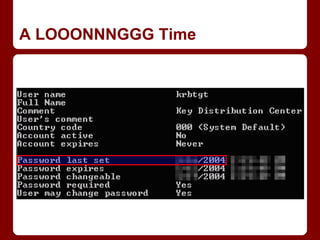
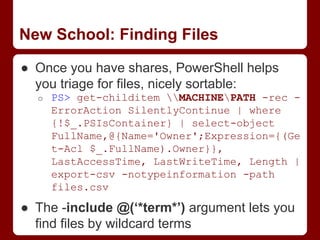
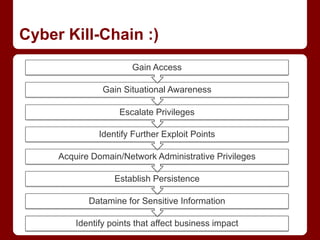
This document discusses tactics for red team operations on Windows networks. It begins by covering techniques for gaining initial access and situational awareness, such as using PowerShell commands to enumerate users, computers, and network information. It then discusses abusing domain trust relationships and using PowerView to operate across trusts. Escalation techniques like PowerUp for privilege escalation and Mimikatz for token manipulation are also covered. The document discusses persistence methods like Golden Tickets and WMI. It finally covers techniques for locating and accessing file shares to retrieve sensitive information, using PowerView commands. The overall message is that while tactics remain the same, tools and implementations are continually evolving to facilitate red team operations.


















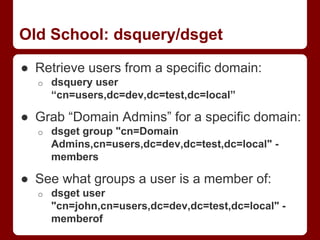
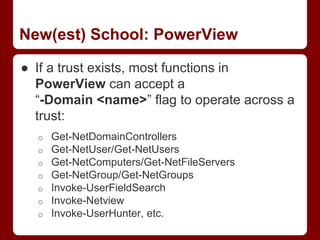
![New School: Trusts and PowerShell
● Of course you can do this (and with greater
ease) using PowerShell:
o ([System.DirectoryServices.ActiveDirecto
ry.Forest]::GetCurrentForest()).Domains
o ([System.DirectoryServices.ActiveDirecto
ry.Domain]::GetCurrentDomain()).GetAllTr
ustRelationships()
● PowerShell AD functionality can easily
operate on domains to which there's an
existing trust
o finding domain controllers, querying users,
enumerating domain groups, etc.](https://image.slidesharecdn.com/derbycon-passingthetorch-140926164850-phpapp01/85/Derbycon-Passing-the-Torch-27-320.jpg)