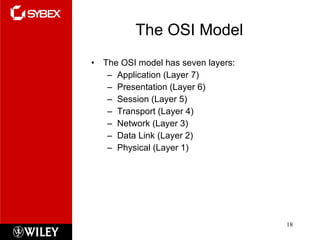
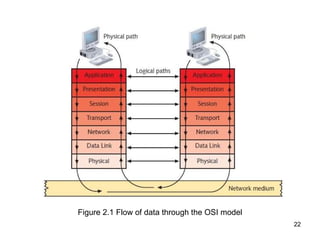
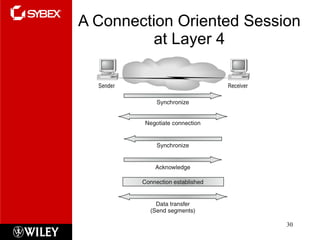
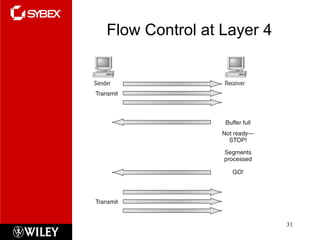
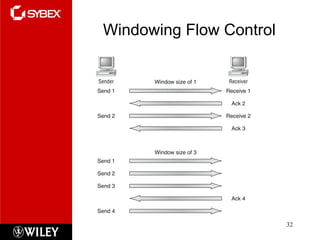
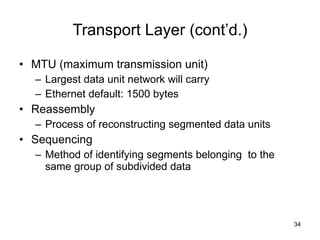
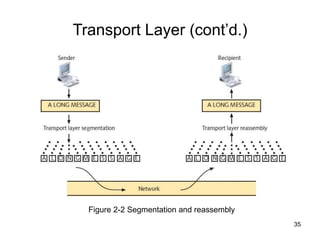
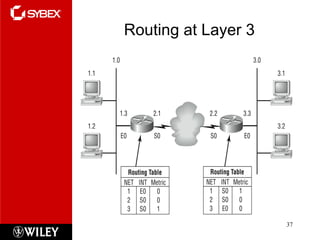
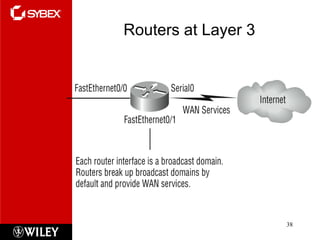
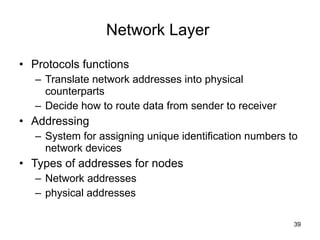
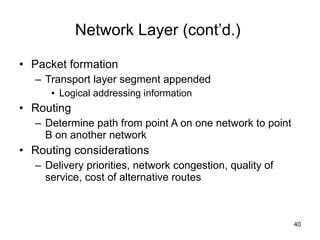
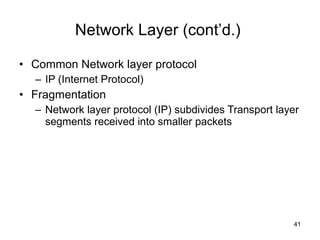
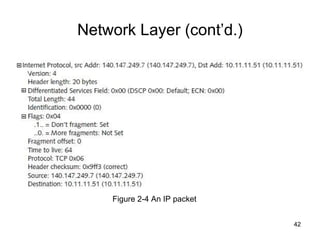
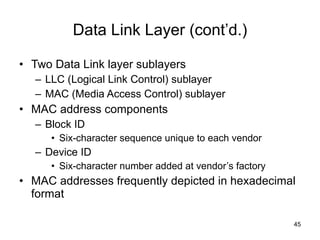
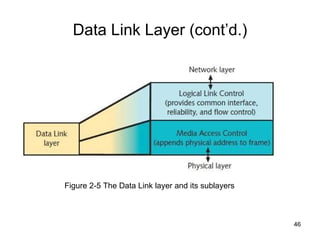
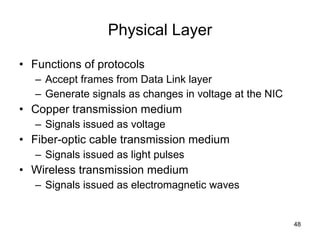
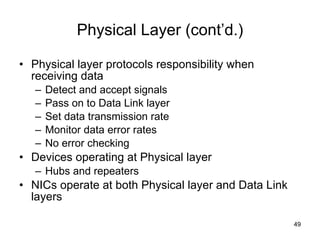
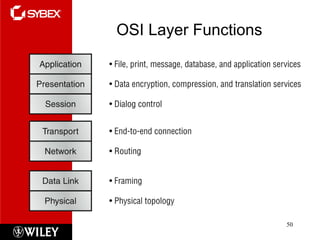
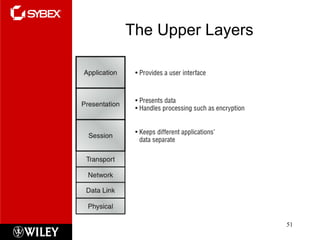
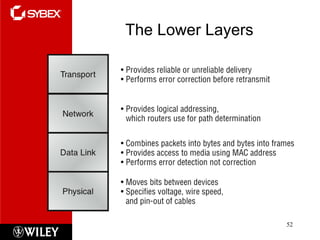
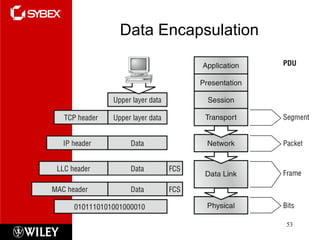
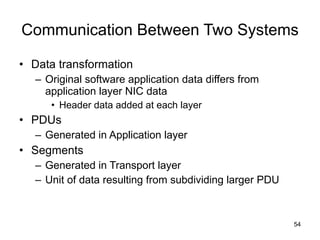
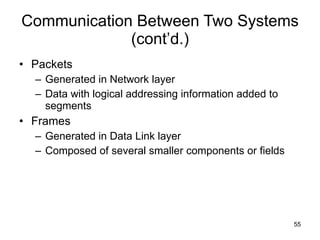
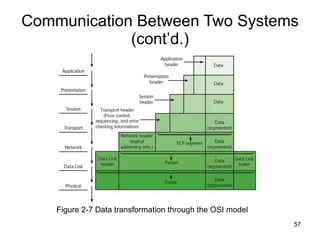
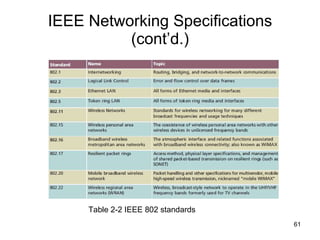
The document summarizes the seven-layer OSI model and its purpose in standardizing network communication. It describes each layer's function, from the physical layer dealing with hardware up to the application layer interacting with software programs. Standards organizations like IEEE, ISO, and IANA help ensure compatibility by defining protocols for each OSI layer.