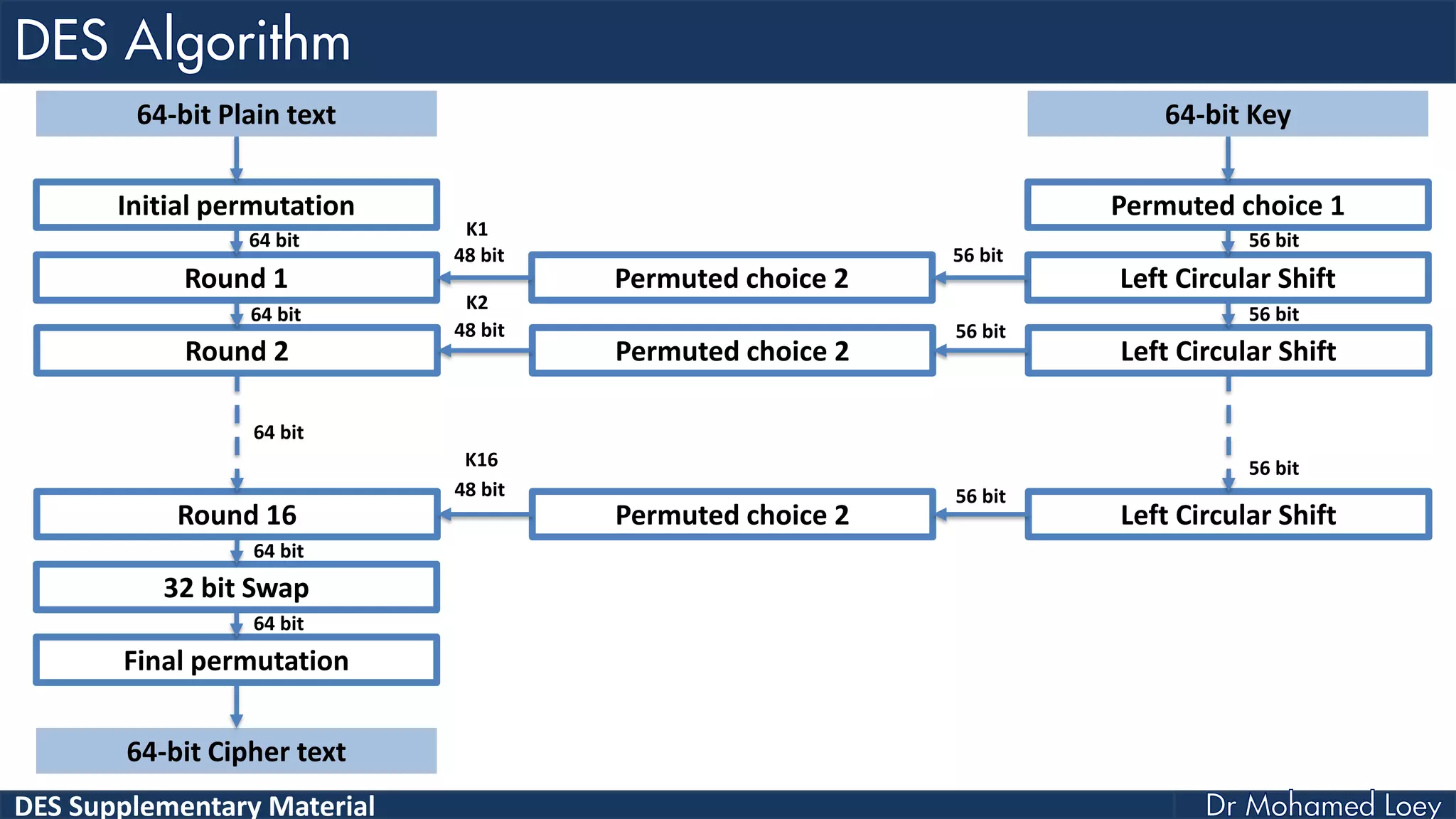
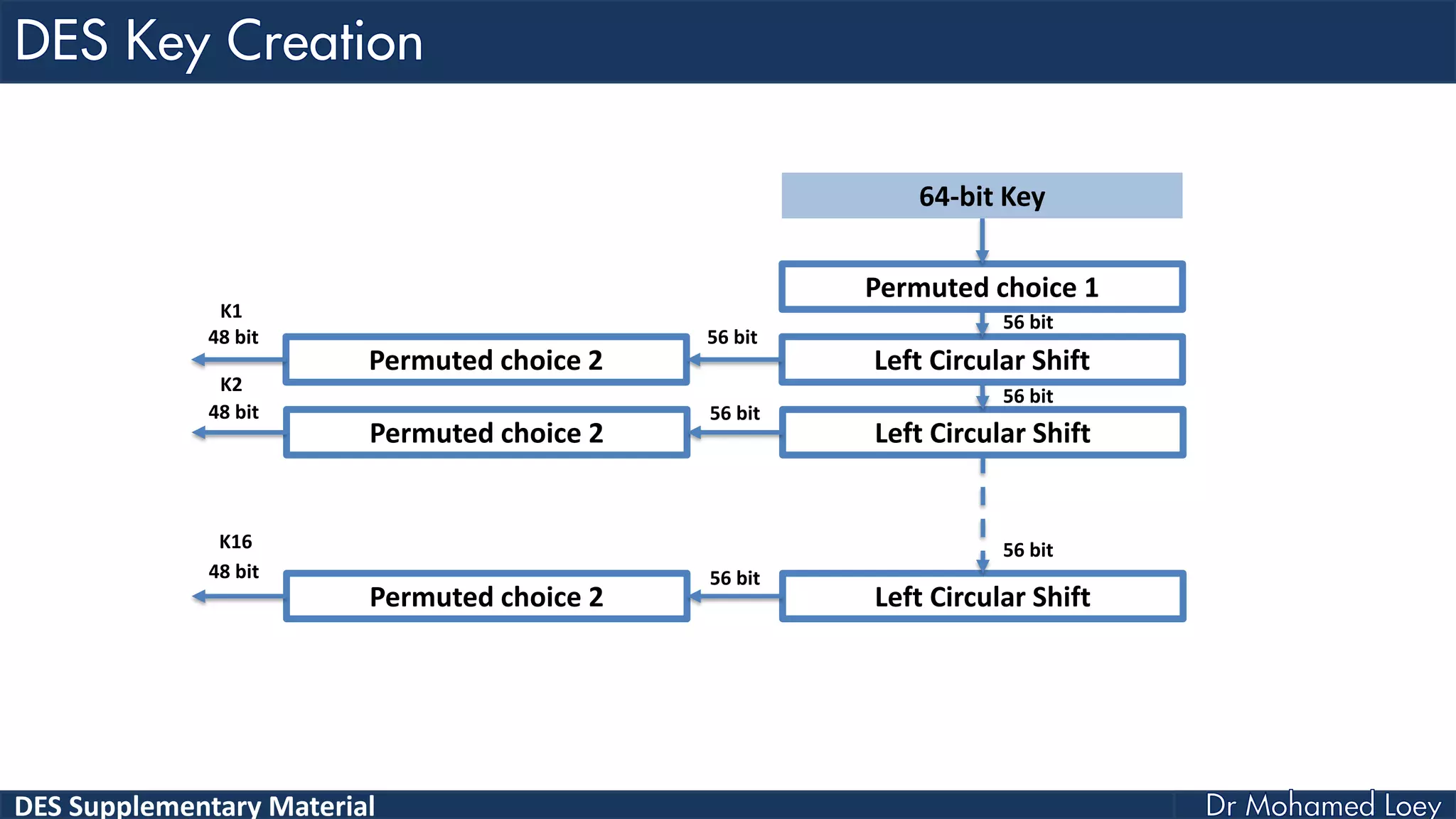
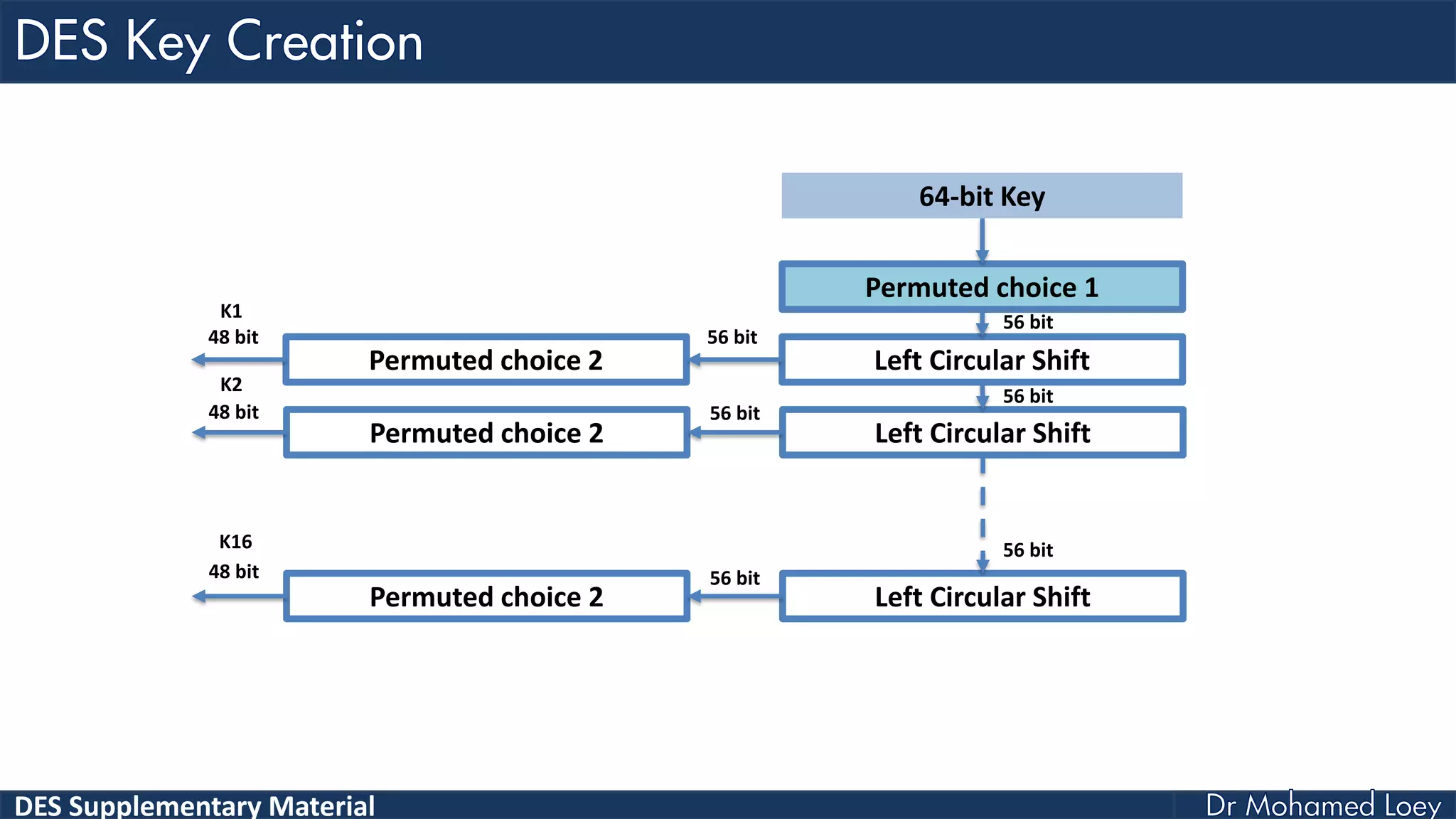
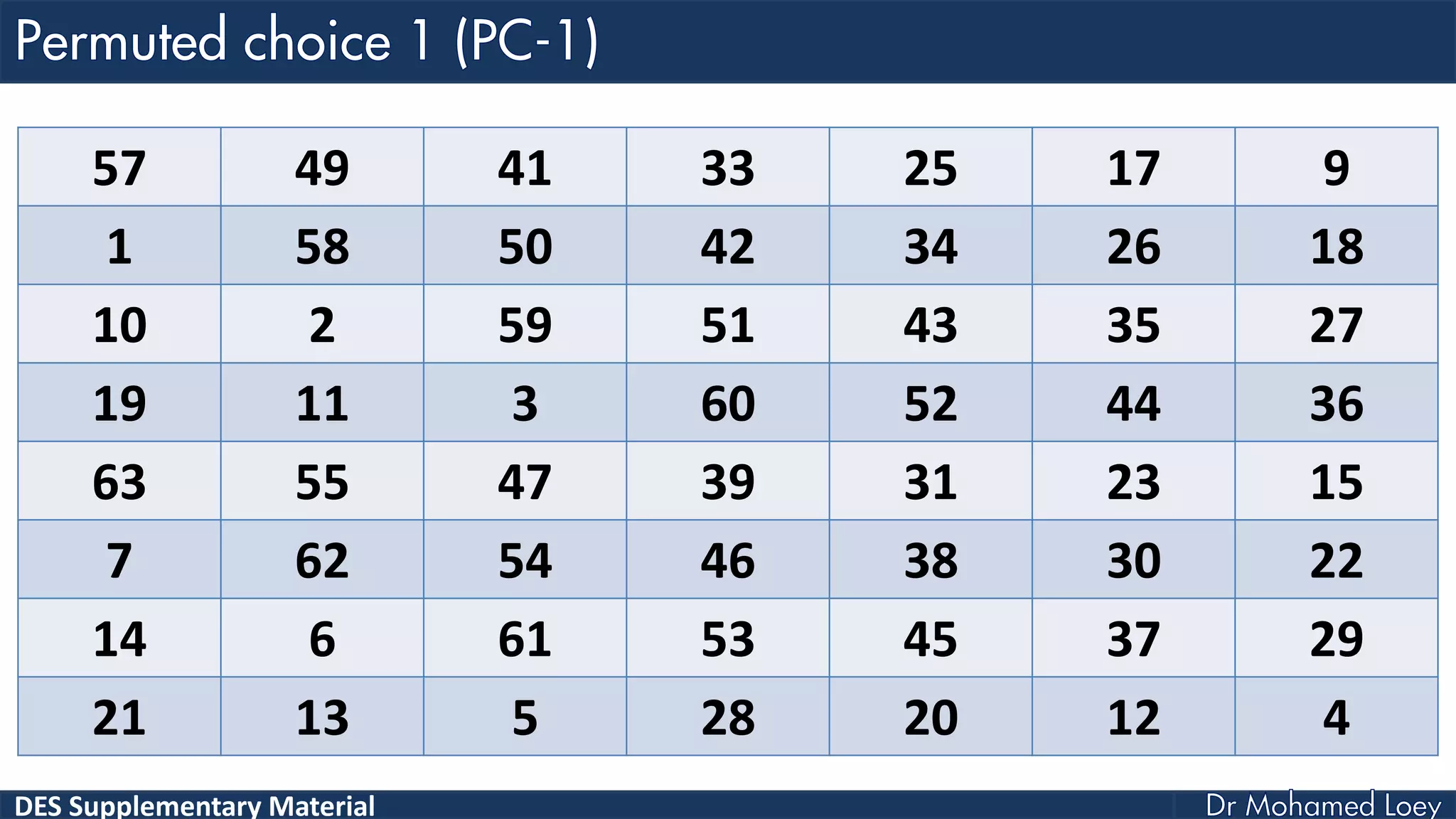
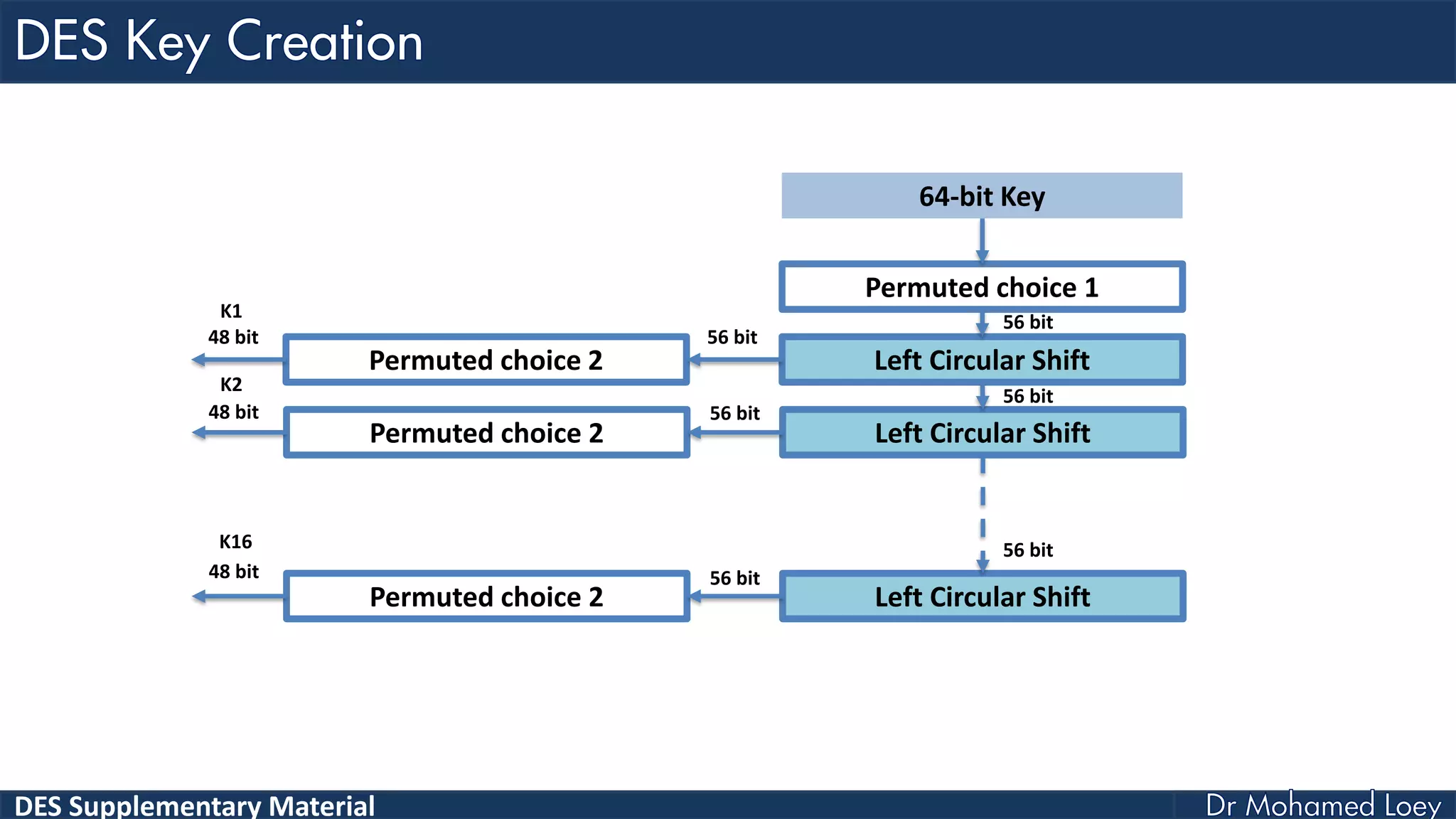
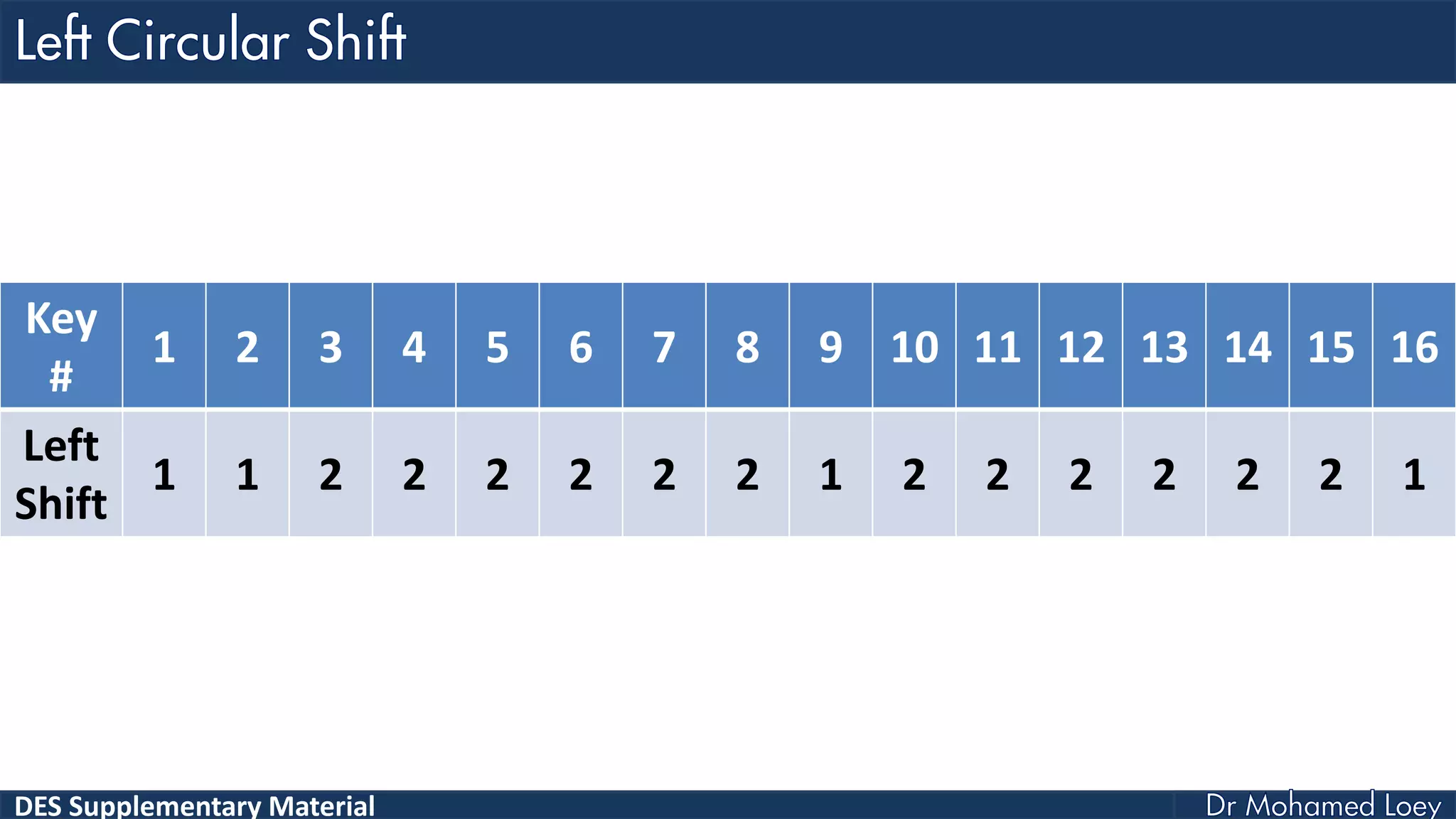
