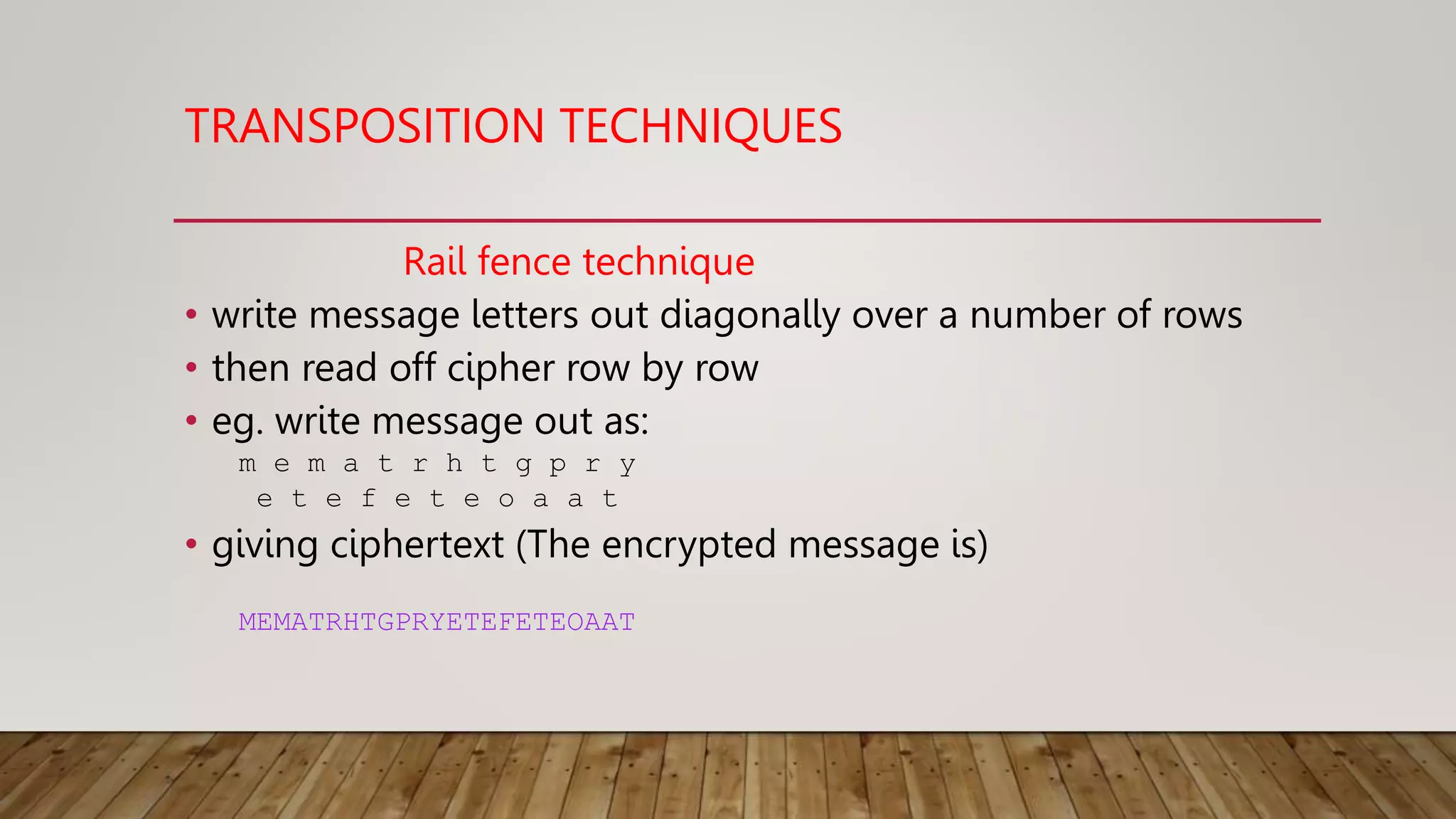
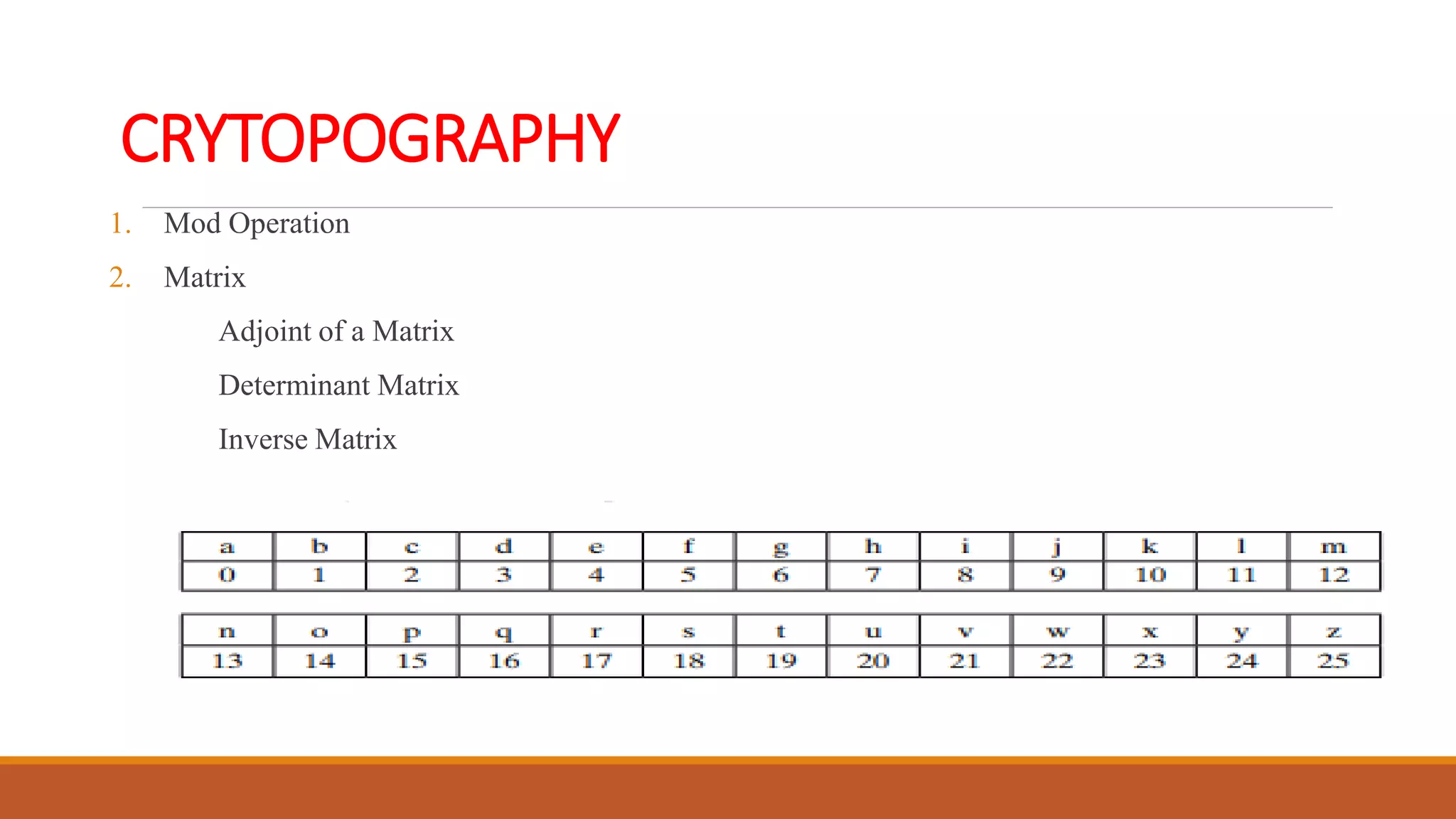
The document discusses various cryptographic techniques including:
