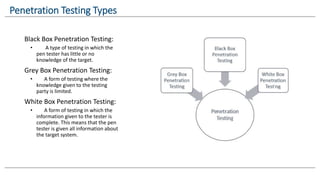
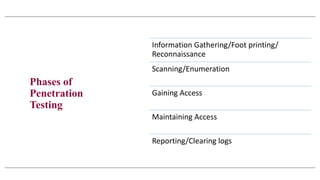
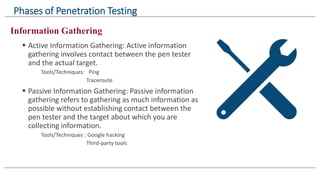
The document provides an overview of penetration testing, detailing its definition, types (black box, grey box, white box), and phases including information gathering, scanning, gaining access, maintaining access, and reporting. It emphasizes that penetration testing simulates attacks to assess the security of systems with permission from owners and utilizes various tools throughout the process. Key techniques highlighted include active and passive information gathering, scanning for vulnerabilities, and methods to maintain access and report findings.