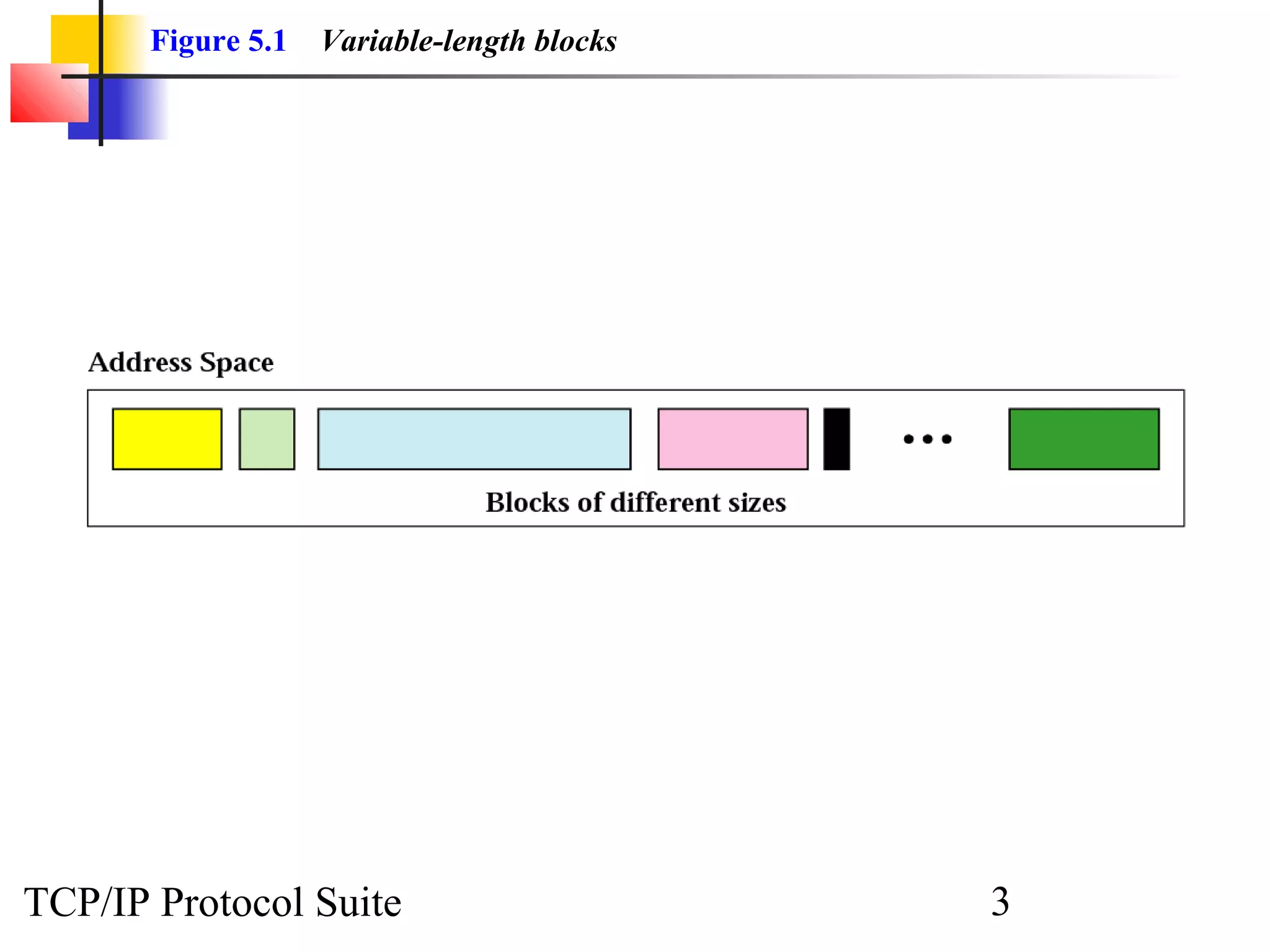
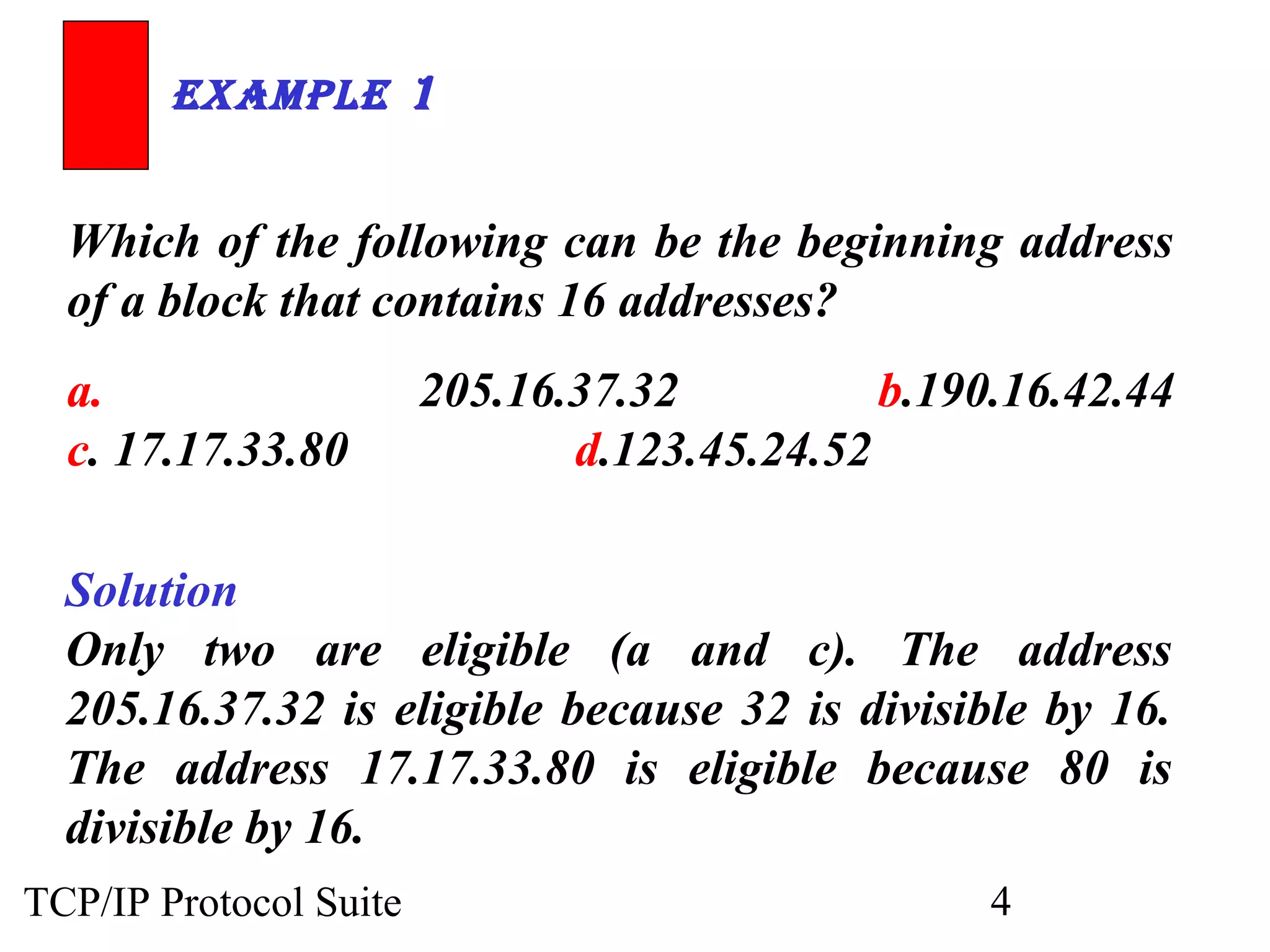
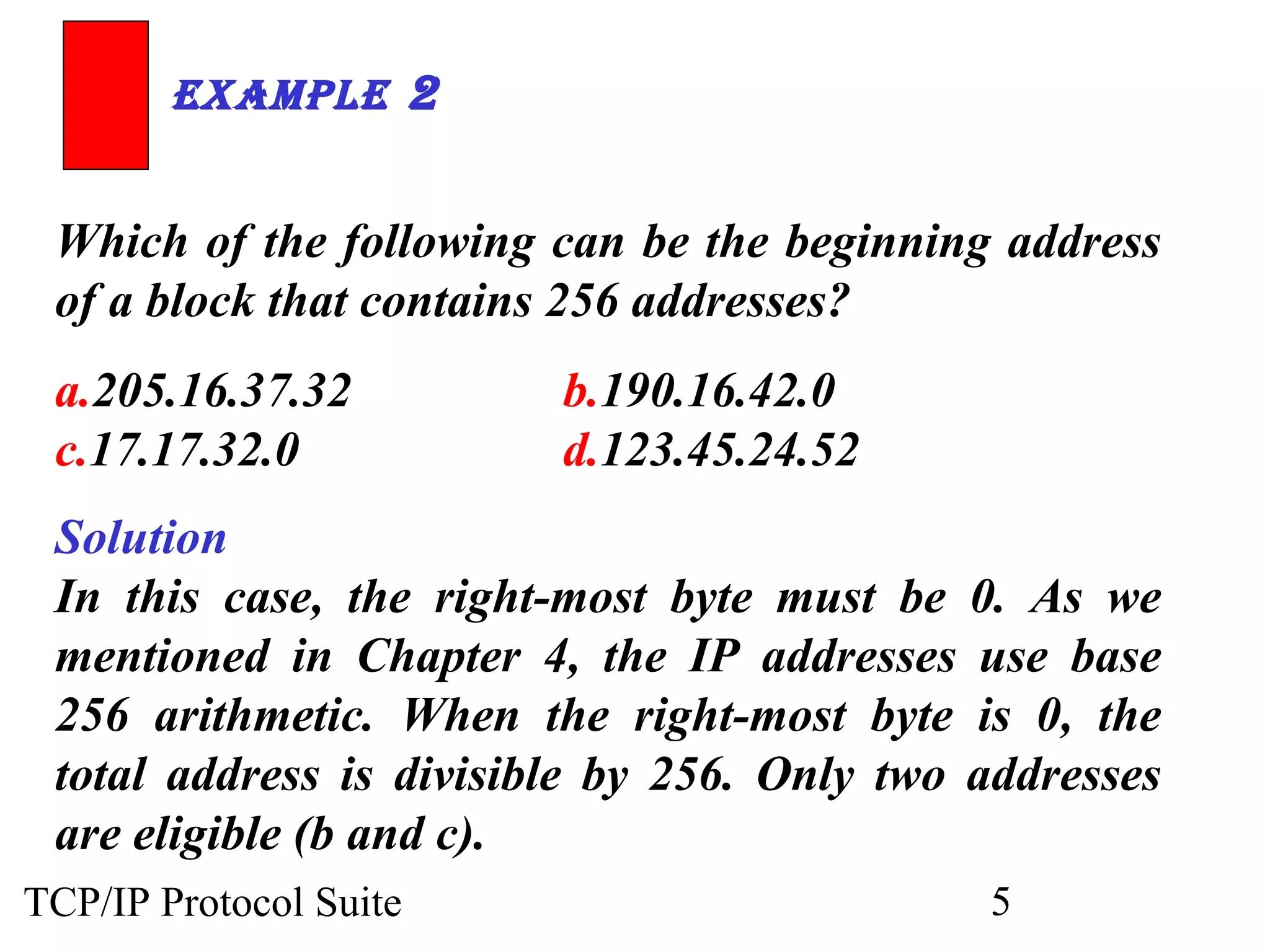