1. Symmetric and asymmetric encryption which use secret keys or public/private key pairs to encrypt messages.
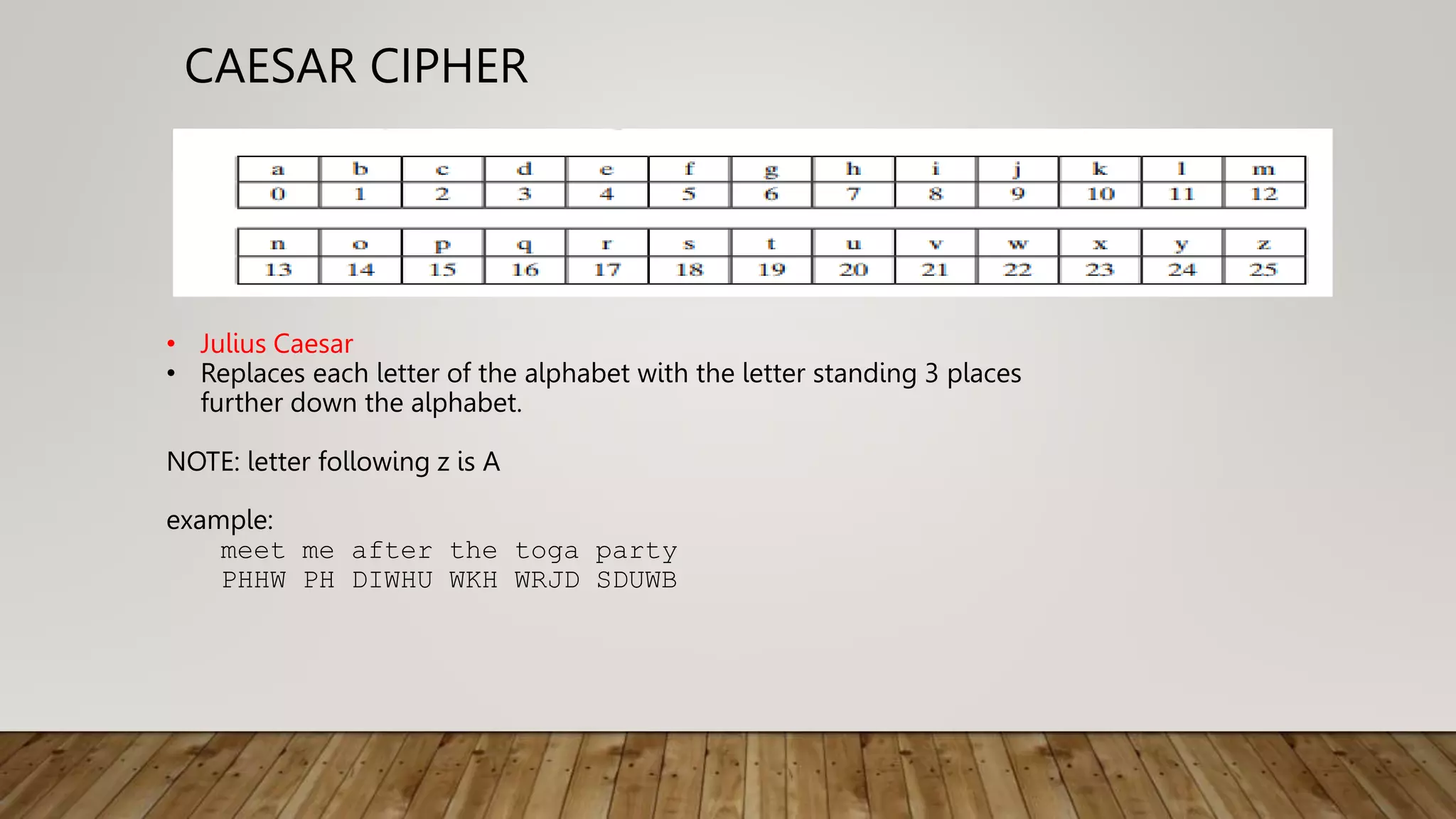
