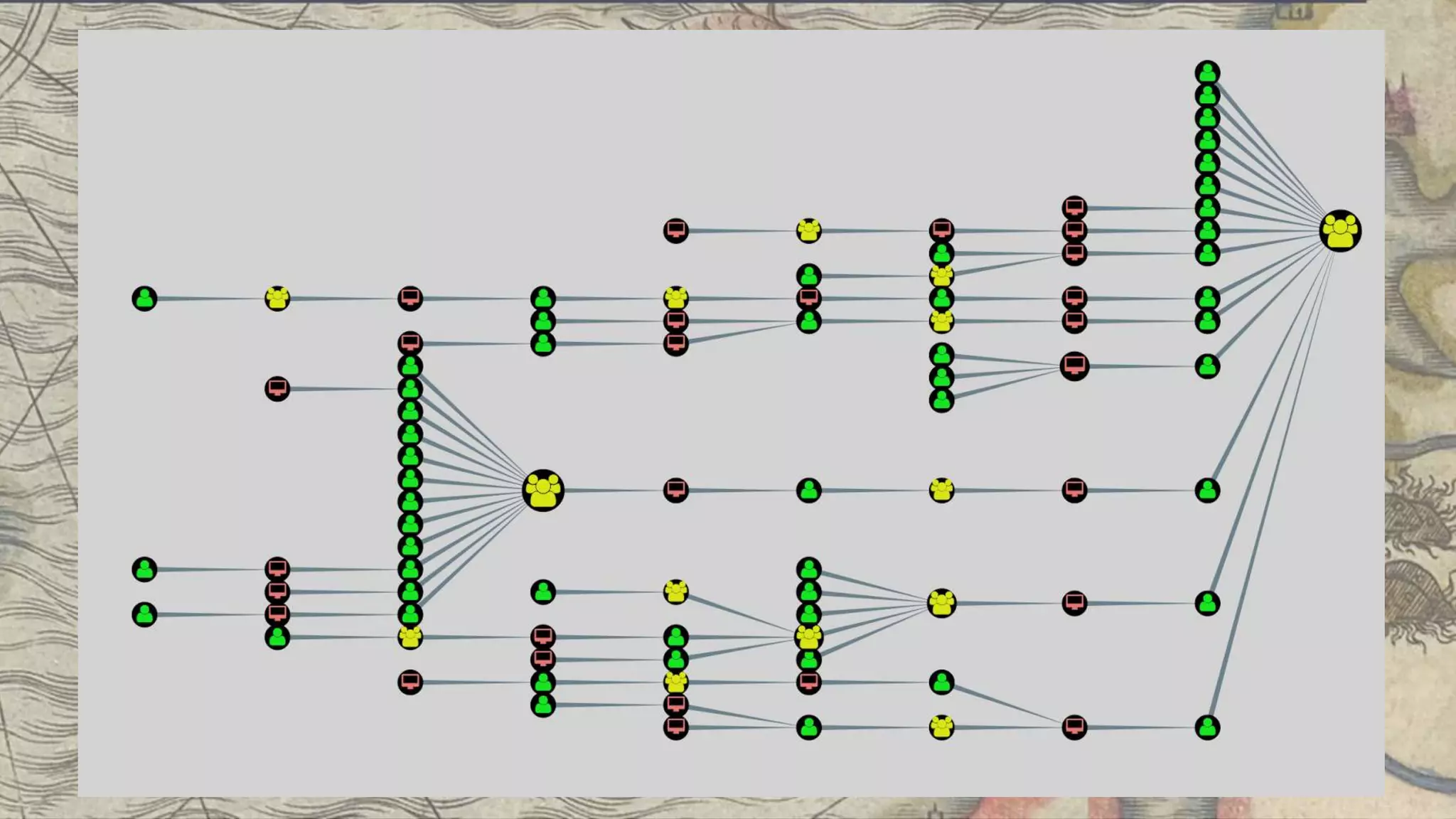
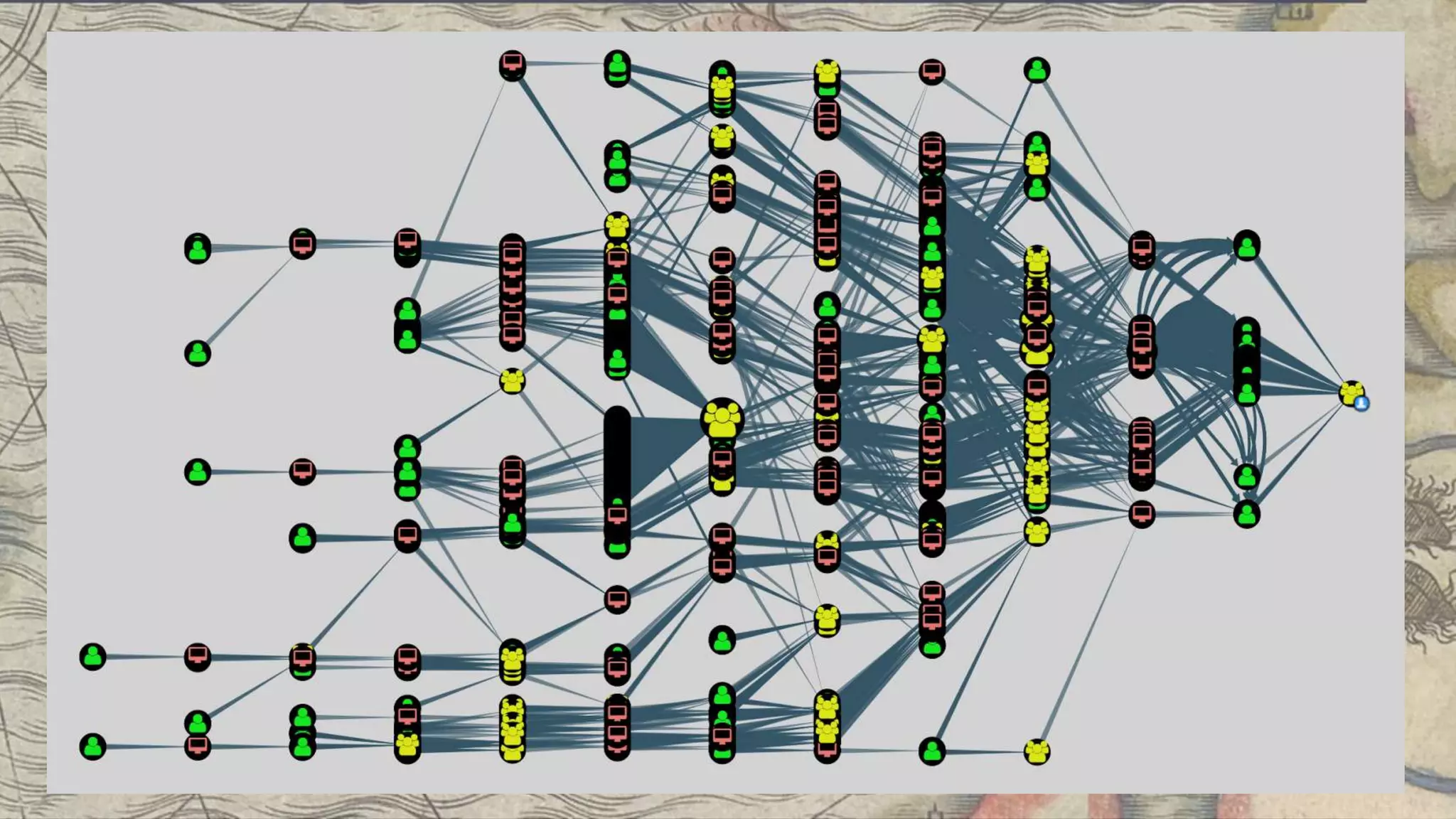
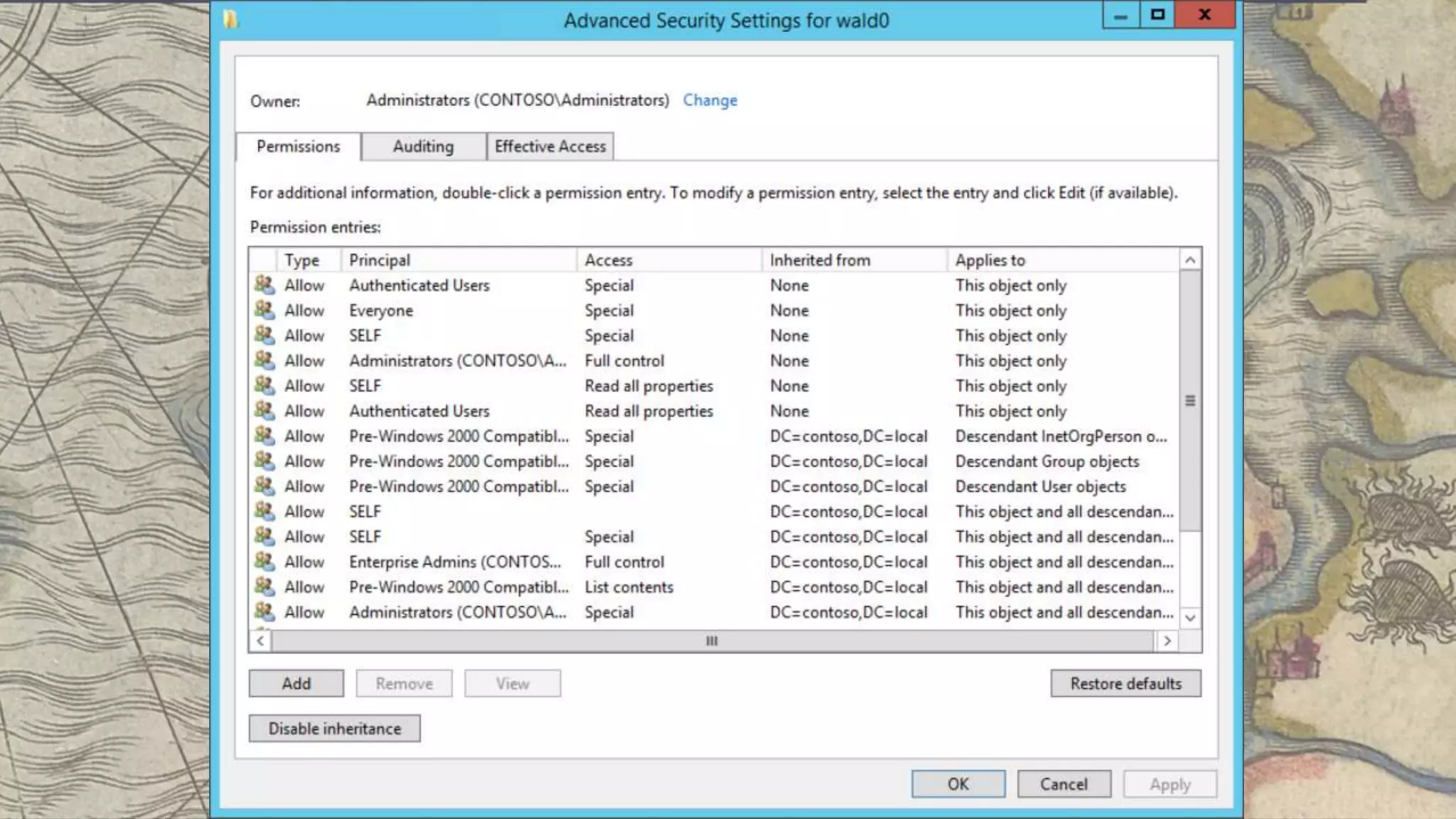