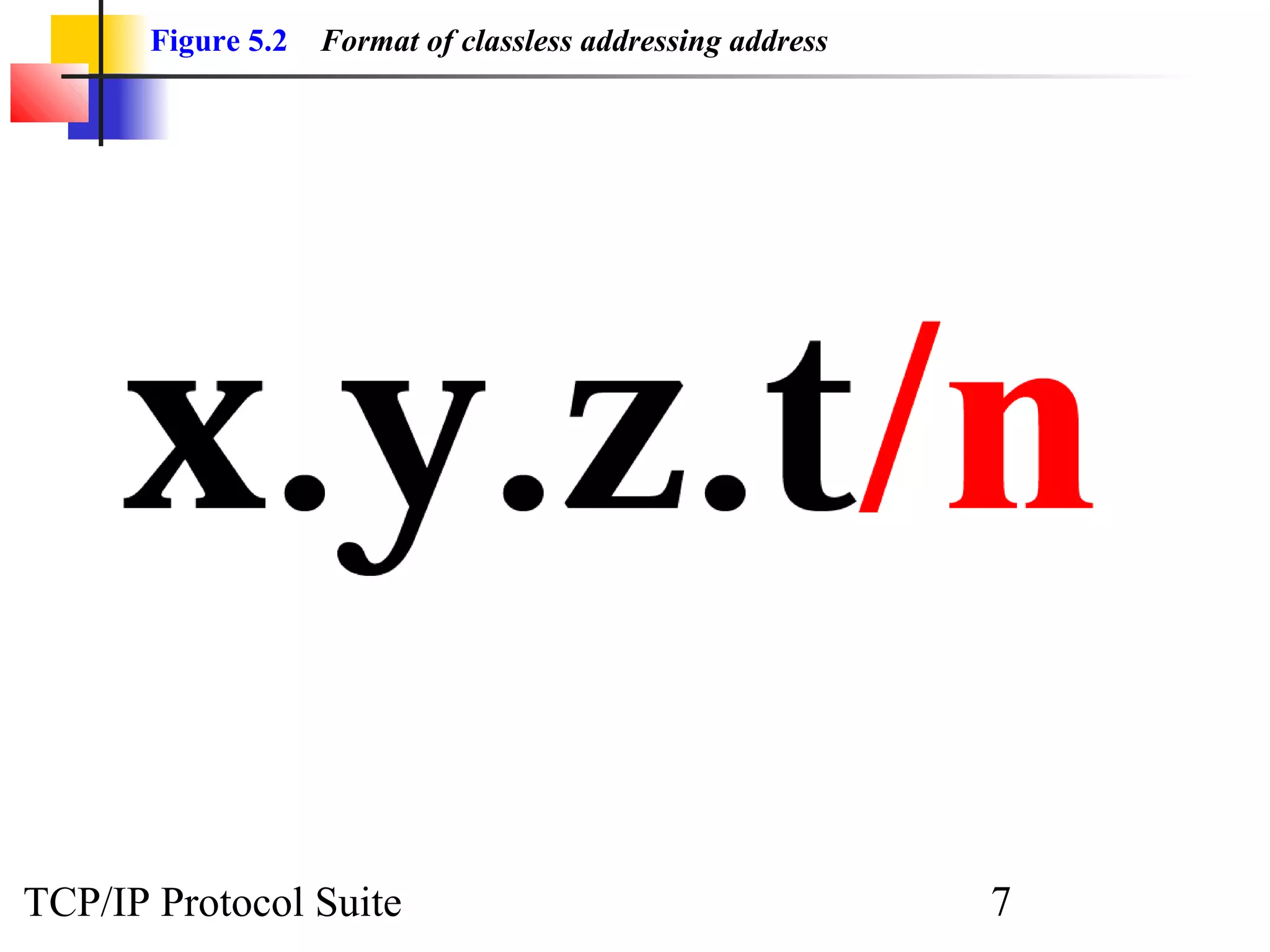
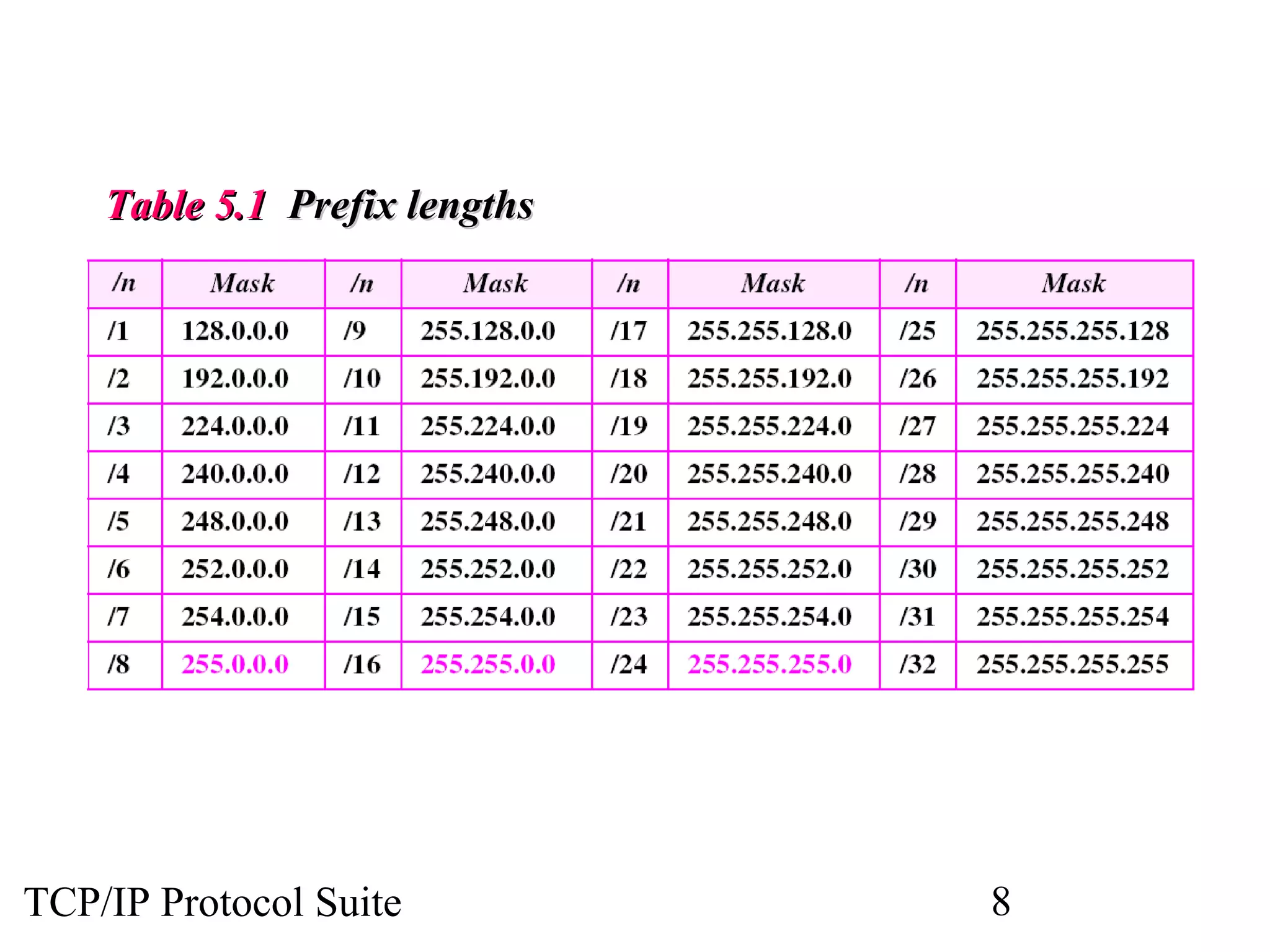
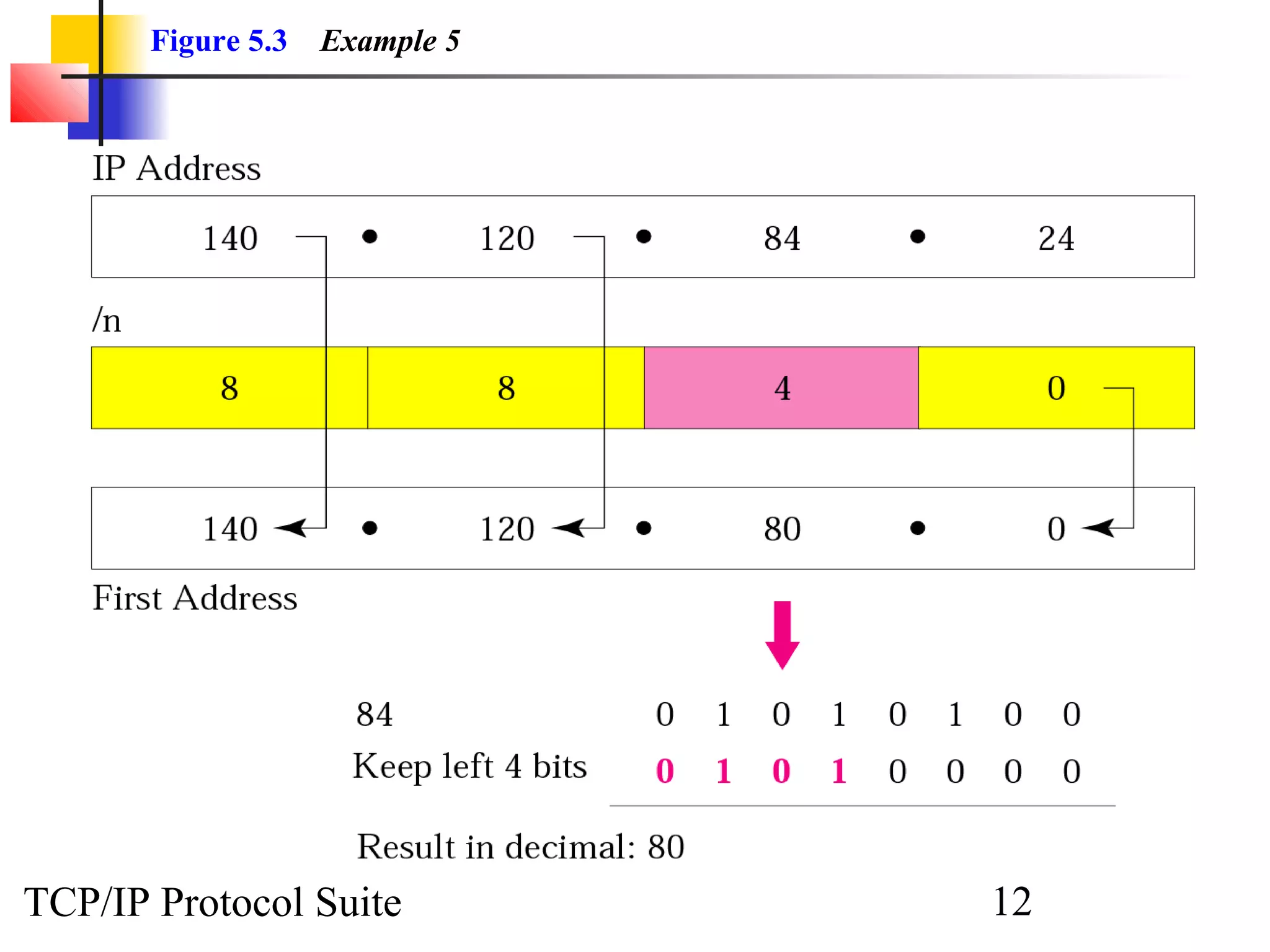