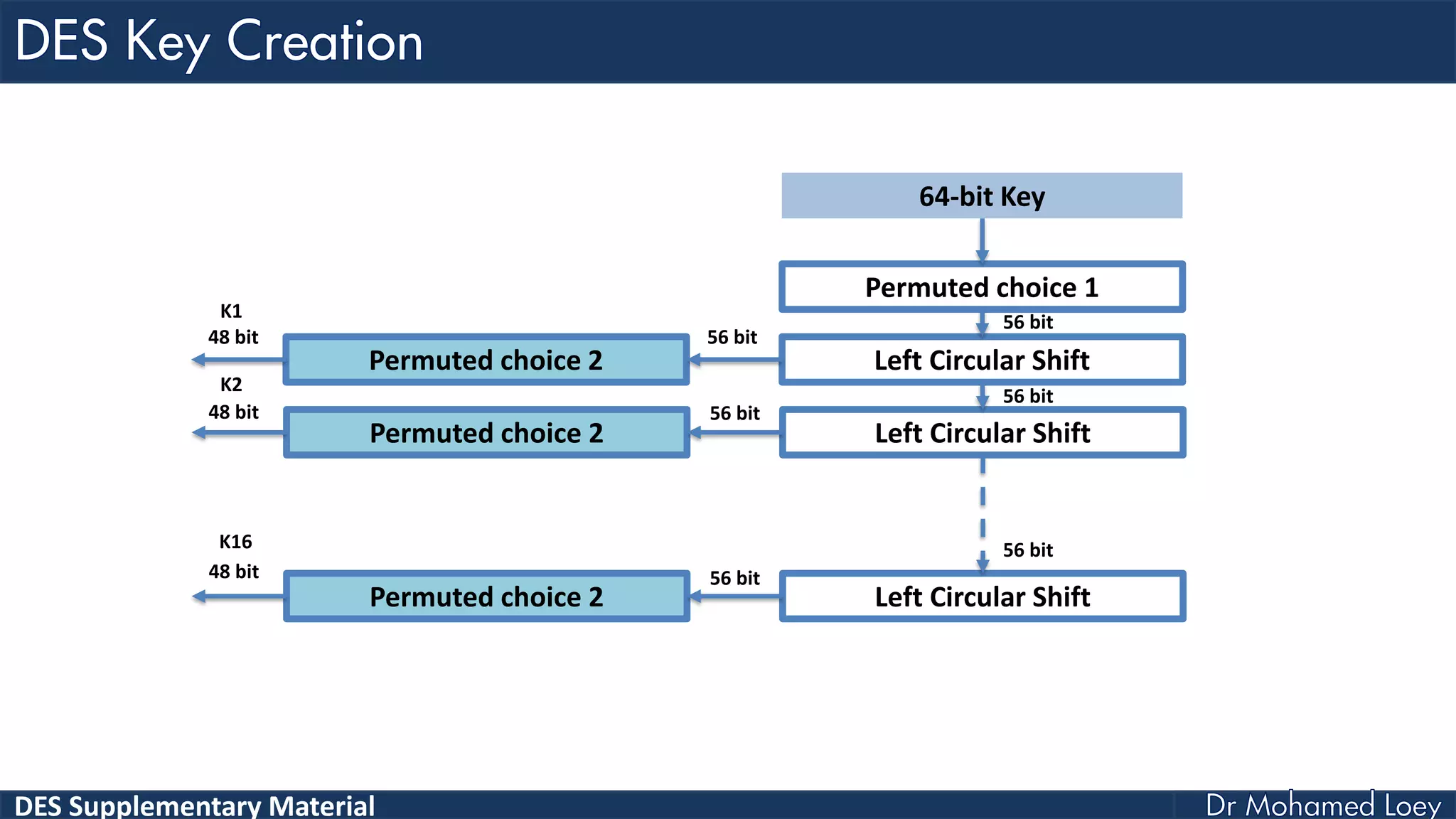
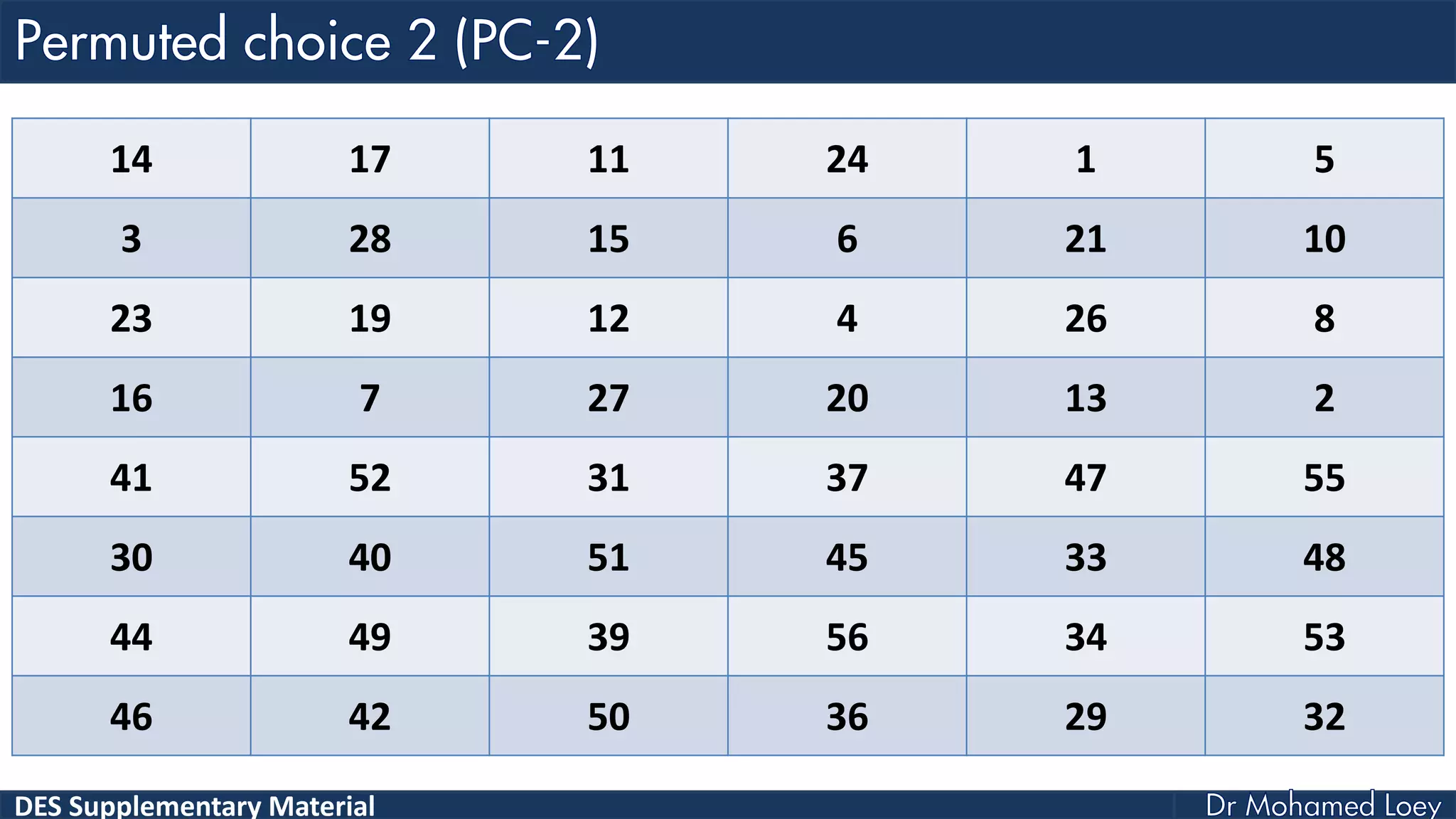
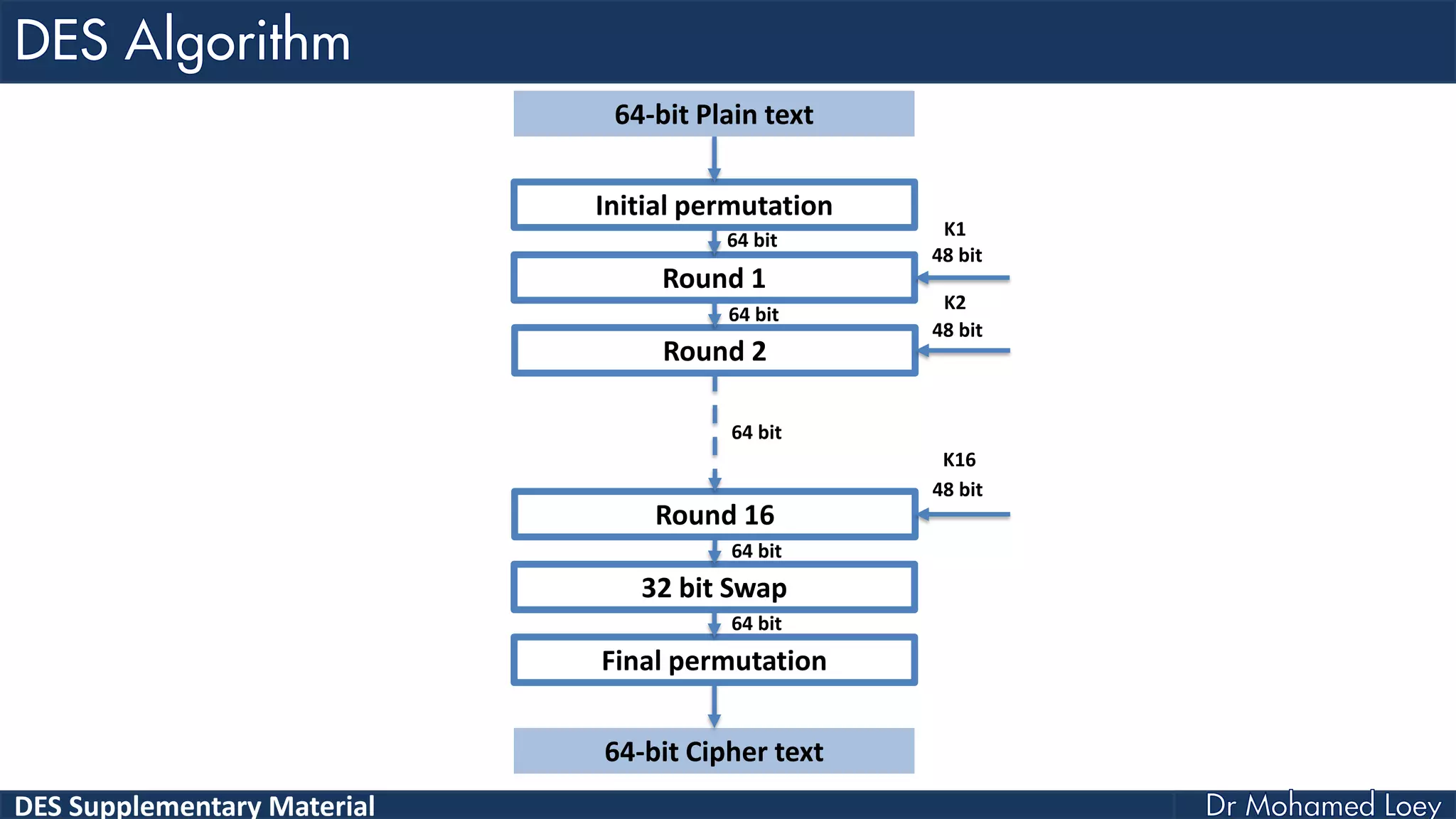
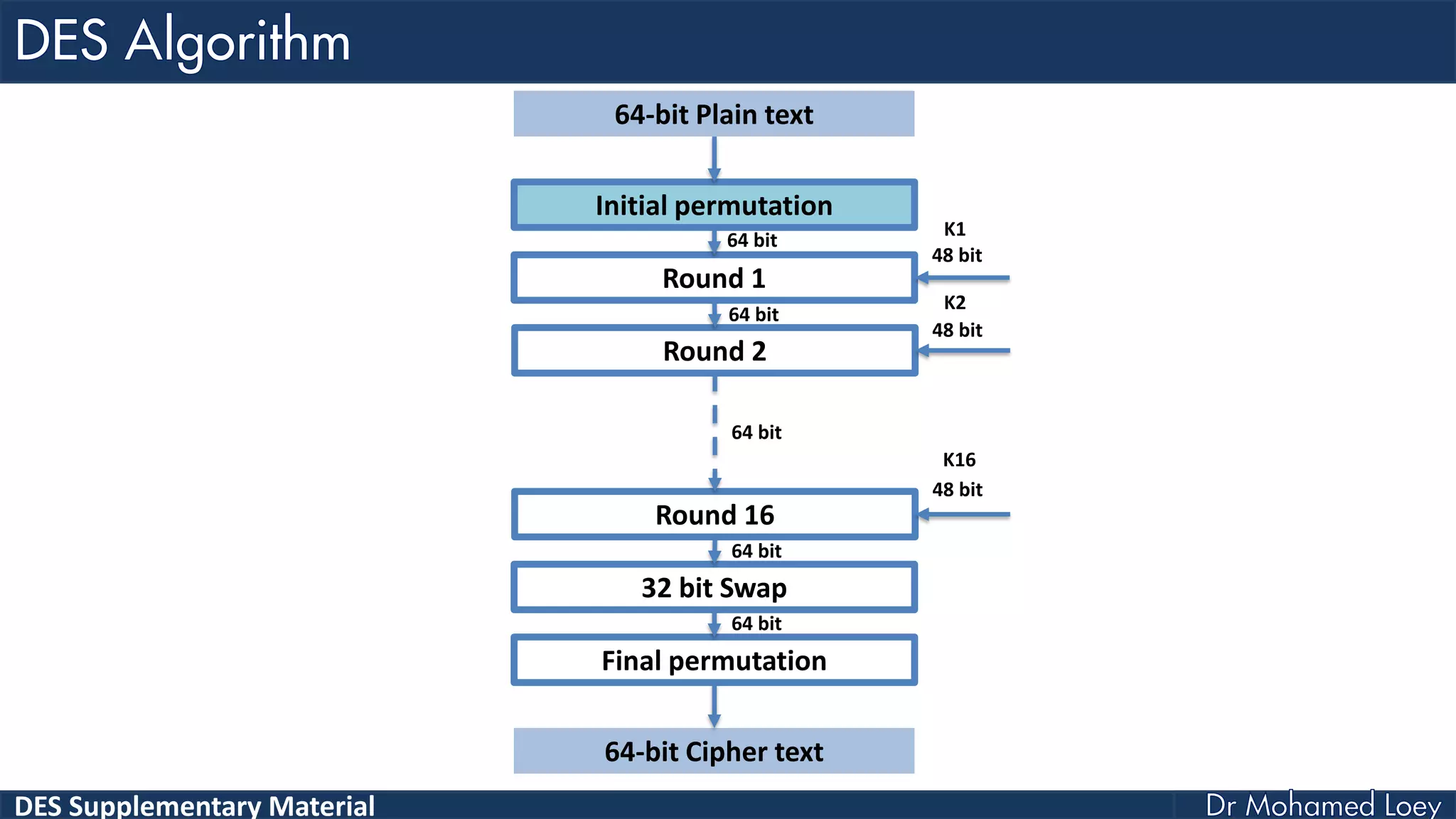
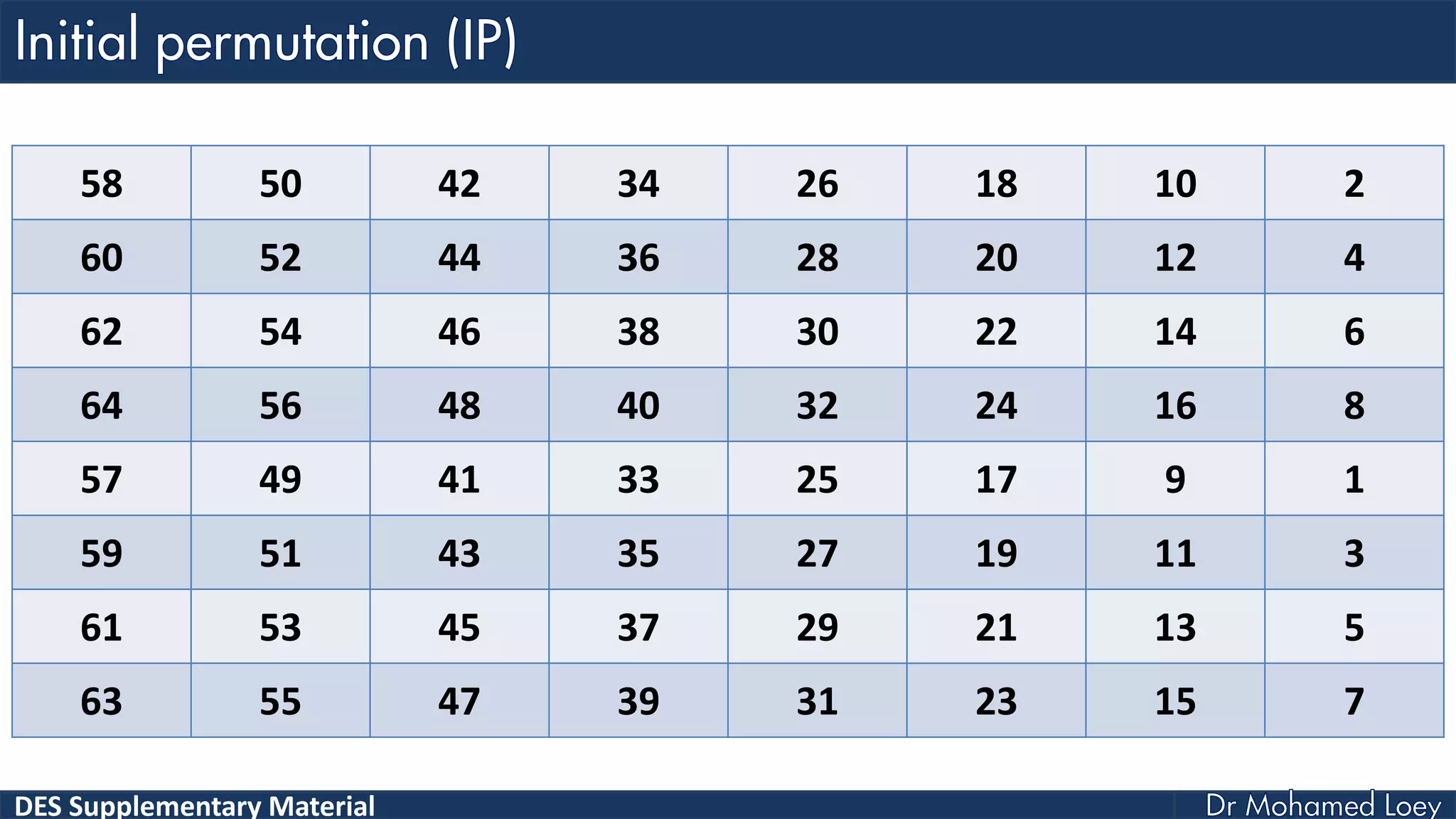
