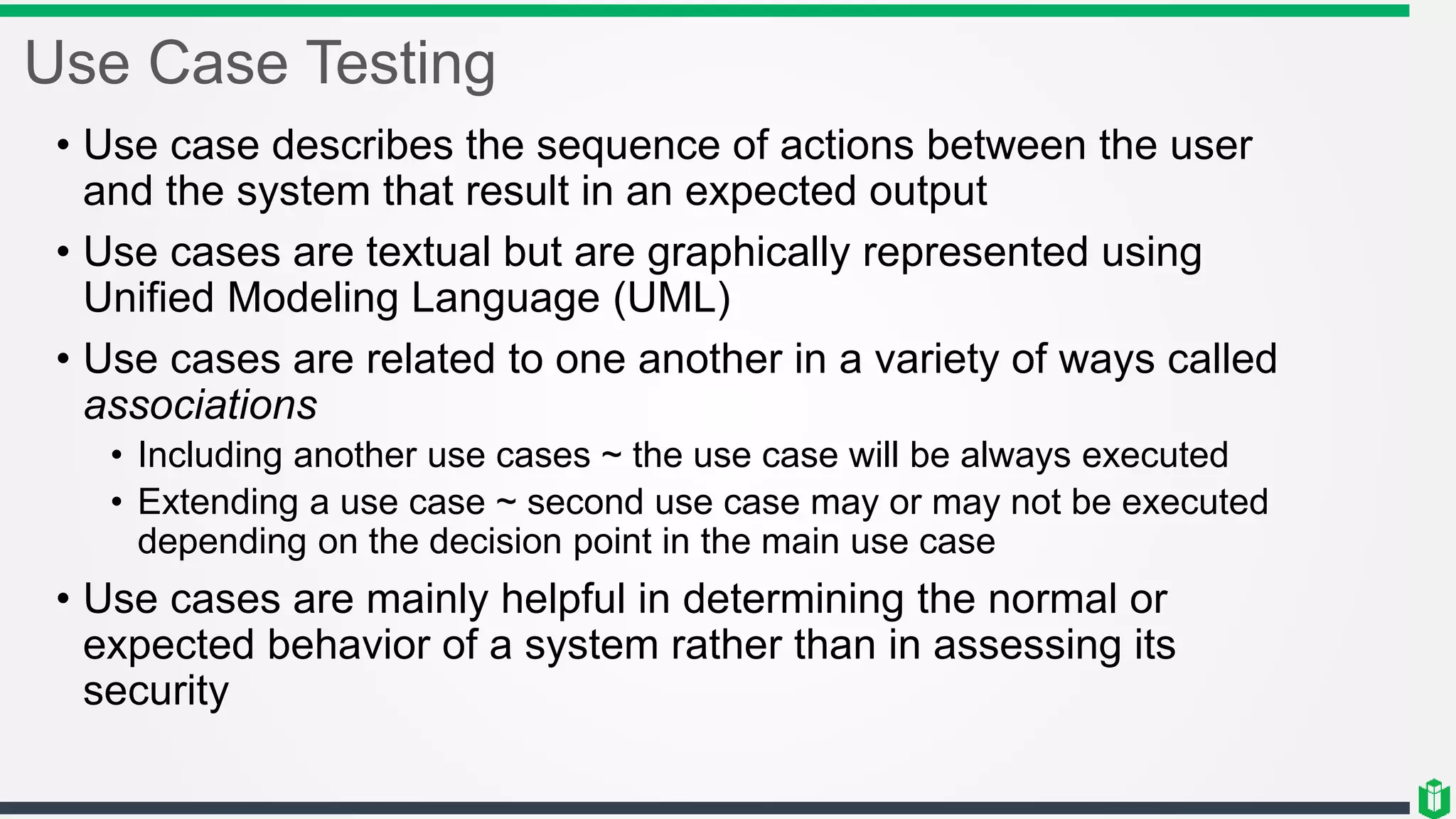
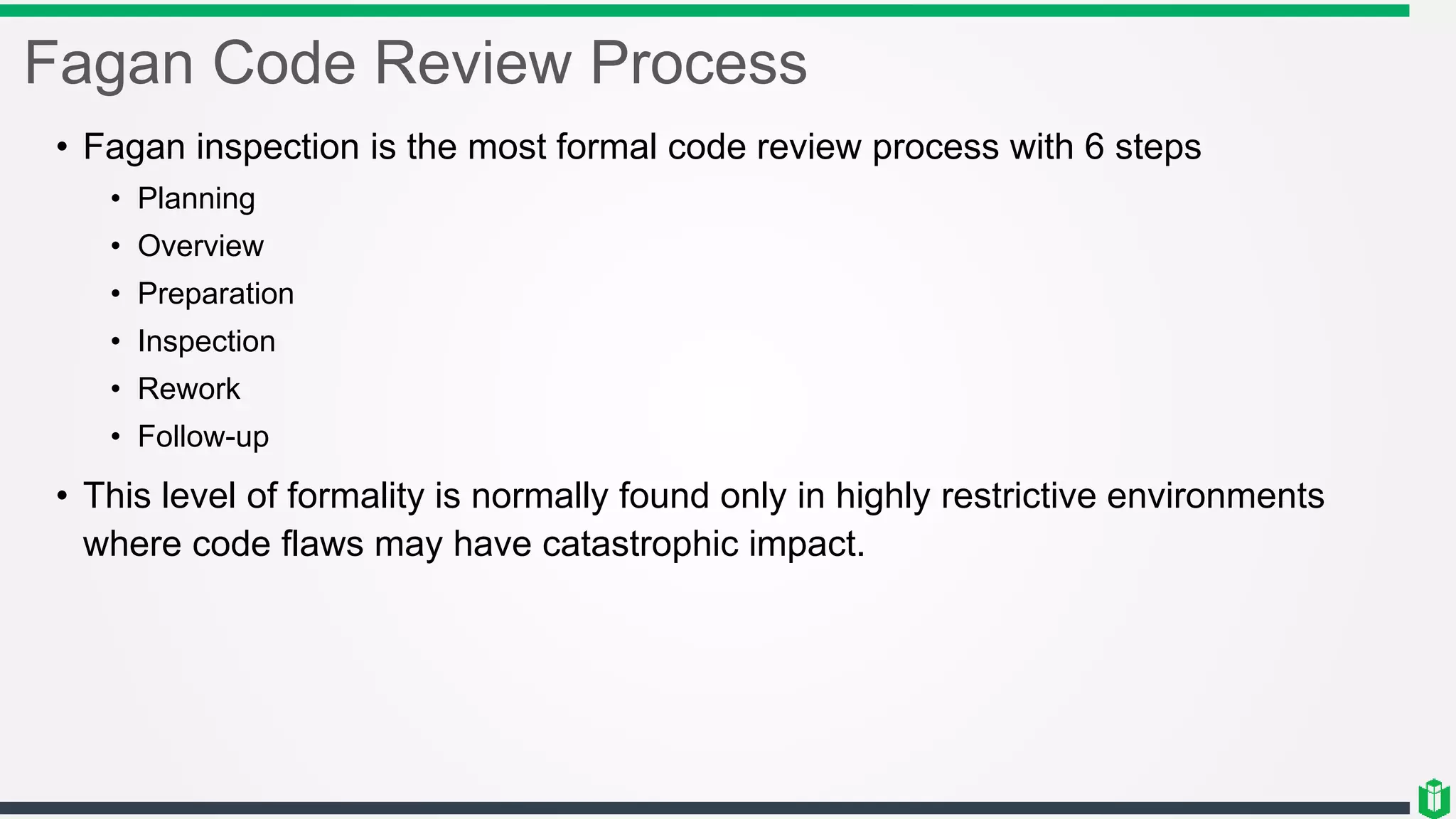
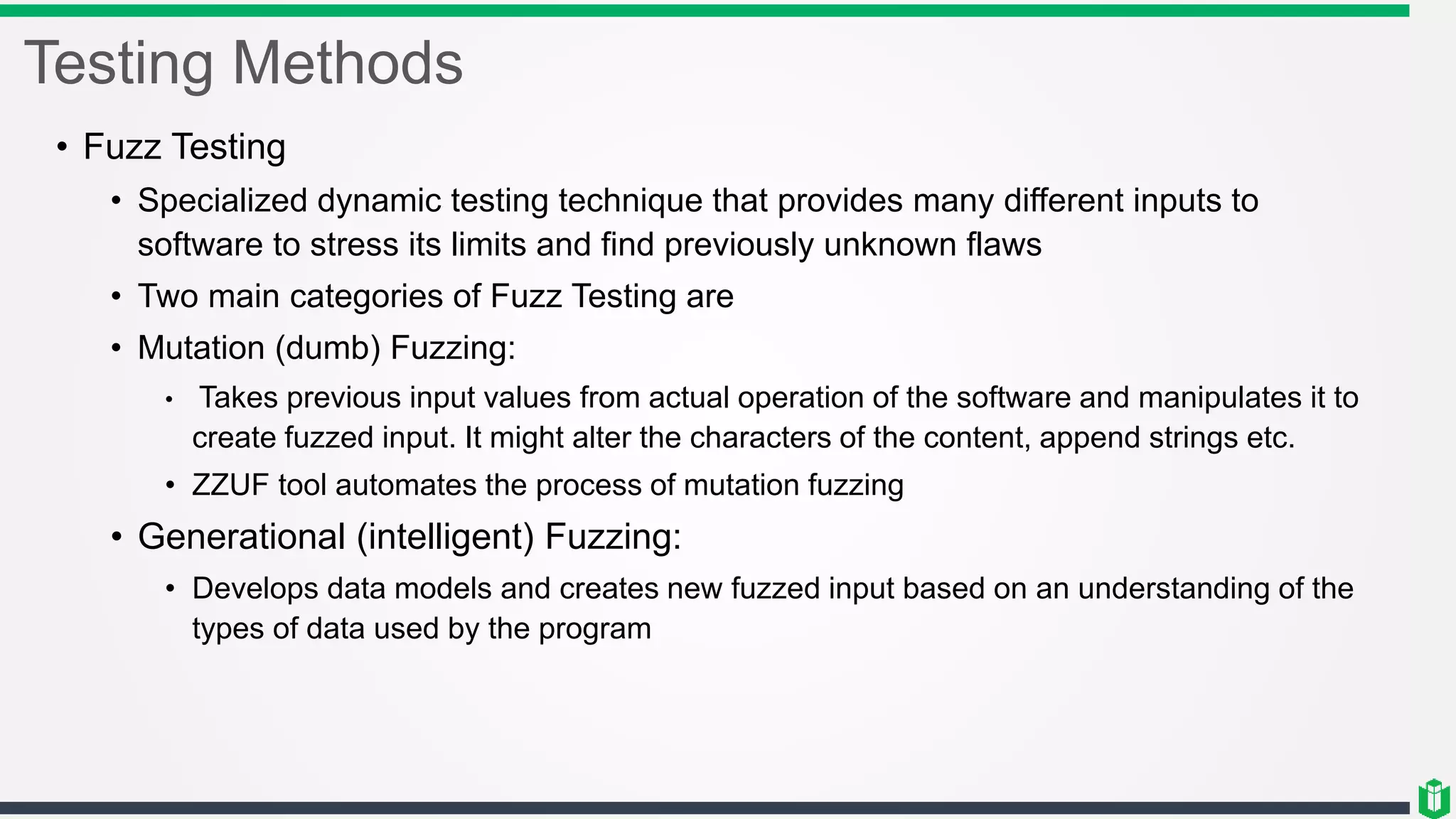
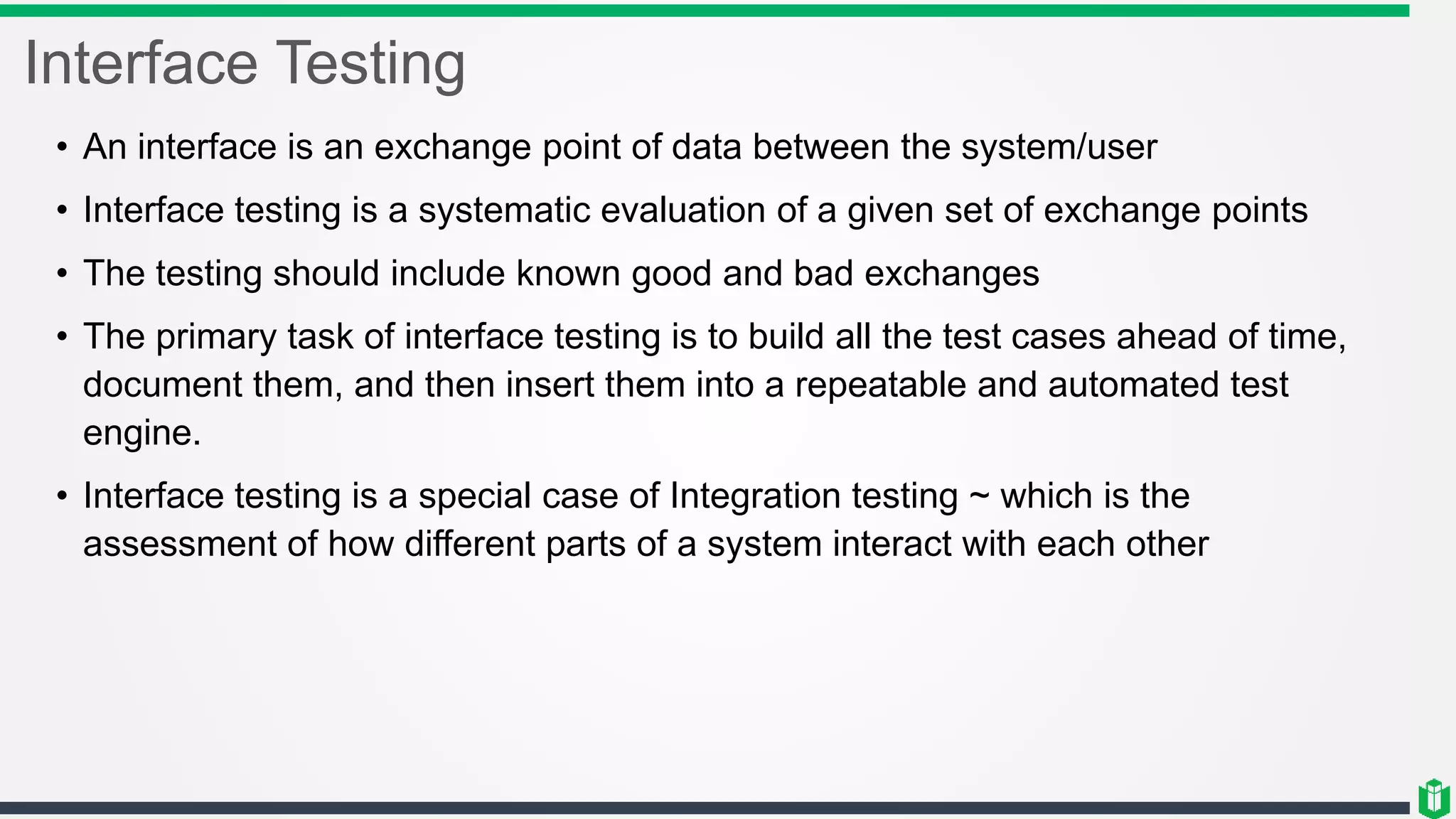
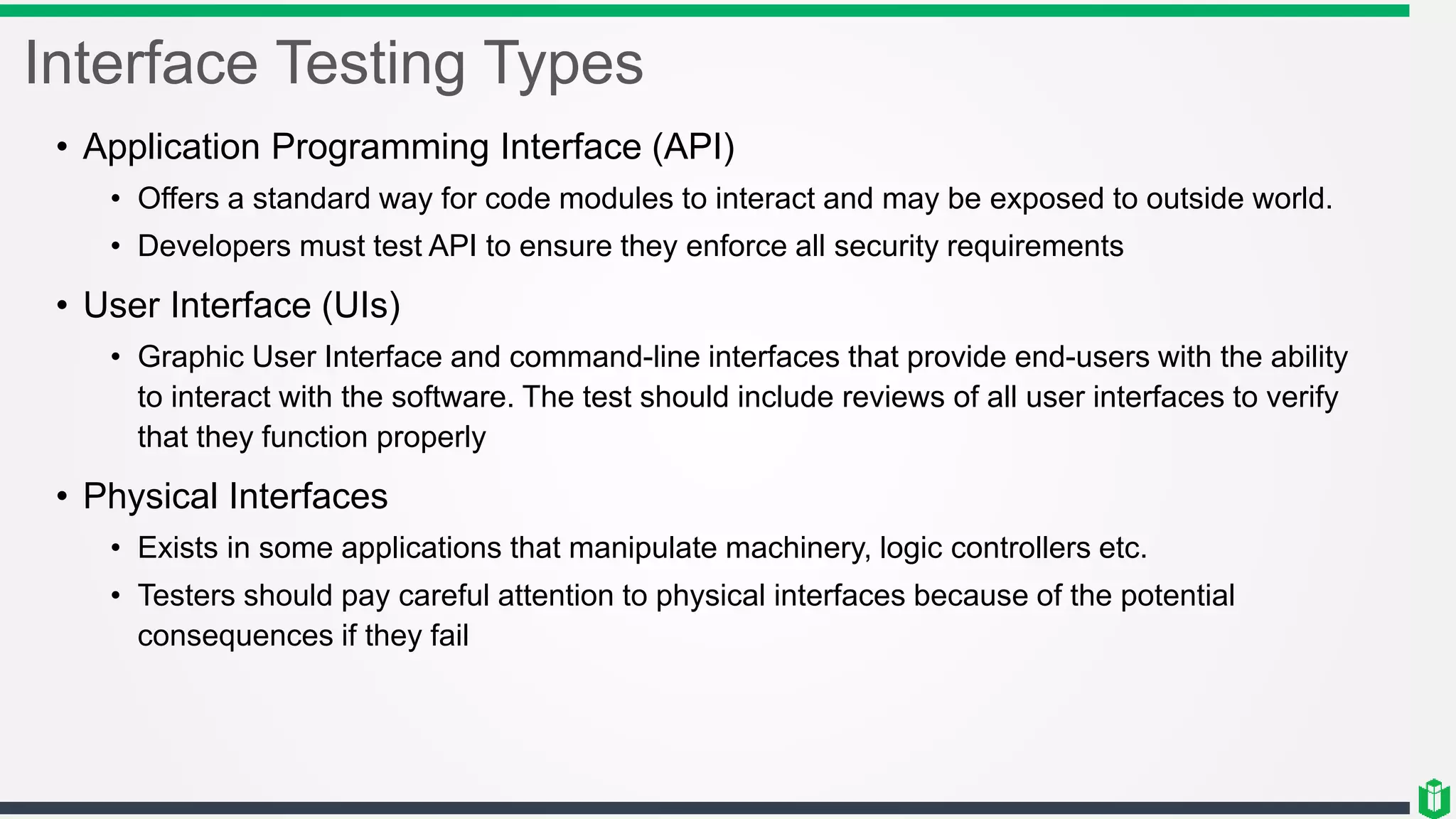
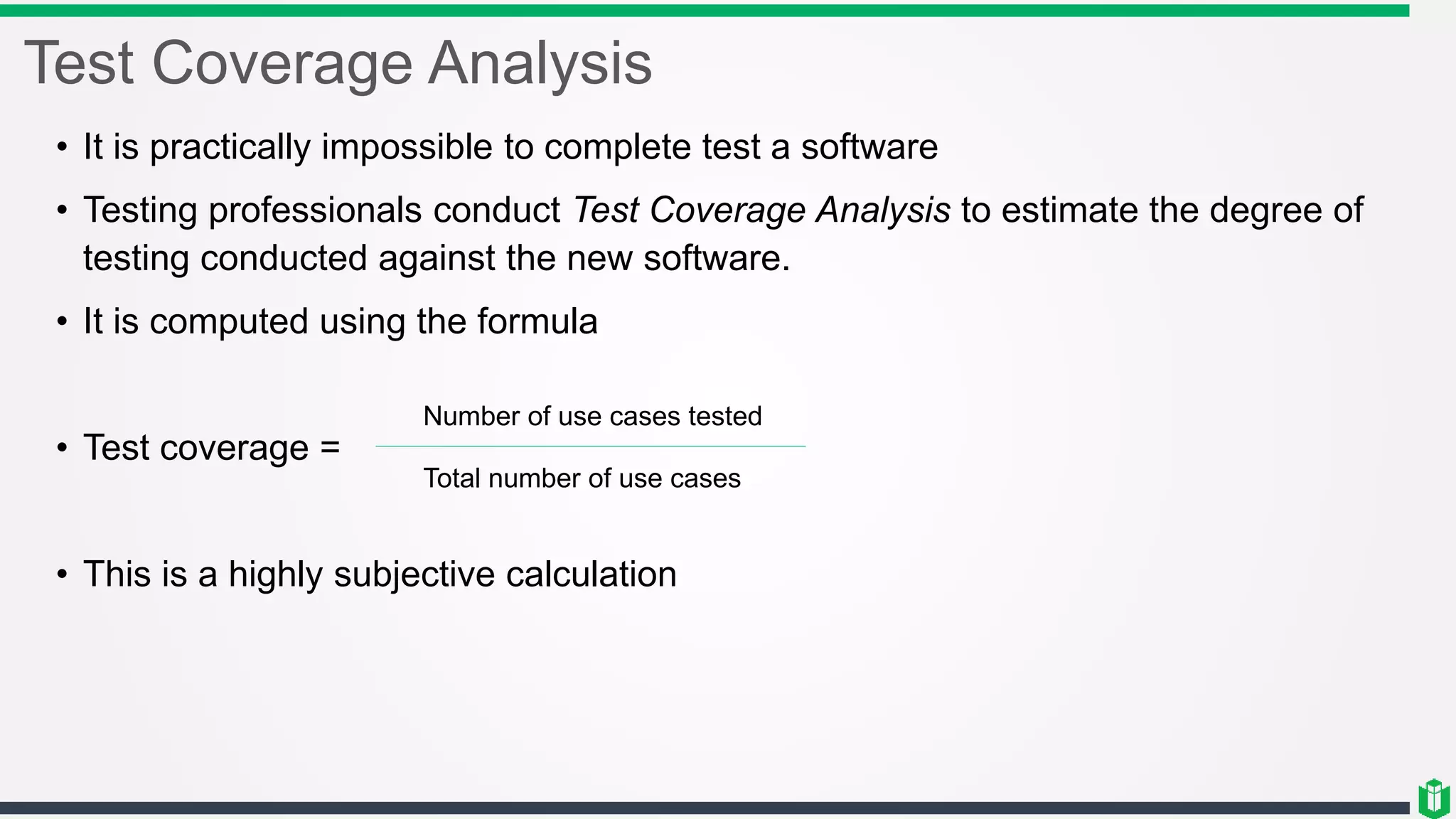
