The document provides an overview of incident response including:
1) It defines the difference between an event and an incident, noting that all incidents are events but not all events are incidents.
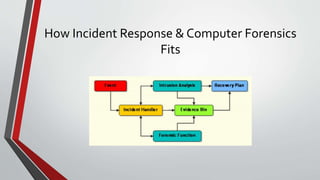
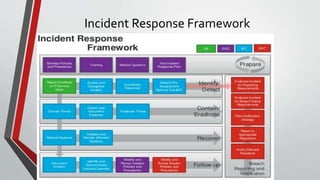
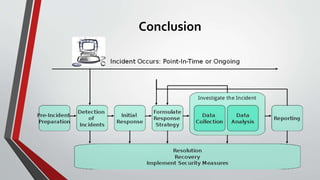
2) It outlines the typical steps in an incident response framework including pre-incident preparation, detection, initial response, formulating a response strategy, investigation, reporting, and resolution.
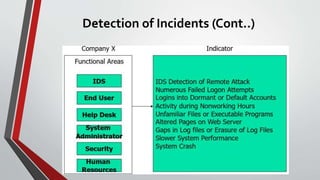
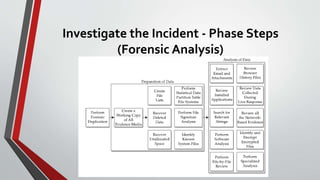
3) It describes each step in more detail, explaining activities like assembling an incident response team, collecting data, analyzing forensic evidence, documenting findings, restoring systems, and implementing countermeasures to prevent future incidents.