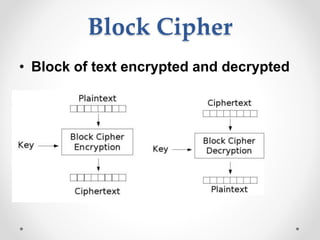
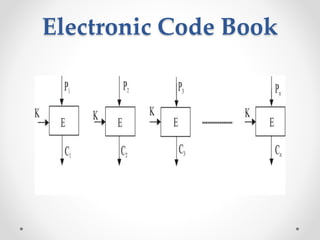
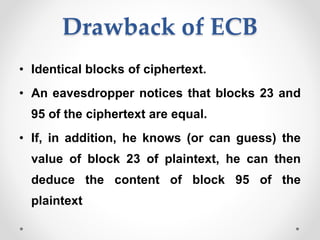
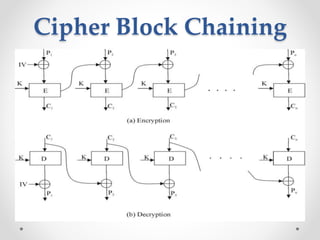
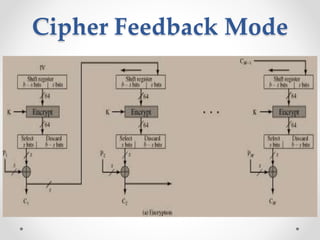
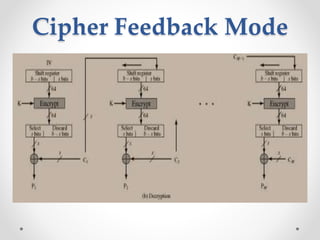
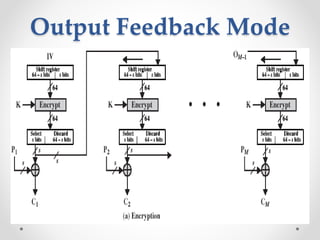
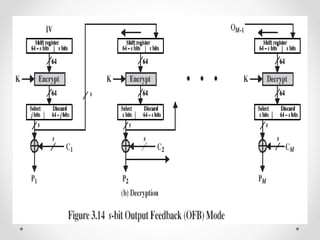
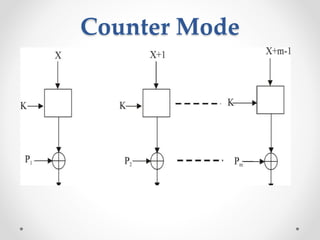
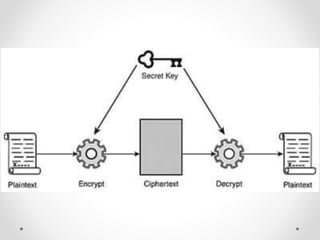
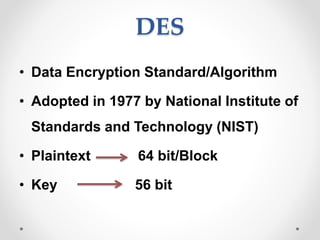
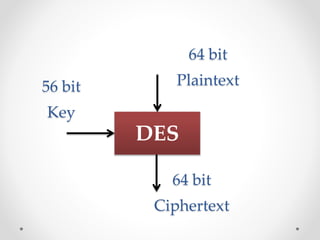
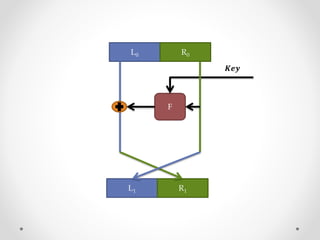
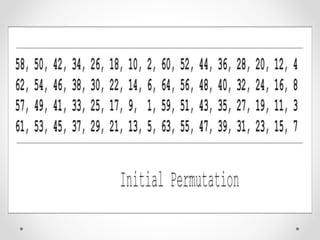
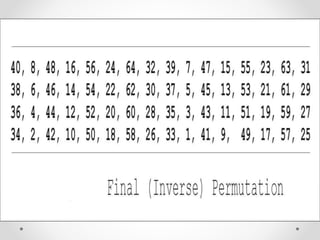
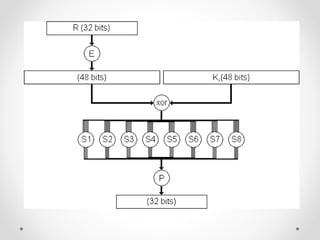
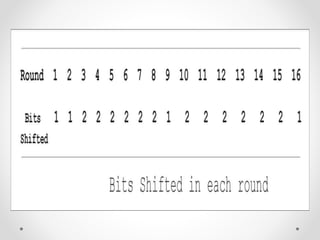
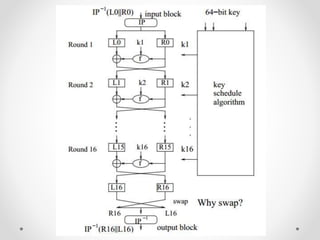
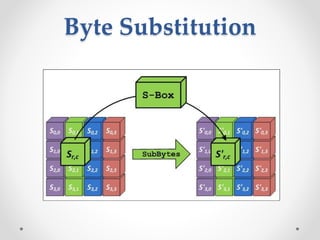
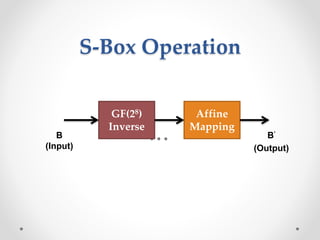
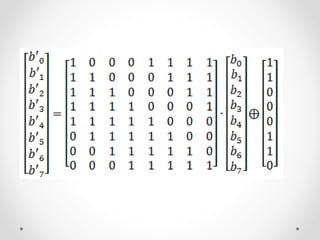
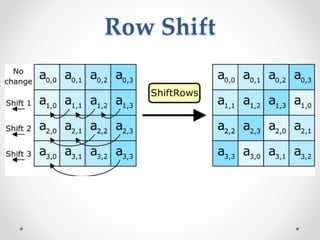
