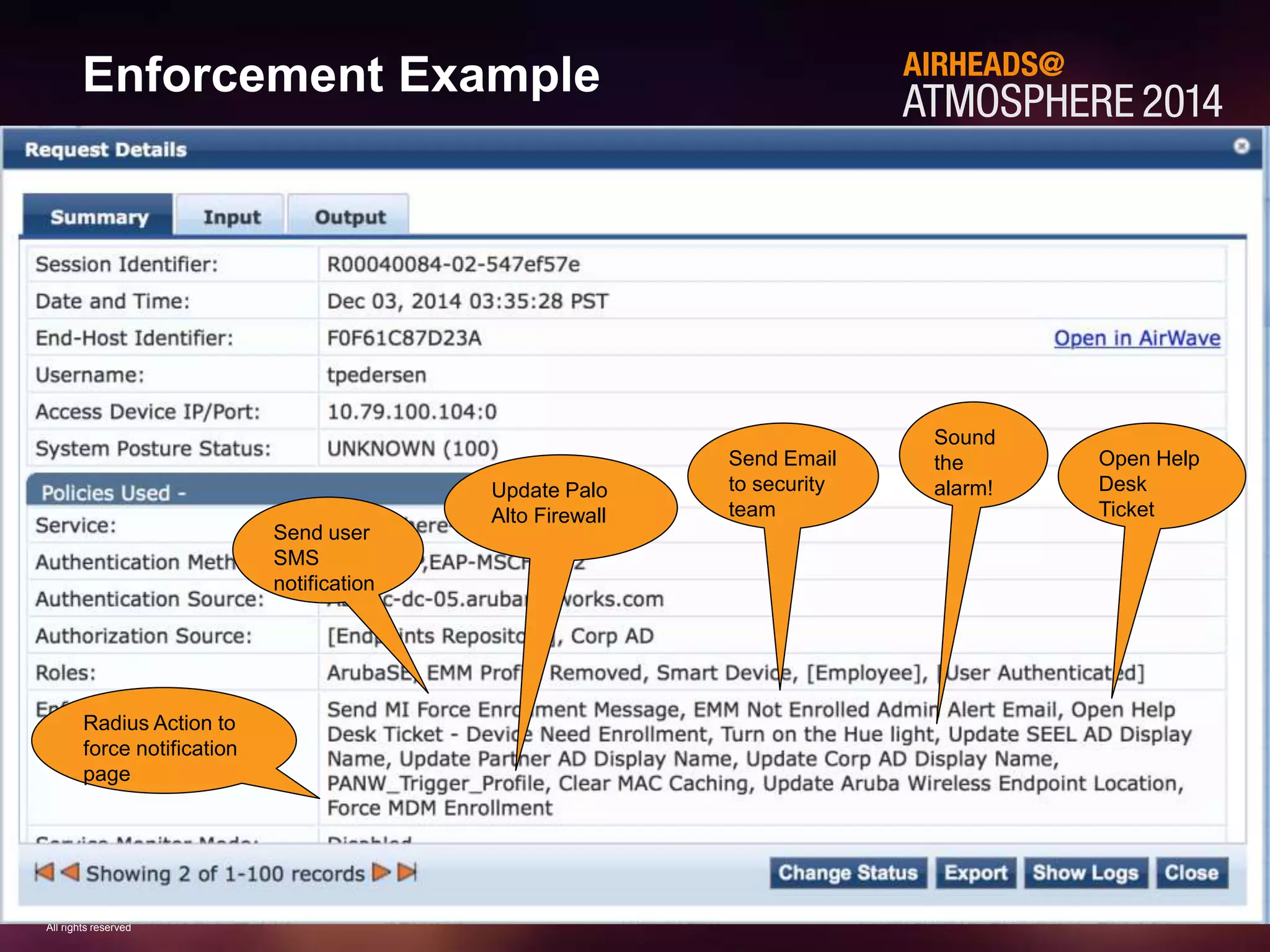
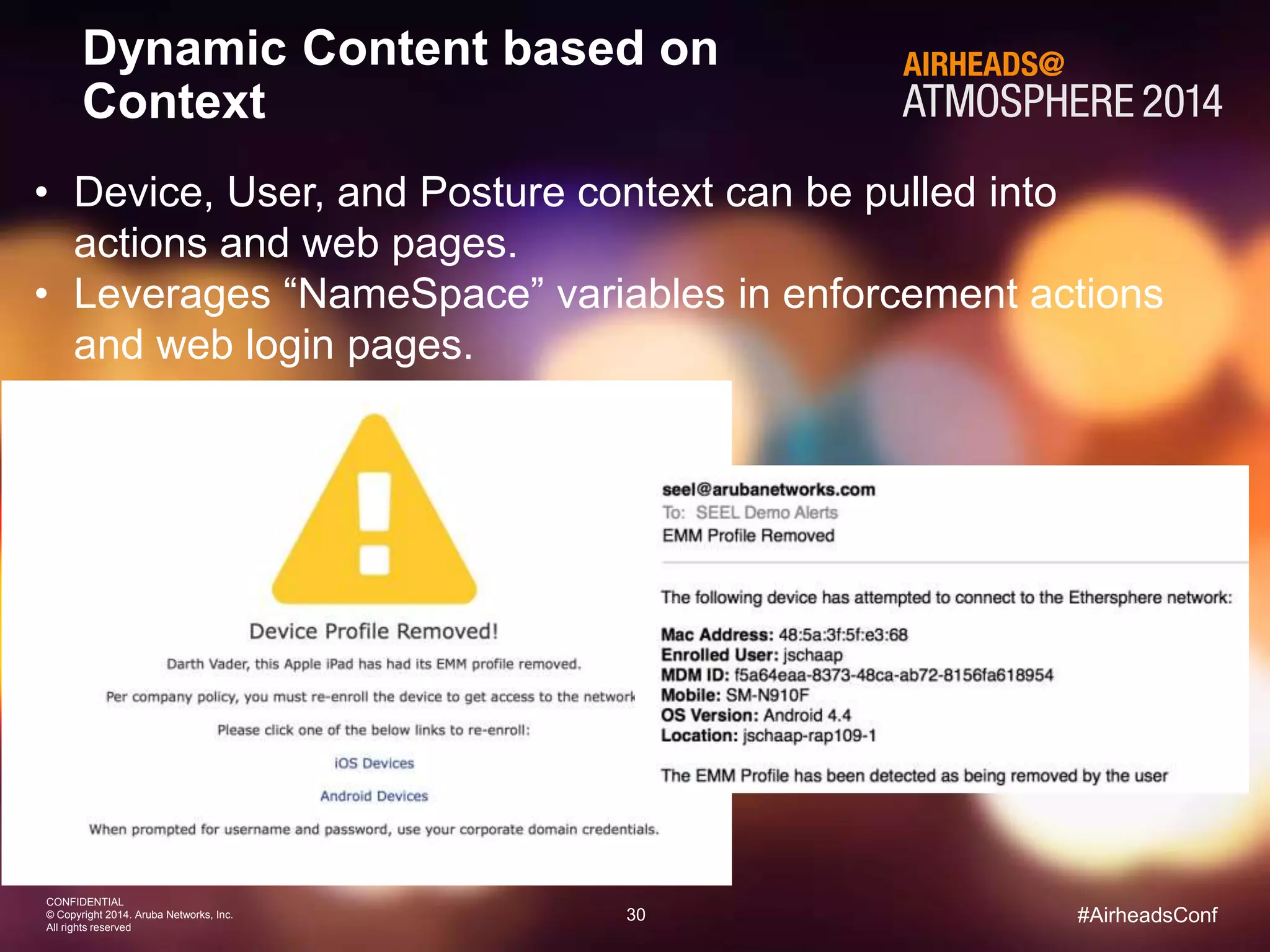
The document discusses how Aruba ClearPass provides adaptive network access policies through context-based authentication and authorization. It describes how ClearPass collects contextual information from various sources to make policy decisions. This context includes attributes about the user, device, location, authentication method, and more. ClearPass then maps collected context to roles and enforces policies based on matching roles and device posture to take actions like sending Radius responses, updating firewall rules, or triggering remediation. The adaptive policies allow for a more coordinated approach to security, operations, and user experience.



![8
CONFIDENTIAL
© Copyright 2014. Aruba Networks, Inc.