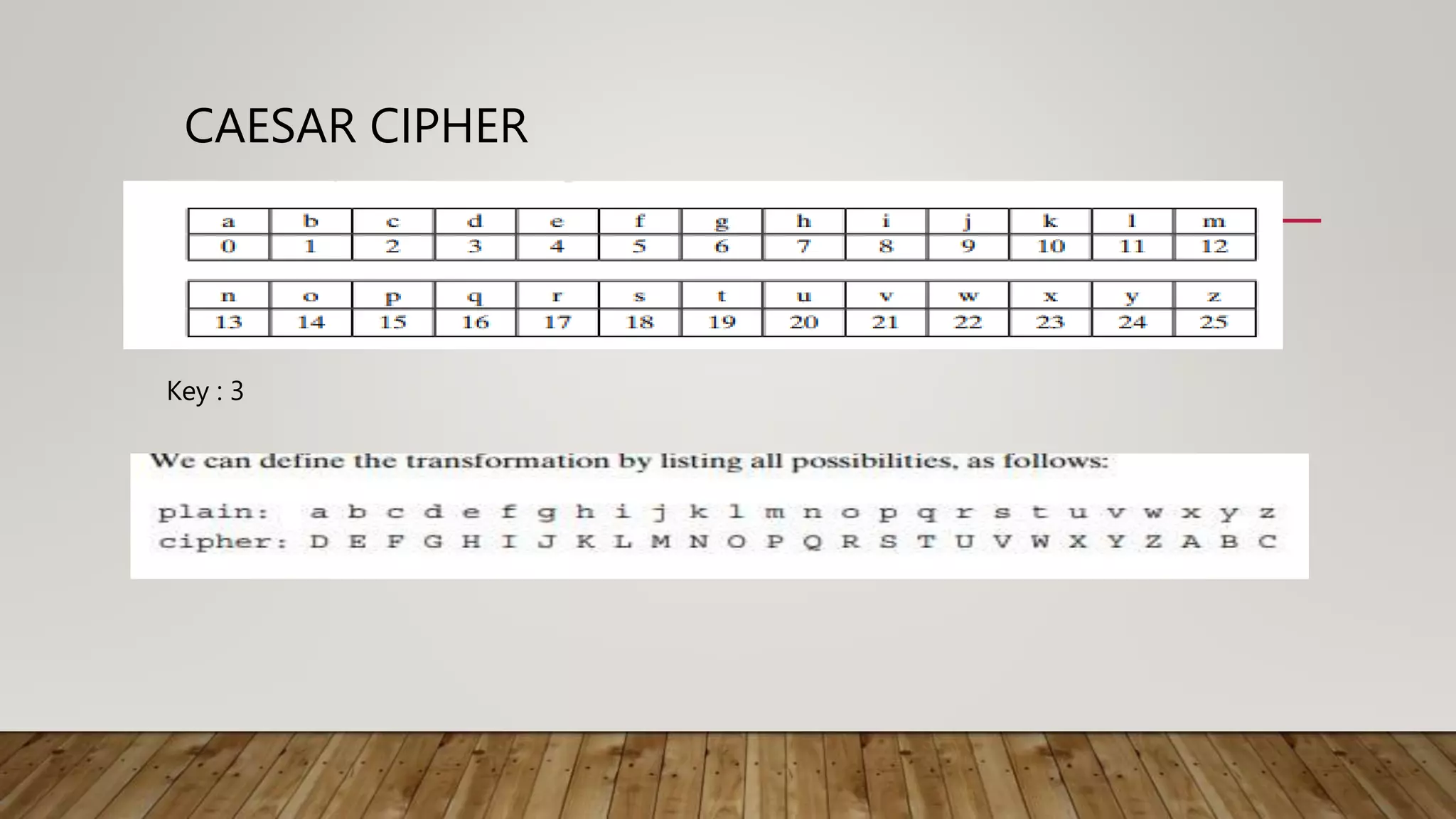
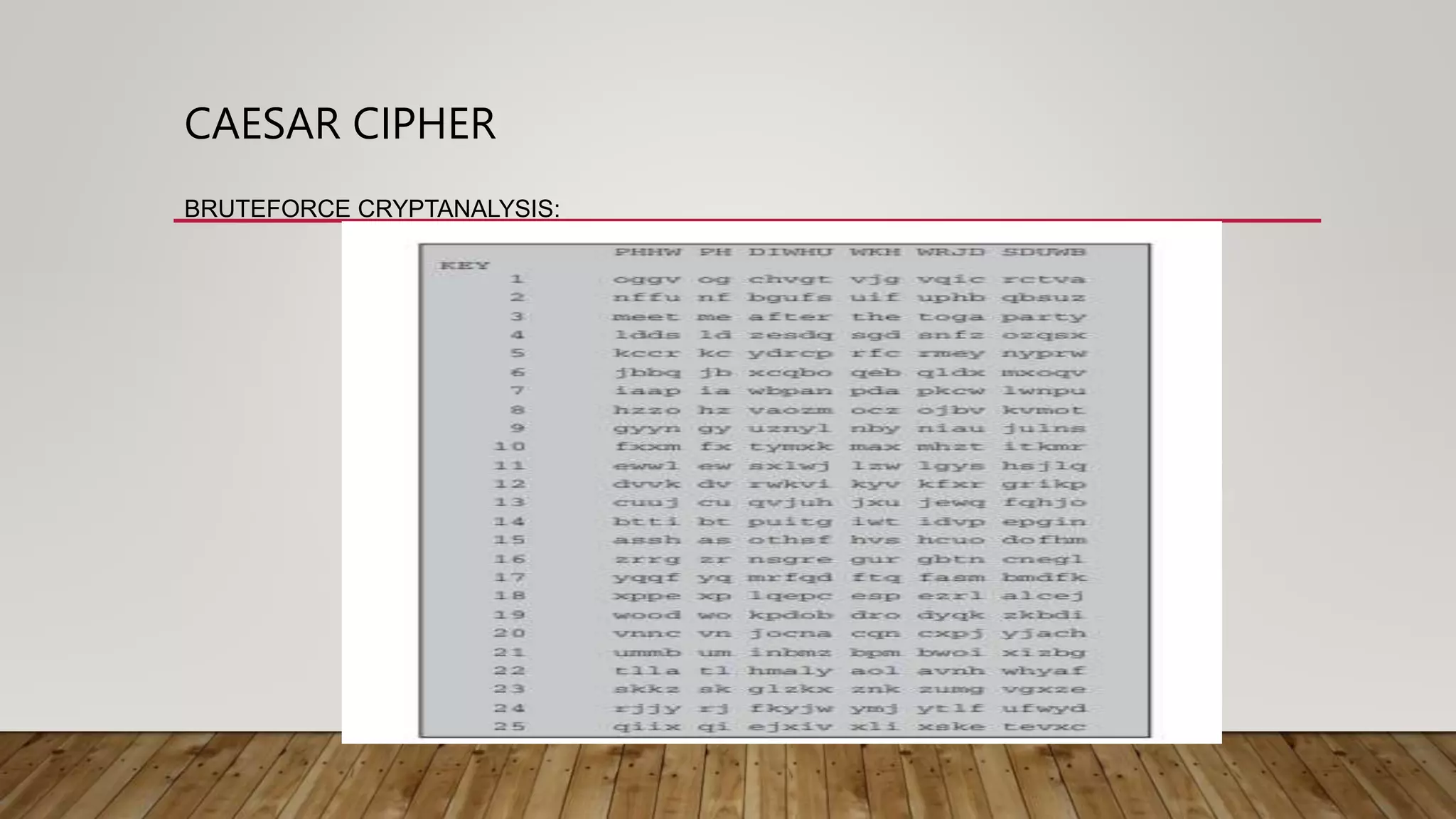
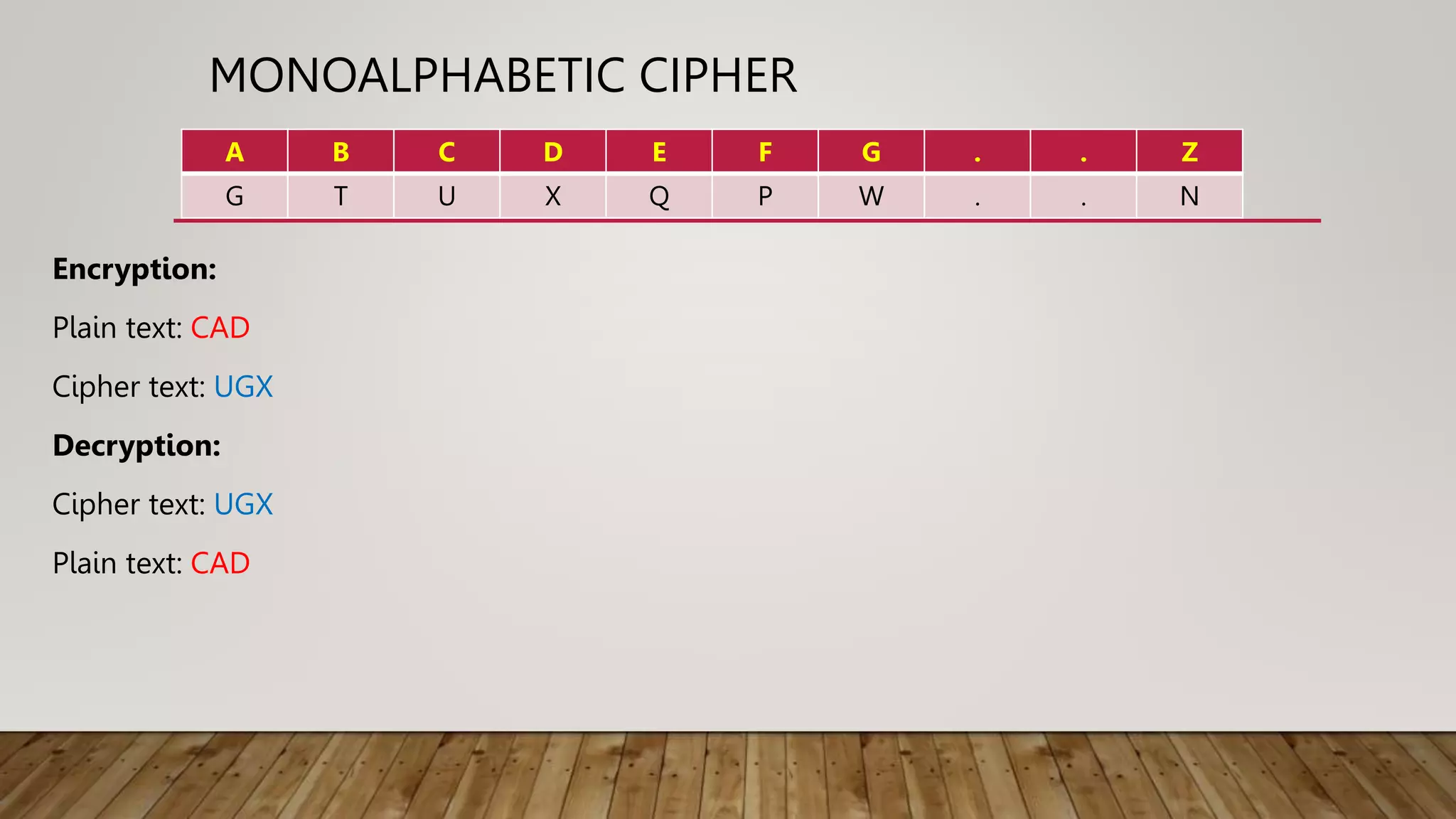