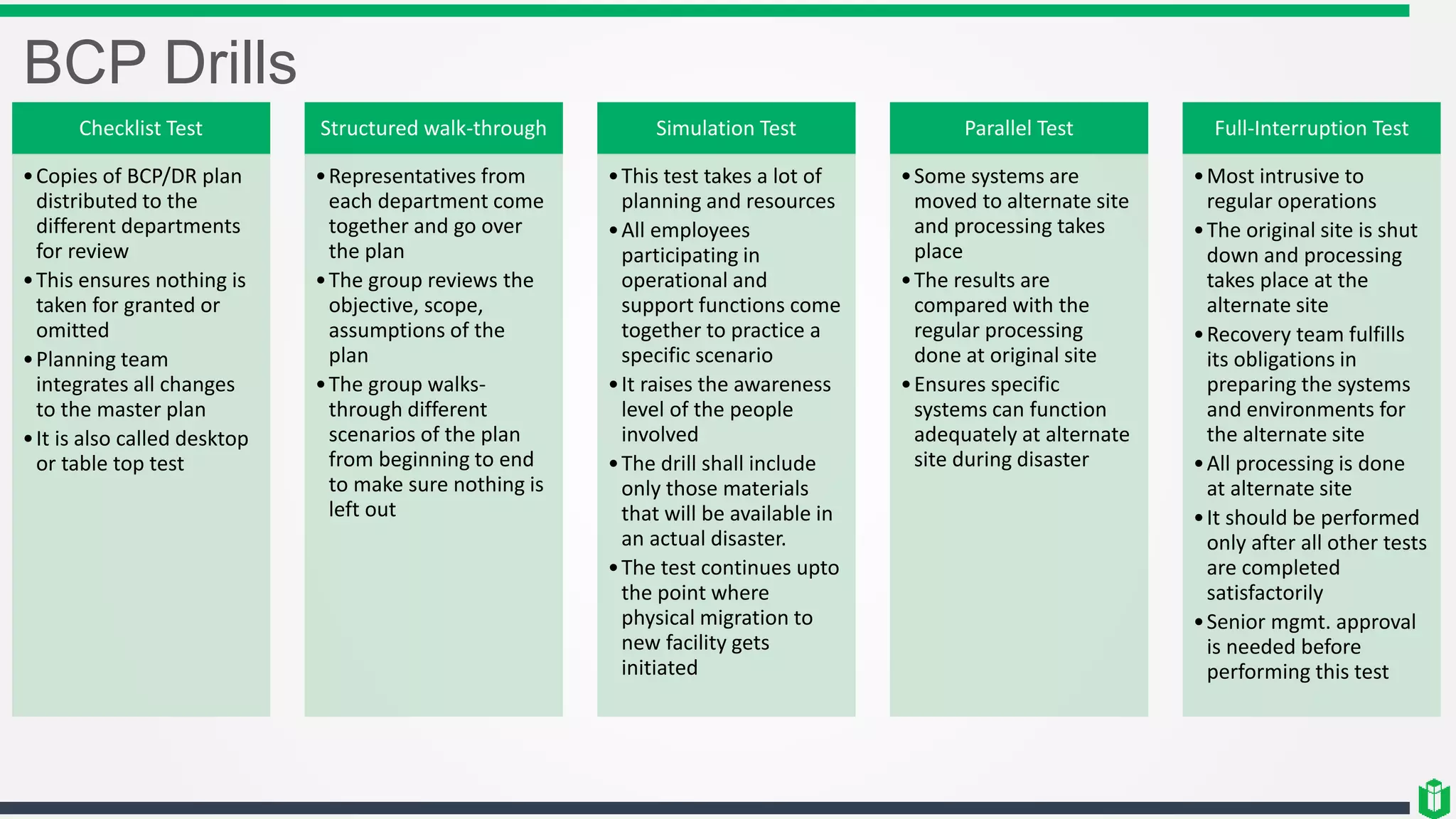
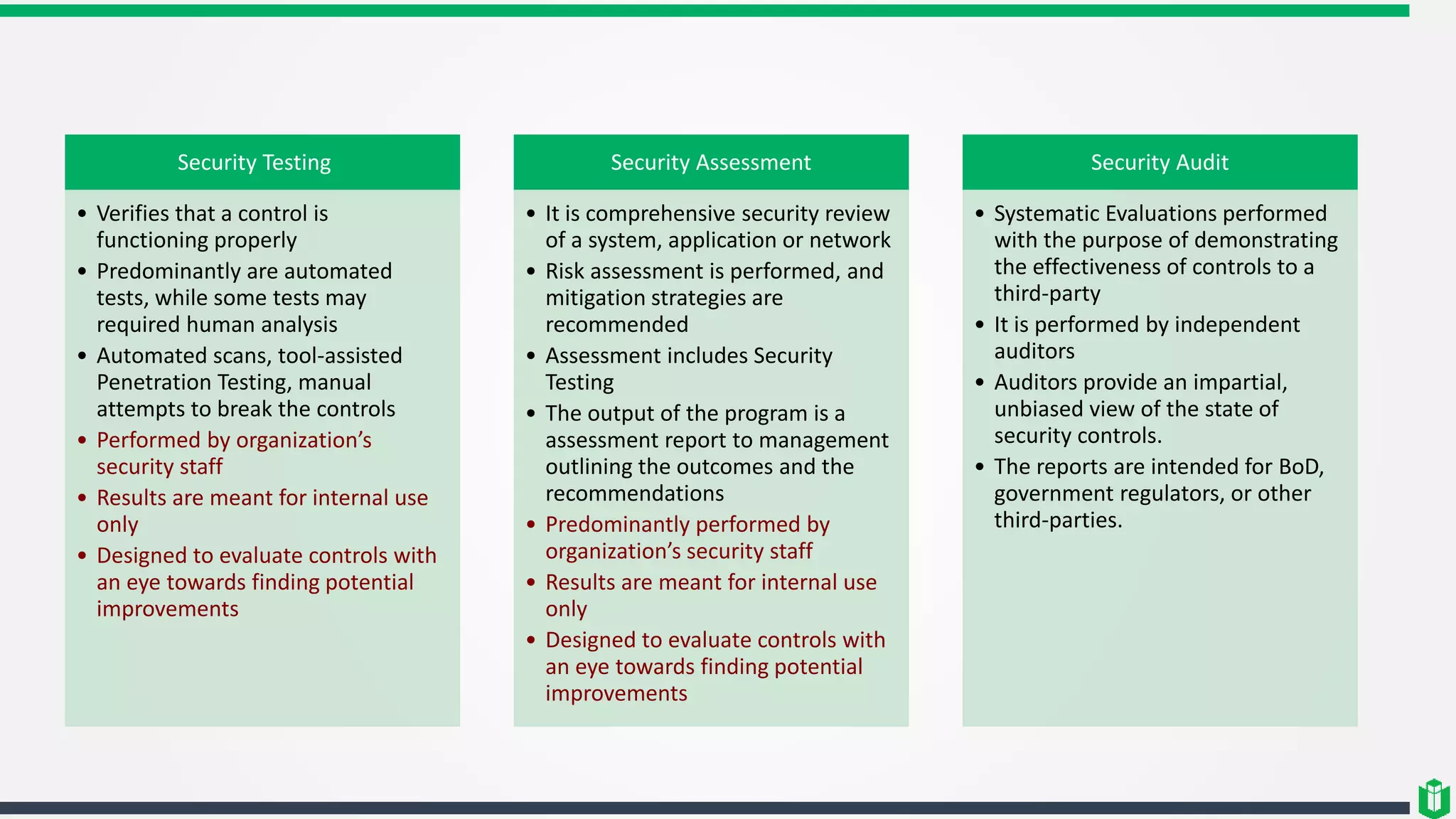
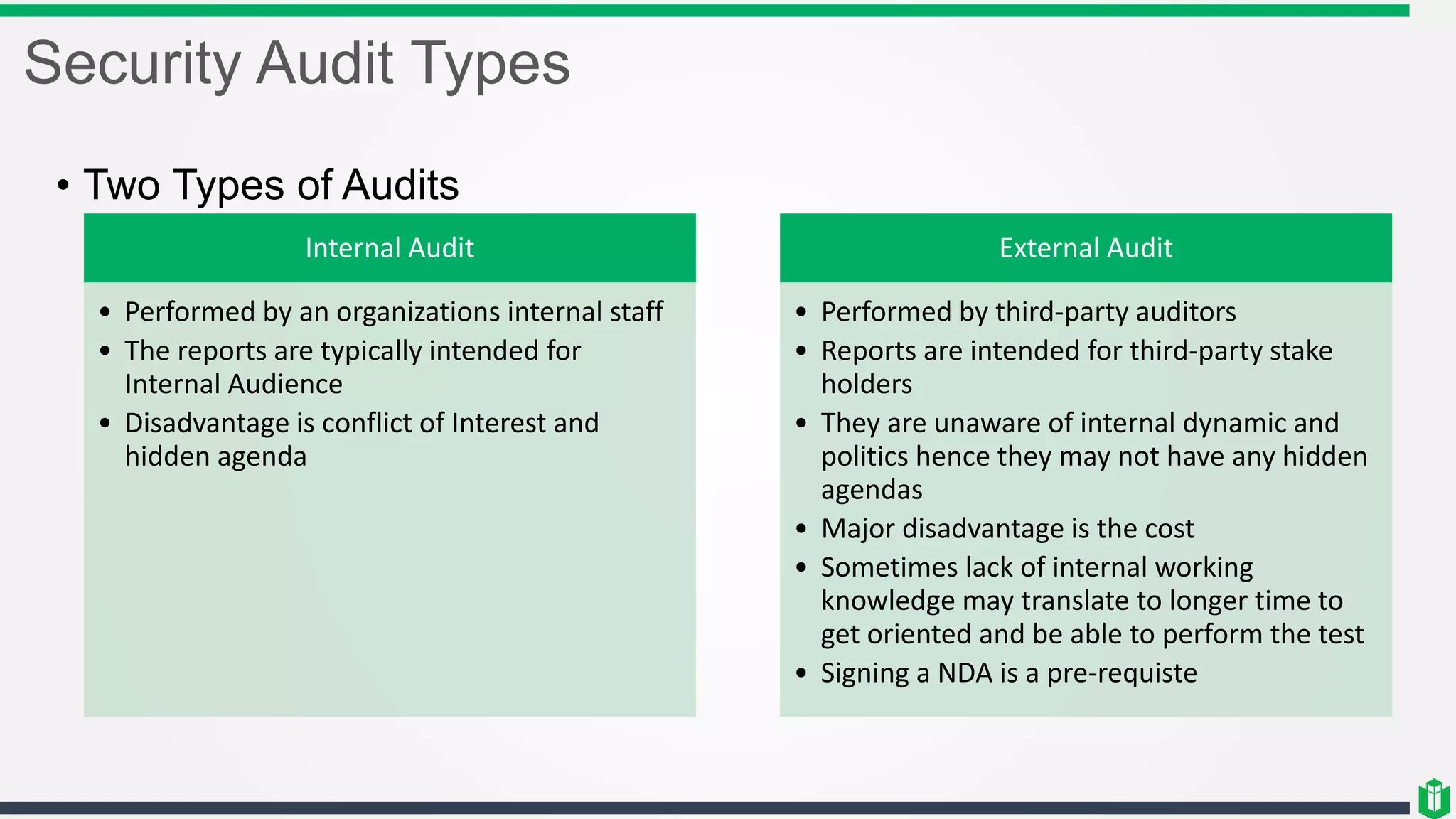
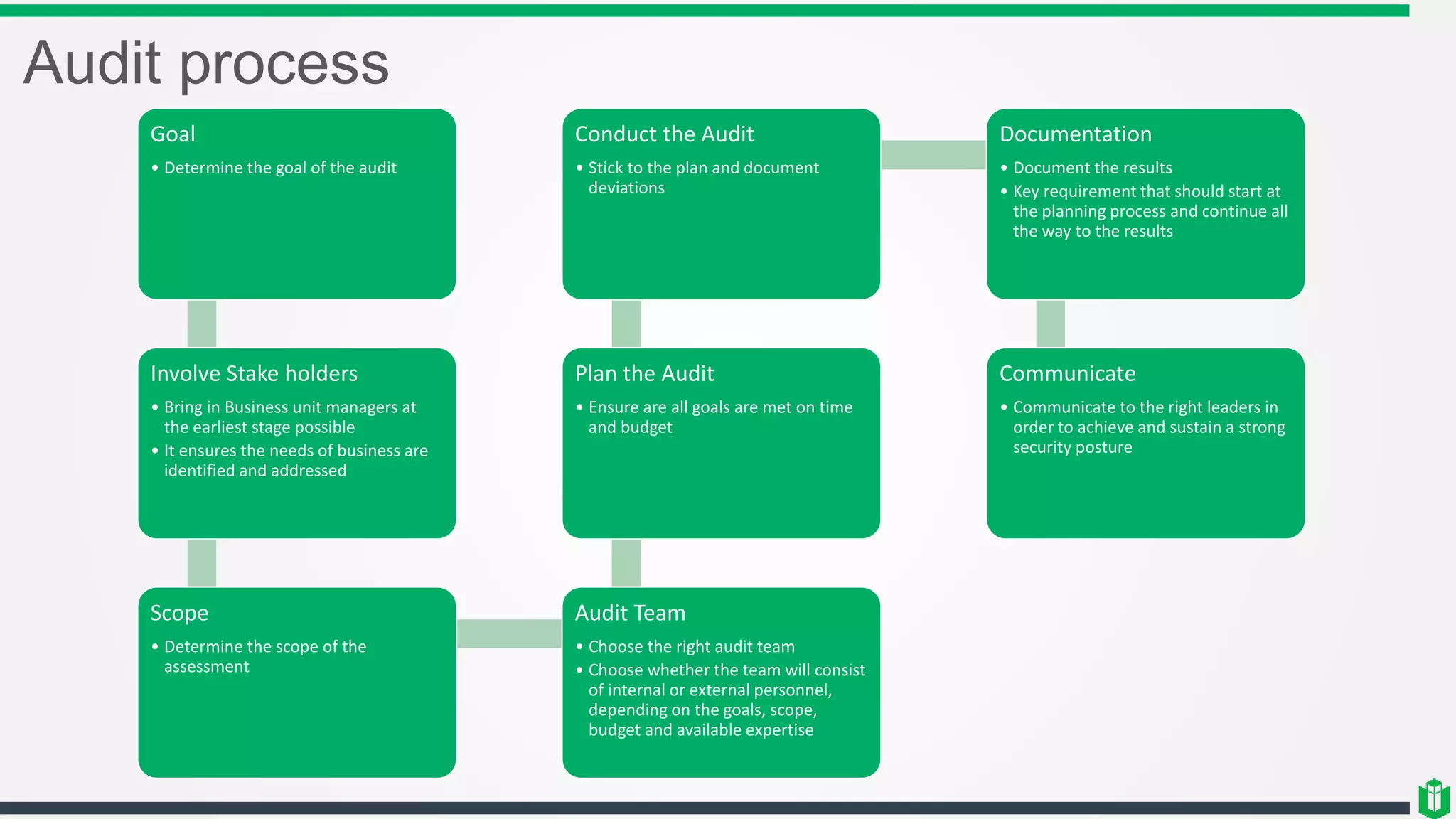
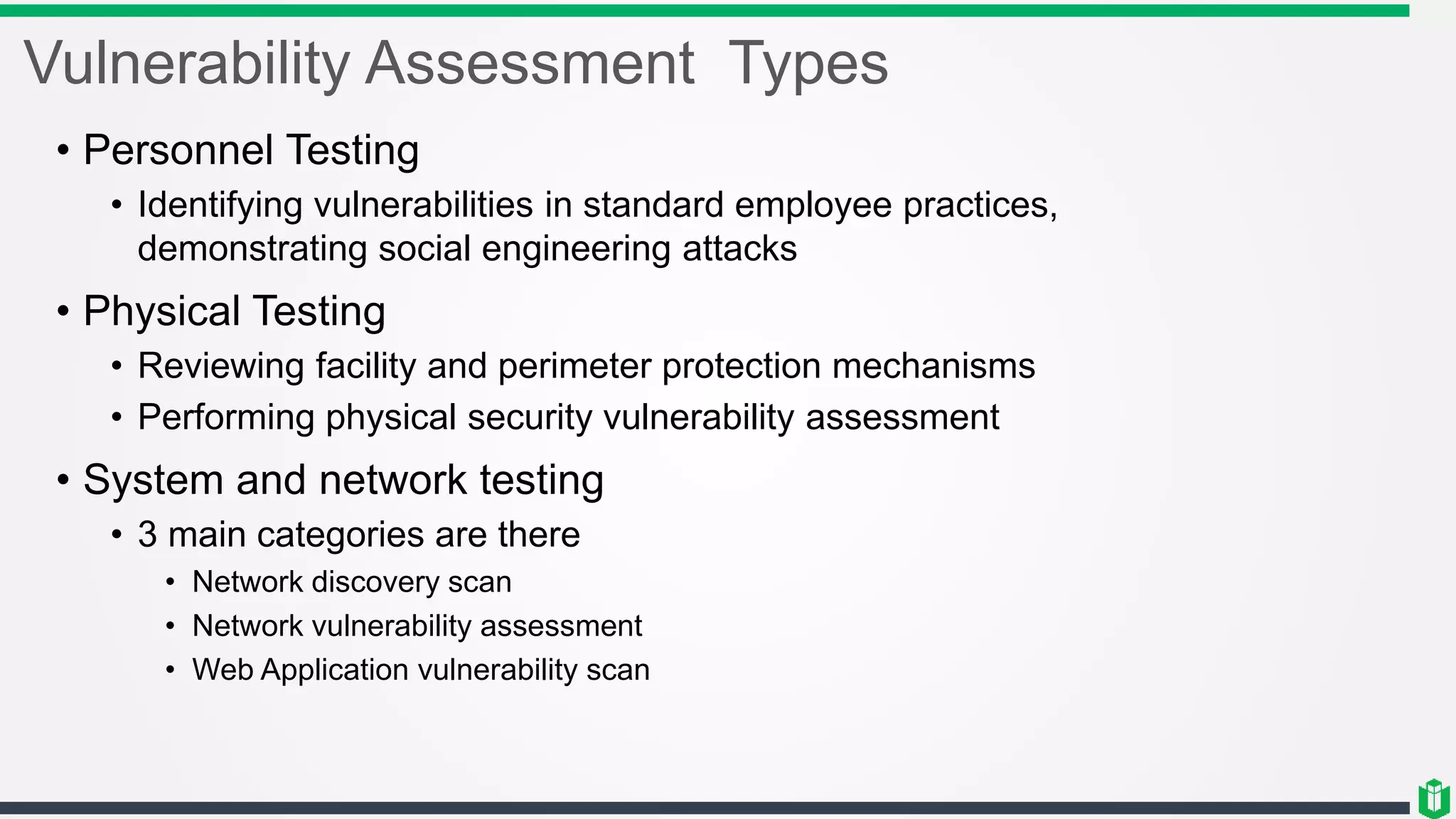
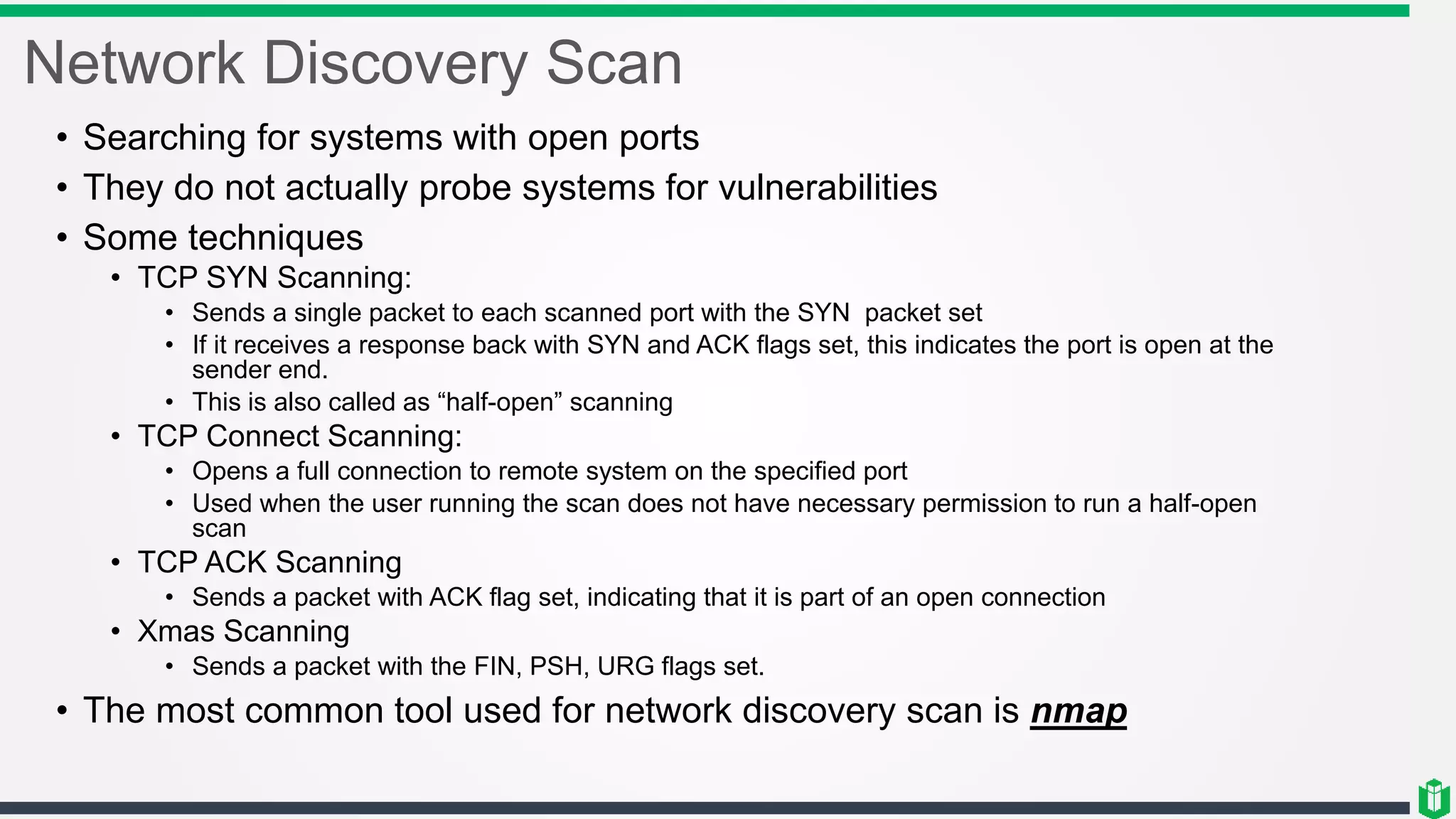
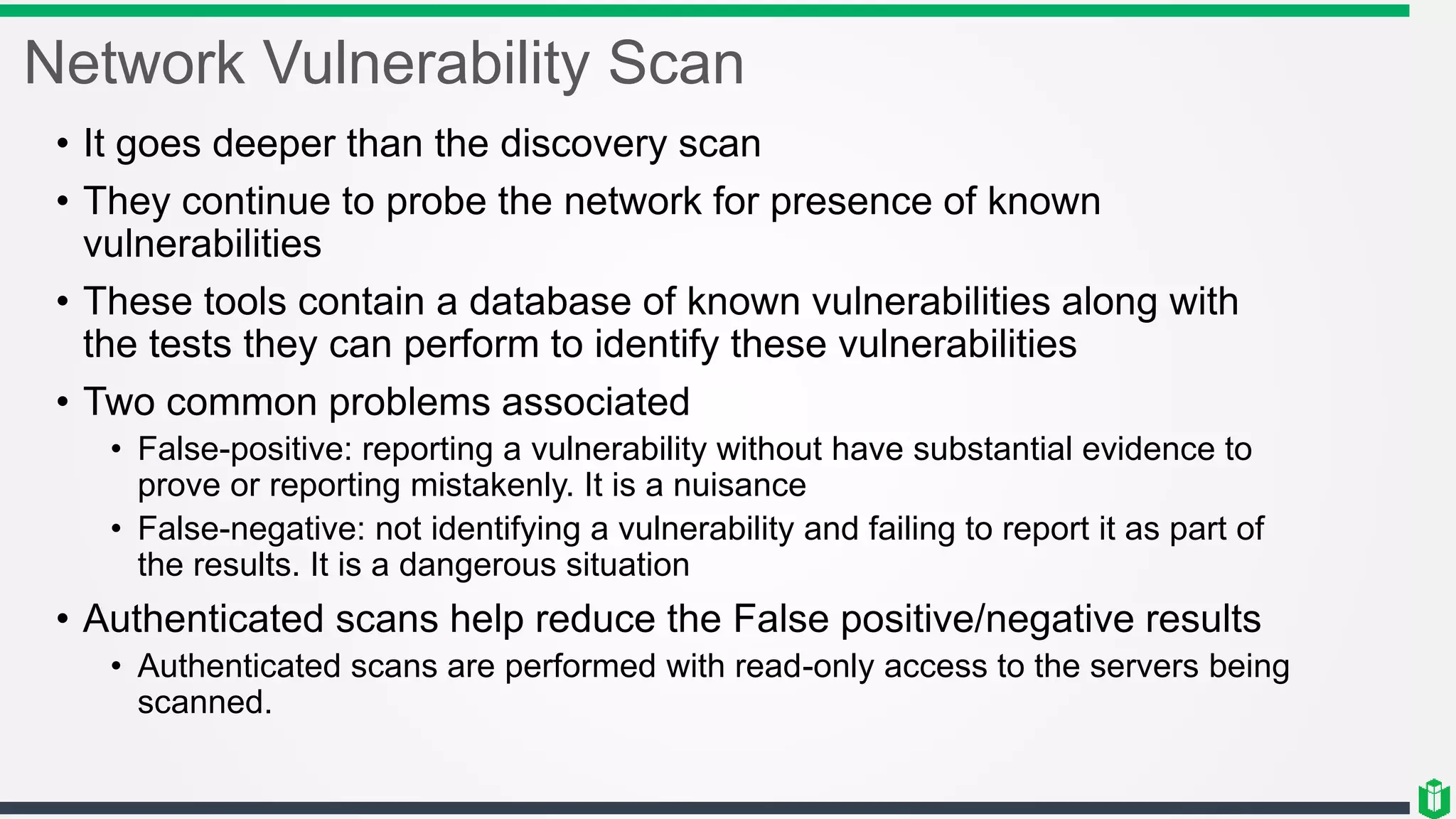