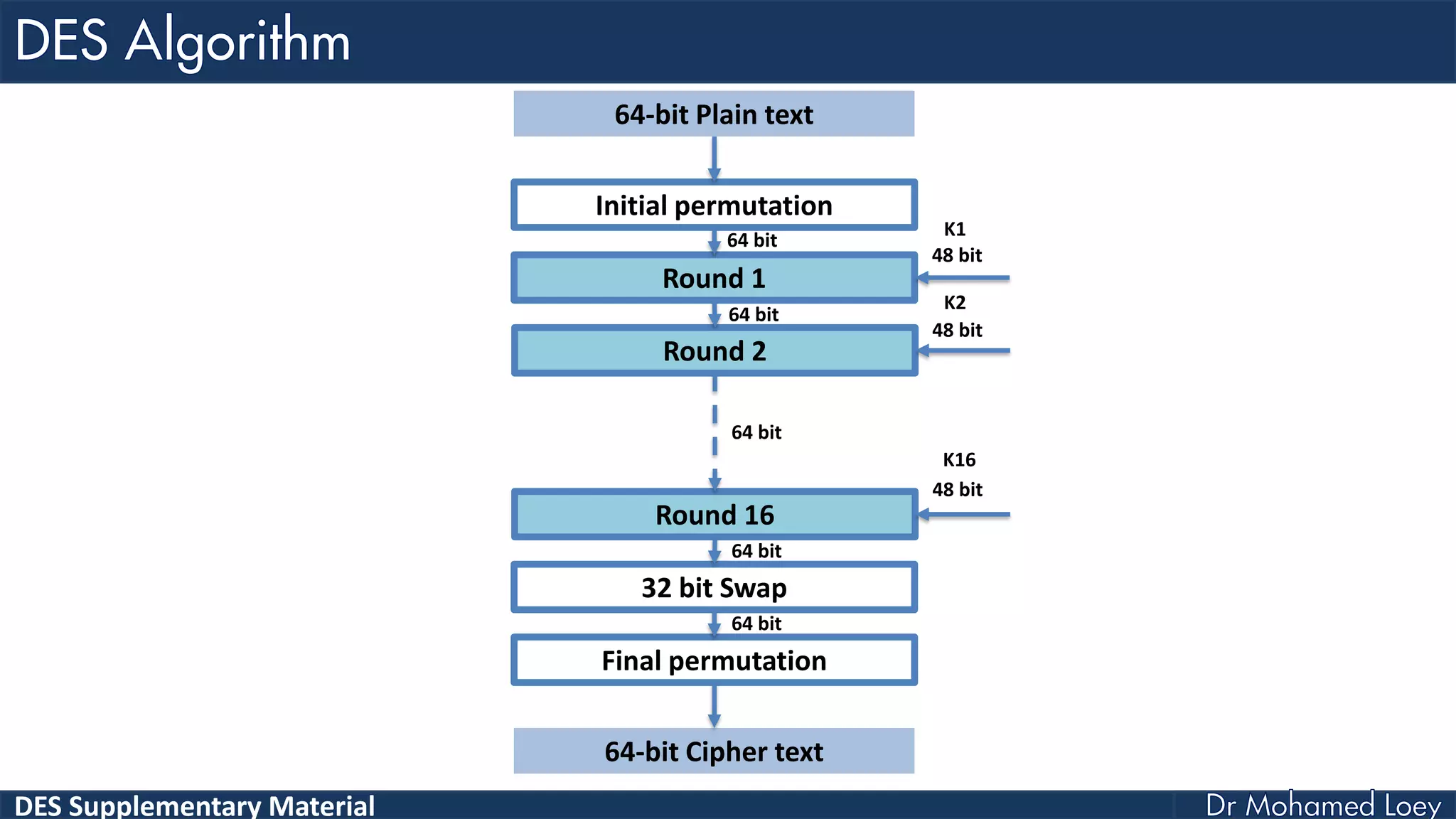
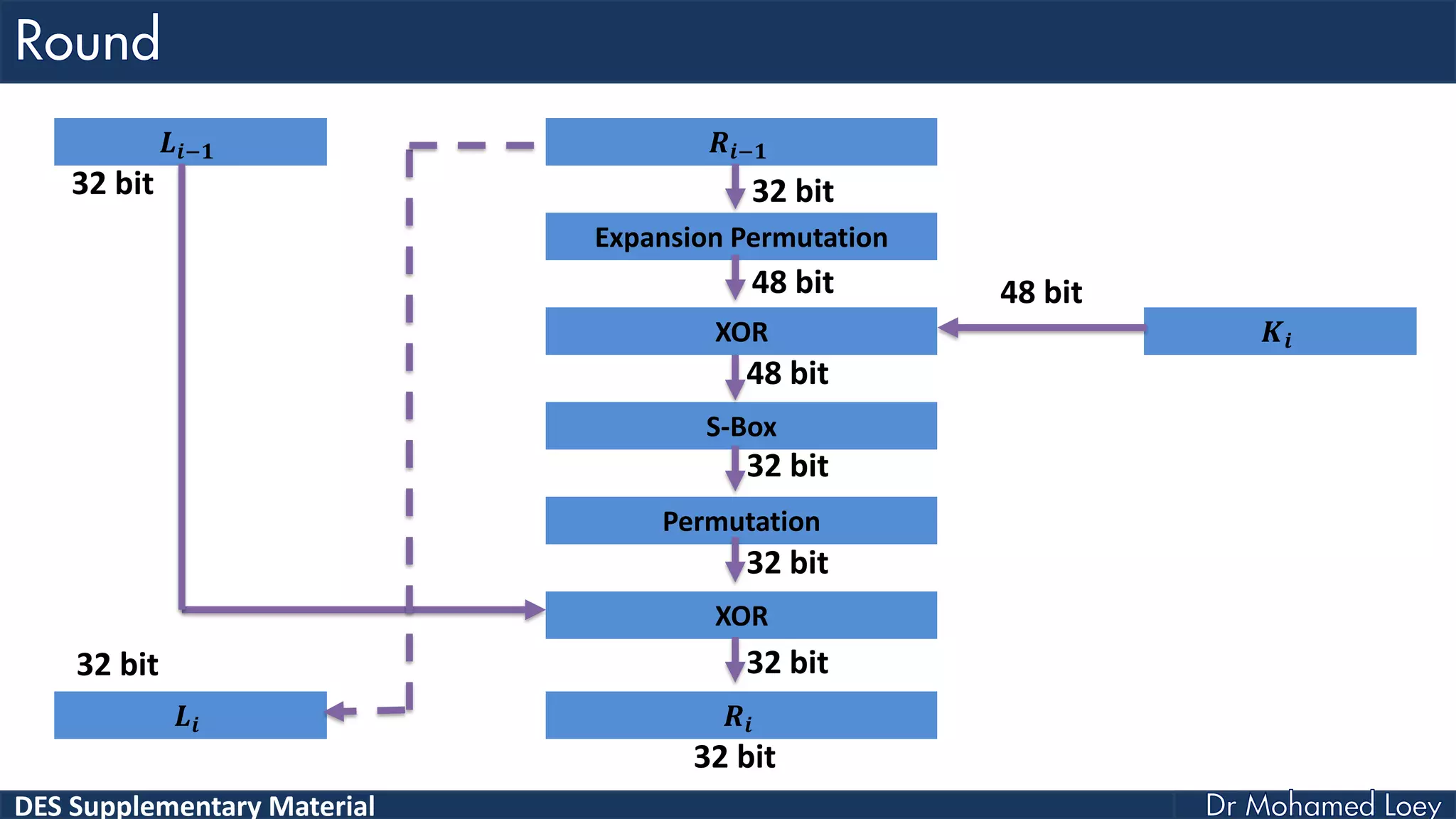
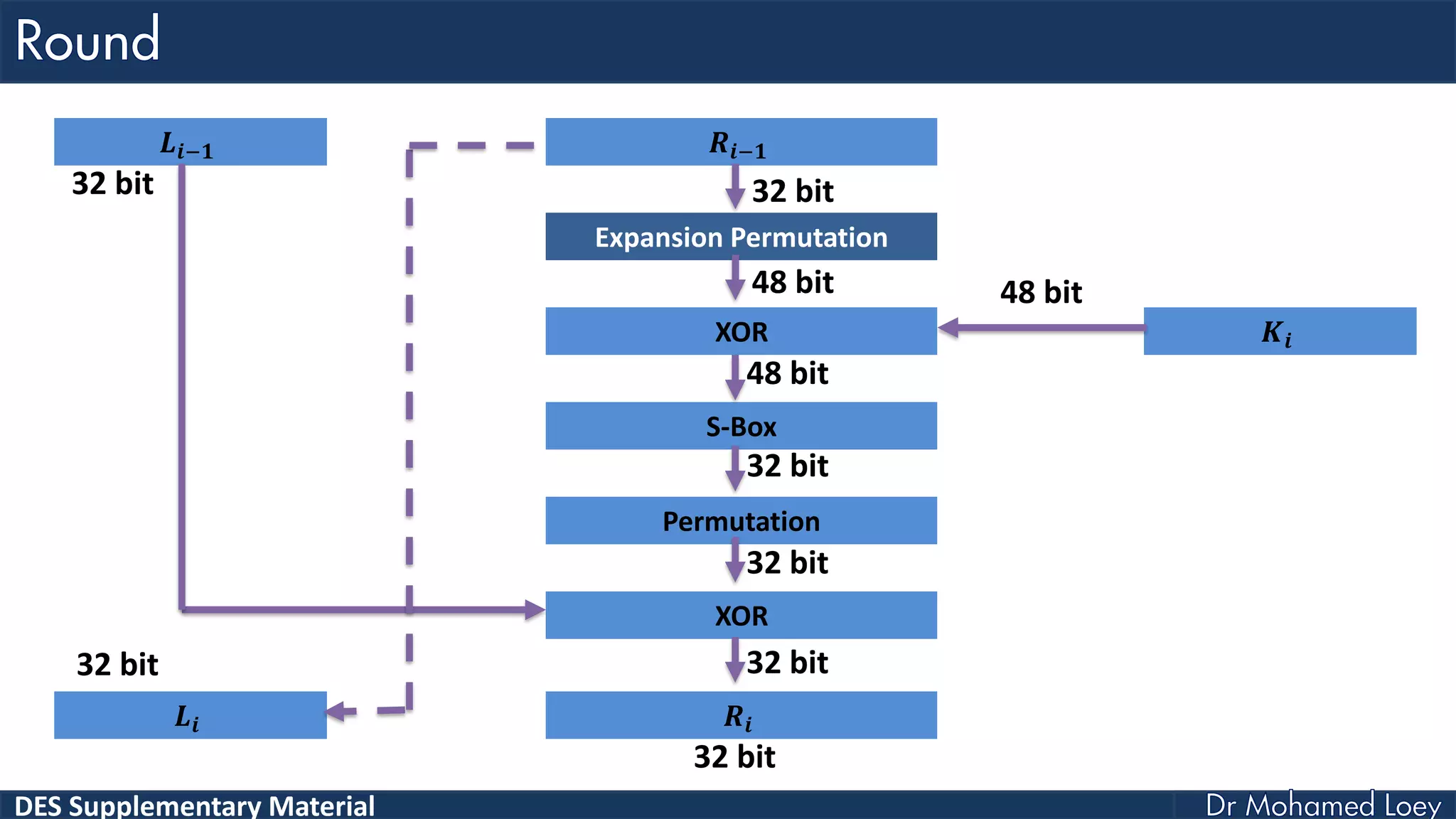
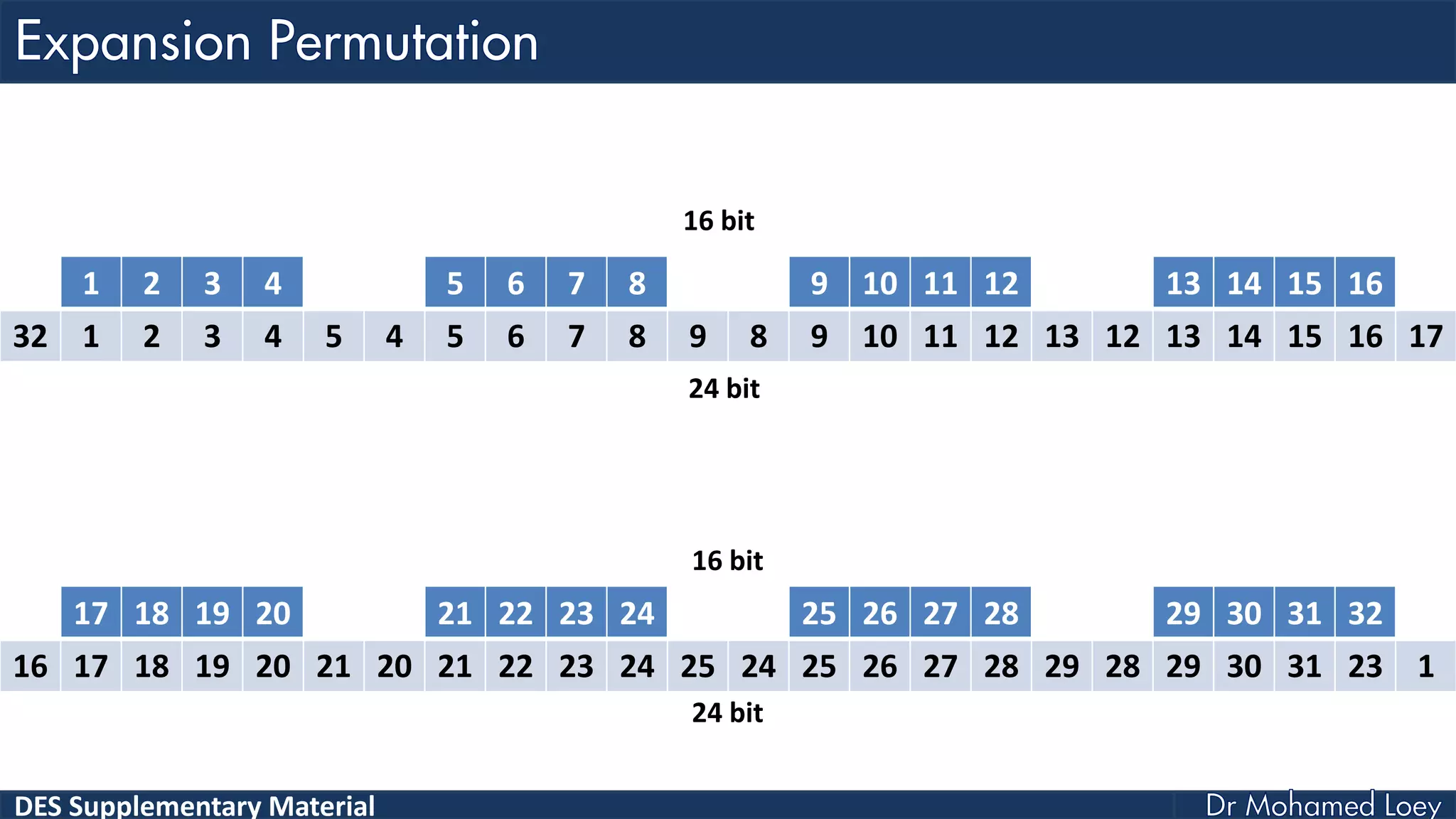
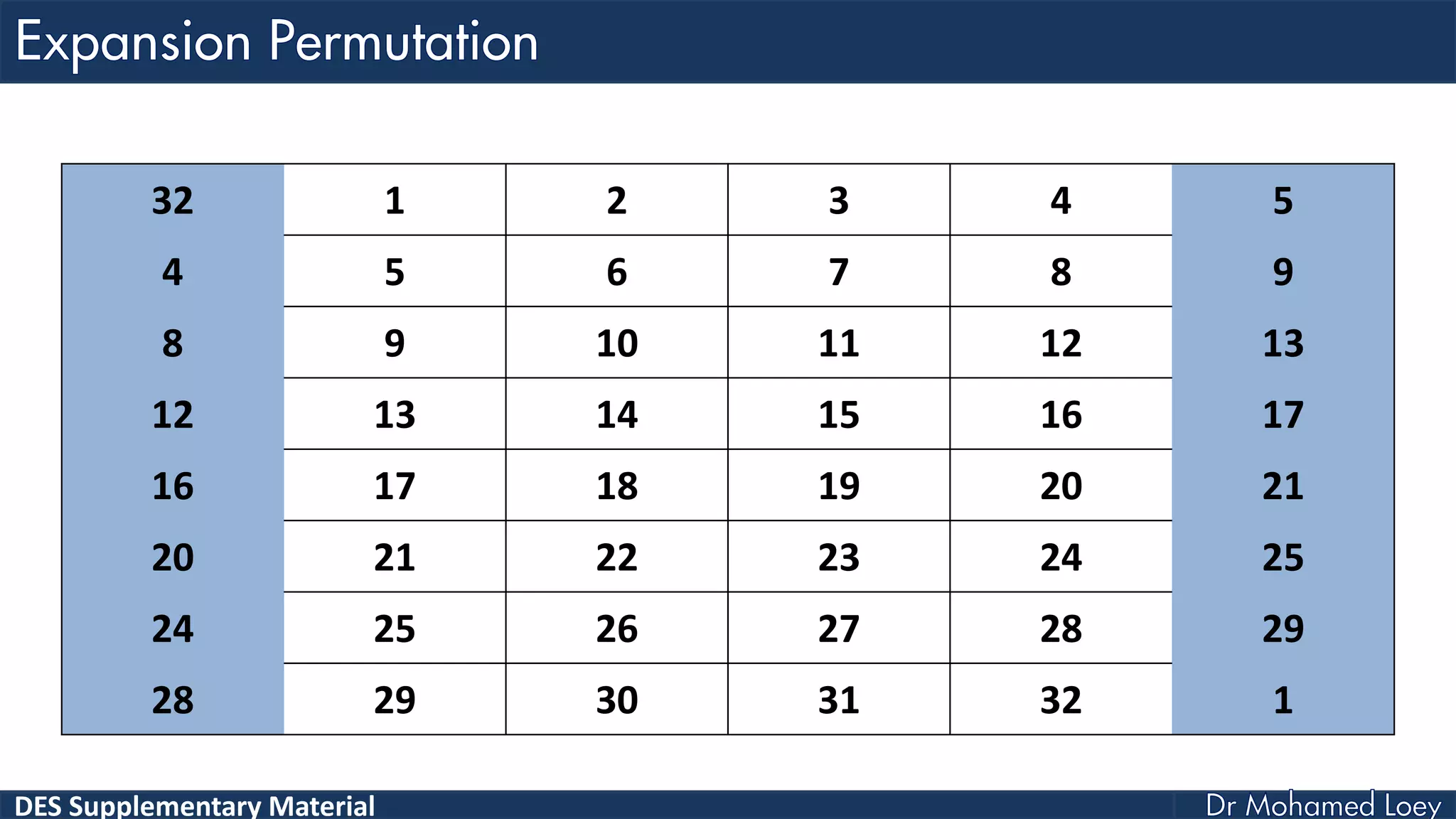
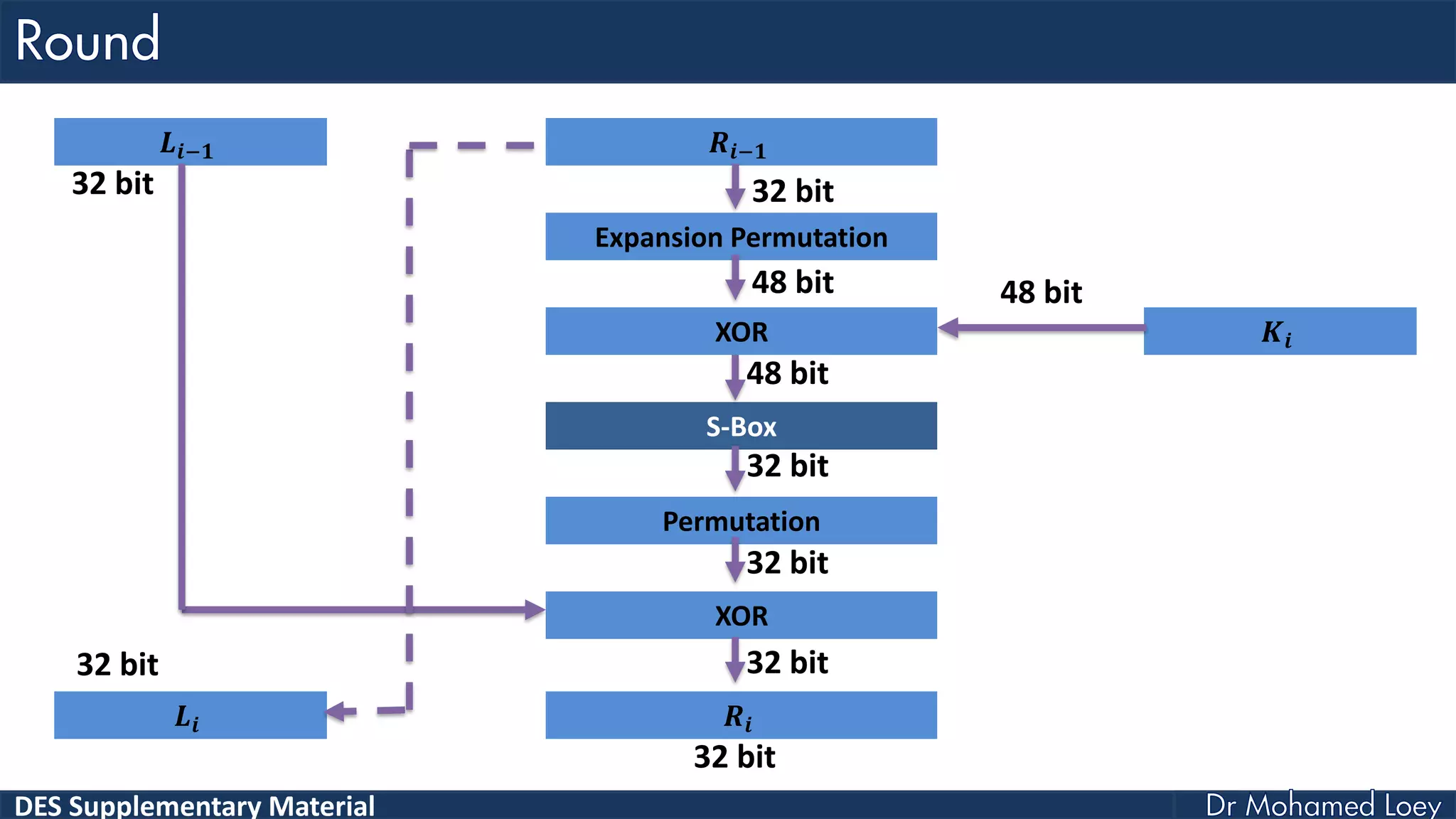
