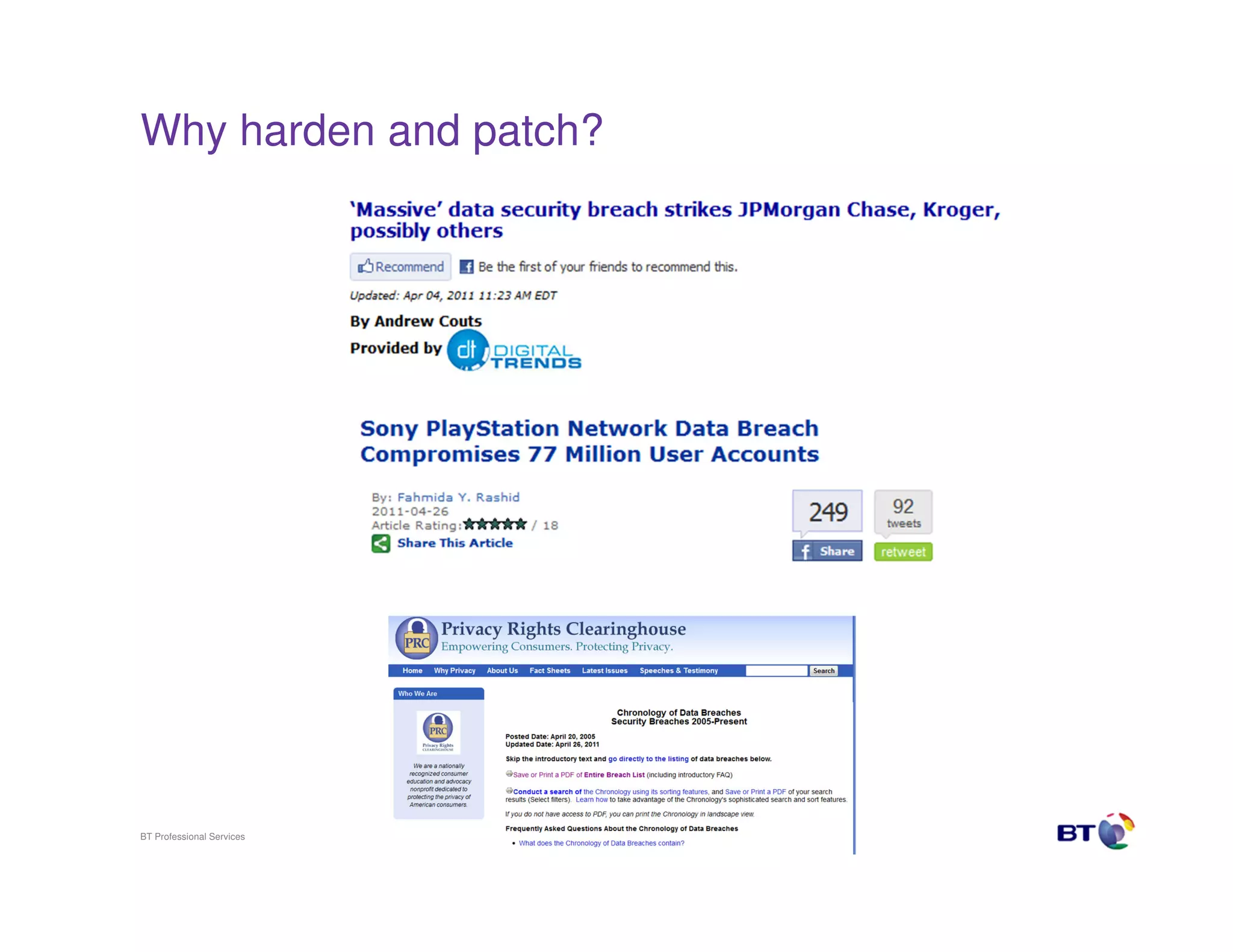
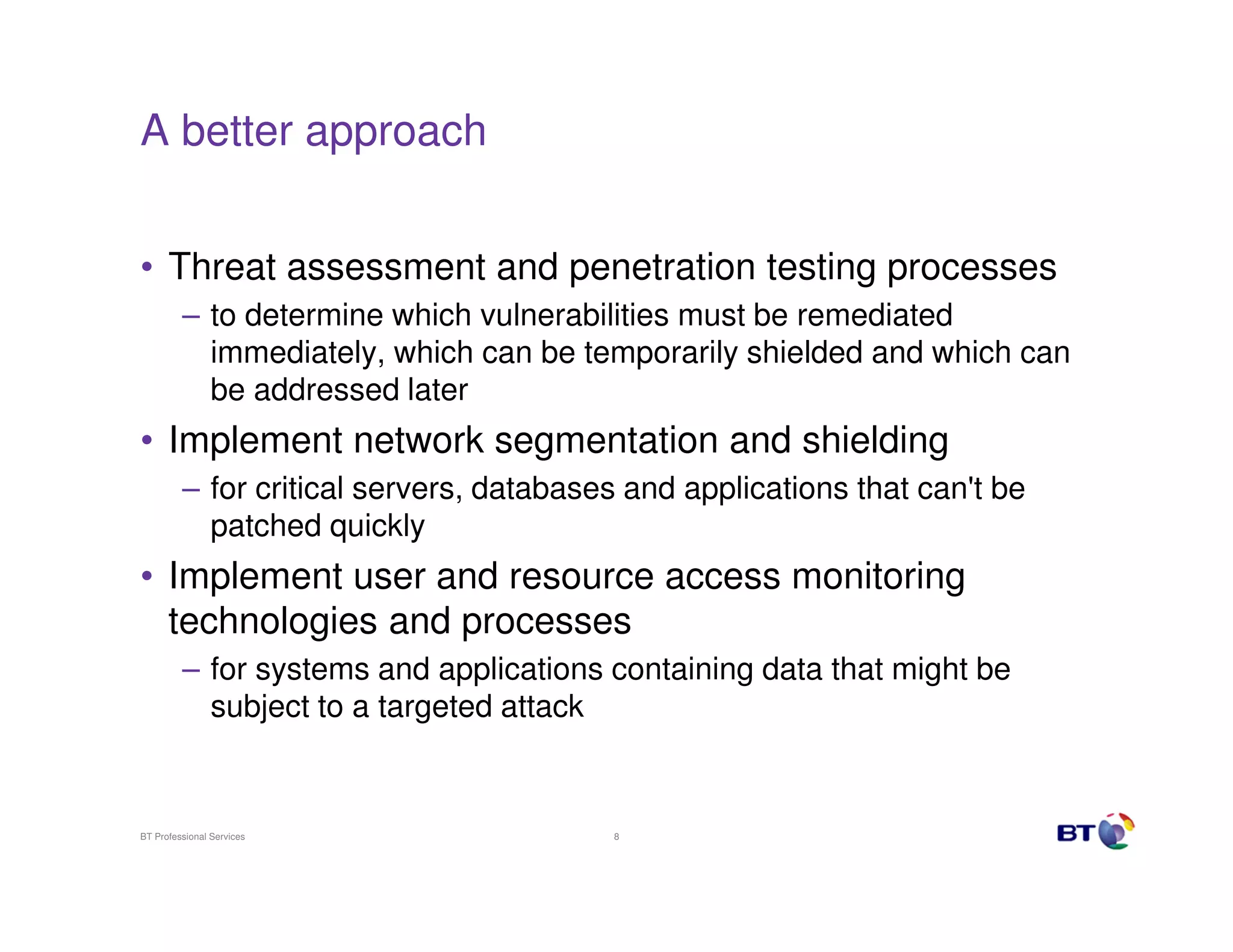
The document discusses approaches to securing systems when rapid patching is not possible. It recommends implementing network segmentation, monitoring technologies, and user access controls to shield vulnerable systems that cannot be patched quickly. While patching is important, it is not a panacea, and targeted attacks use other vectors beyond exploiting unpatched vulnerabilities. A proactive application security program integrated into the development lifecycle can help mitigate issues before exploits are found. When patching is truly not possible, additional defenses like host-based IPS, firewalls, and encryption should be used to minimize risk.