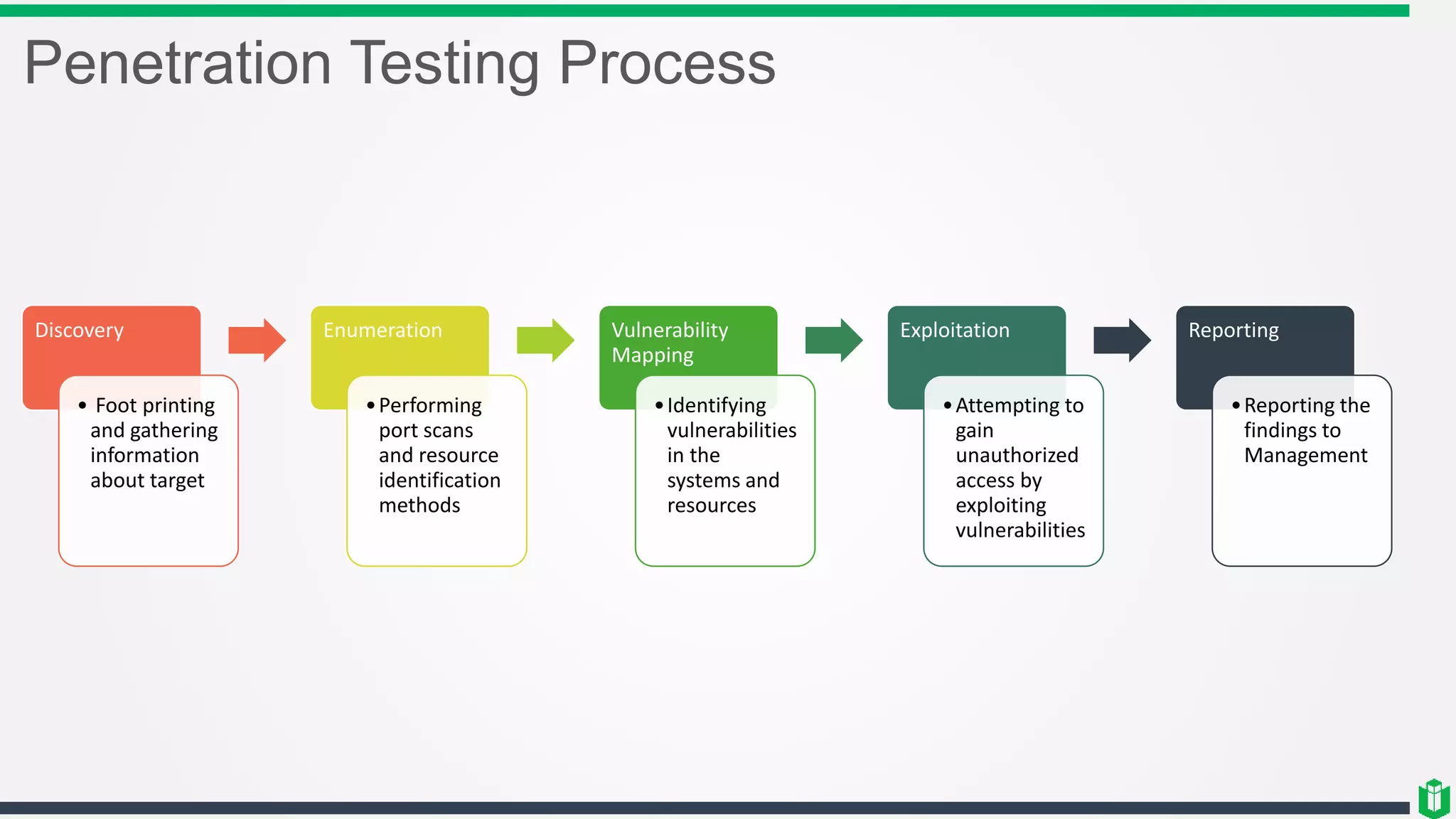
There are three main components of security assessment and testing: security tests, security assessments, and security audits. Security tests verify controls are functioning properly through automated and manual tests. Security assessments perform comprehensive reviews of systems and networks to identify risks and recommend mitigations. Security audits systematically evaluate controls to demonstrate effectiveness to third parties. Other topics covered include penetration testing, vulnerability assessments, code reviews, logging, and different testing methods.




![Penetration/ Vulnerability testing Types
Black box testing
[Zero Knowledge]
• The tester has no prior
knowledge of the internal
design or features of the
system
• It simulates the external
attacker best
• Disadvantage is that it will
probably not detect all
vulnerabilities
• Another disadvantage is that
the testing team may
inadvertently impact
another system
White box testing
[Full Knowledge]
• The tester has complete
knowledge of the internal
system
• Allows test team to target
specific internal controls and
features
• It may yield a more complete
result
• It may not be representative
of an external hacker
Gray box testing
[Partial knowledge]
• Some Information about
internal working is given to
the tester.
• It helps guide their tactics
towards areas we want to
have thoroughly tested
• This approach mitigates the
risks of the other two
models](https://image.slidesharecdn.com/chapter6-securityassessment-170706151434/75/CISSP-Security-Assessment-16-2048.jpg)