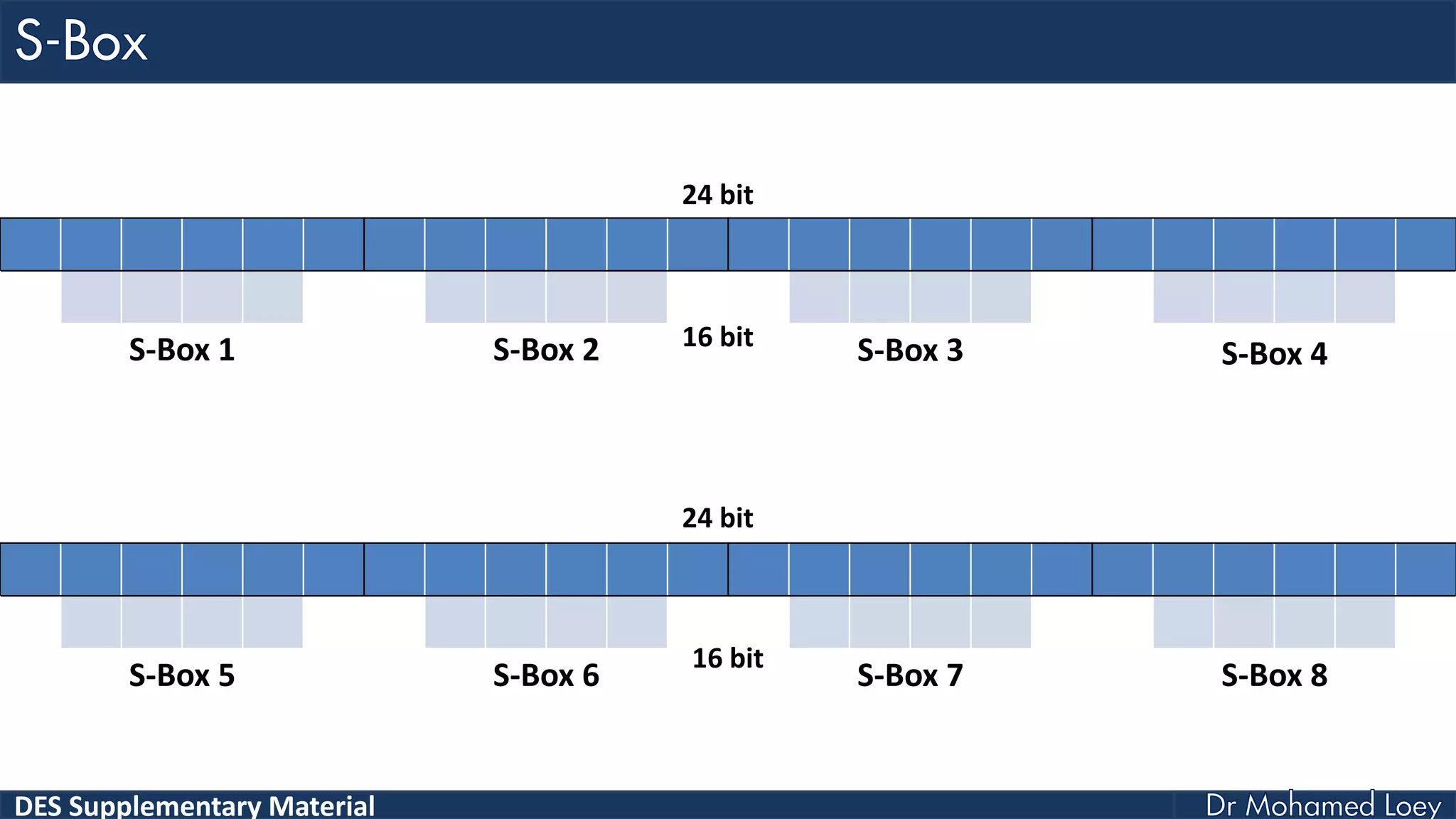
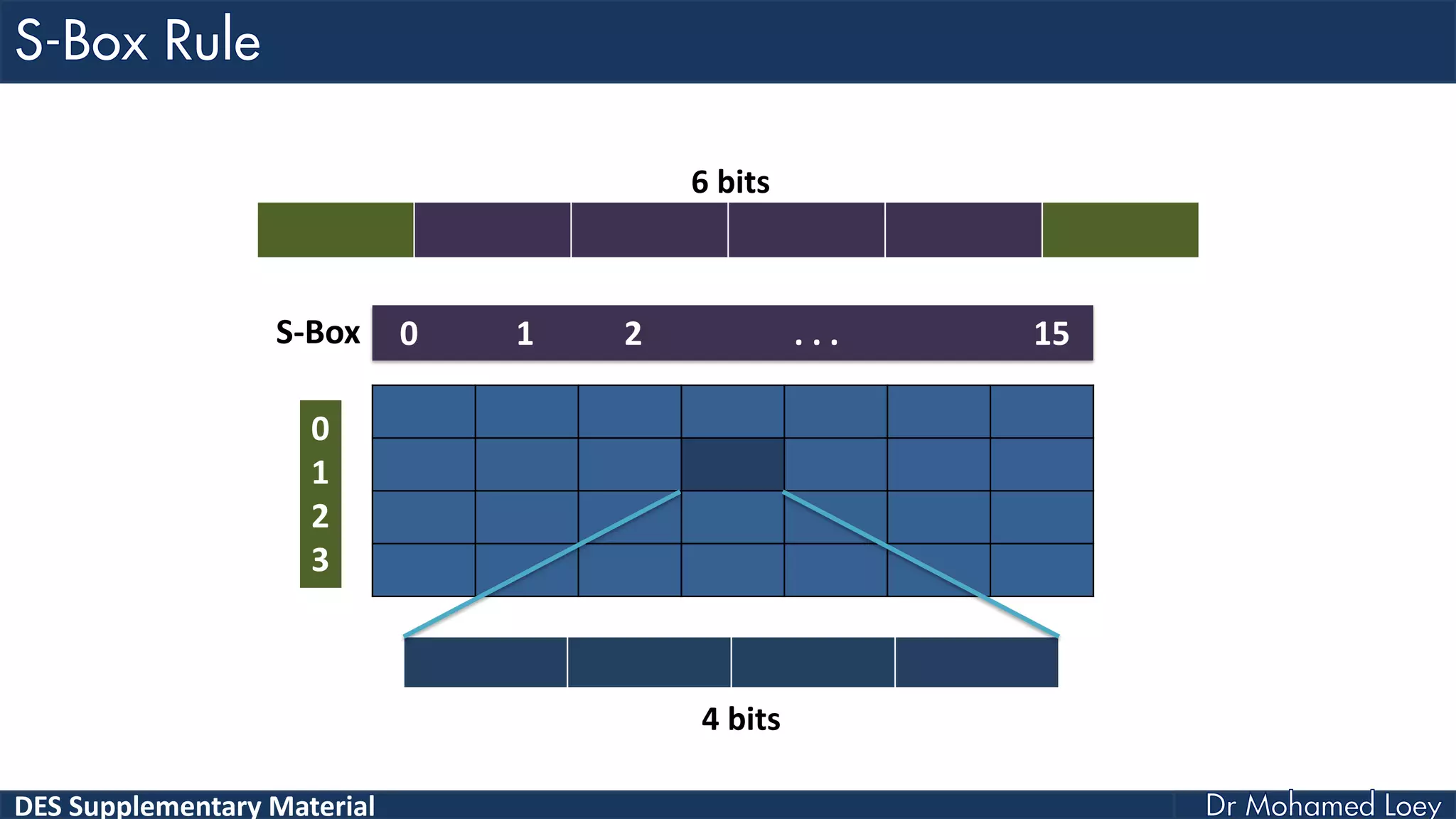
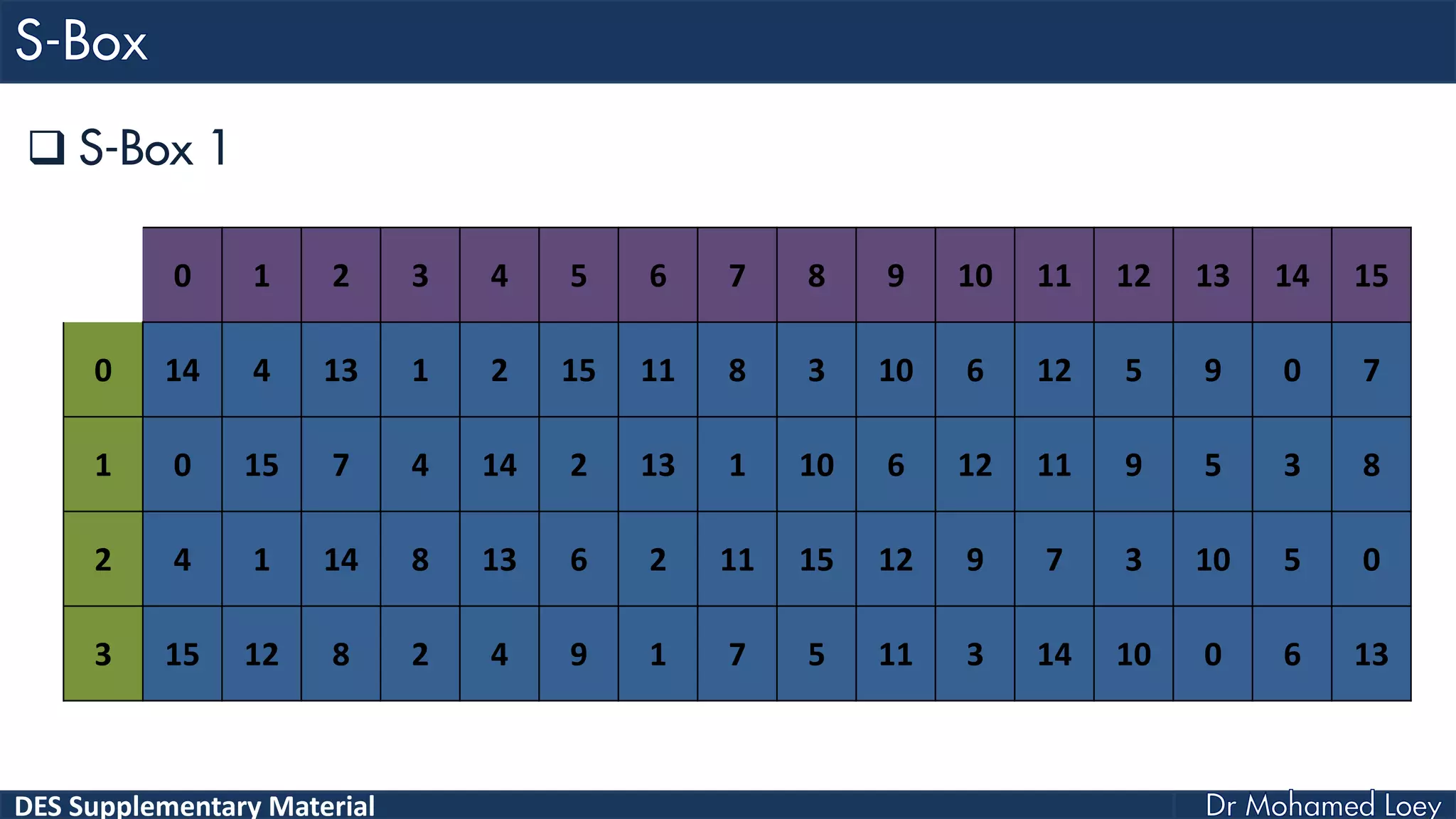
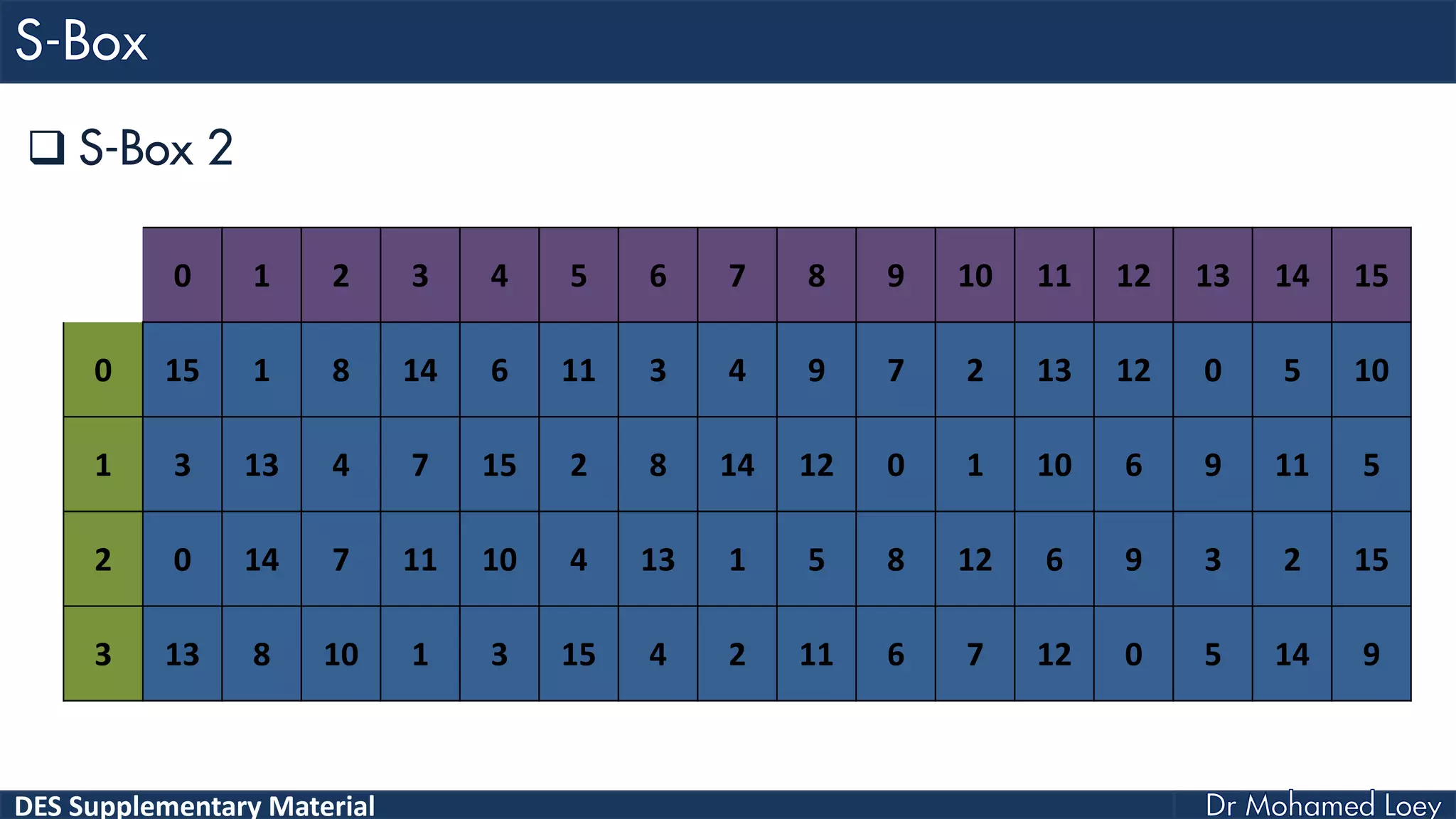
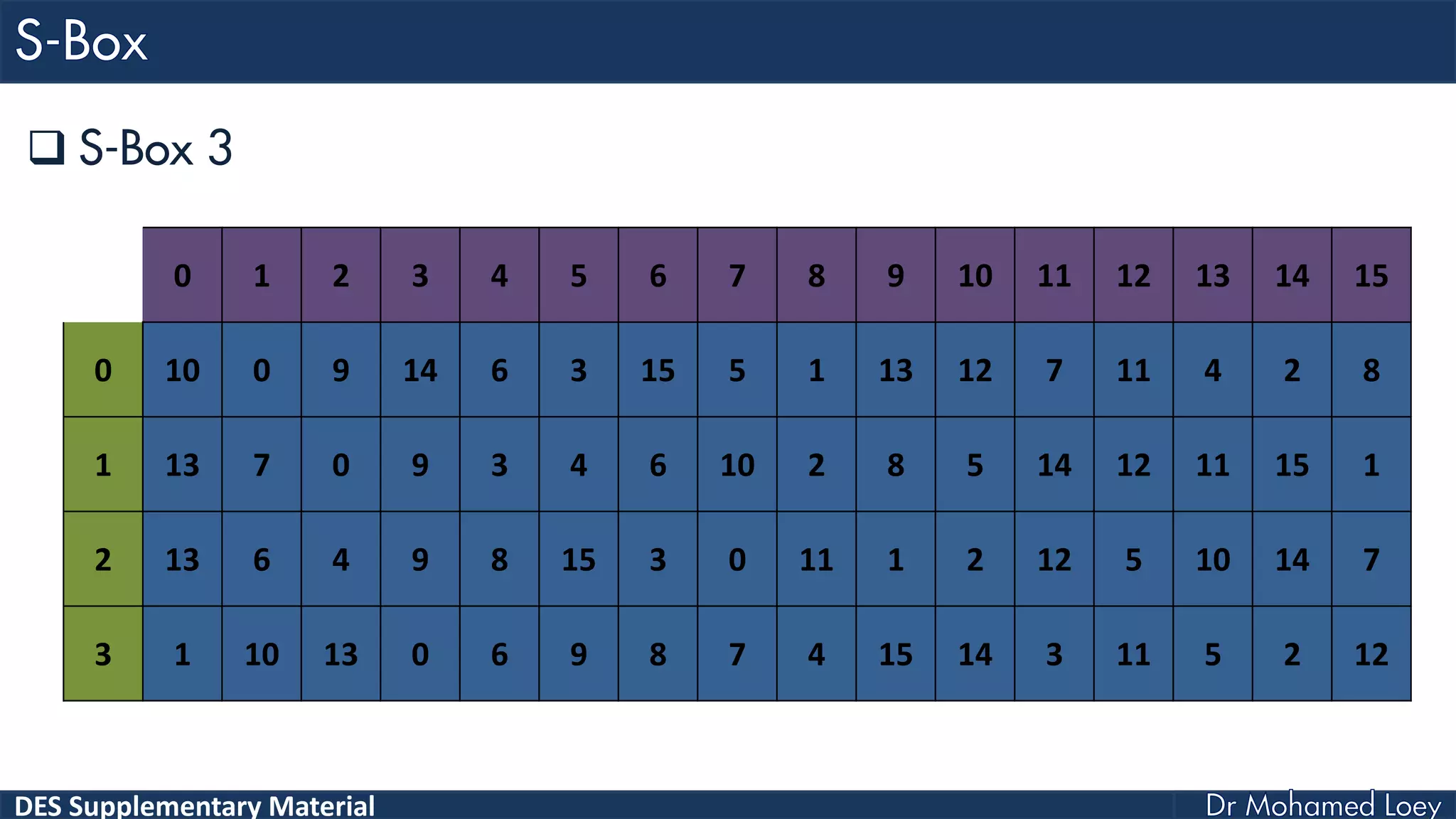
