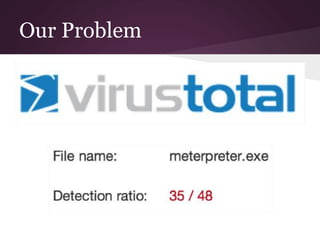
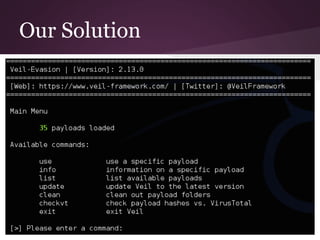
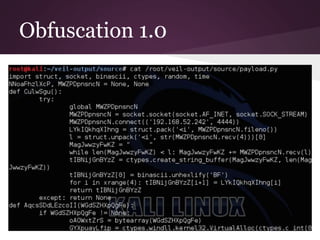
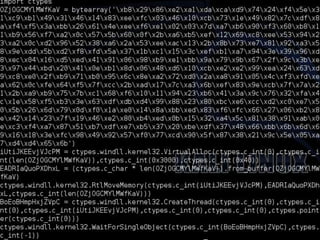
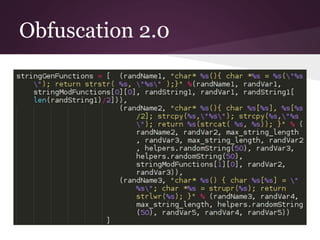
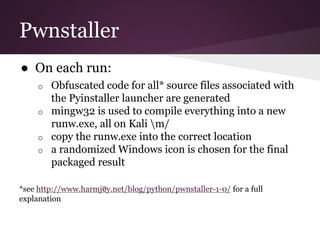
The document discusses innovative techniques for evading antivirus detection by employing various obfuscation methods and payload generation strategies utilized by penetration testers. It highlights the challenges posed by the evolving landscape of cybersecurity and the continuous arms race between security measures and attackers. The author emphasizes the importance of understanding anti-virus limitations and the ethical implications of developing tools that can bypass these defenses.