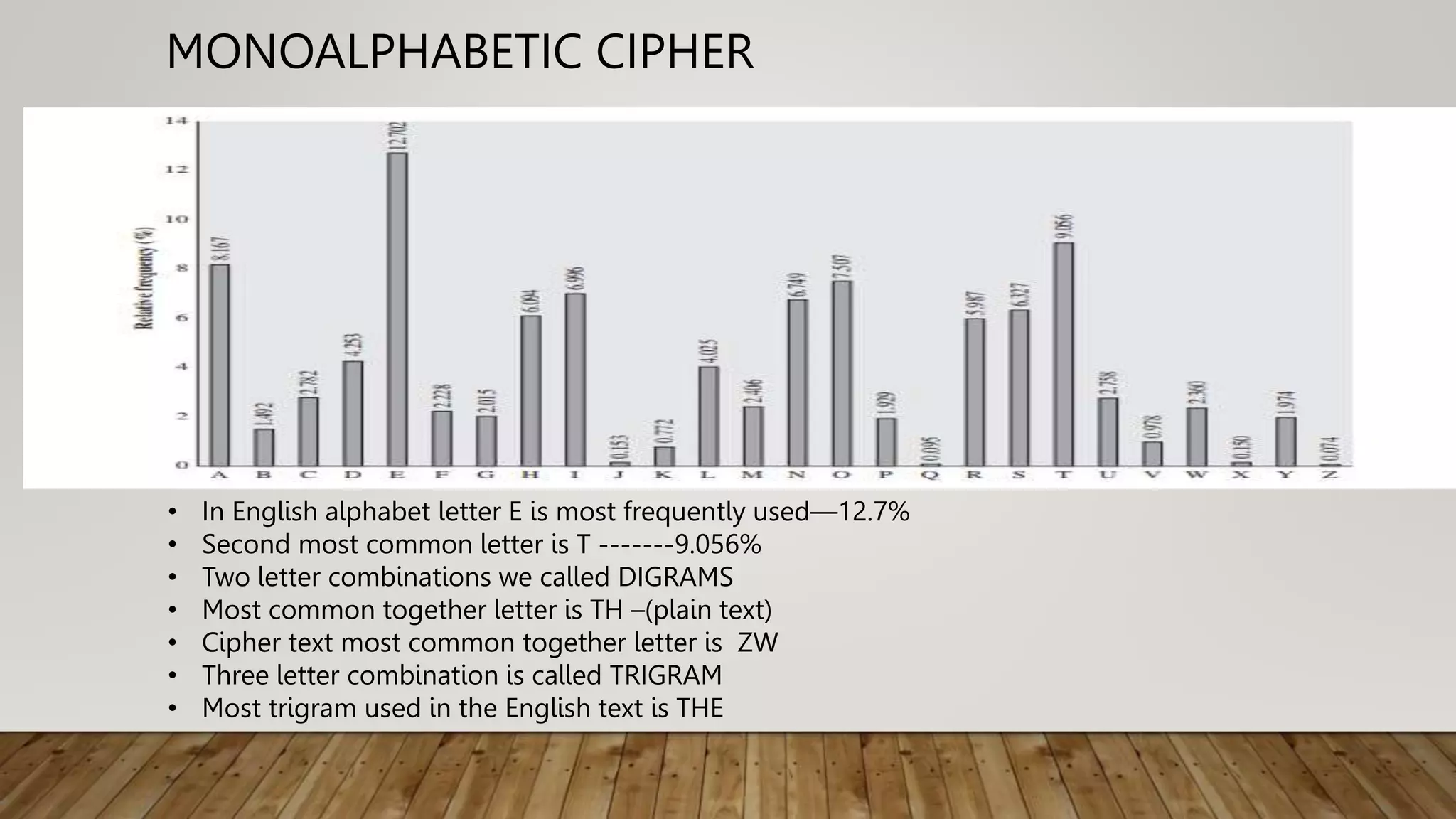
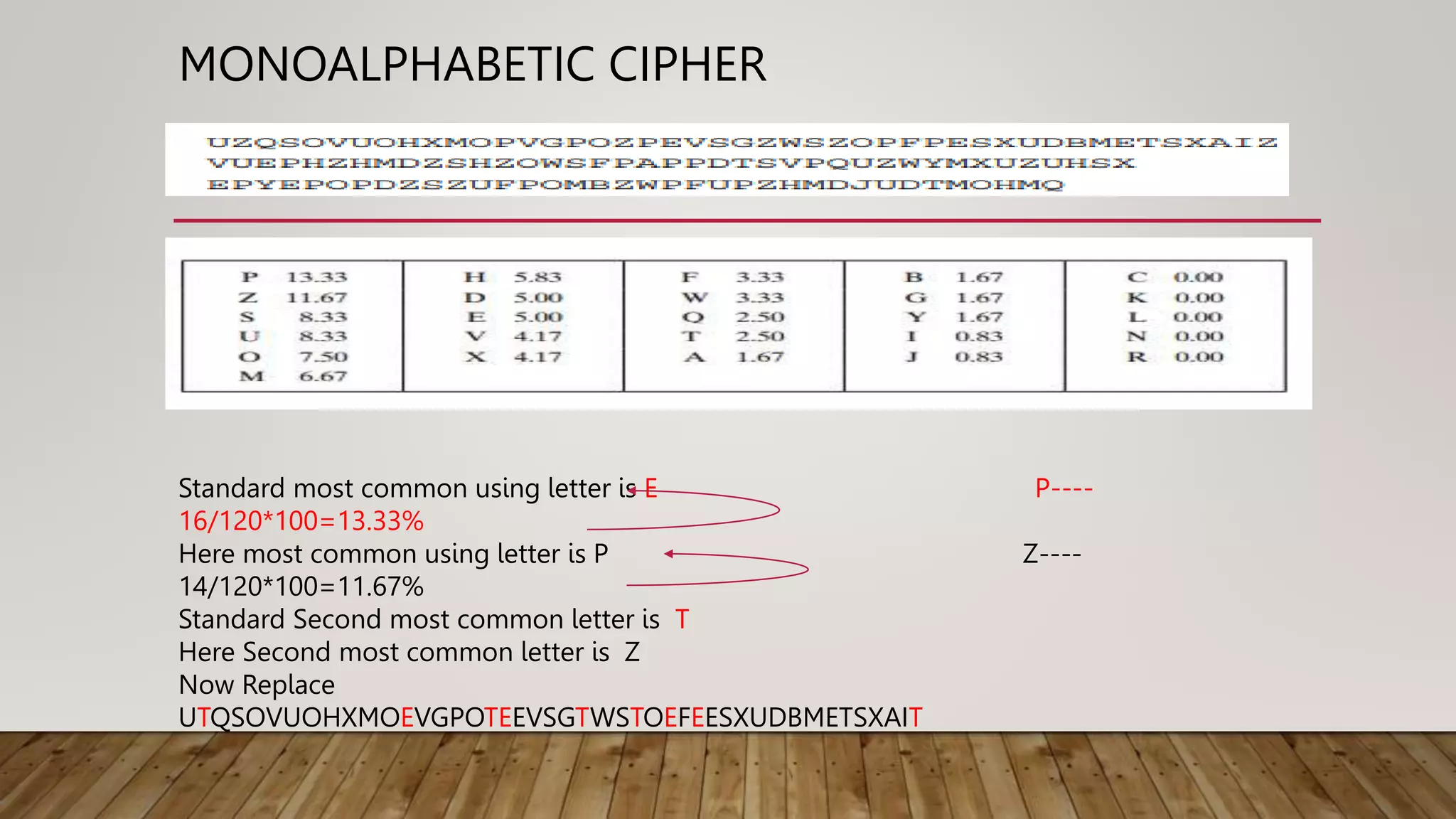
2. Classical techniques like the Caesar cipher which shifts letters, monoalphabetic substitution ciphers using letter permutations, and the Playfair cipher which encrypts digrams.