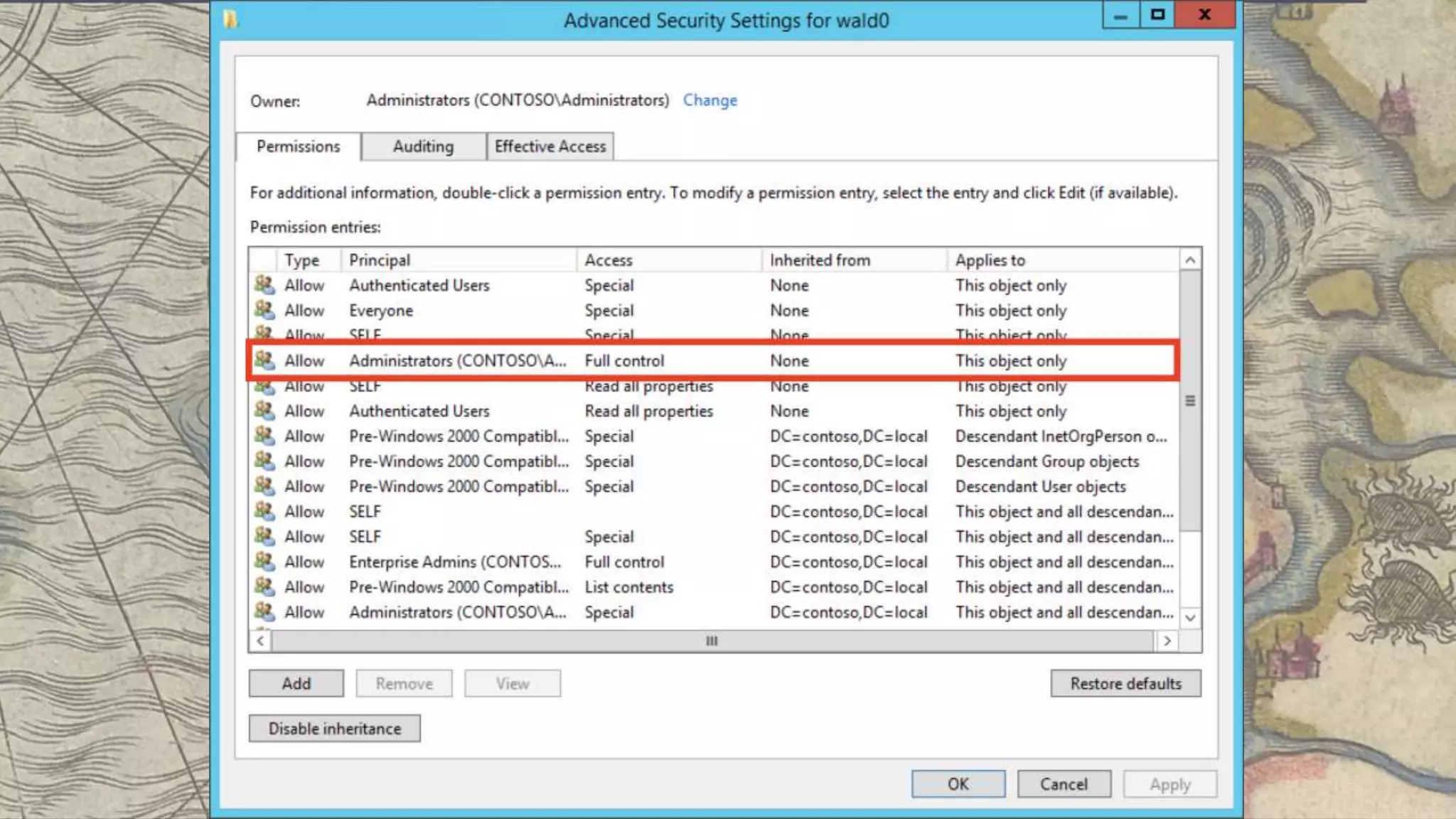
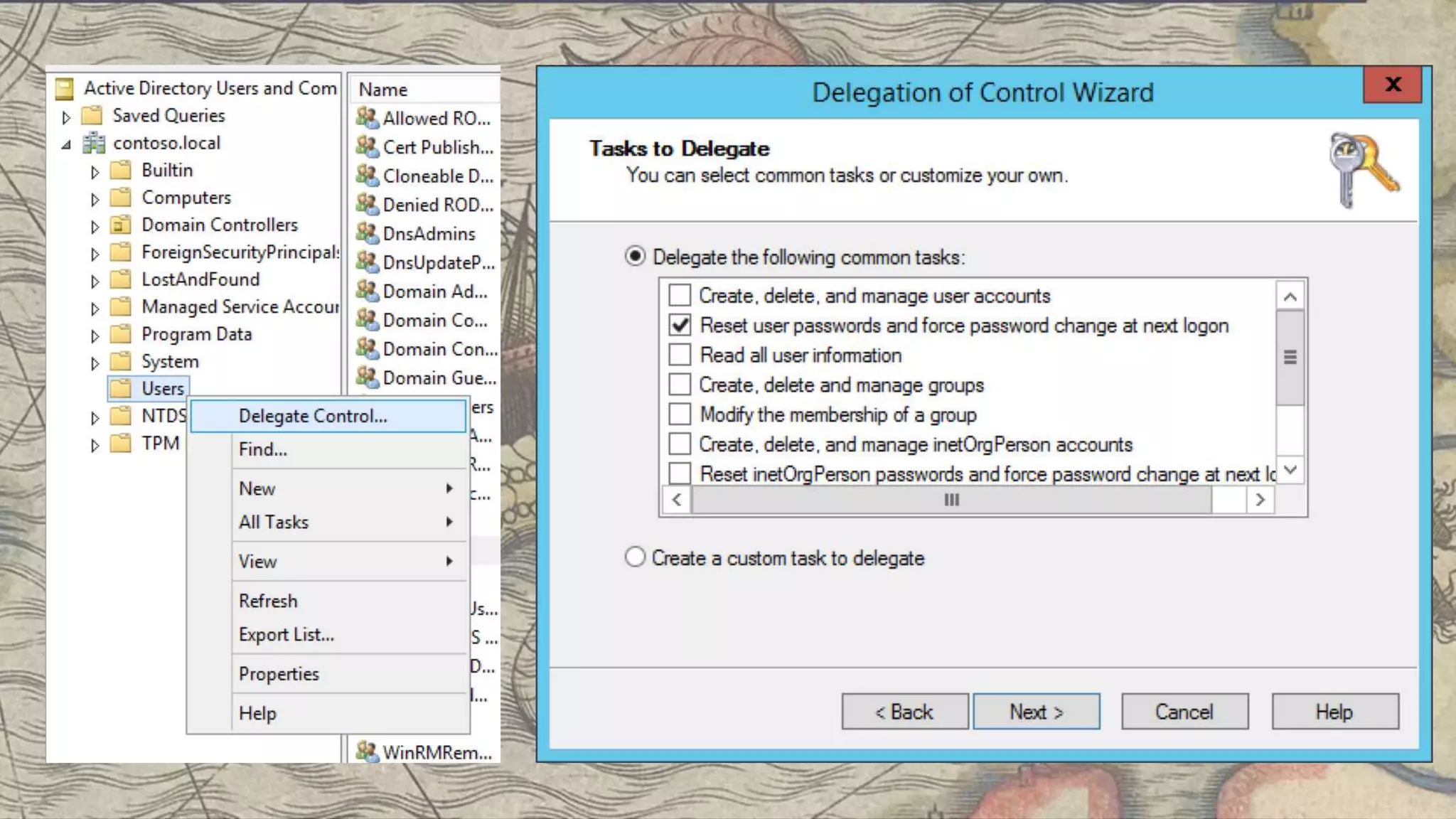
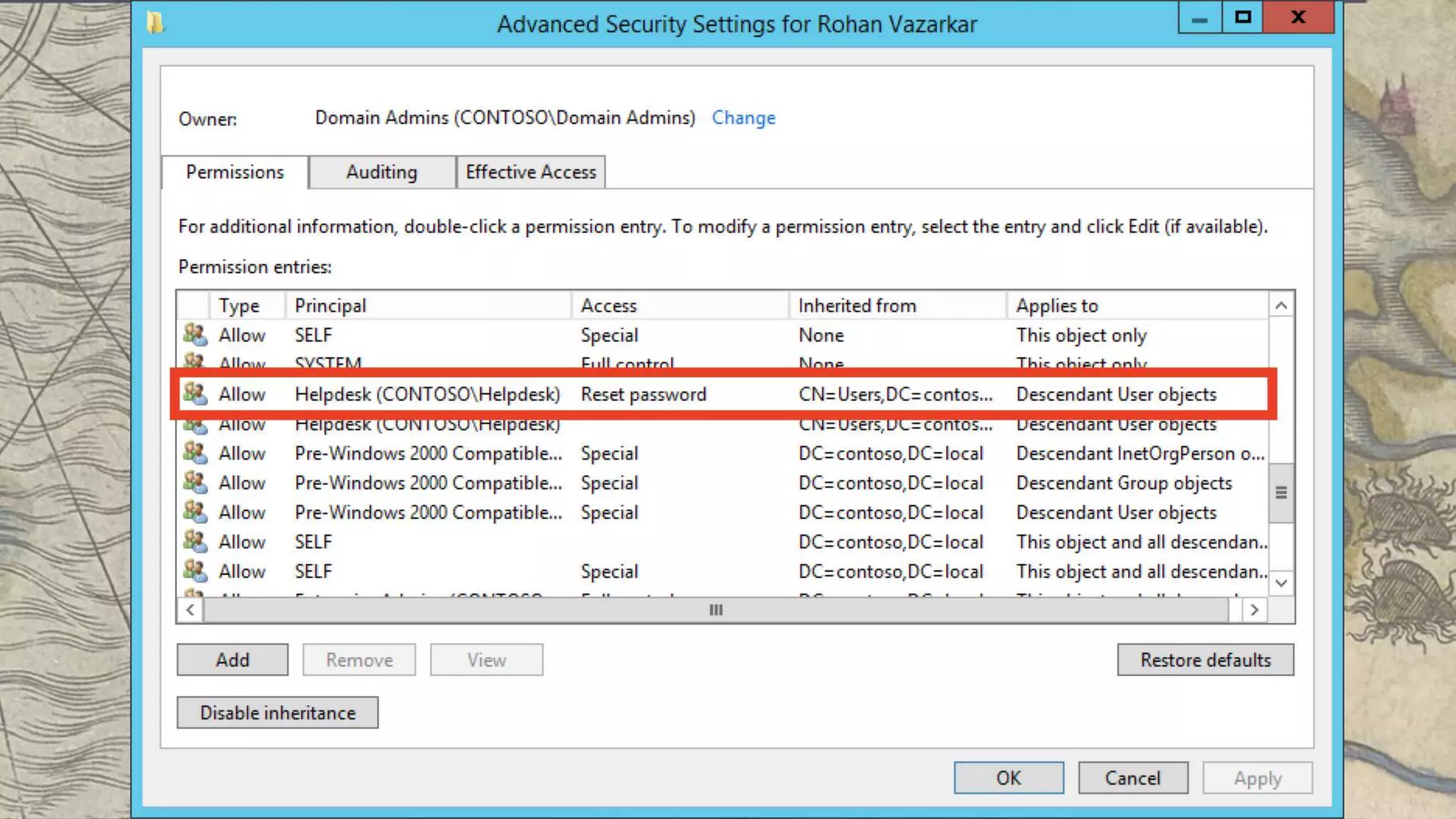
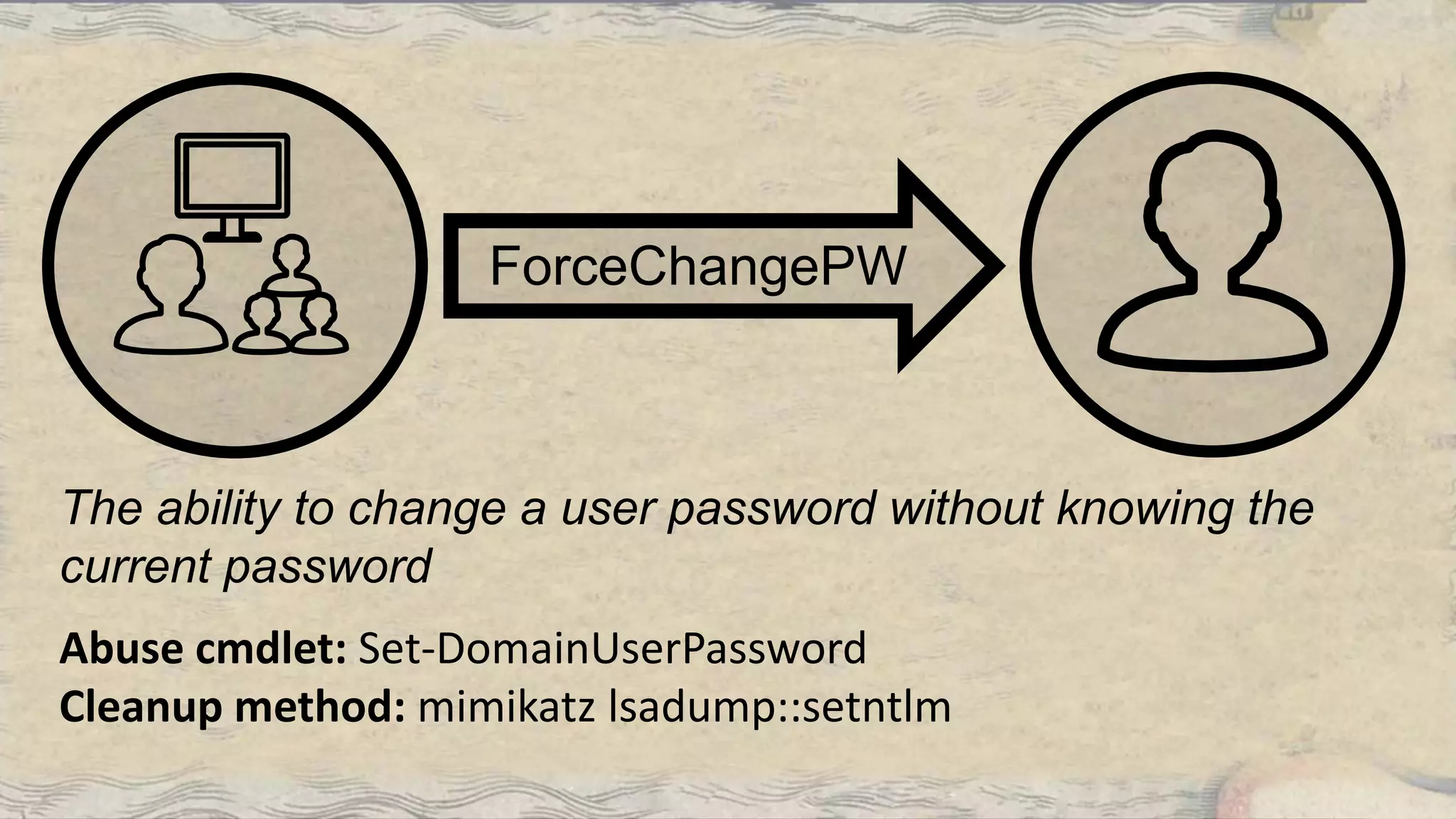
