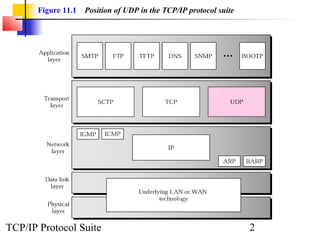
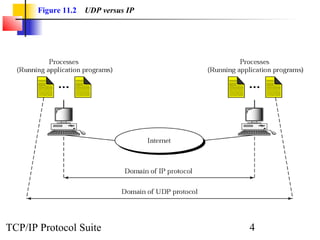
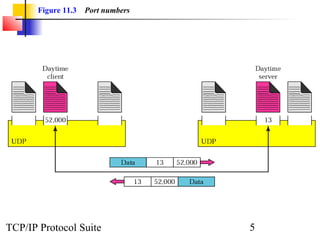
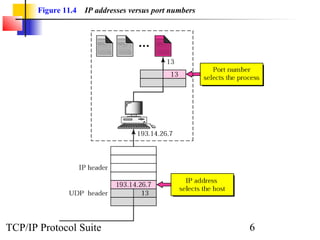
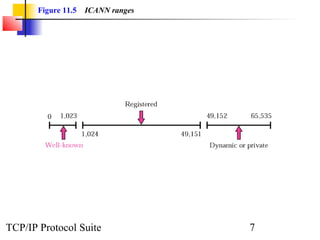
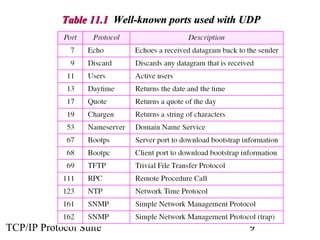
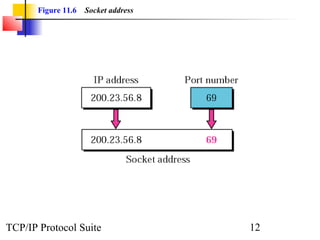
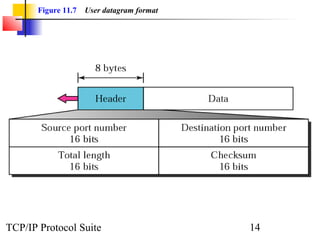
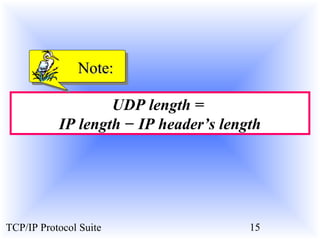
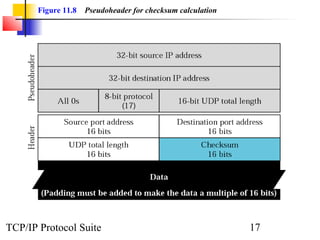
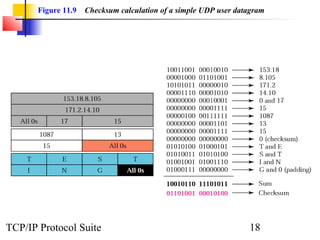
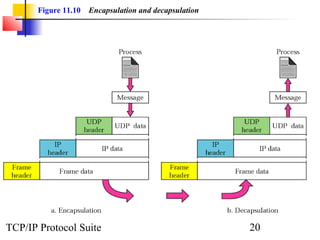
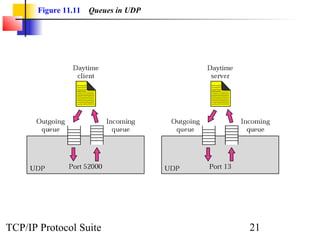
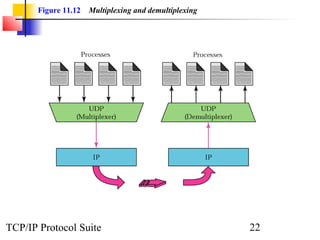
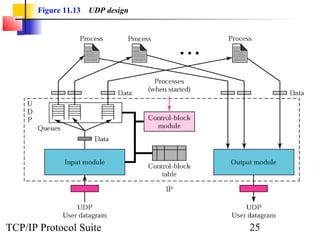
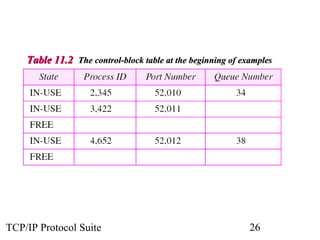
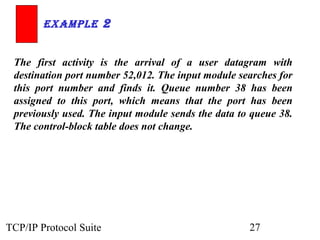
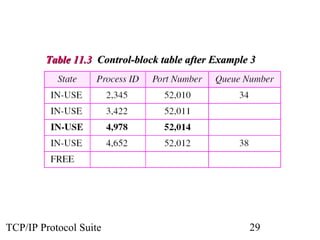
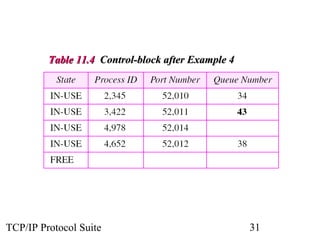
This document provides an overview of the UDP protocol. It discusses process-to-process communication, the format of UDP datagrams which include a 8-byte header, and how UDP checksums are calculated differently than IP and ICMP checksums by including a pseudoheader. UDP is connectionless and provides minimal error checking, using queues for input and output. Examples are given of how a sample UDP package tracks communication using a control block table and modules for input, output, and the control block.