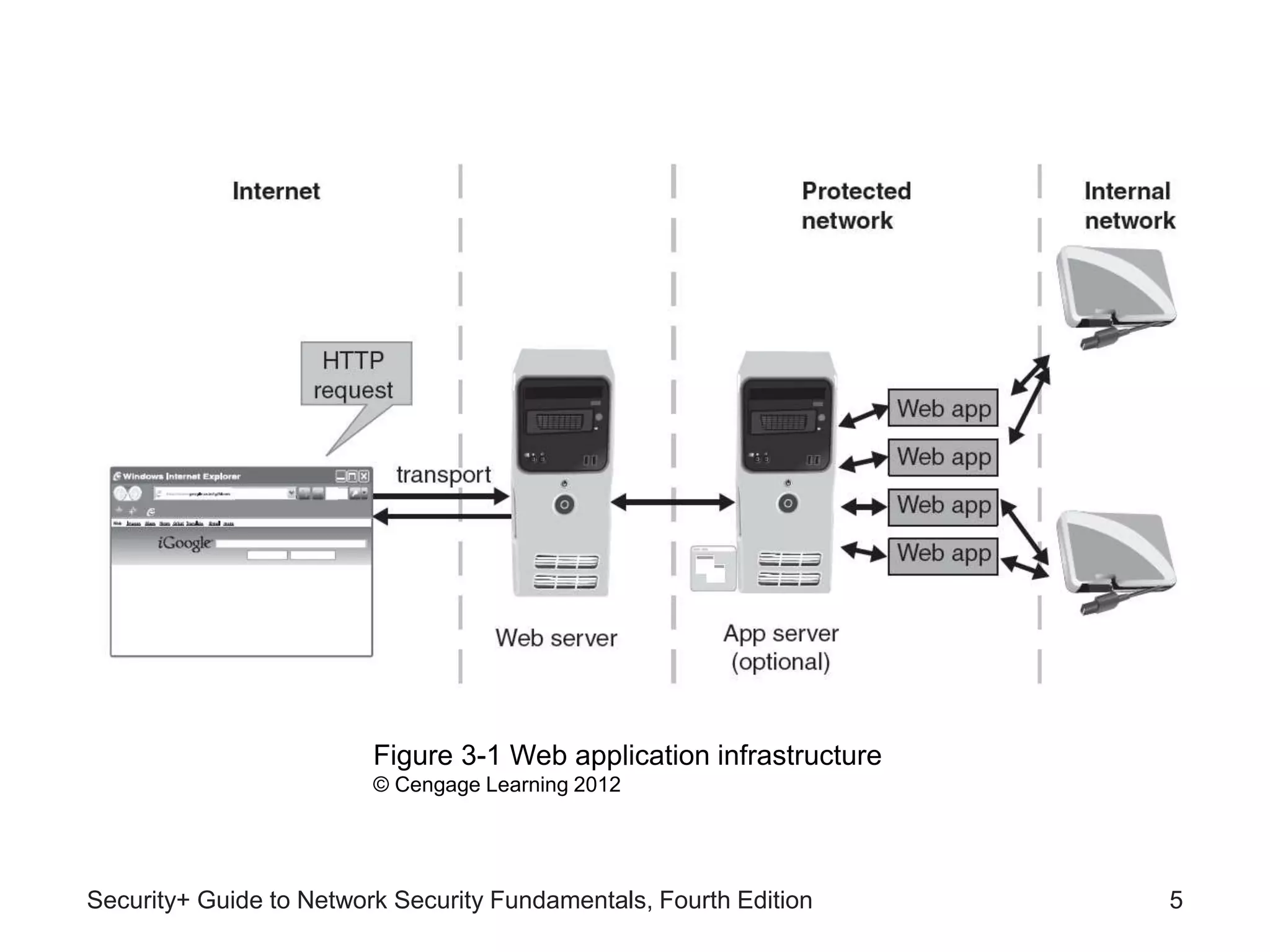
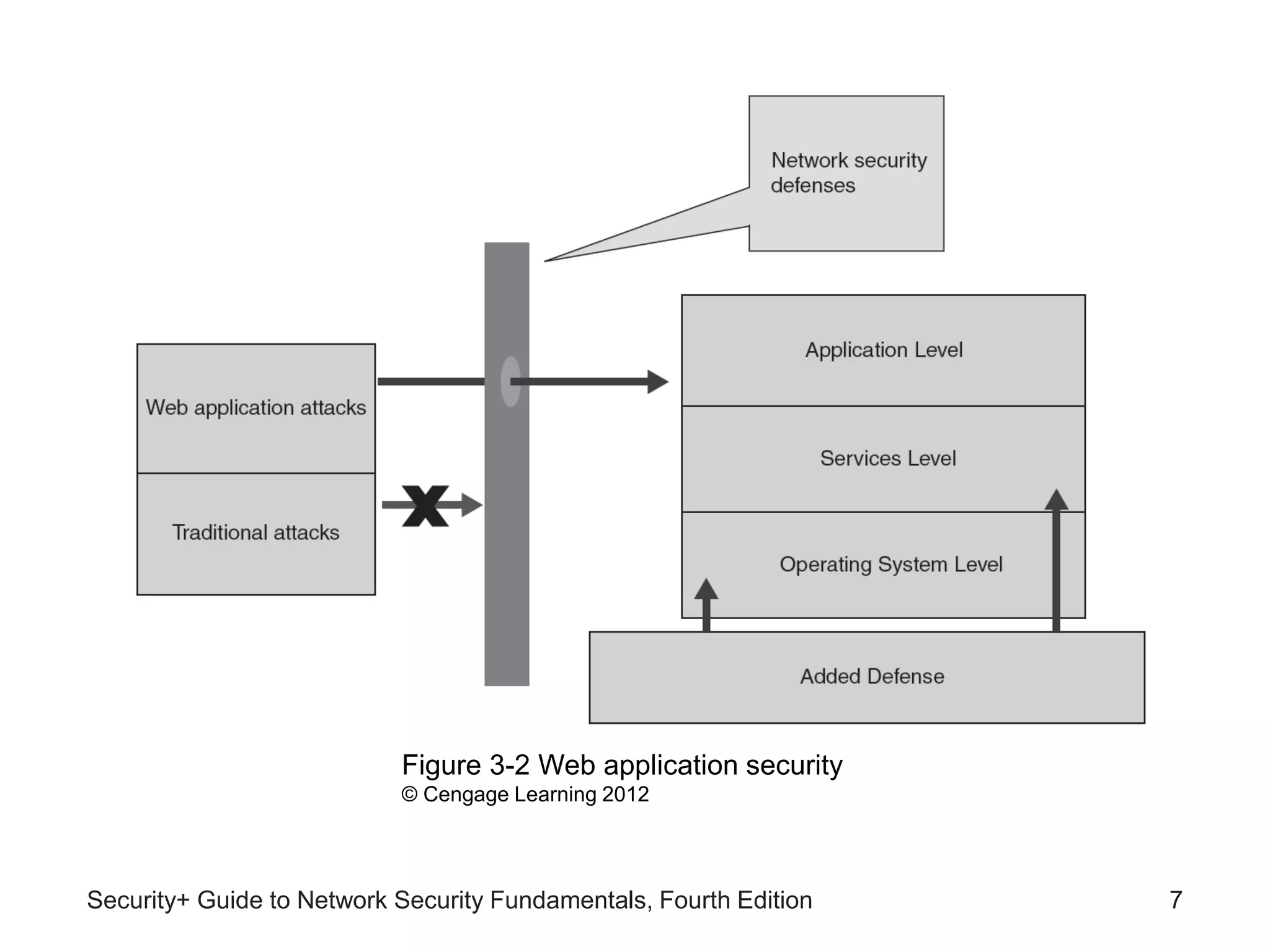
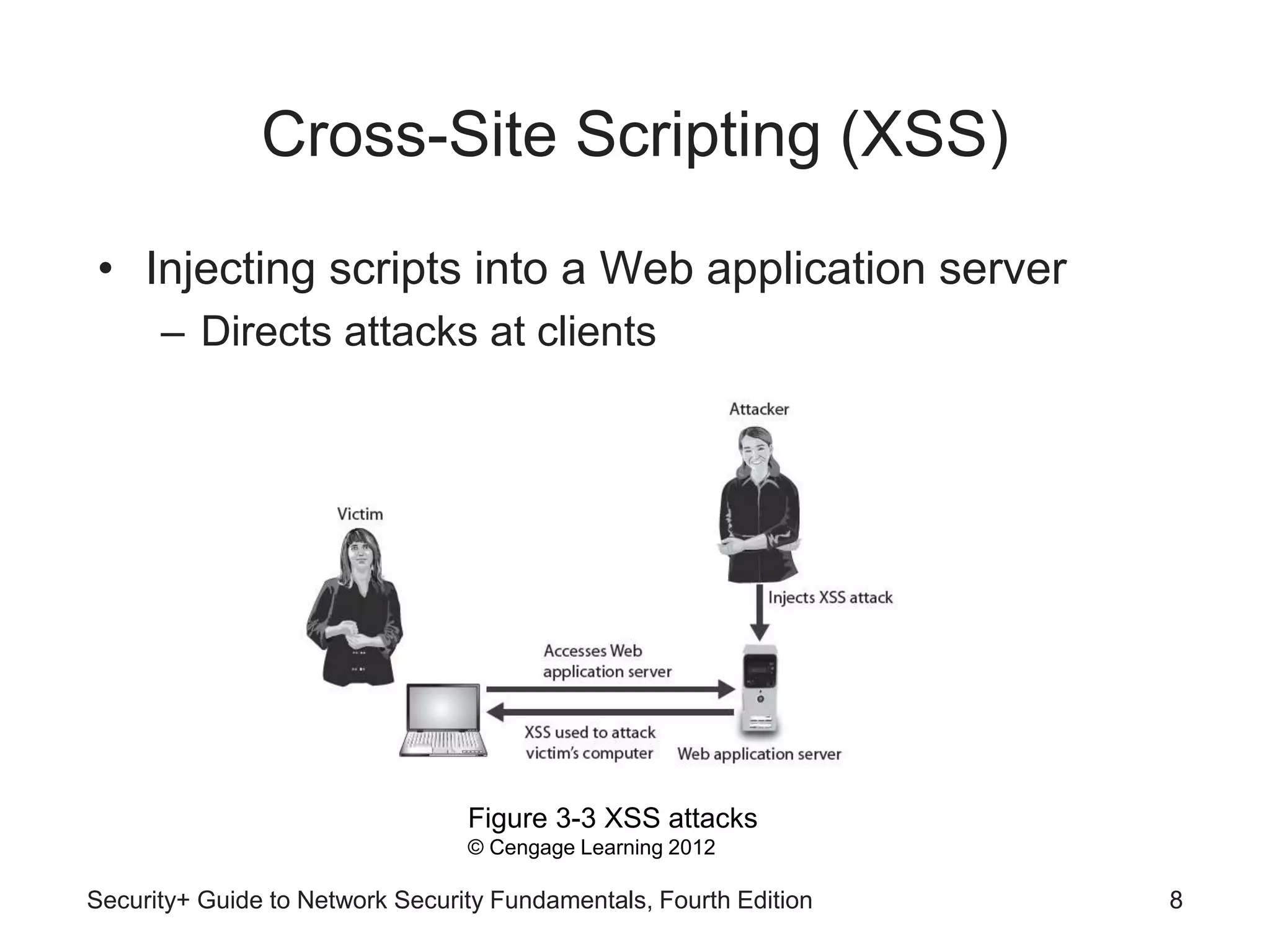
