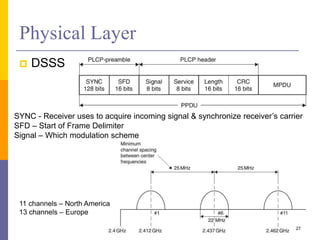
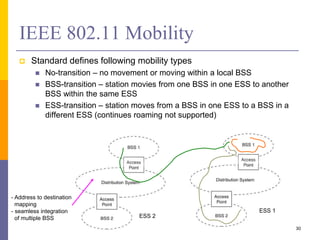
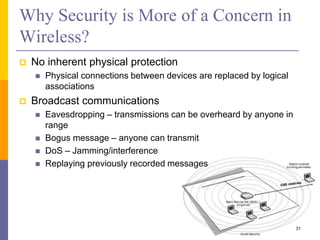
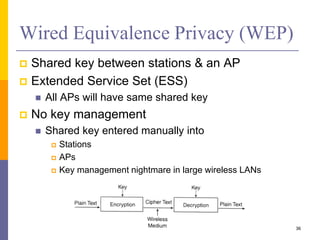
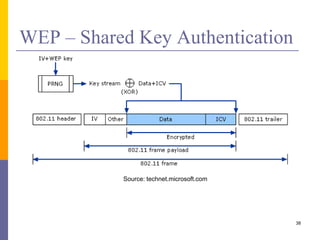
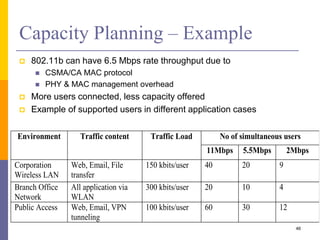
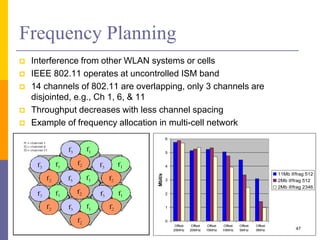
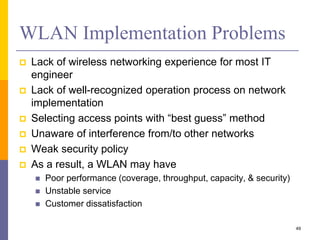
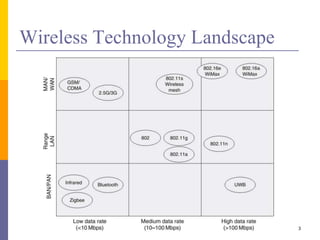
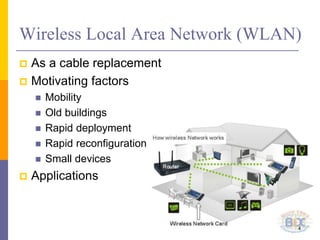
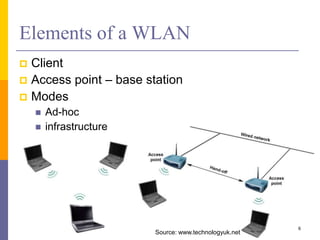
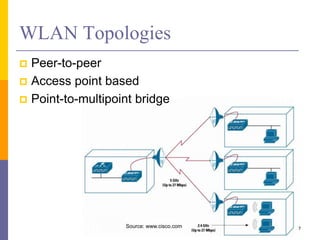
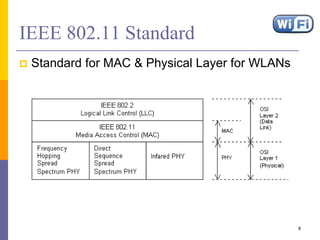
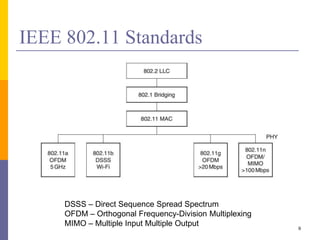
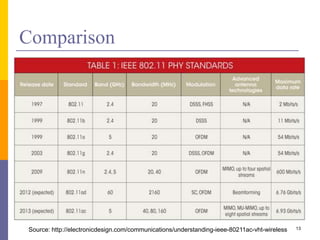
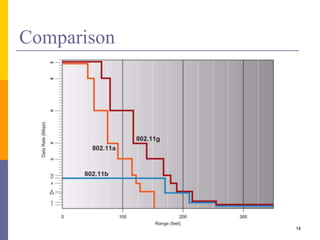
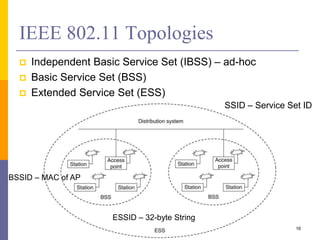
The document discusses wireless local area networks (WLANs) including their motivations, IEEE 802.11 standards, and practical issues such as security concerns and network planning. It provides an overview of WLAN components, topologies, and wireless communication protocols, as well as various versions of the IEEE 802.11 standard and their characteristics. Additionally, it addresses challenges like data speed, interference, and roaming, emphasizing the importance of effective planning and implementation for optimal performance.









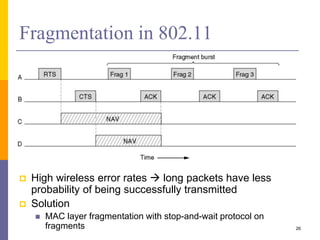
![802.11 Overhead
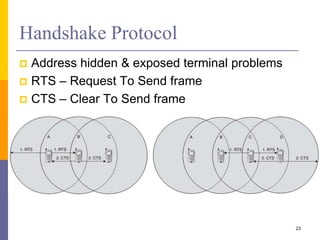
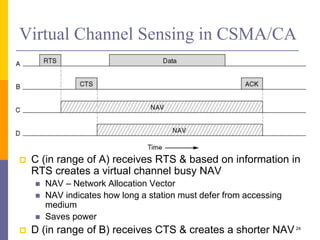
Channel contention resolved using backoff
Nodes choose random backoff interval from [0, CW]
Count down for this interval before transmission
Backoff & (optional) RTS/CTS handshake before
transmission of data frame
25
Random
backoff
Data Transmission/ACKRTS/CTS](https://image.slidesharecdn.com/03-wlans-140707011420-phpapp02/85/Wireless-Local-Area-Networks-25-320.jpg)