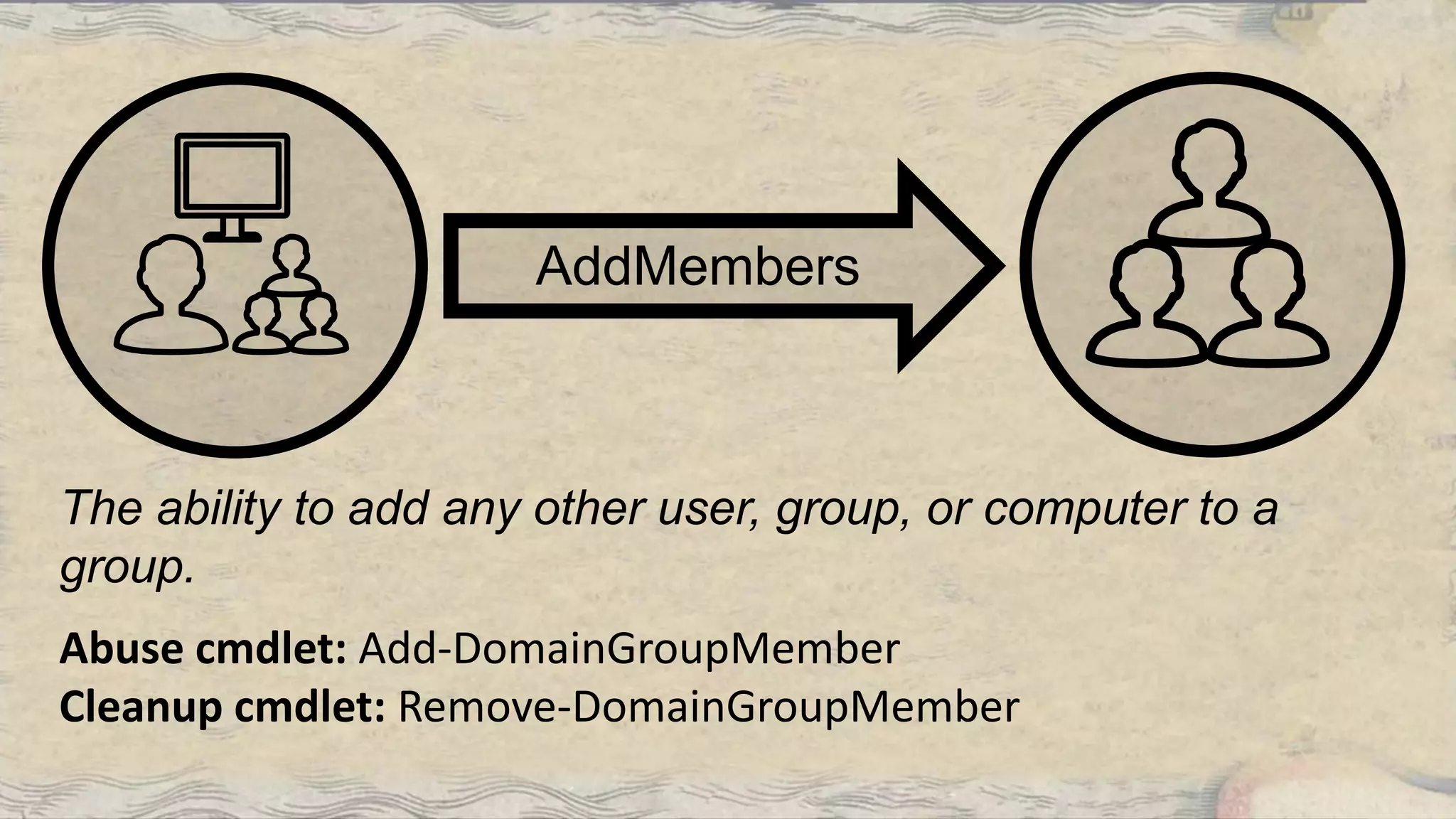
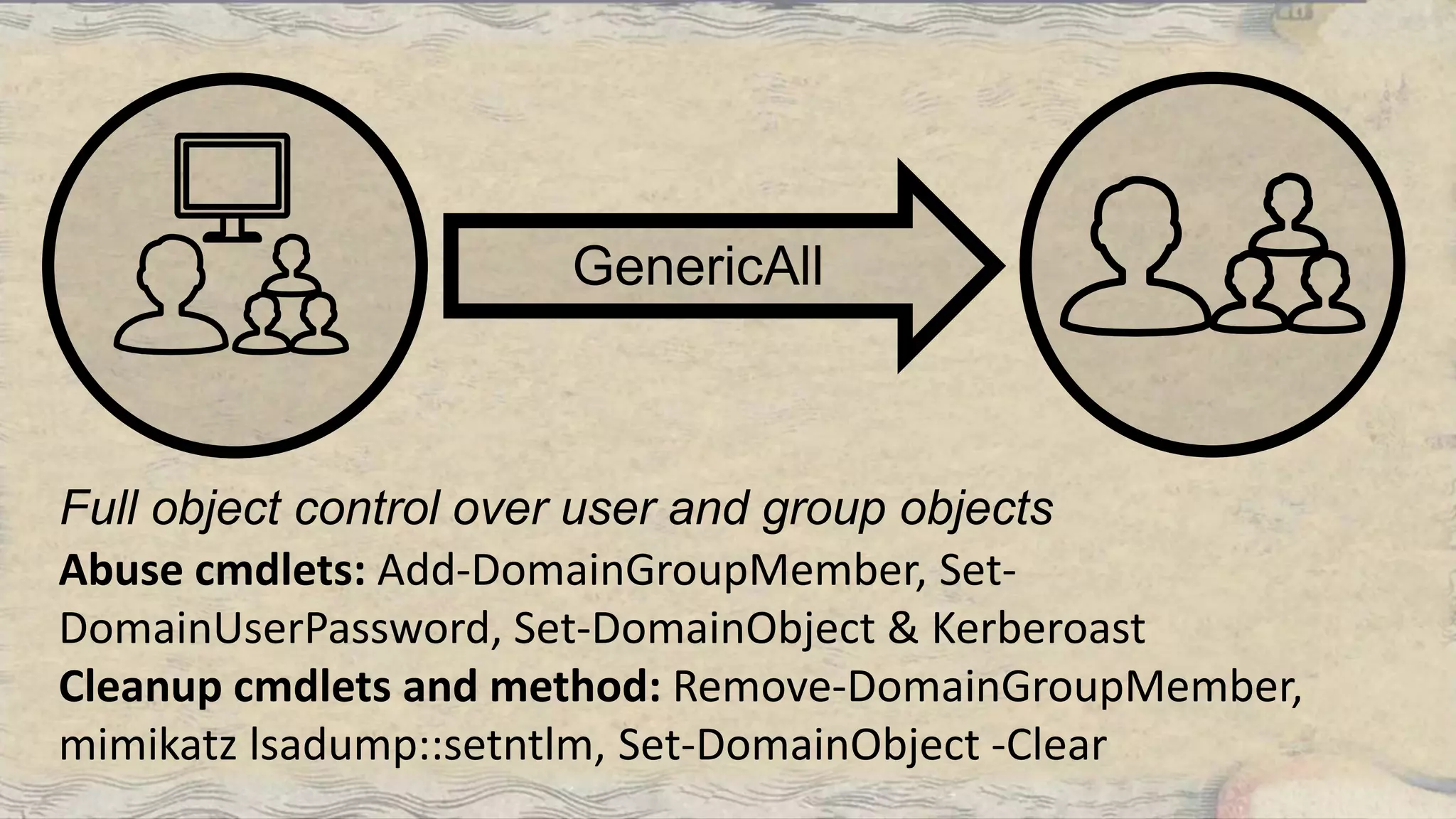
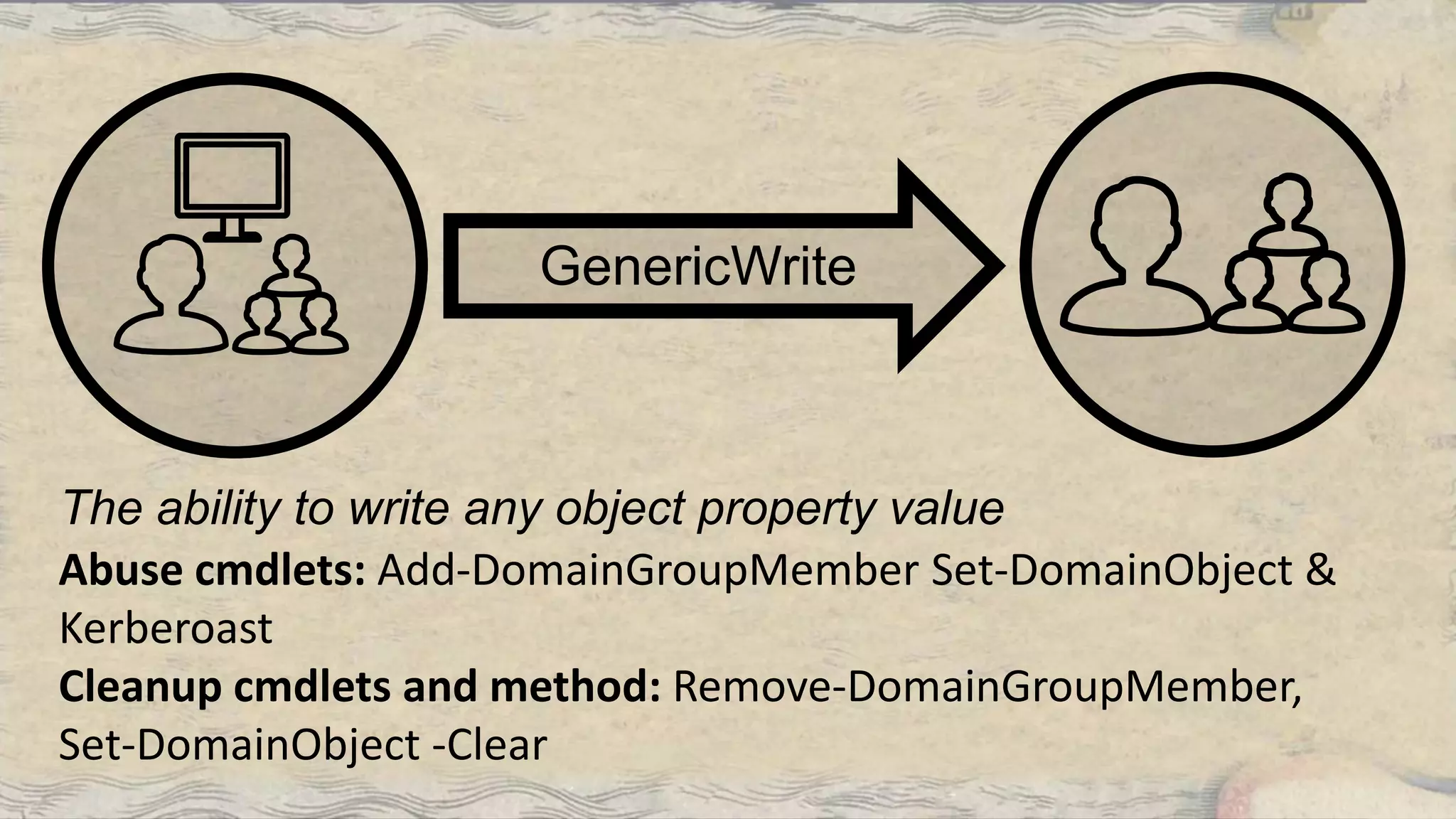