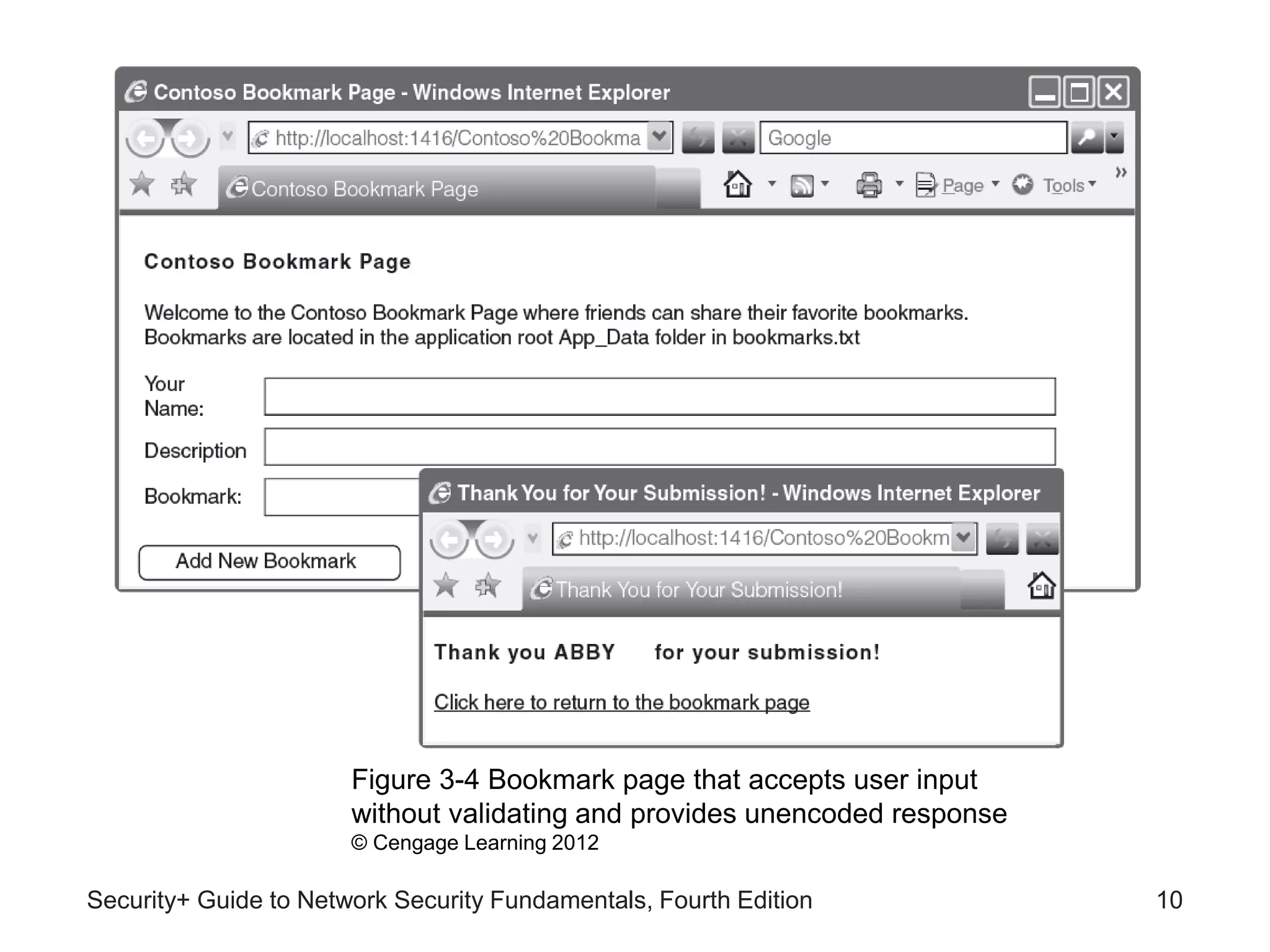
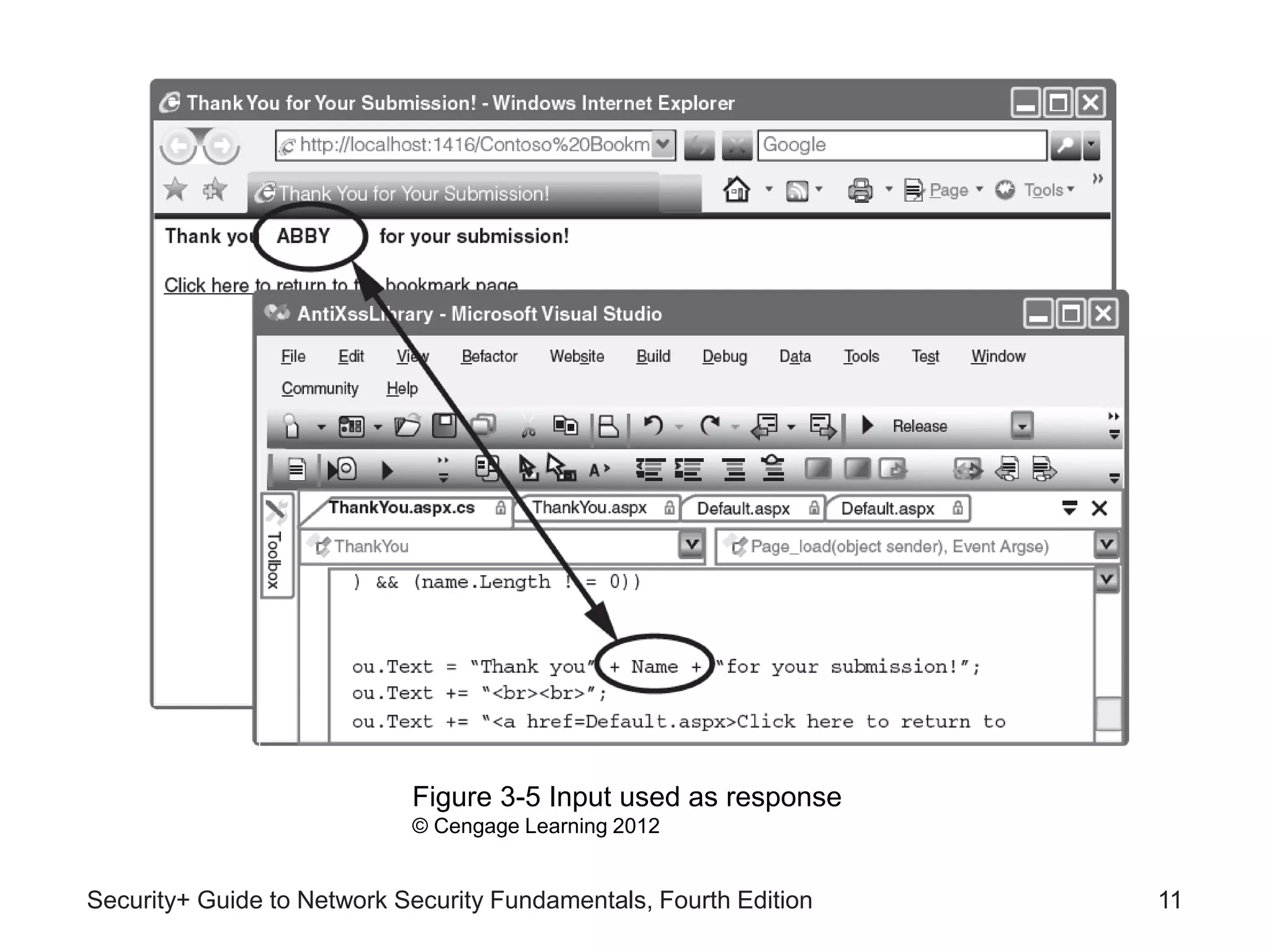
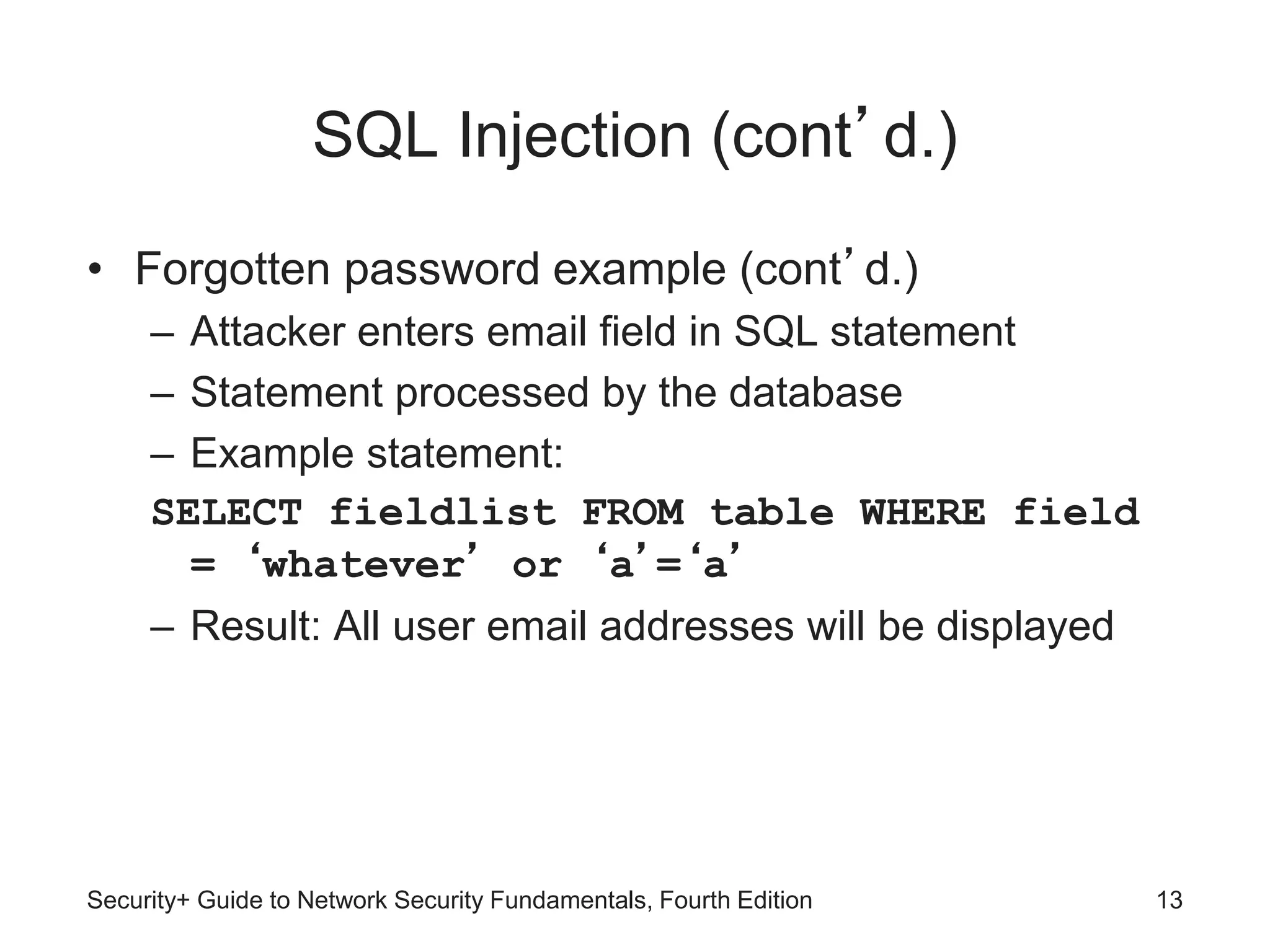
