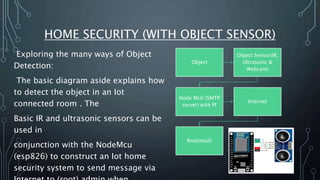
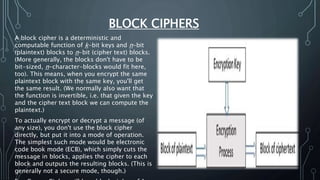
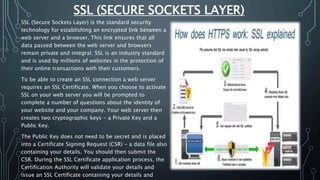
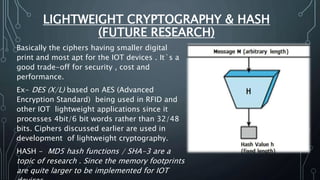
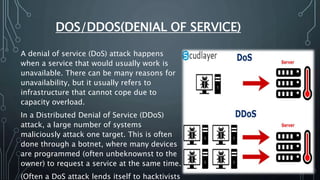
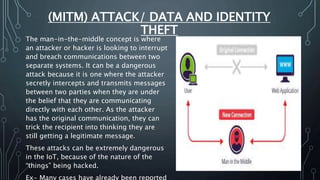
The document discusses Internet of Things (IoT) security challenges and countermeasures. It begins with basics of IoT and sensors, then discusses how IoT connects to the internet. It outlines several approaches to securing IoT, including restricted access, encryption of network and data, managing default APIs, addressing human elements of security, and learning from past exploits. Specific threats like denial of service attacks, man-in-the-middle attacks, and brute force/dictionary attacks are examined. The document concludes that IoT security design must enable open yet secure infrastructure while respecting user privacy through individual policies.