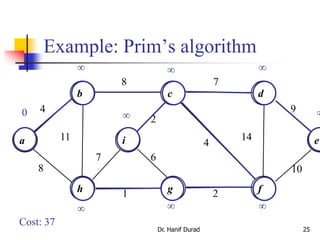
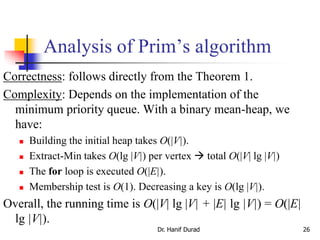
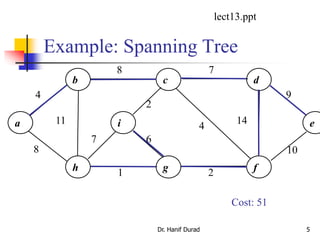
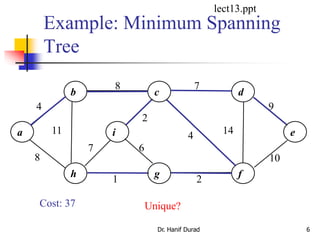
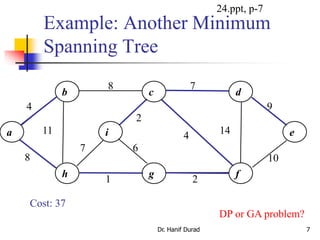
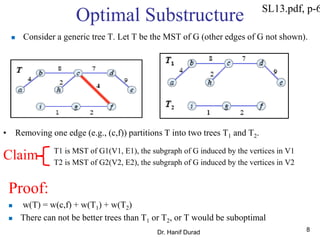
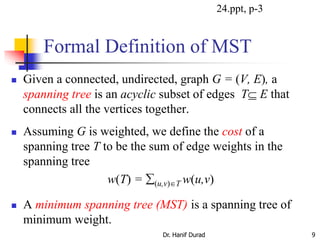
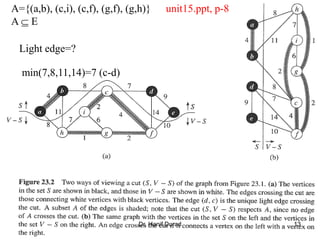
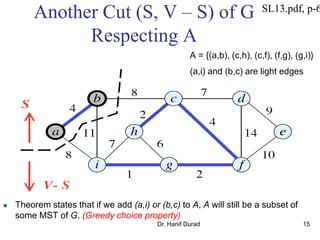
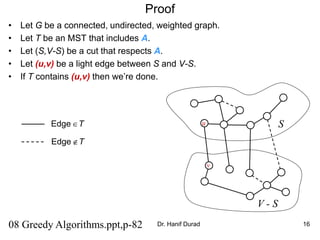
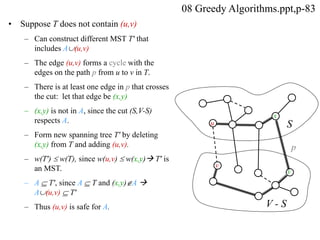
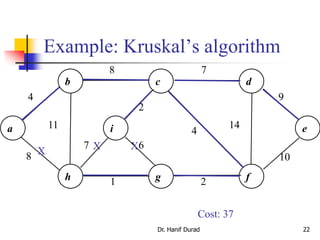
This document summarizes key concepts about minimum spanning trees from a lecture by Dr. Muhammad Hanif Durad. It discusses motivation for finding minimum spanning trees, properties of MSTs, and algorithms like Kruskal's algorithm and Prim's algorithm for finding an MST in polynomial time. Kruskal's algorithm finds the MST by greedily adding the minimum weight edge that connects two components in a forest. Prim's algorithm finds the MST by growing a tree by greedily adding the minimum weight edge connecting the growing tree to a vertex not yet included.













![Prim’s algorithm
MST-Prim(G, root)
for each vertex vV do
key(v) ∞; π[v] null
key(root) 0; Q V
while Q is not empty do
u Extract-Min(Q)
for each v that is a neighbor of u do
if vQ and w(u,v) < key(v)
then π[v] u
key(v) w(u,v) /*decrease value of key */
Note: A = {(v, [v]) : v v - {r} - Q}.
21-greedy.ppt](https://image.slidesharecdn.com/chapter24aoa-190904110933/85/Chapter-24-aoa-24-320.jpg)