All rights reserved
#AirheadsConf
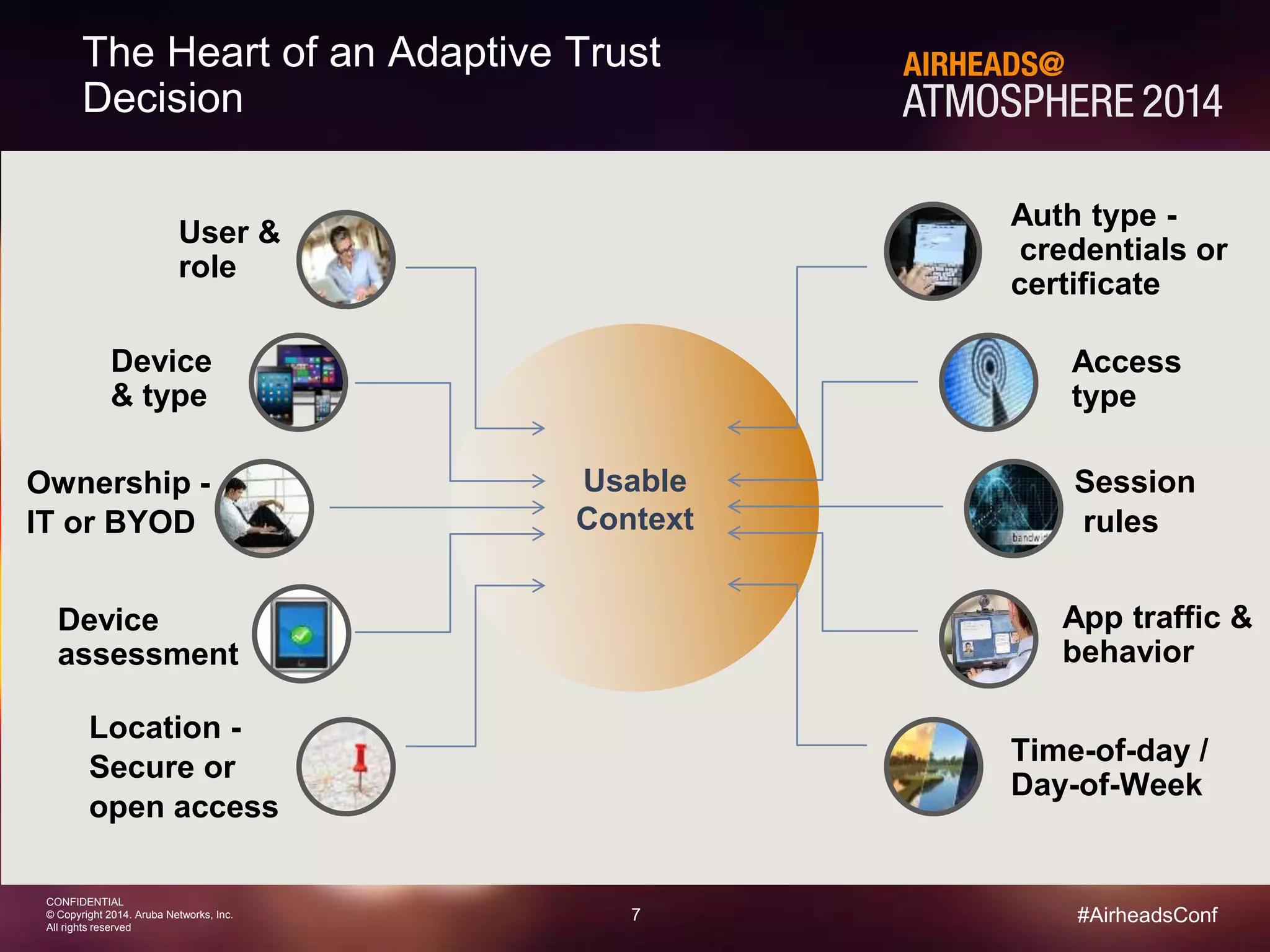
Sources of Usable Context
Device
Profiling
• Samsung SM-G900
• Android
• “Jons-Galaxy”
EMM/MDM
• Personal owned
• Registered
• OS up-to-date
• Hansen, Jon [Sales]
• MDM enabled = true
• In-compliance = true
Identity
Stores
Enforcement
Points
• Hansen, Jon [Sales]
• Title – COO
• Dept – Executive office
• City – London
• Location – Bldg 10
• Floor – 3
• Bandwidth – 10Mbps](https://image.slidesharecdn.com/finalaccessmanagementwitharubaclearpass-120814-longformat-141210171710-conversion-gate01/75/Shanghai-Breakout-Access-Management-with-Aruba-ClearPass-8-2048.jpg)
![Adaptive Trust
9
CONFIDENTIAL
© Copyright 2014. Aruba Networks, Inc.
All rights reserved
#AirheadsConf
Sources of Usable Context
Device
Profiling
• Samsung SM-G900
• Android
• “Jons-Galaxy”
EMM/MDM
• Personal owned
• Registered
• OS up-to-date
• Hansen, Jon [Sales]
• MDM enabled = true
• In-compliance = true
Identity
Stores
Enforcement
Points
• Hansen, Jon [Sales]
• Title – COO
• Dept – Executive office
• City – London
• Location – Bldg 10
• Floor – 3
• Bandwidth – 10Mbps
Identity
• Hansen, Jon [Sales]
• COO, Executive Office
• London
• Personal Owned
• Samsung SM-G900
• Android 4.4, Knox
• MDM enabled = true
• In-compliance = true
• At Bldg 10, floor 3
• 21:22GMT, 21/12/14](https://image.slidesharecdn.com/finalaccessmanagementwitharubaclearpass-120814-longformat-141210171710-conversion-gate01/75/Shanghai-Breakout-Access-Management-with-Aruba-ClearPass-9-2048.jpg)