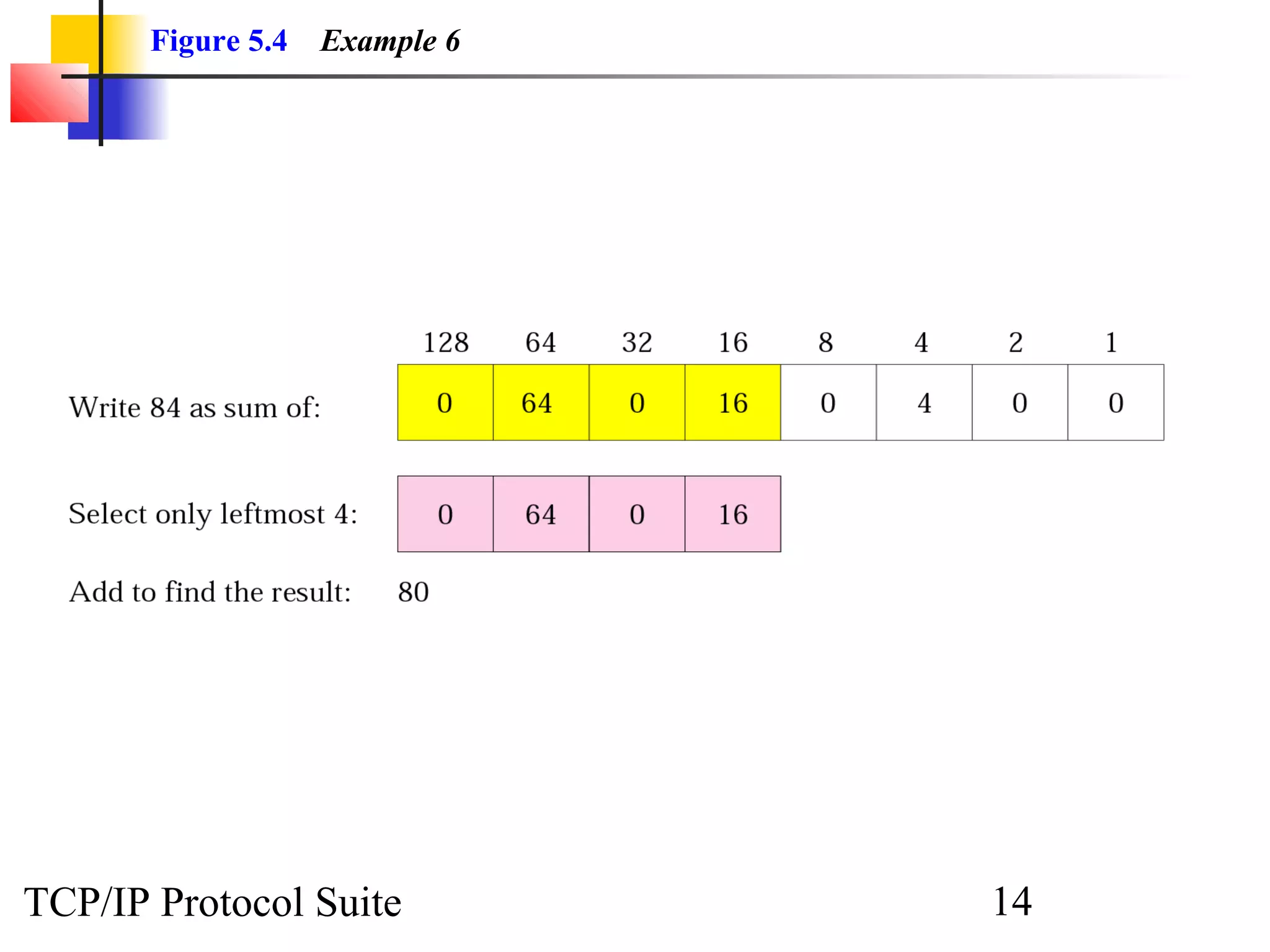
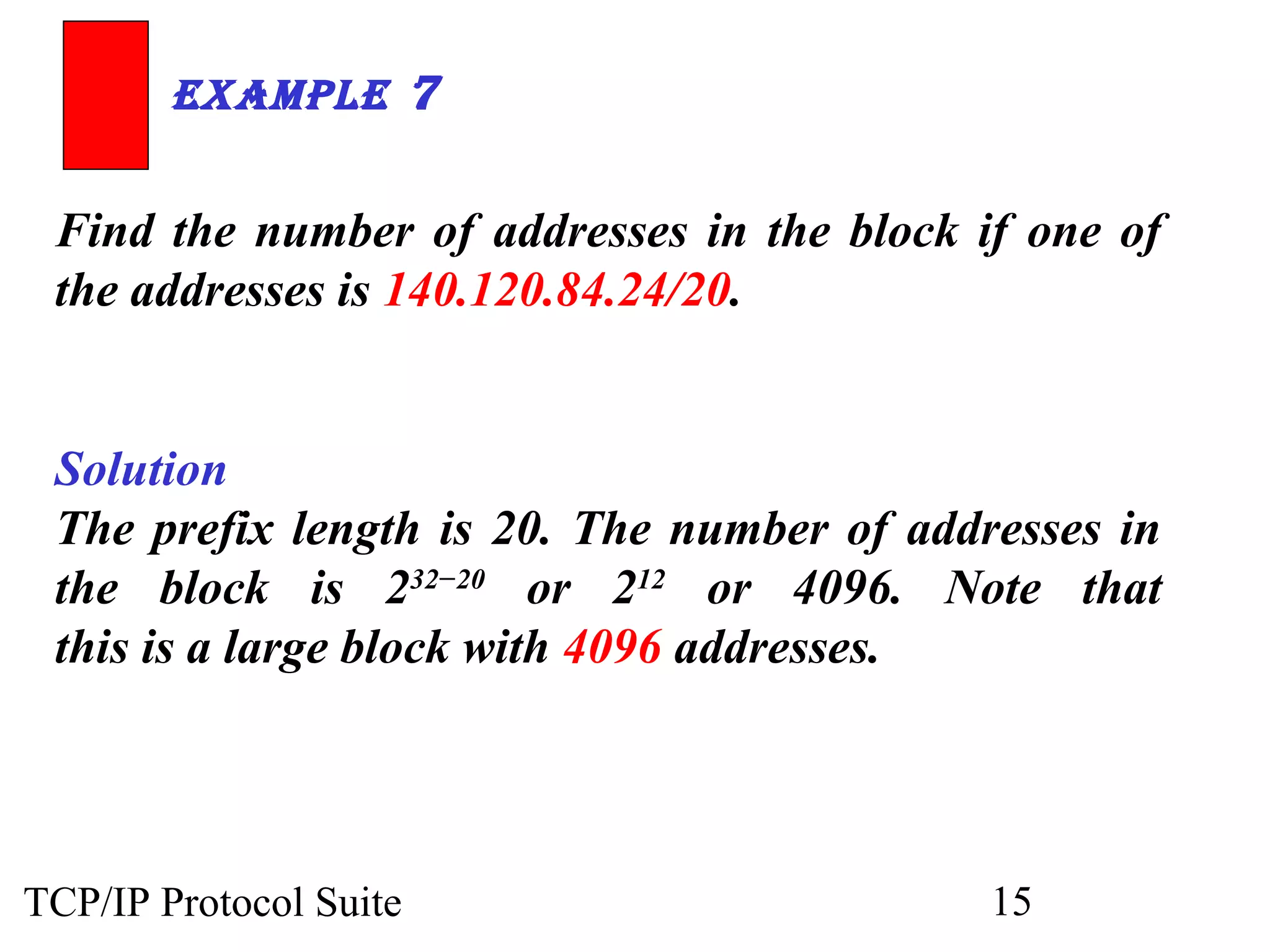
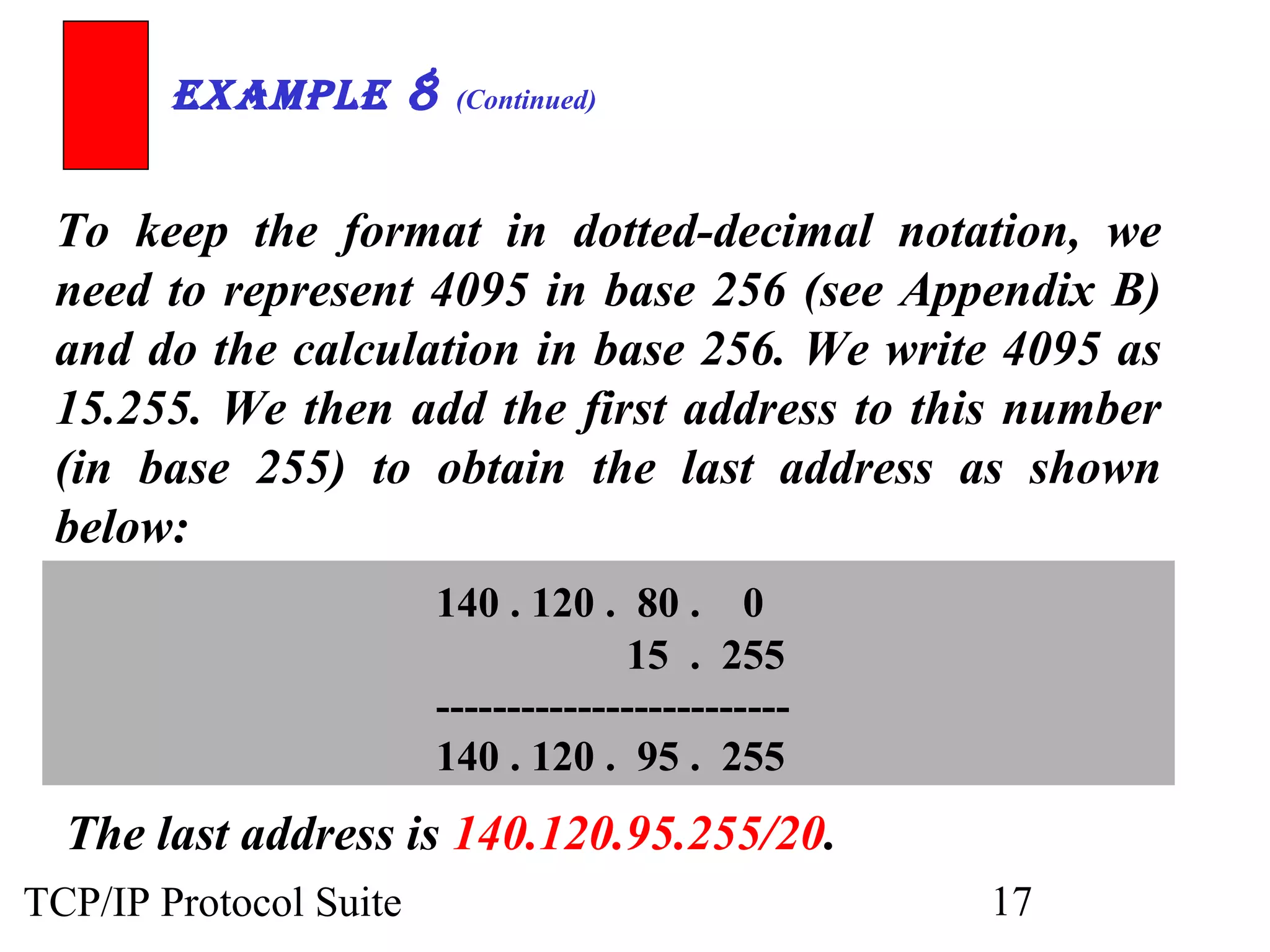