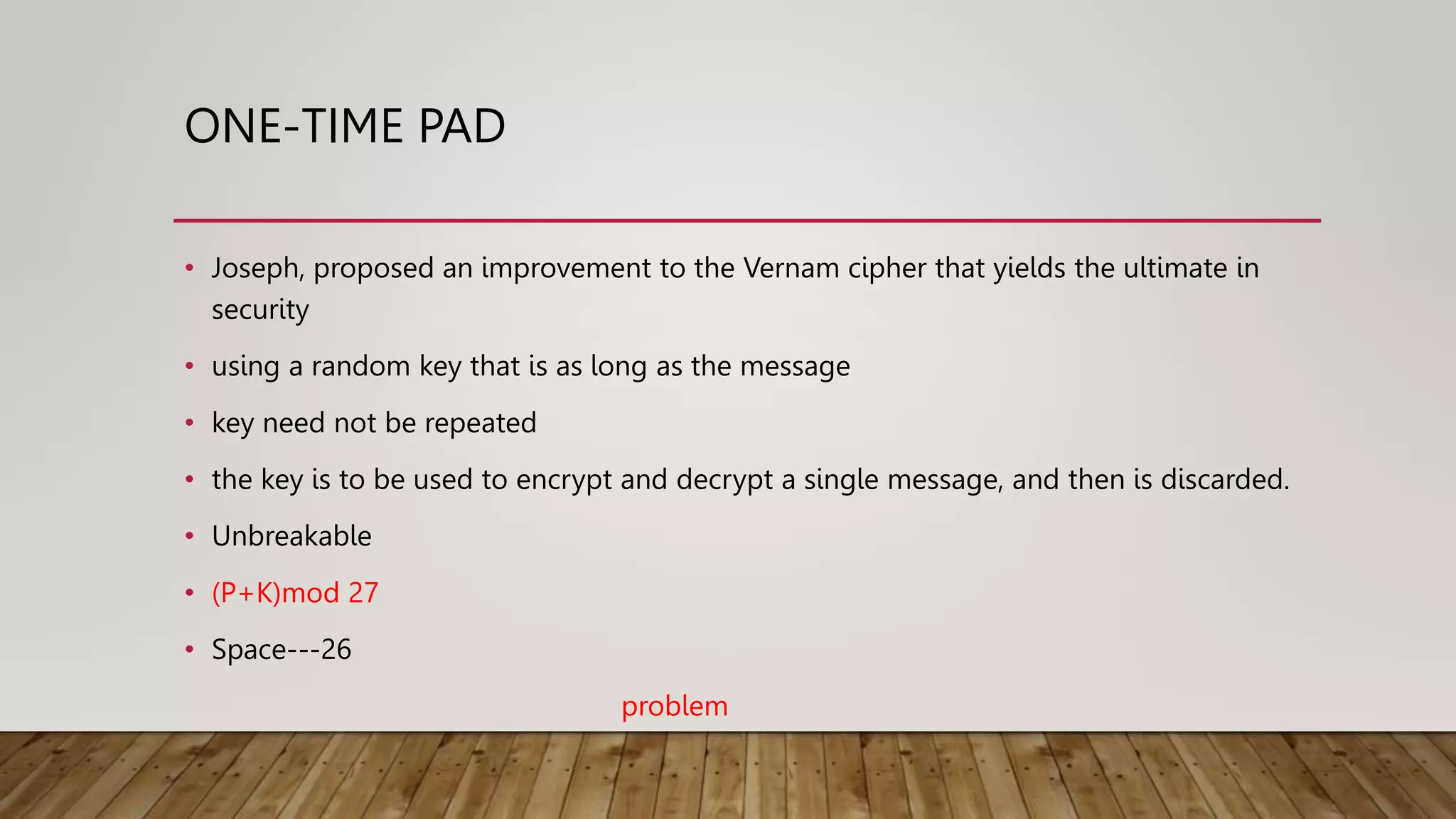
3. The one-time pad cipher which is unbreakable if a truly random key is used only once but has key distribution issues.




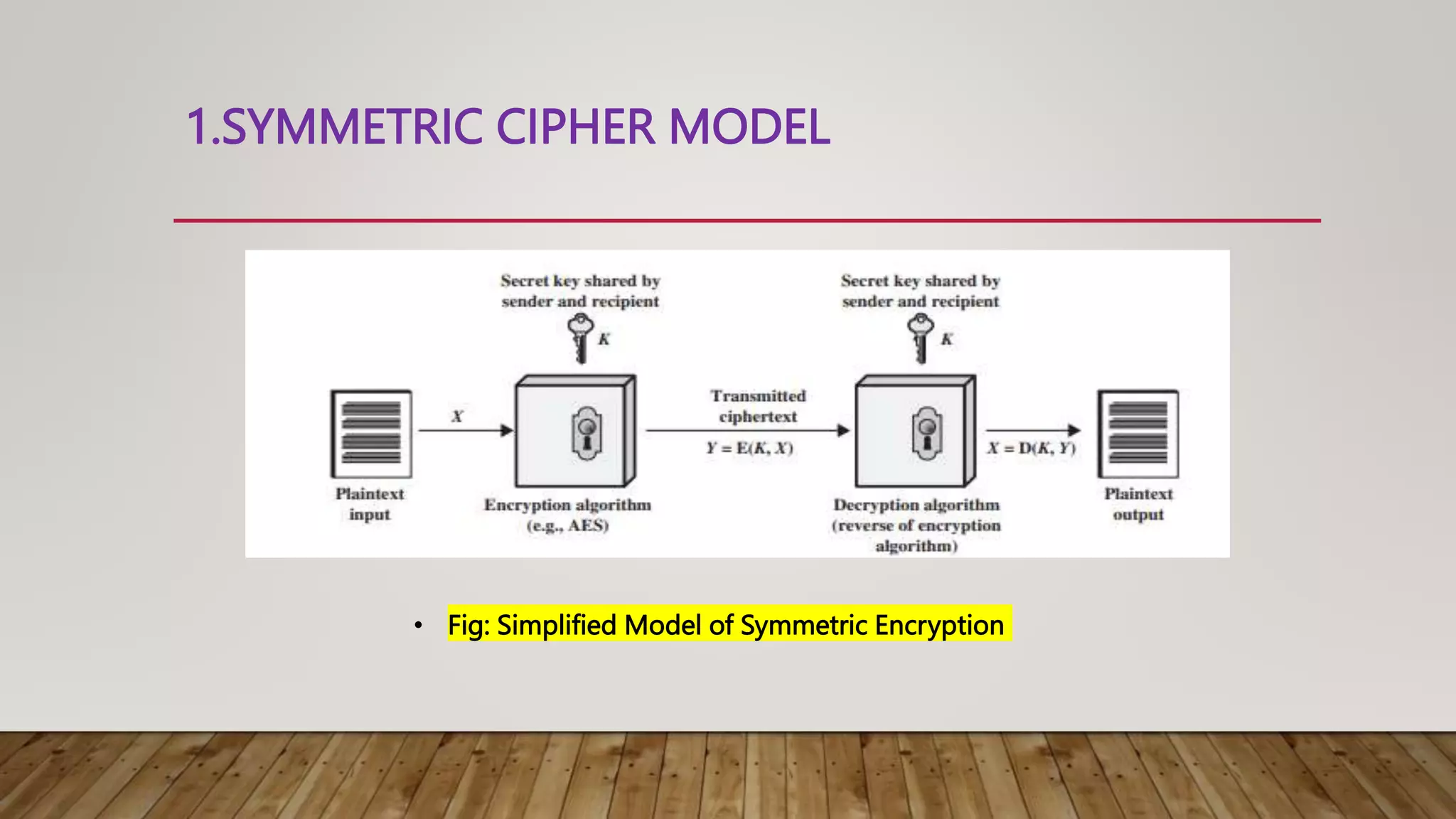

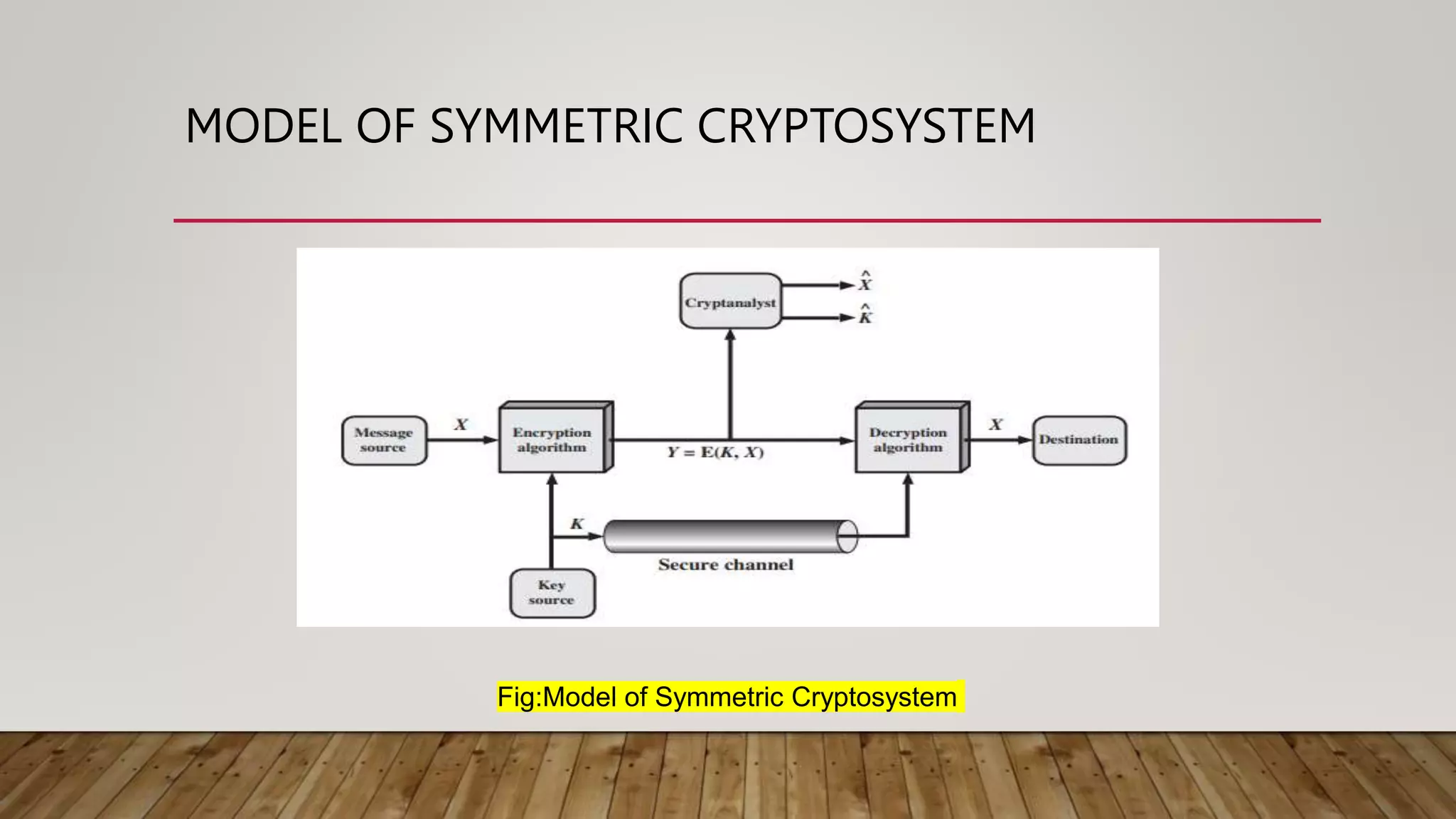
![MODEL OF SYMMETRIC CRYPTOSYSTEM
• A source produces a message in plaintext, X = [X1, X2, ….. XM].
• For encryption, a key of the form K = [K1, K2, ….., KJ] is generated
• The encryption algorithm forms the ciphertext Y = [Y1, Y2, ….. YN].