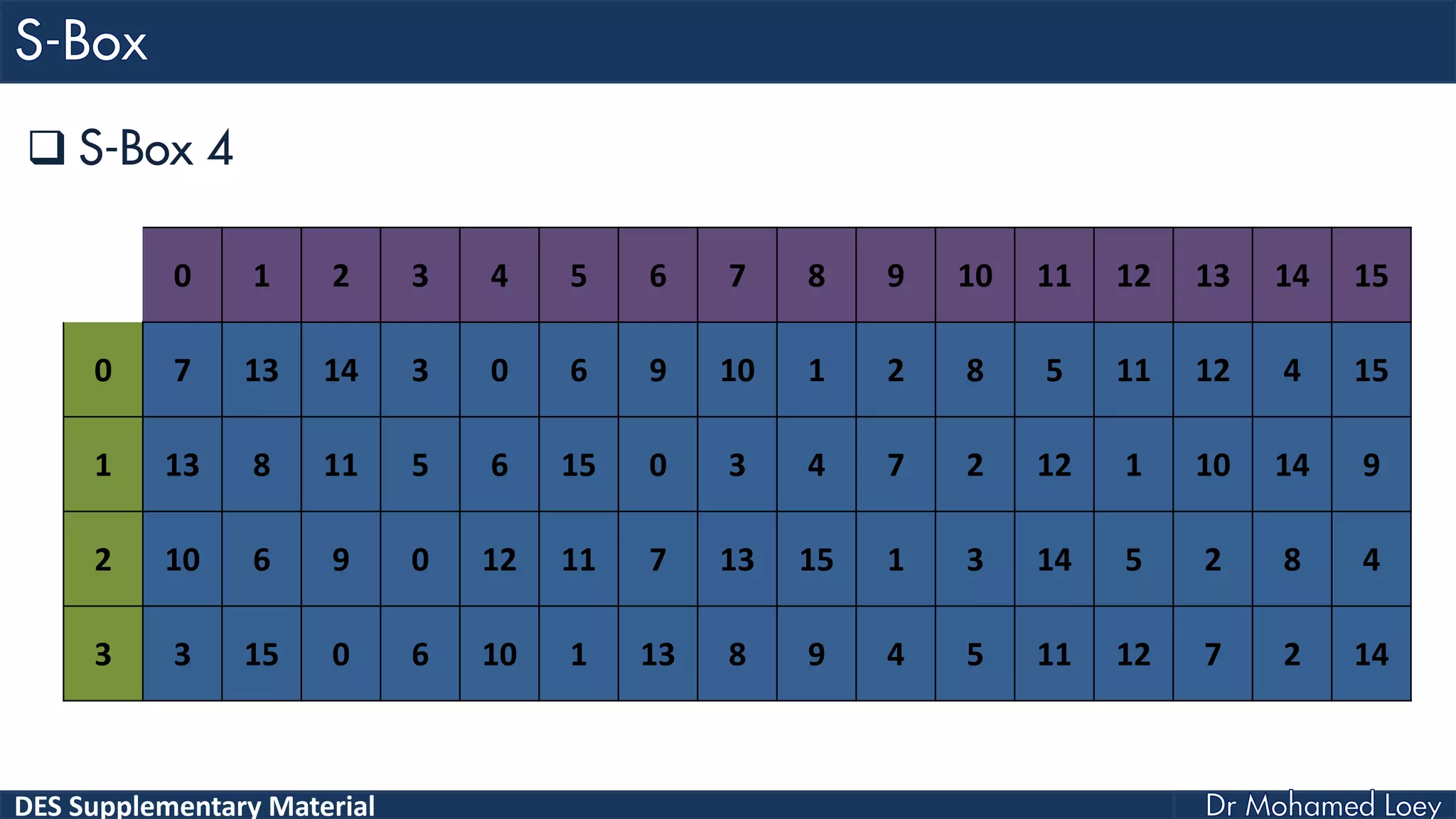
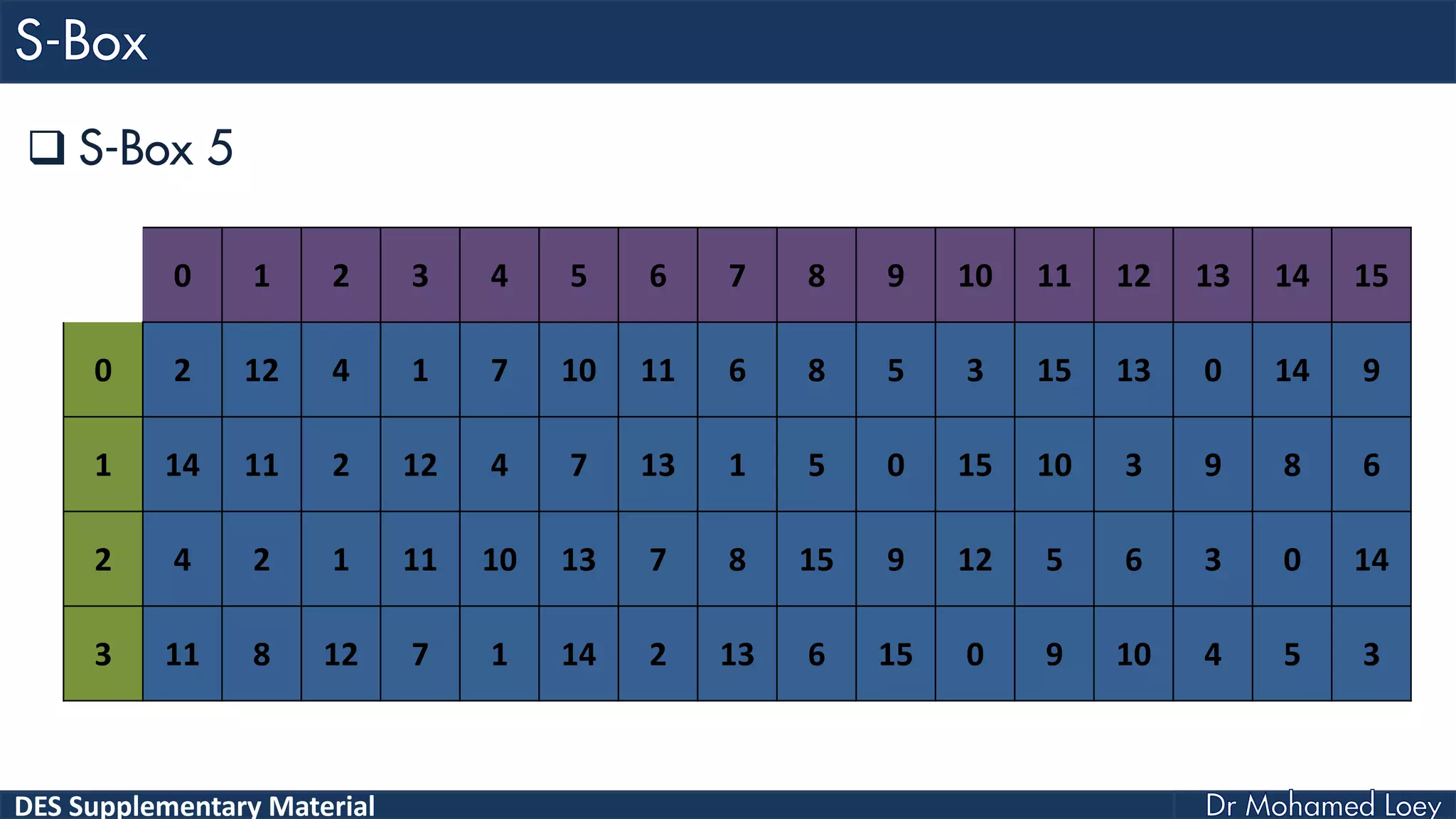
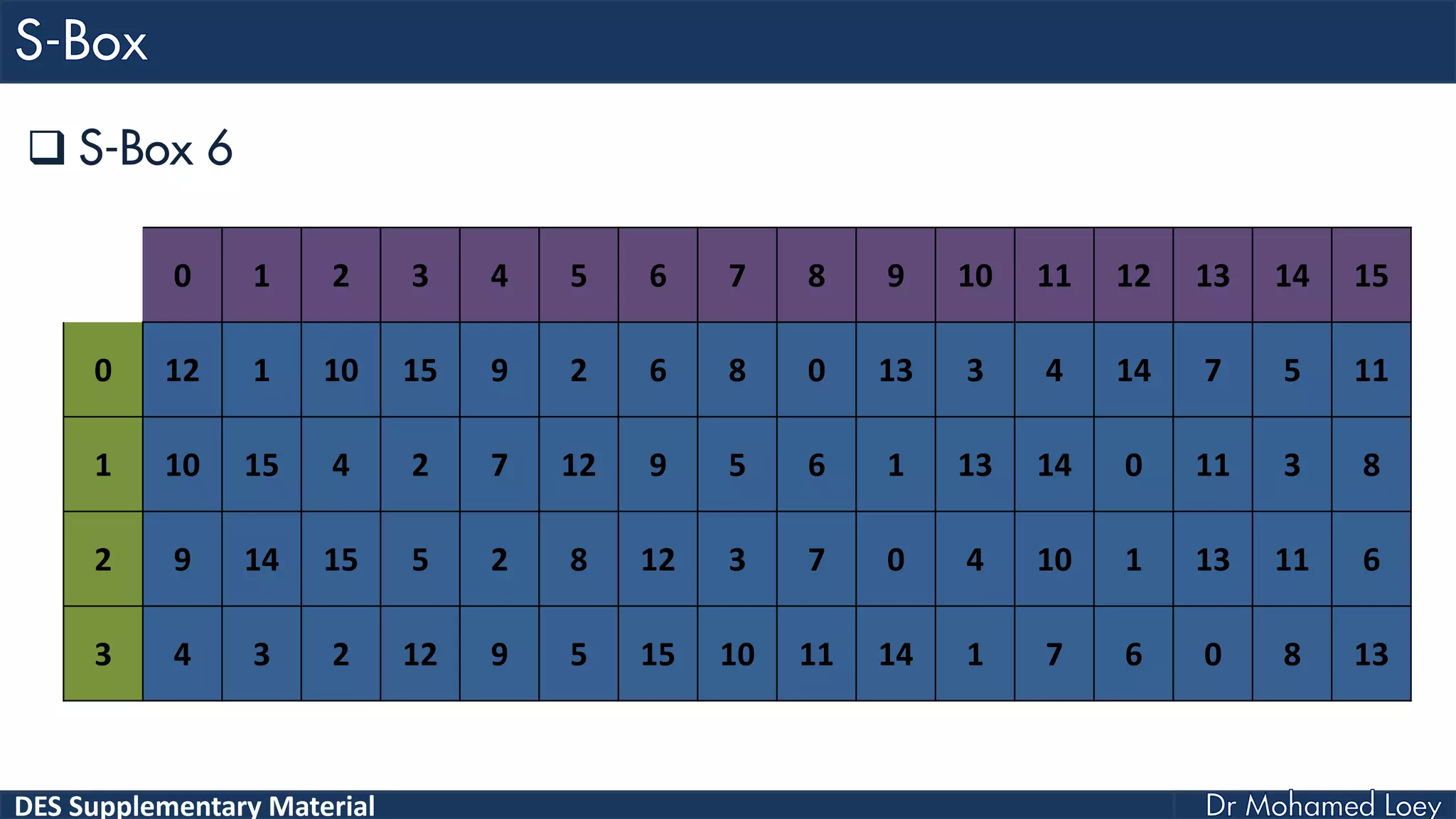
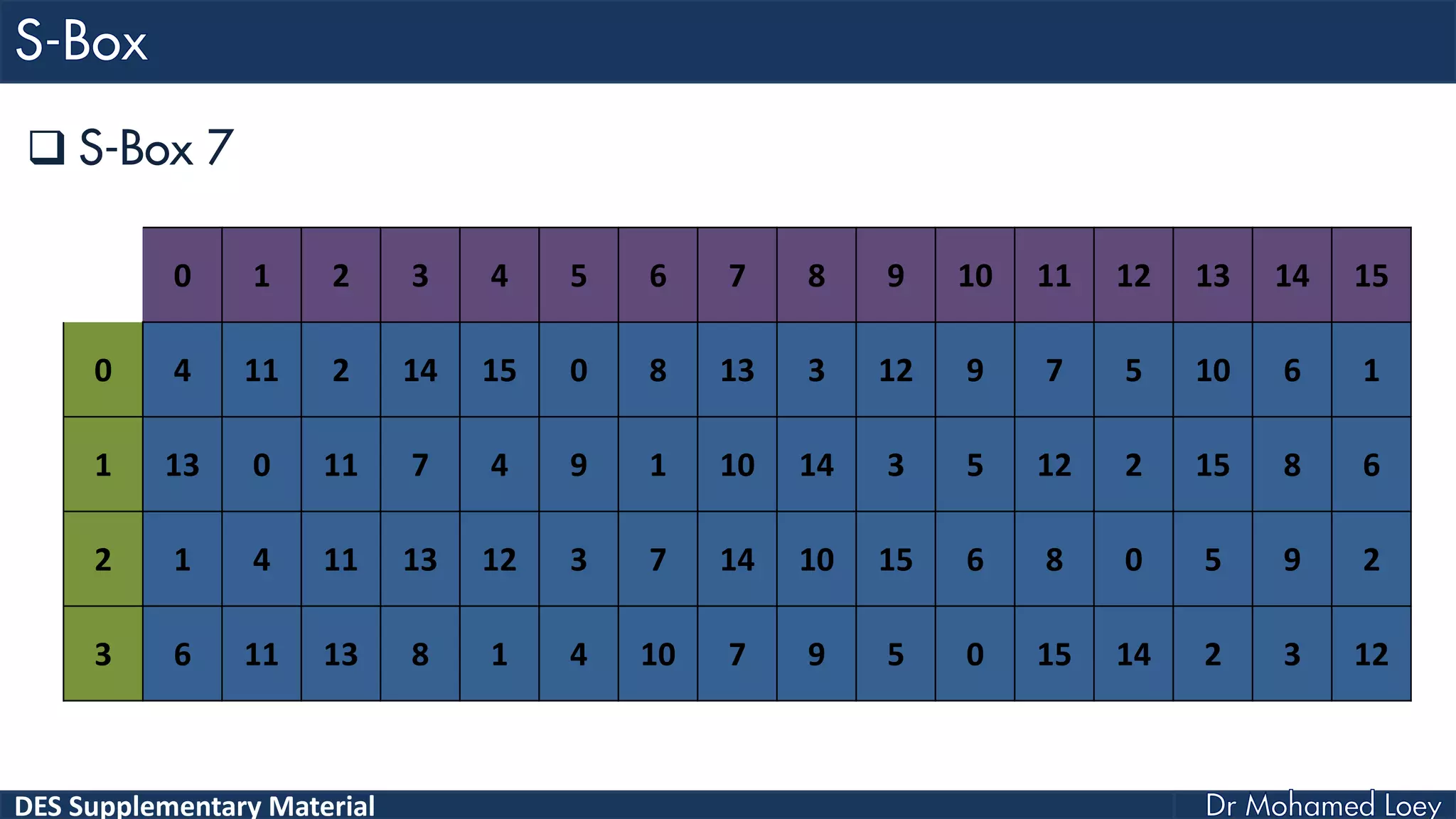
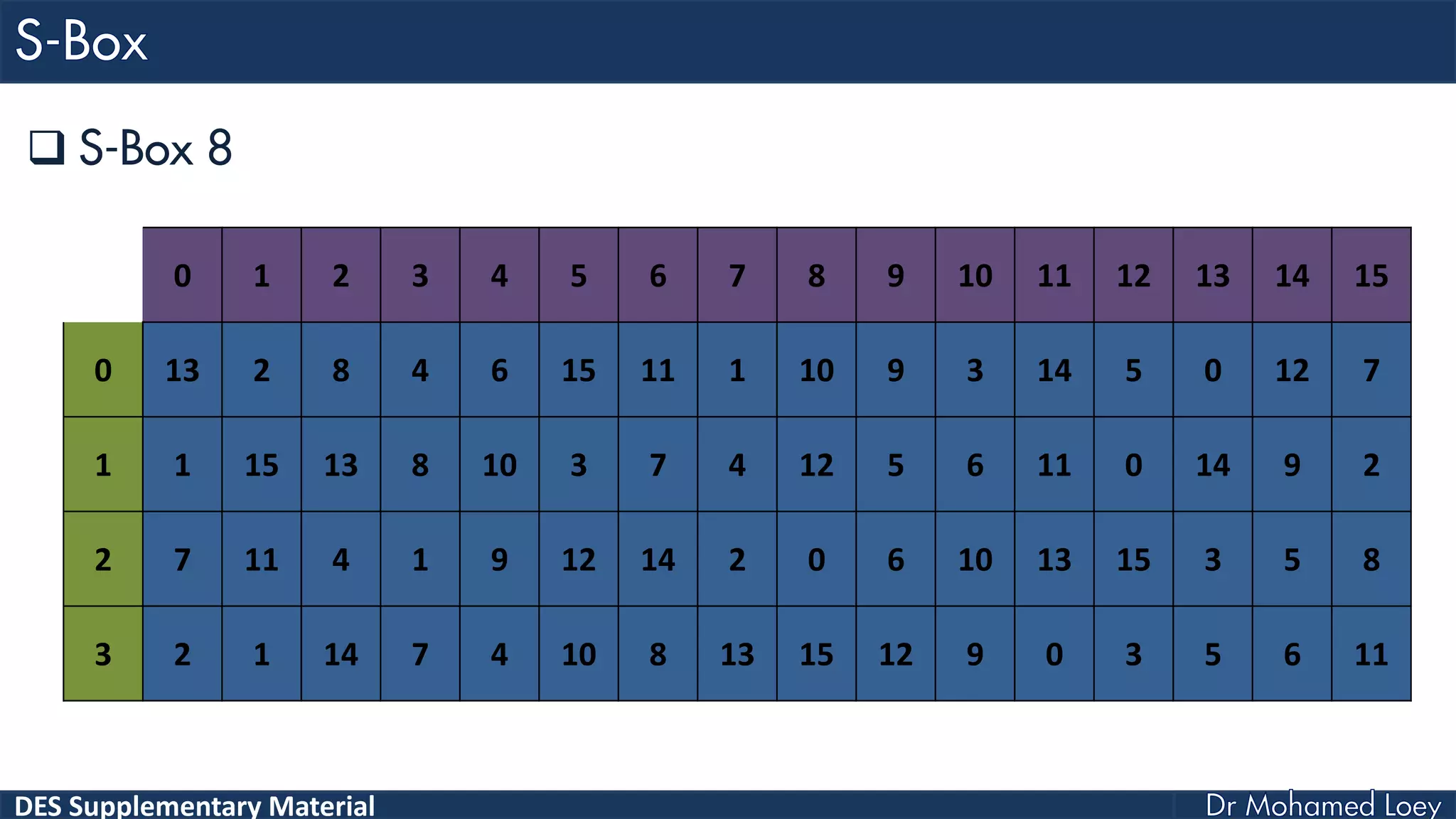
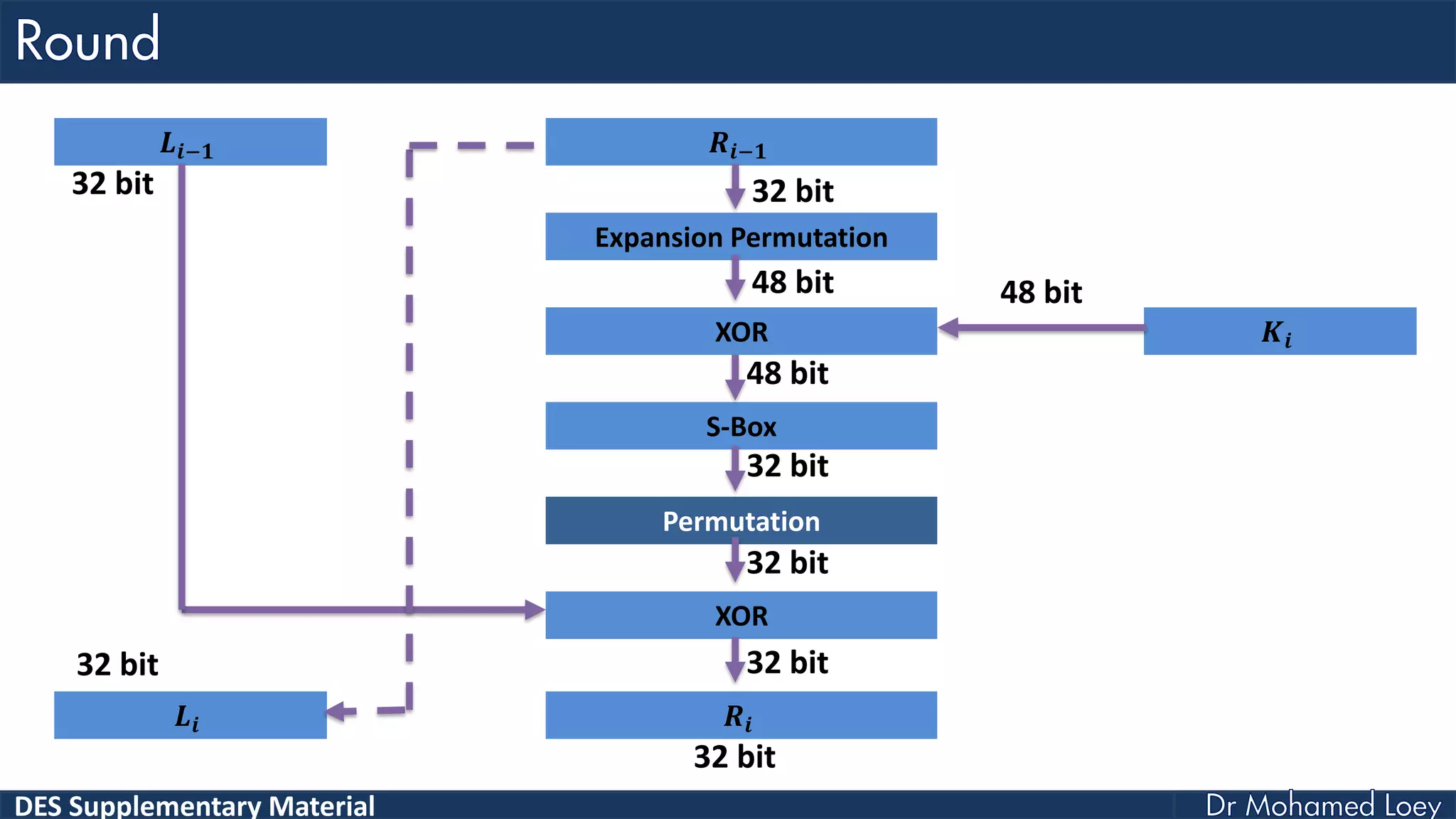