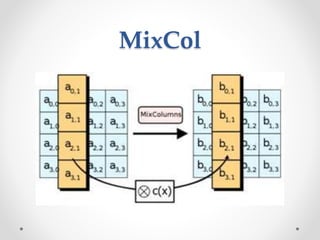
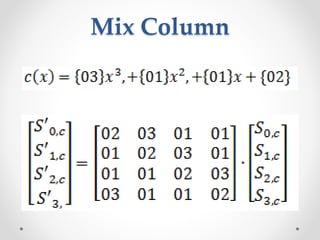
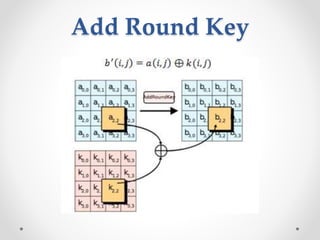
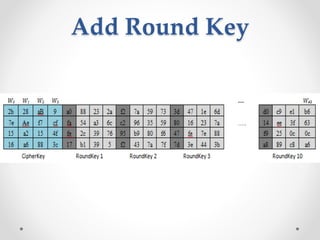
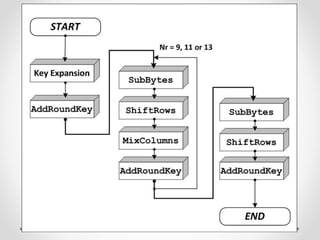
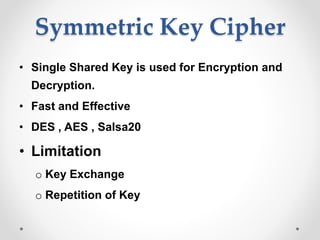
This document discusses modern symmetric key algorithms. It describes stream ciphers and block ciphers, with RC4 and DES provided as examples. The concepts of confusion and diffusion are introduced. Modes of operation for block ciphers are defined, including ECB, CBC, CFB and OFB. DES encryption uses a 64-bit block size and 56-bit key, operating over 16 rounds of feistel network and key schedule. AES was selected to replace DES due to larger block size and key size, operating over 10 to 14 rounds of byte substitution, row shifting, column mixing and subkey addition. Symmetric key ciphers are fast but require secure key exchange and management to prevent repetition.