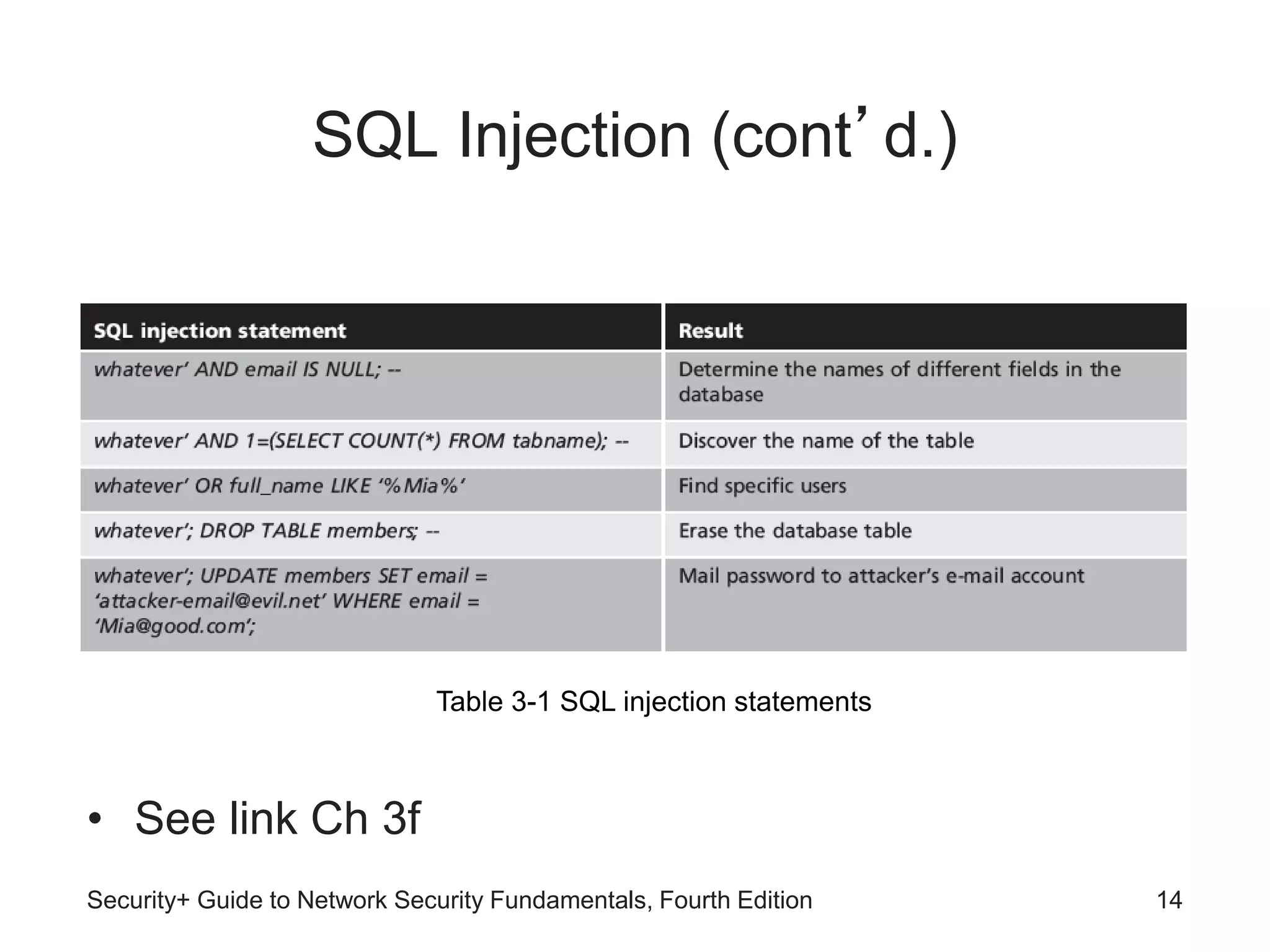
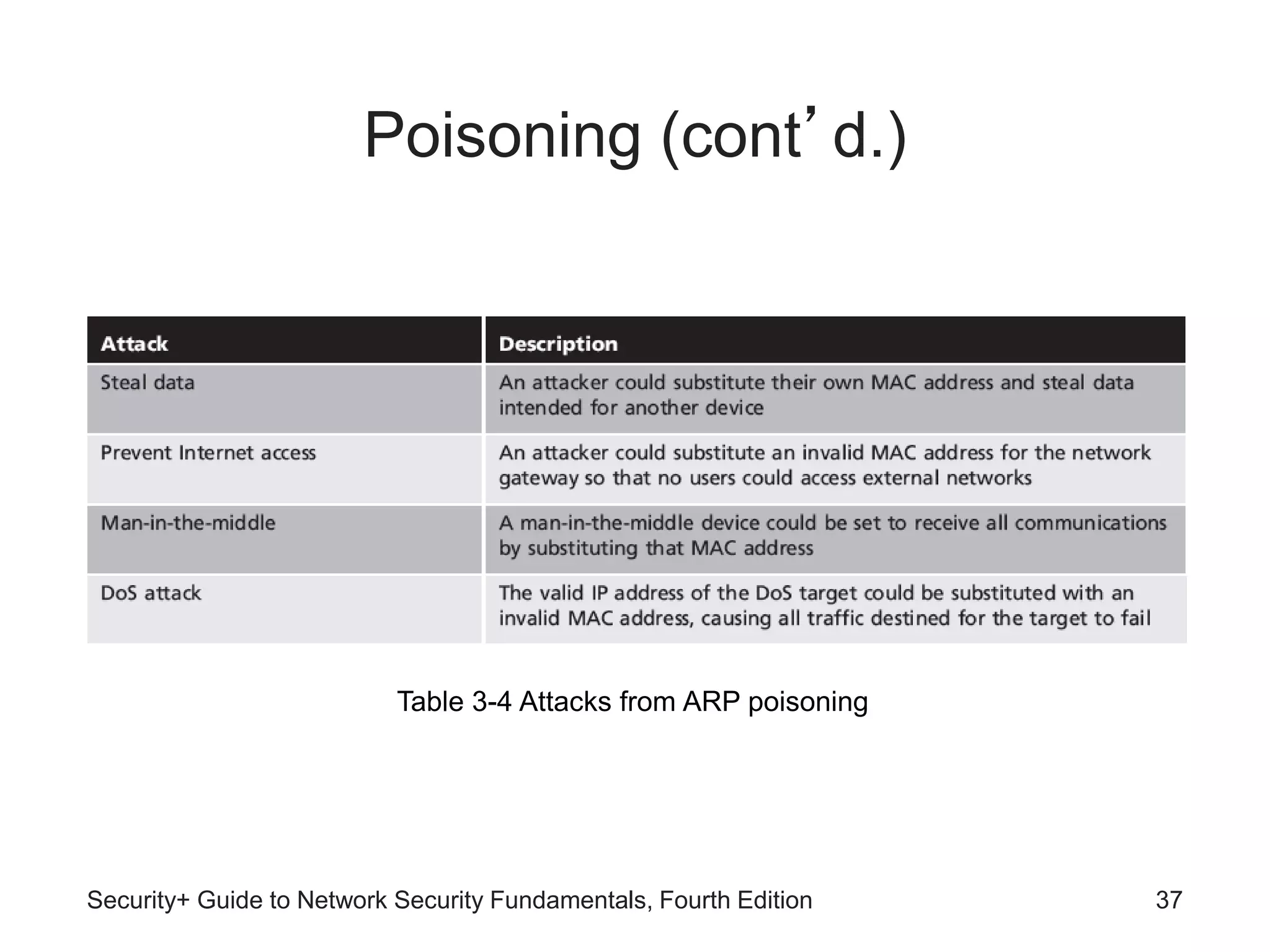
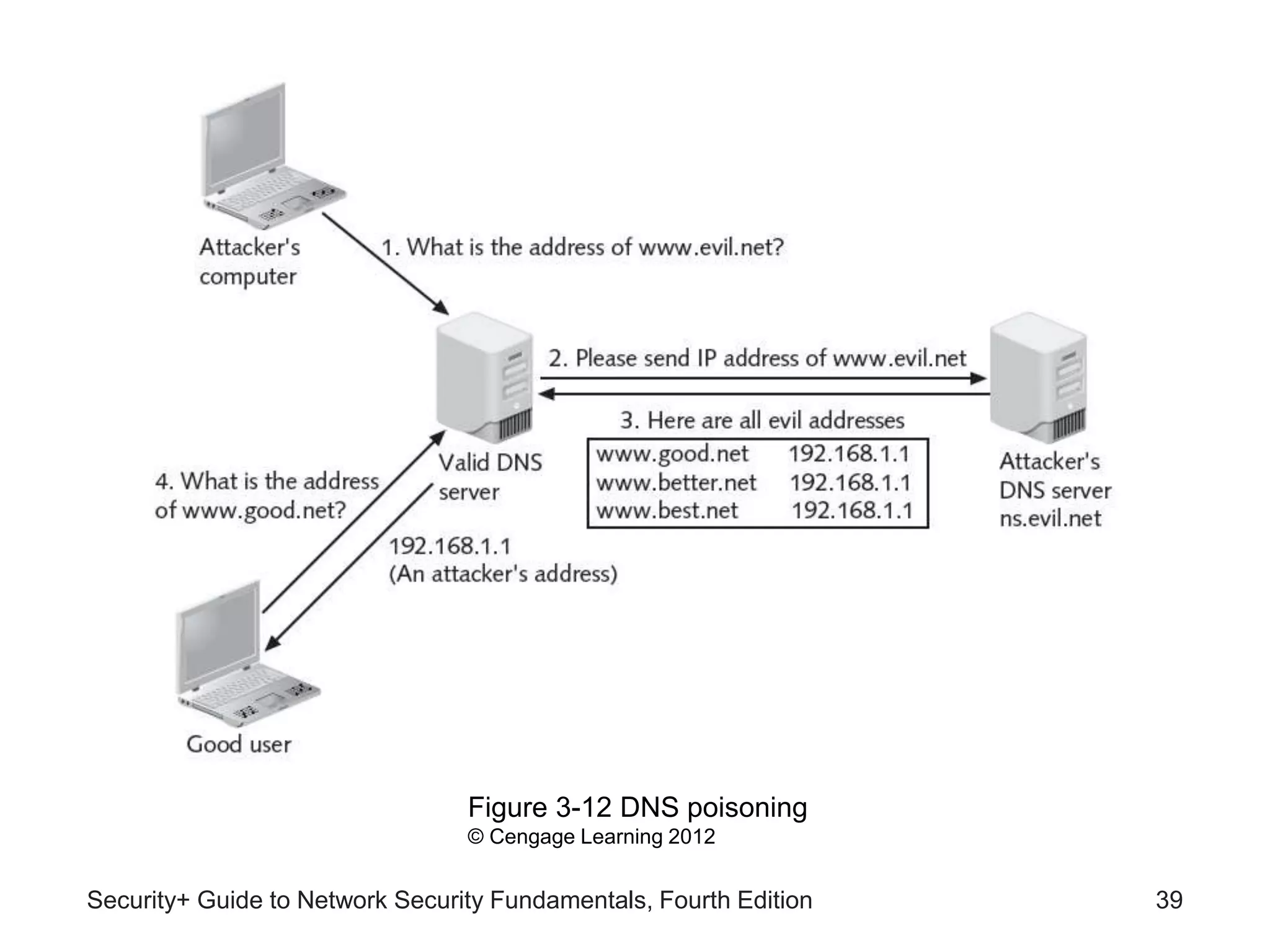
This chapter discusses different types of application and network attacks. It covers web application attacks like cross-site scripting and SQL injection that target vulnerabilities in web applications. It also covers client-side attacks that compromise client computers through drive-by downloads or header manipulation. Additionally, it discusses network-based denial of service attacks and interception attacks like man-in-the-middle attacks that intercept legitimate communications. The chapter aims to explain how buffer overflow attacks and session hijacking work, as well as the risks of cookies, attachments, and malicious browser add-ons.