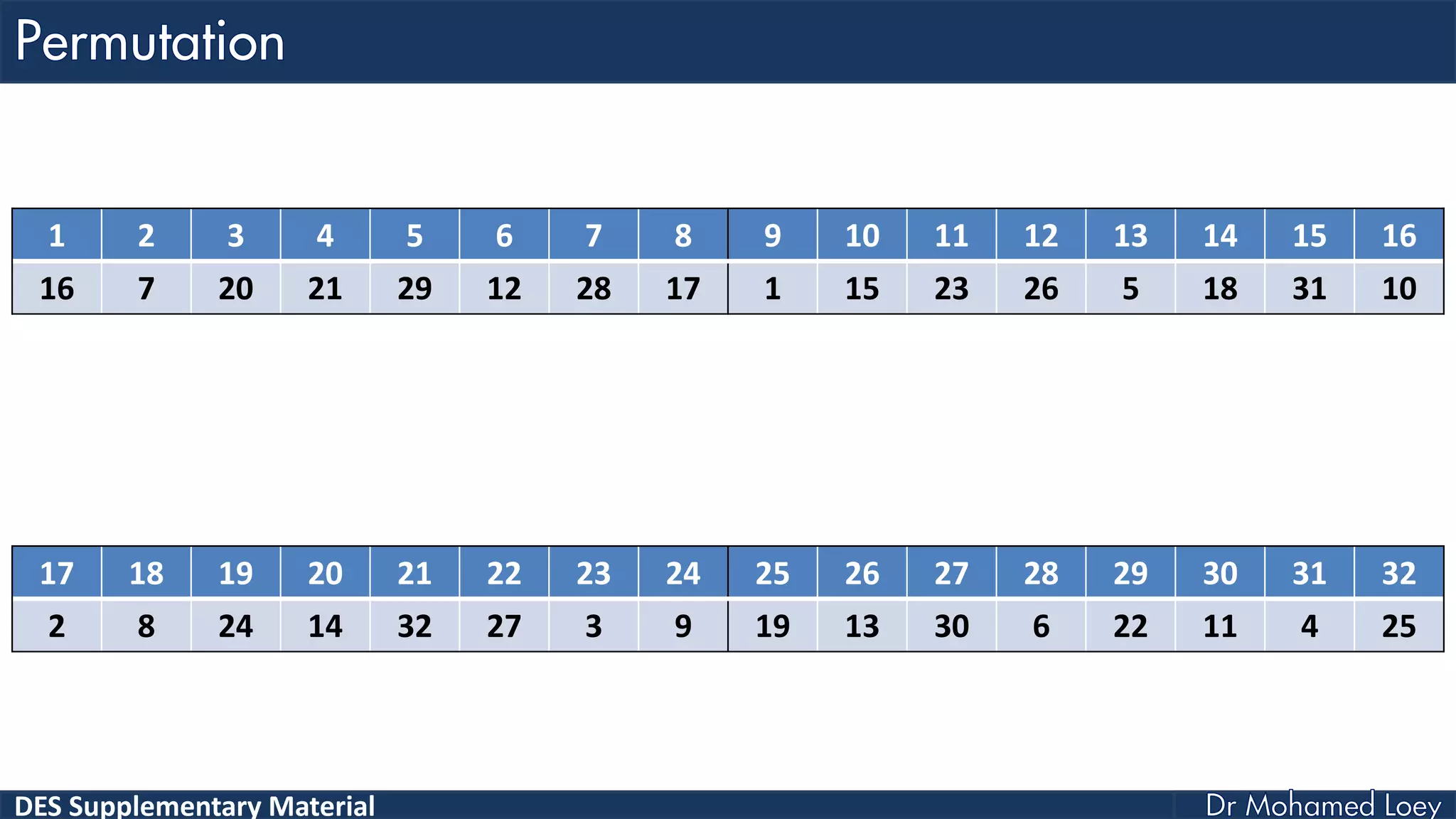
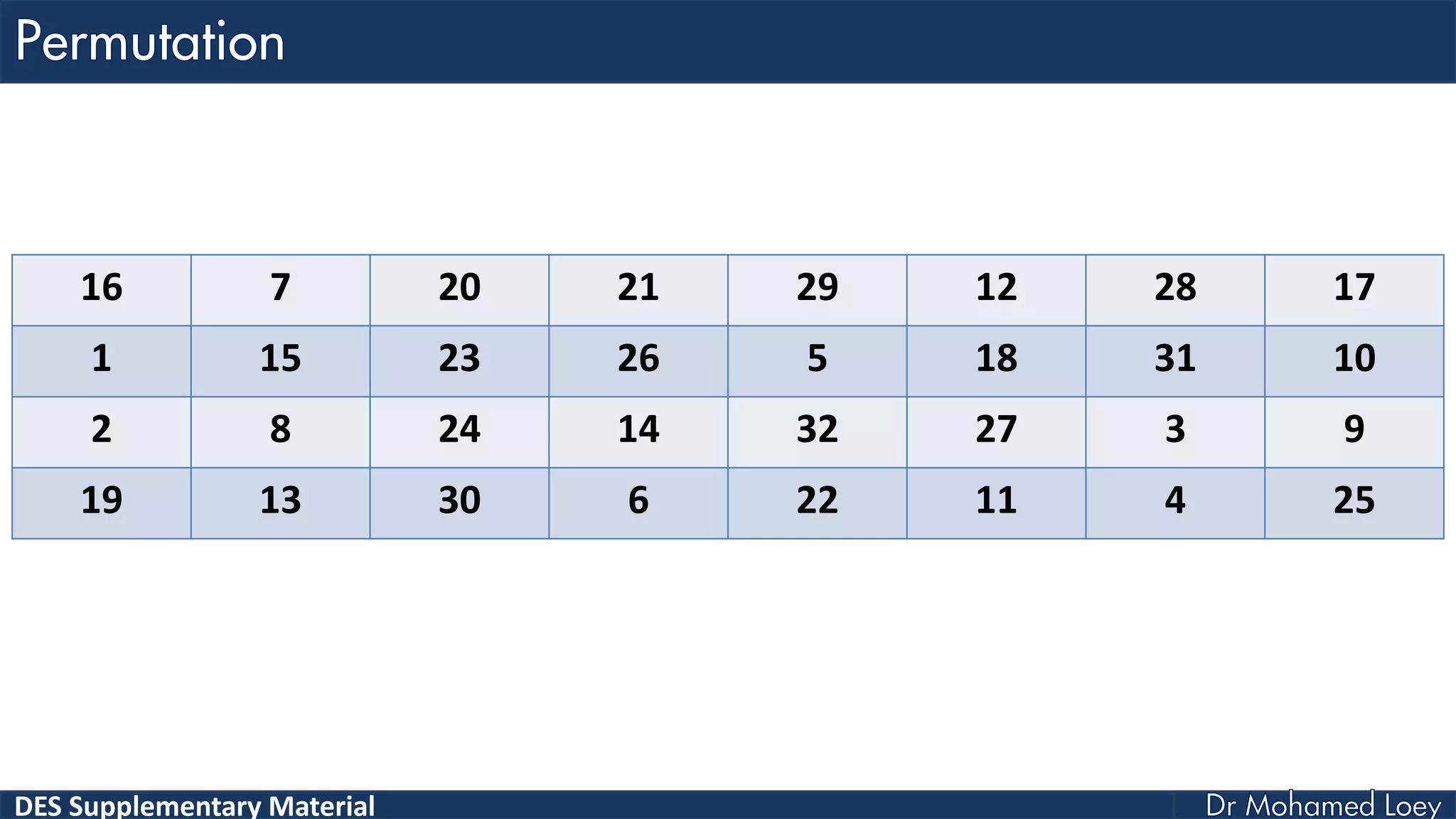
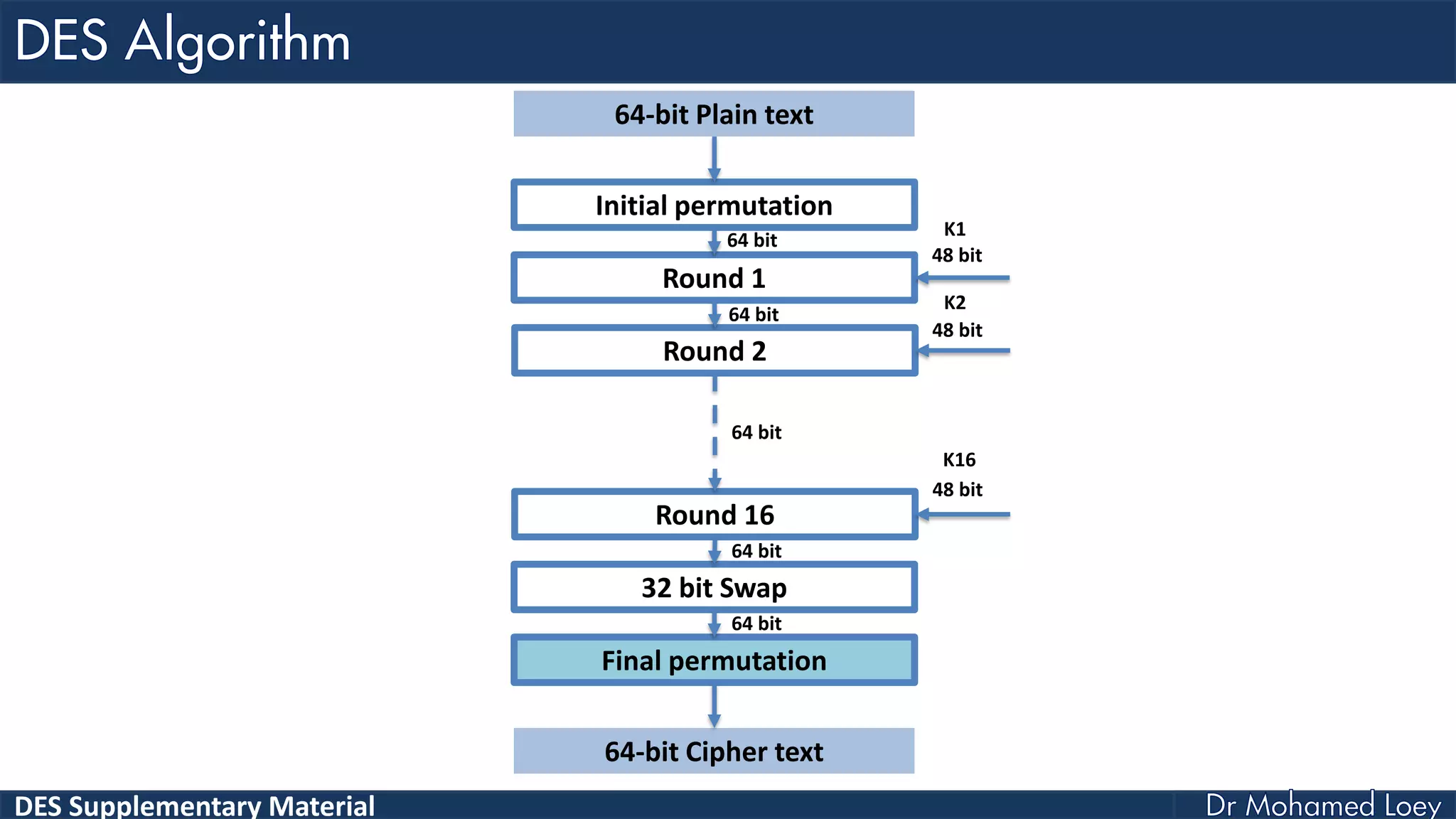
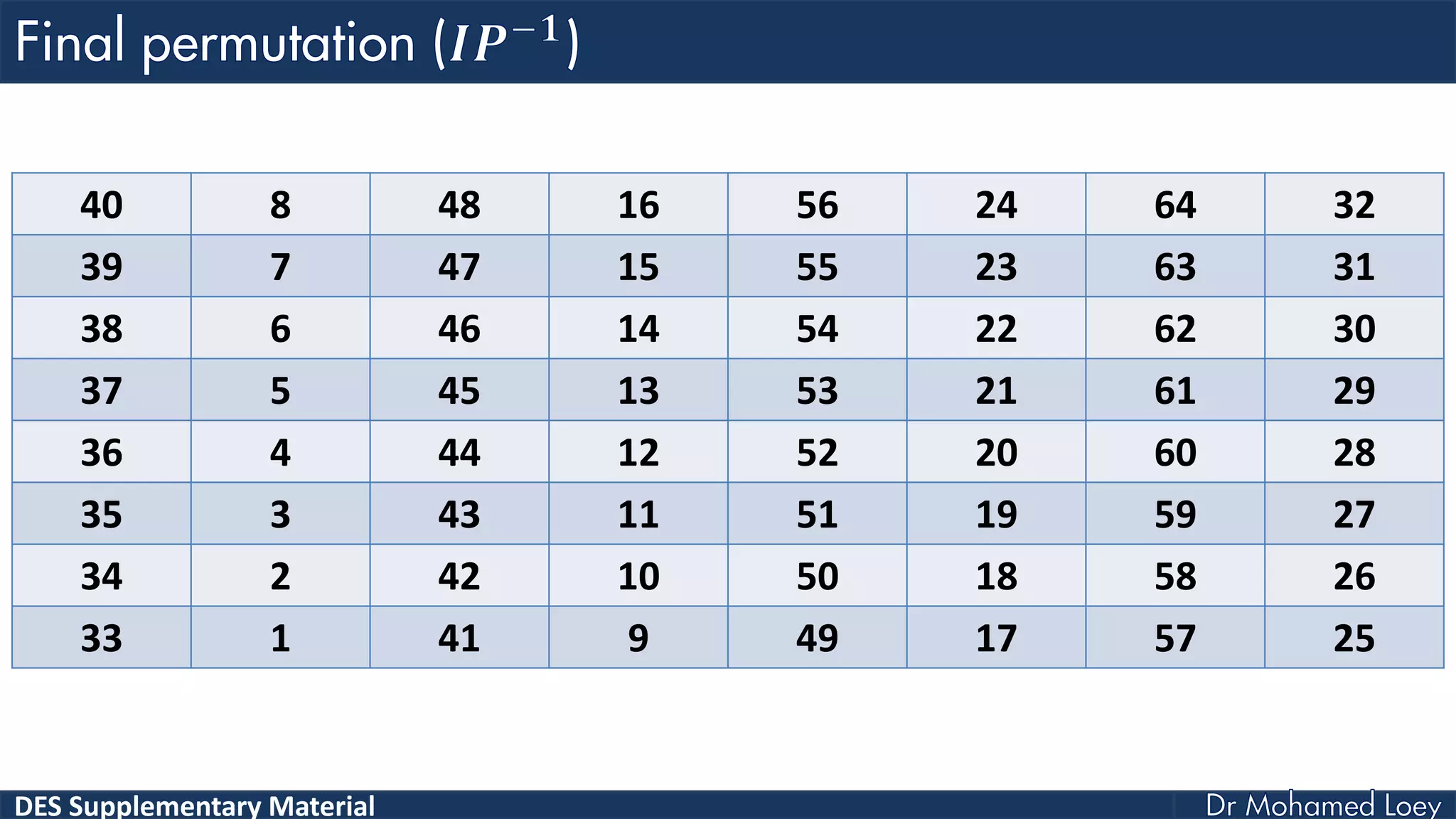
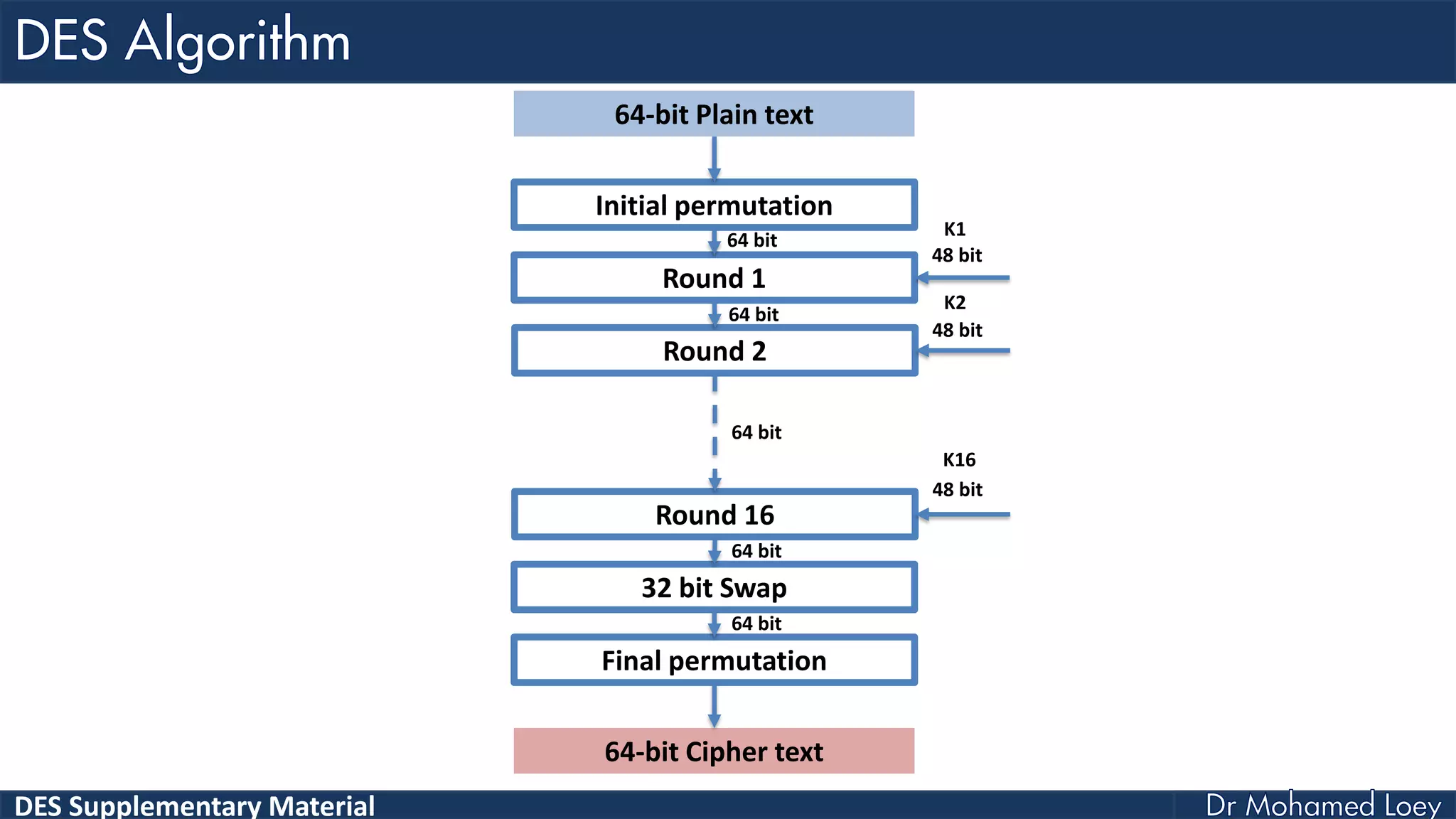
The document discusses the DES (Data Encryption Standard) encryption algorithm, detailing its processes including initial and final permutations, key shifts, and S-boxes. It provides a systematic breakdown of the encryption rounds and permutations involved, showing how plaintext is transformed into ciphertext using specific bit manipulations. Various tables and key schedules are included to illustrate the steps and components necessary for executing the algorithm.