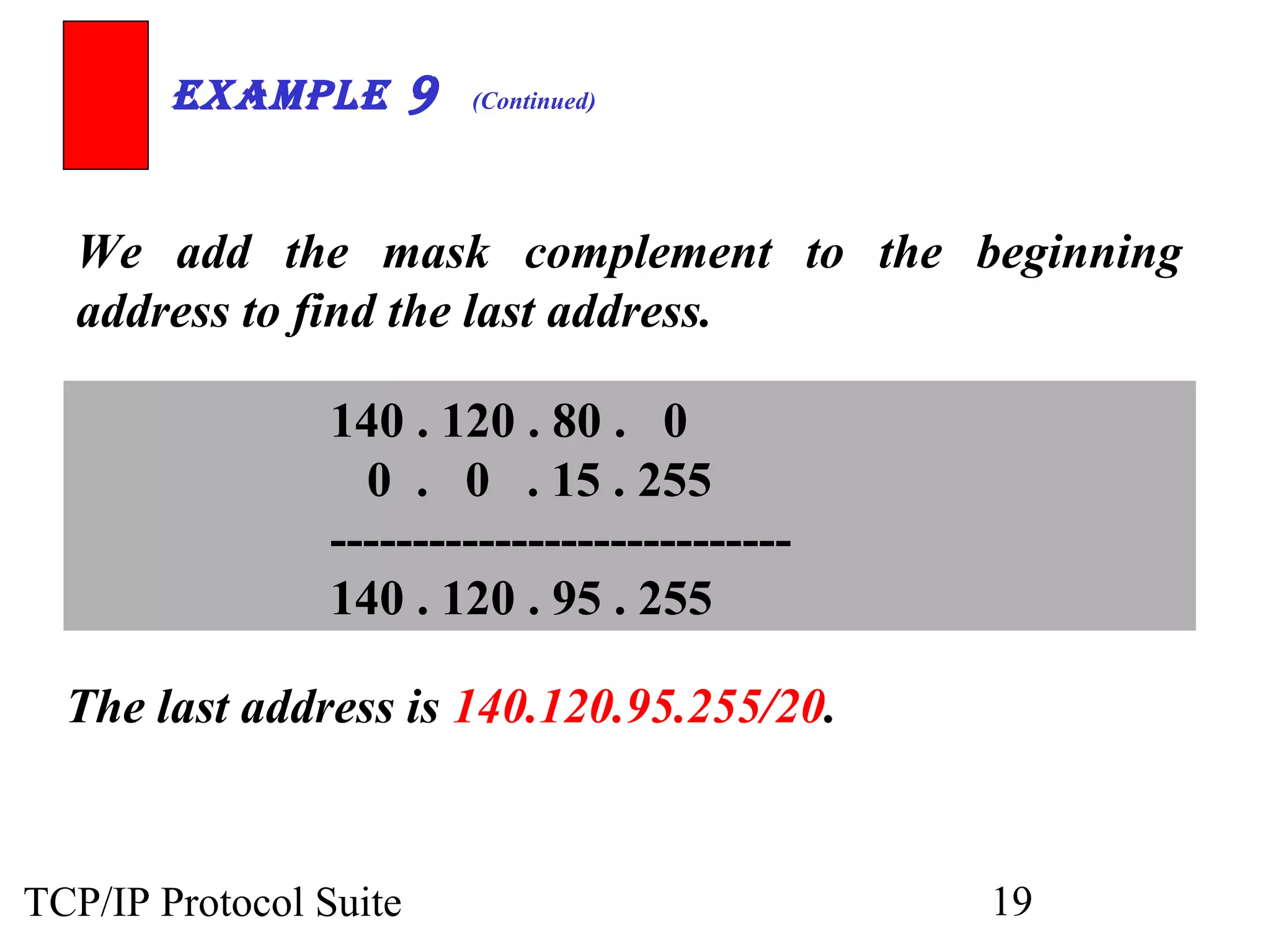
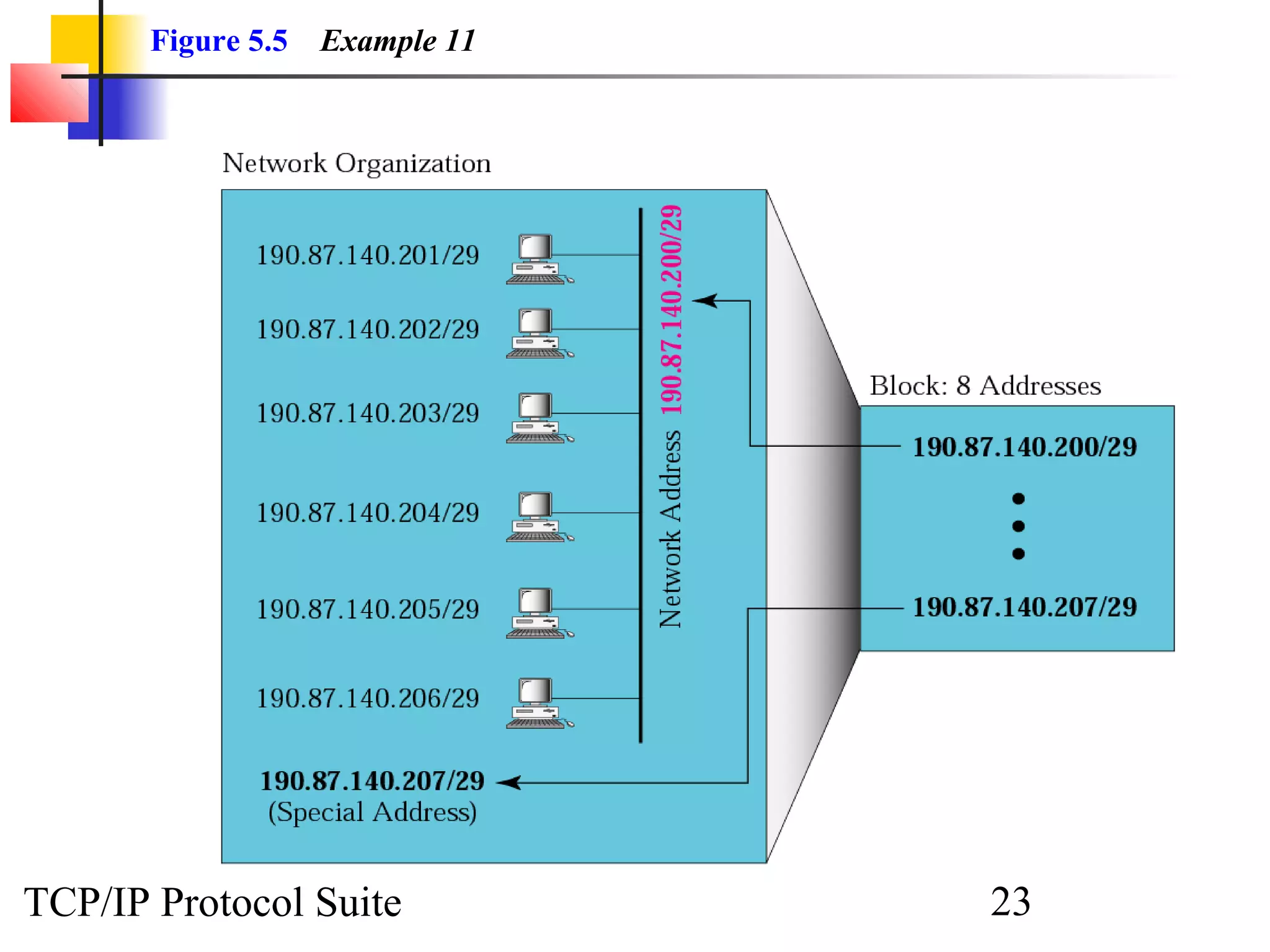
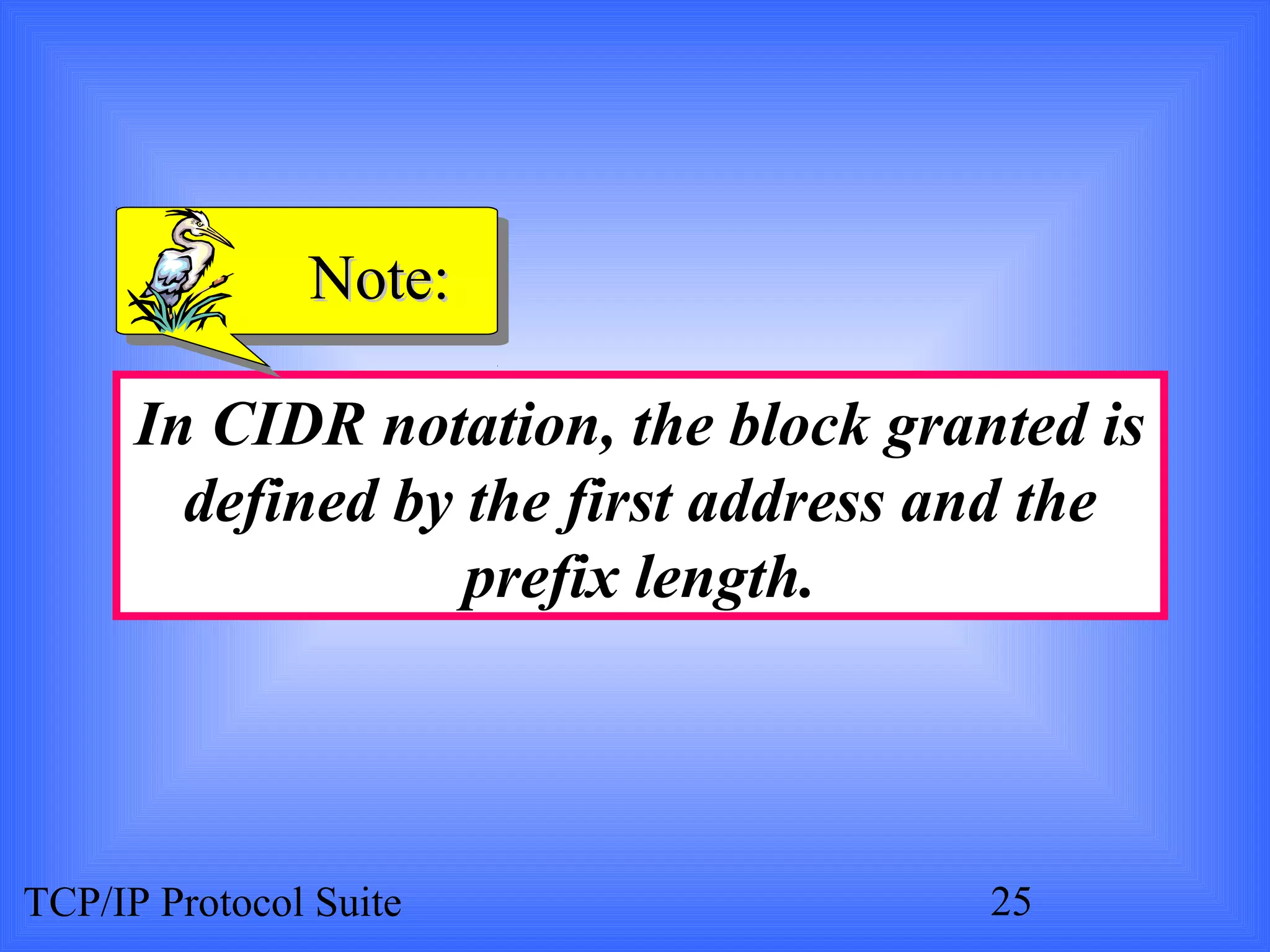