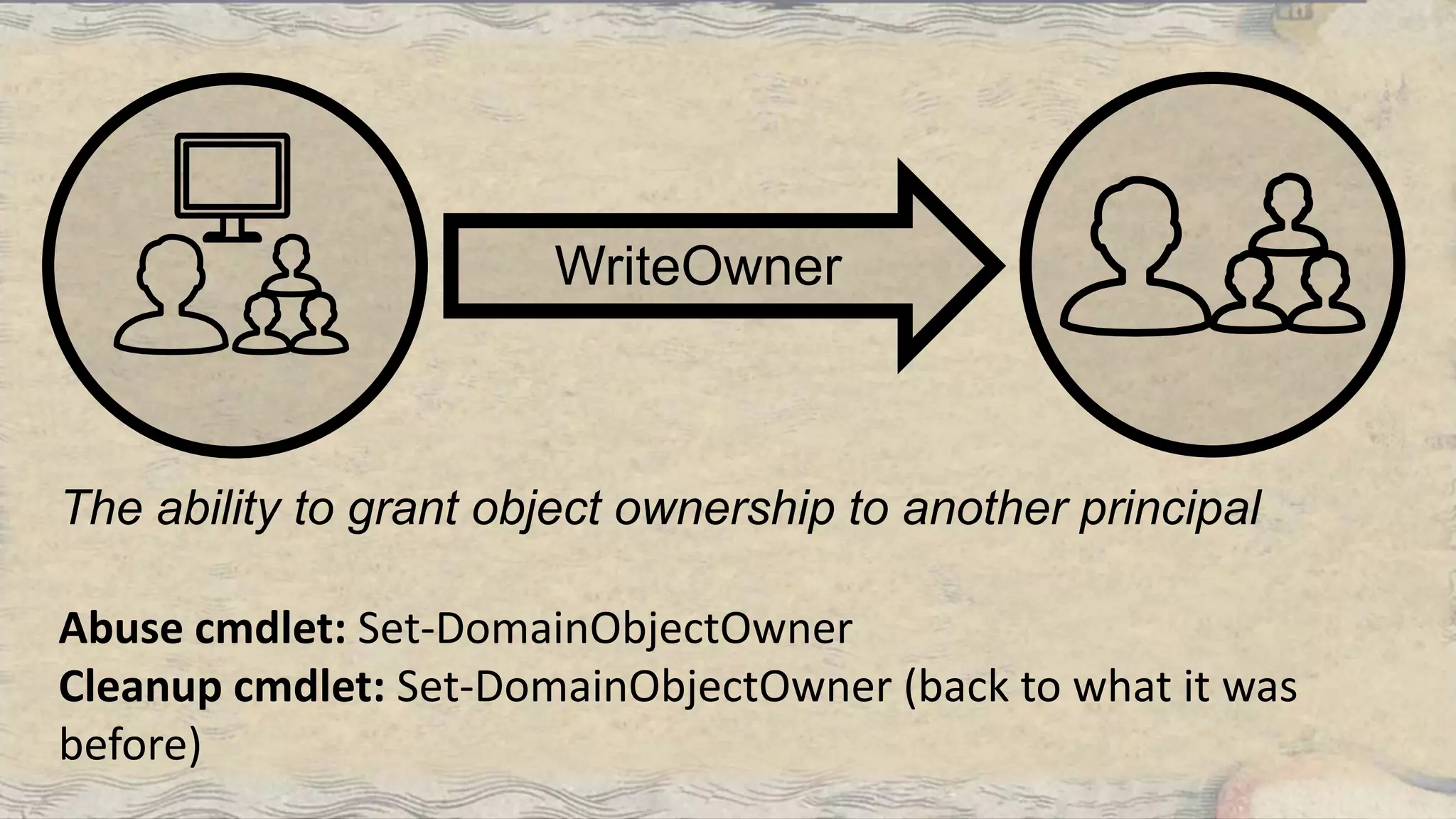
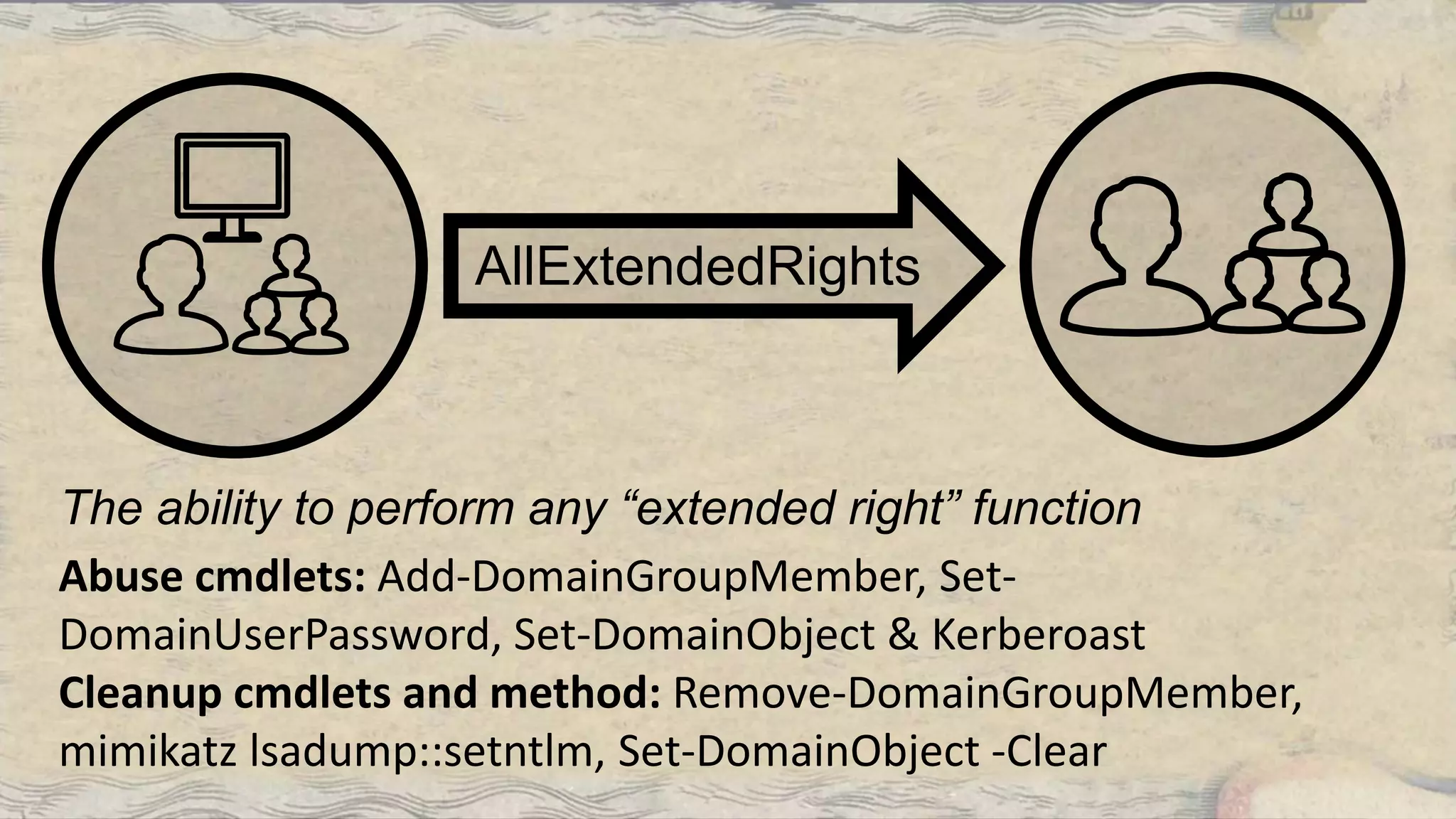
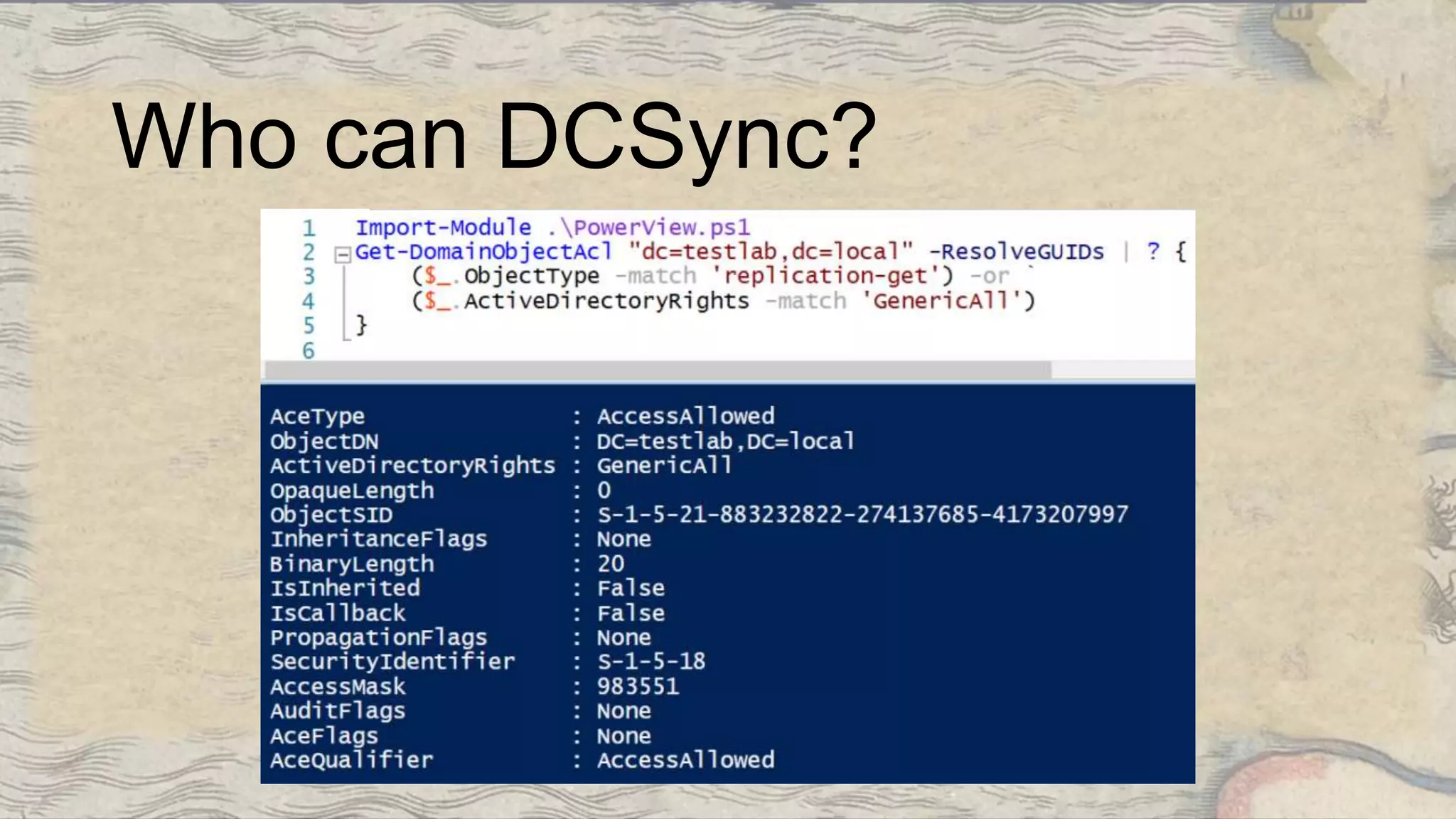
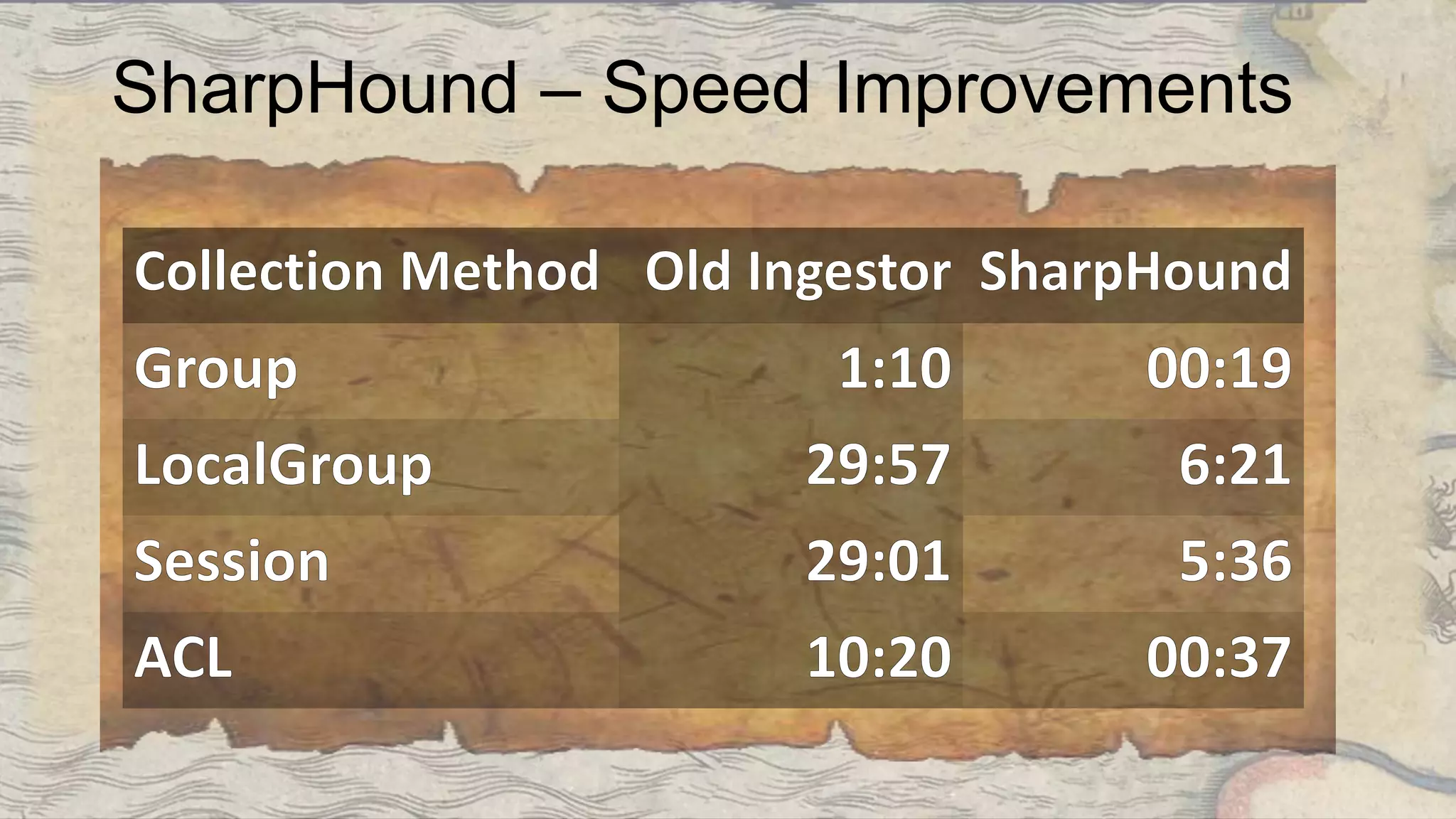
This document summarizes information about three individuals - Andy, Rohan, and Will - who work at Specter Ops creating security tools like BloodHound. It provides details on their jobs, tool development experience, conference presentations, training experience, and Twitter accounts. It then outlines abuse primitives that can be exploited through misconfigurations in Active Directory object ACLs. Finally, it demonstrates how to use tools like PowerView, SharpHound, and BloodHound to find misconfigurations and attack paths in Active Directory.