• Y = E(K, X)
• X = D(K, Y)](https://image.slidesharecdn.com/module1parta-221031074105-67224745/75/cryptography-symmentric-pptx-10-2048.jpg)










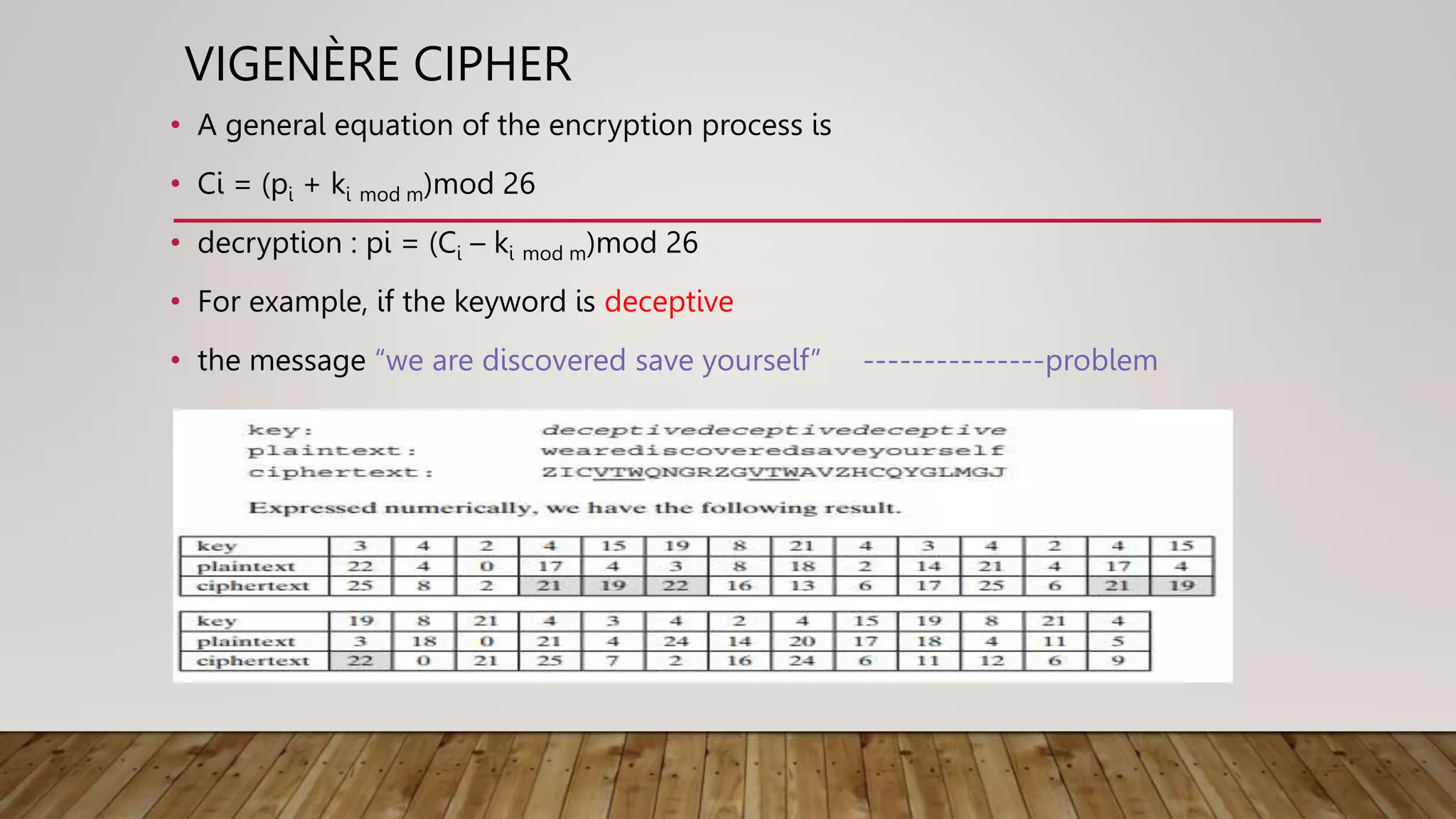
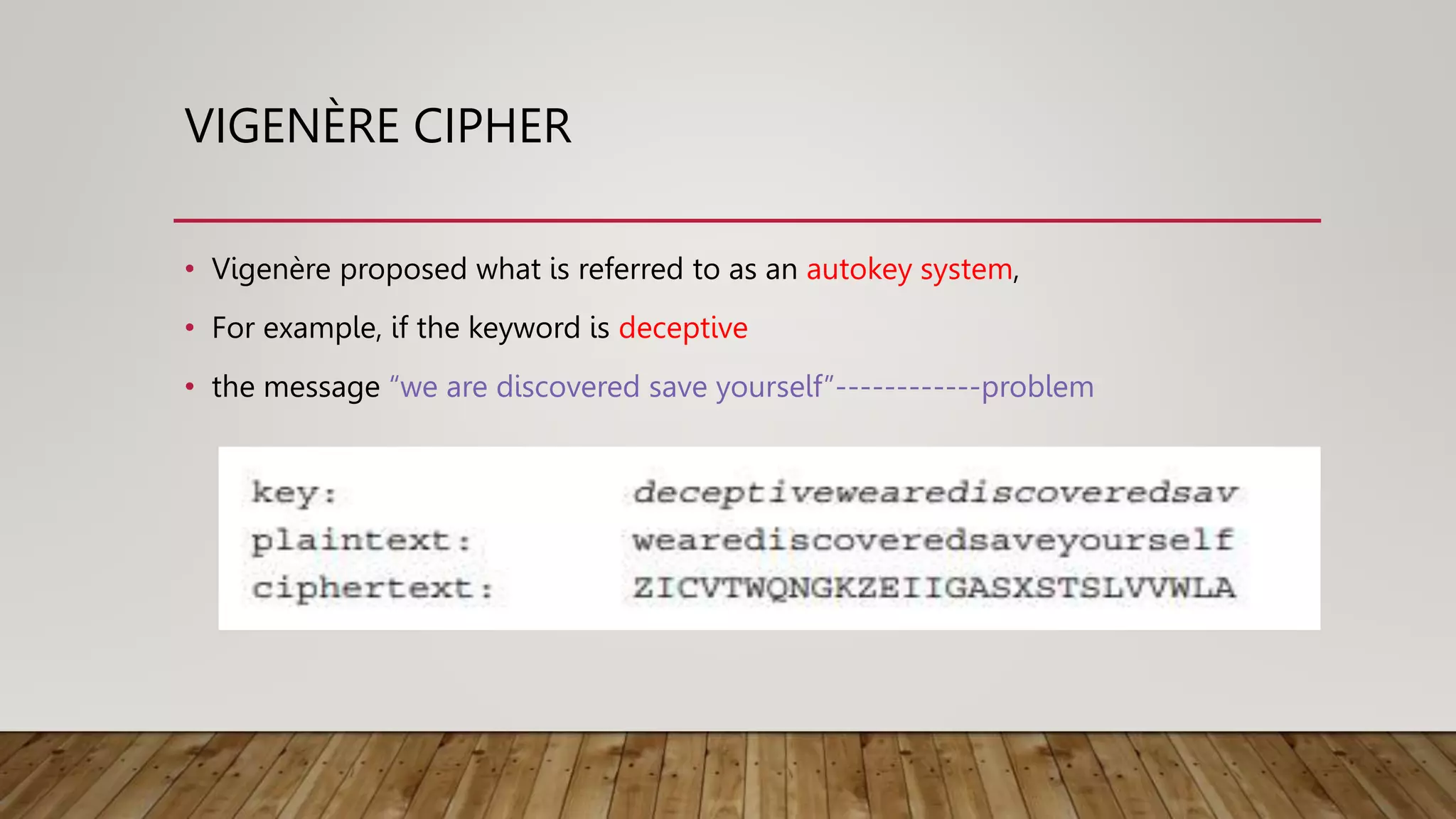
![VIGENÈRE CIPHER
• We can express the Vigenère cipher in the following manner
• Assume a sequence of plaintext letters P = p0, p1, p2, …., pn-1
• key consisting of the sequence of letters K = k0, k1, k2, …., km-1,
• ciphertext letters C = C0, C1, C2, ……, Cn-1
• C=E(K,P)
• C = C0, C1, C2, … Cn-1 = E(K, P) = E[(k0, k1, k2, …, km-1), (p0, p1, p2, …., pn-1)]
• (p0 + k0)mod 26, (p1 + k1)mod 26, ....., (pm-1 + km-1)mod 26,
• the first letter of the key is added to the first letter of the plaintext, mod
26,
• the second letters are added, and so on
• This process continues until all of the plaintext sequence is encrypted](https://image.slidesharecdn.com/module1parta-221031074105-67224745/75/cryptography-symmentric-pptx-29-2048.jpg)