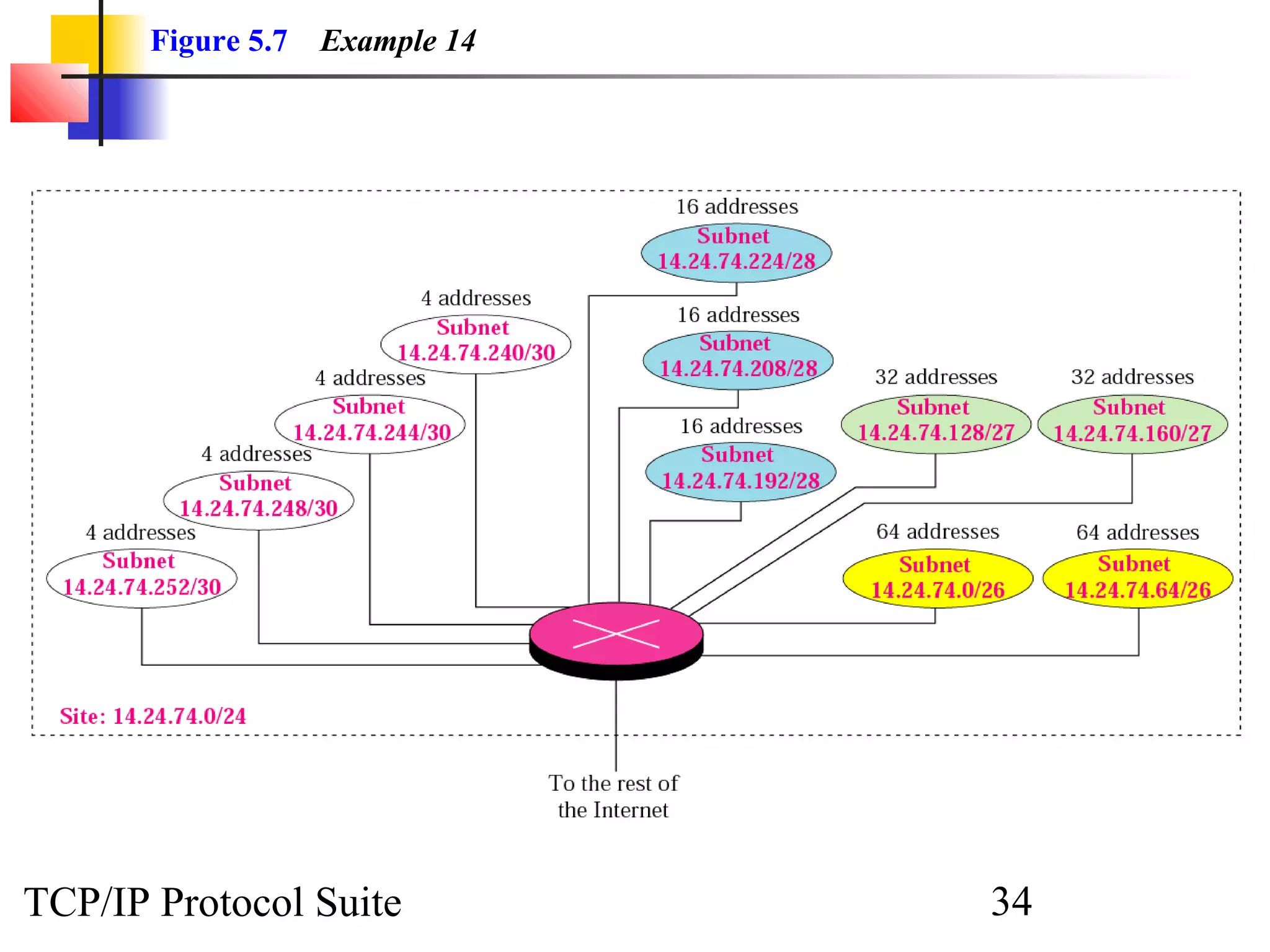
- An organization was granted a block of IP addresses with