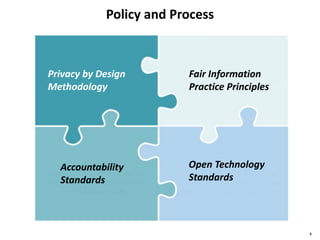
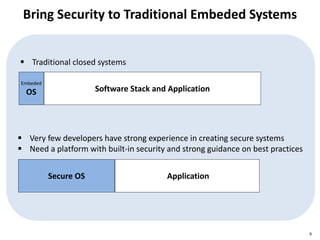
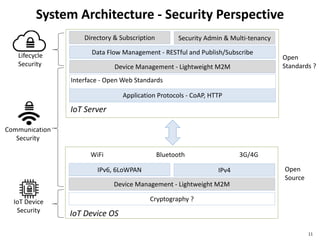
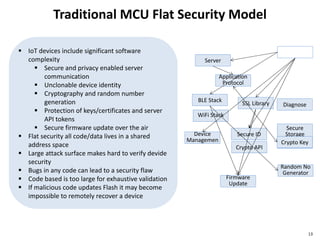
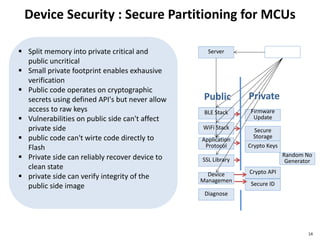
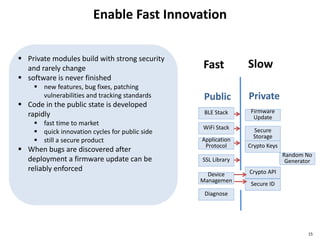
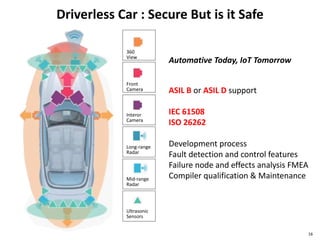
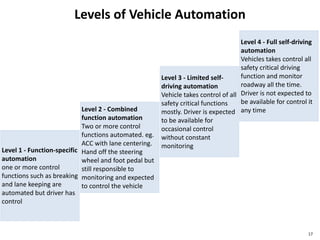
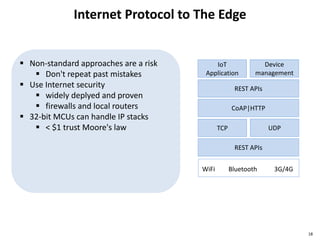
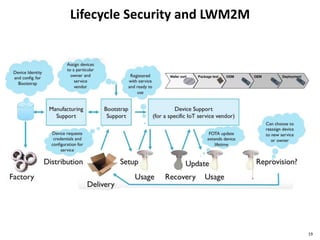
The document discusses several IoT security and privacy considerations, including using privacy by design principles to embed privacy into systems from the start, establishing accountability standards and open technology standards to build trust, and addressing common problems like lack of developer security experience, insecure communication protocols, and ensuring secure firmware updates throughout the lifecycle of IoT devices.