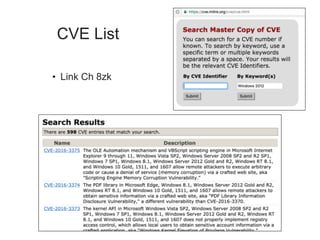
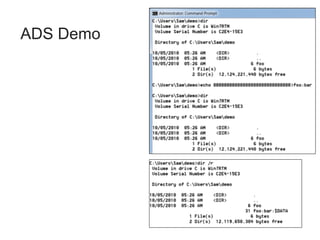
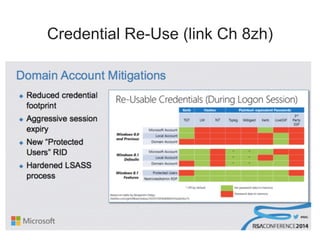
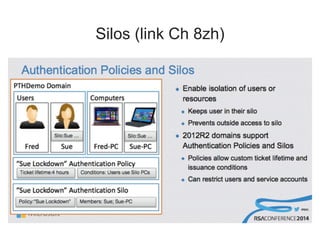
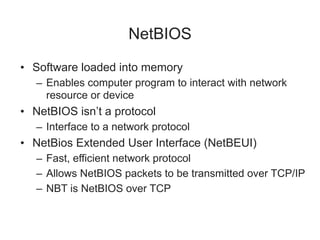
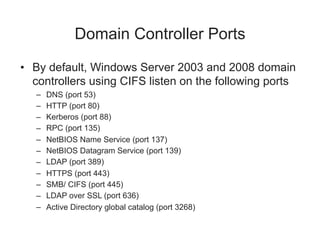
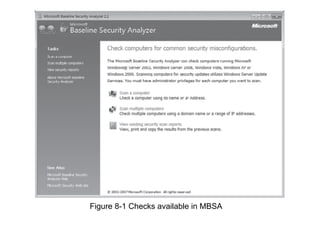
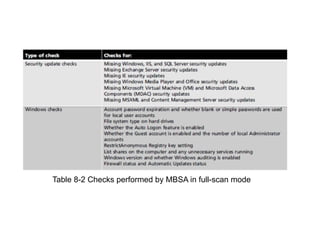
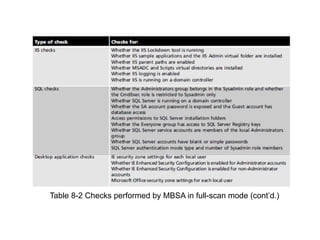
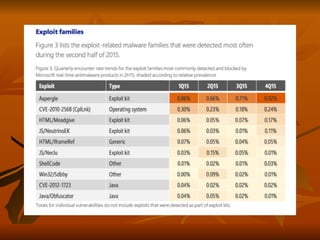
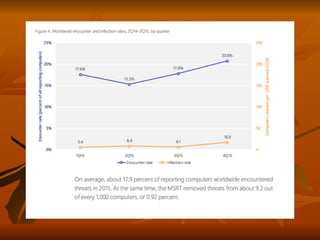
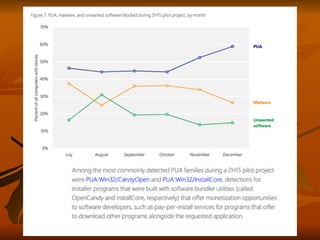
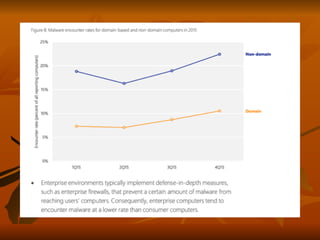
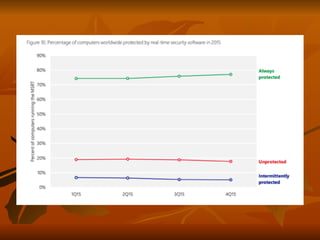
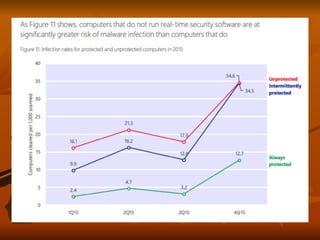
Chapter 8 of 'Hands-On Ethical Hacking and Network Defense' discusses vulnerabilities in Windows and Linux operating systems, highlighting major issues like legacy software flaws and lack of security protocols. It emphasizes the necessity of system hardening, regular updates, and awareness of password security as core components of network defense. The chapter also covers various tools for identifying vulnerabilities and best practices for ensuring system security, including configuration management and user training.