the beginning address 14.24.74.0/24, containing 256 addresses total.
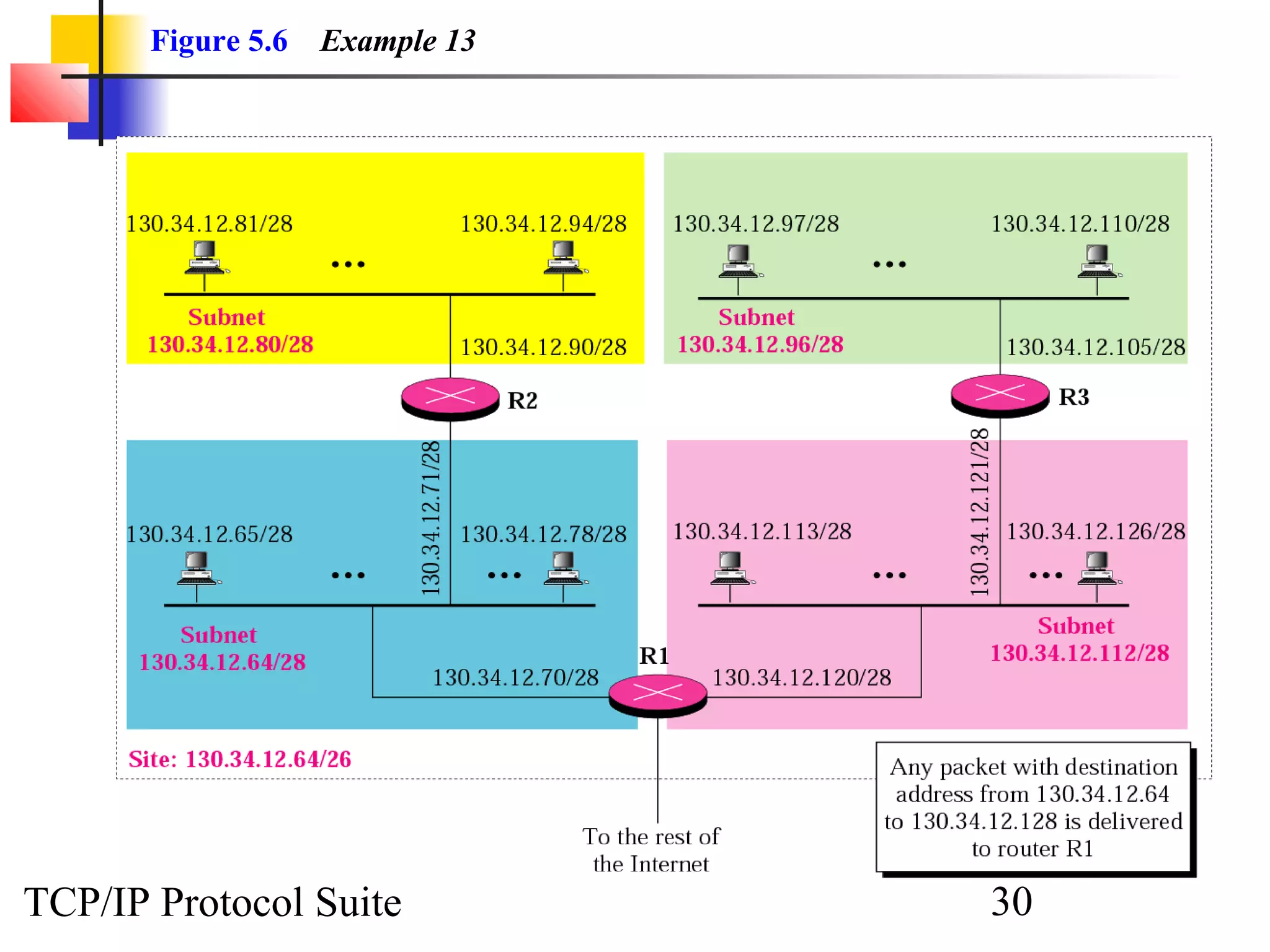
- The organization needs to create 11 subnets within this block to meet its networking needs.
- To create 11 subnets, the subnet prefix length would need to increase by 4 bits to /28, dividing the block into 16-address subnets (2^4 = 16 subnets).