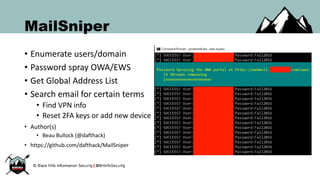
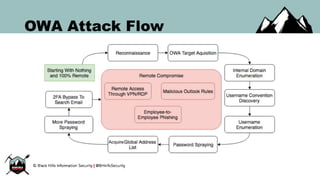
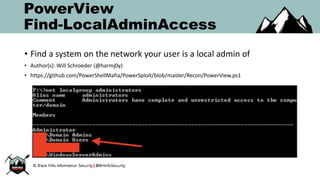
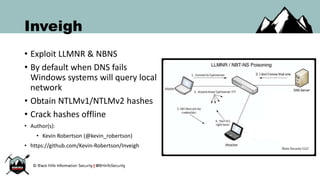
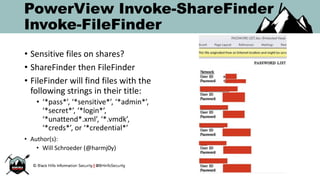
The document discusses the rise of PowerShell-based penetration testing tools and provides an overview of using PowerShell for various cyber attack techniques, including remote attacks, privilege escalation, and post-exploitation. It highlights specific tools and methods, such as PowerMeta for metadata extraction, MailSniper for email enumeration, and Invoke-Mimikatz for credential extraction, along with effective mitigations against these attacks. The conclusion emphasizes the ongoing power and adaptability of PowerShell in cyber threats while underscoring the need for enhanced defensive measures.