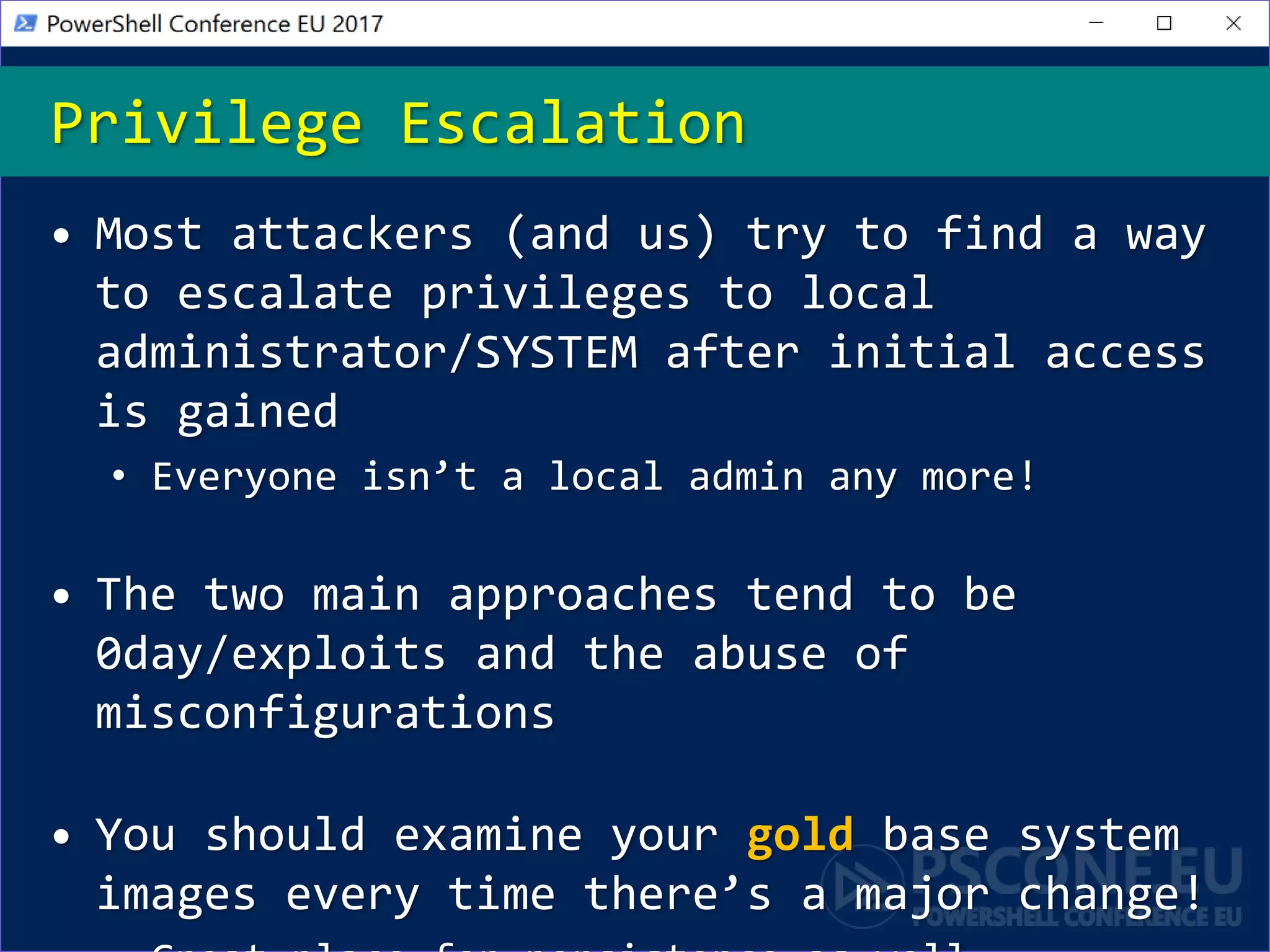
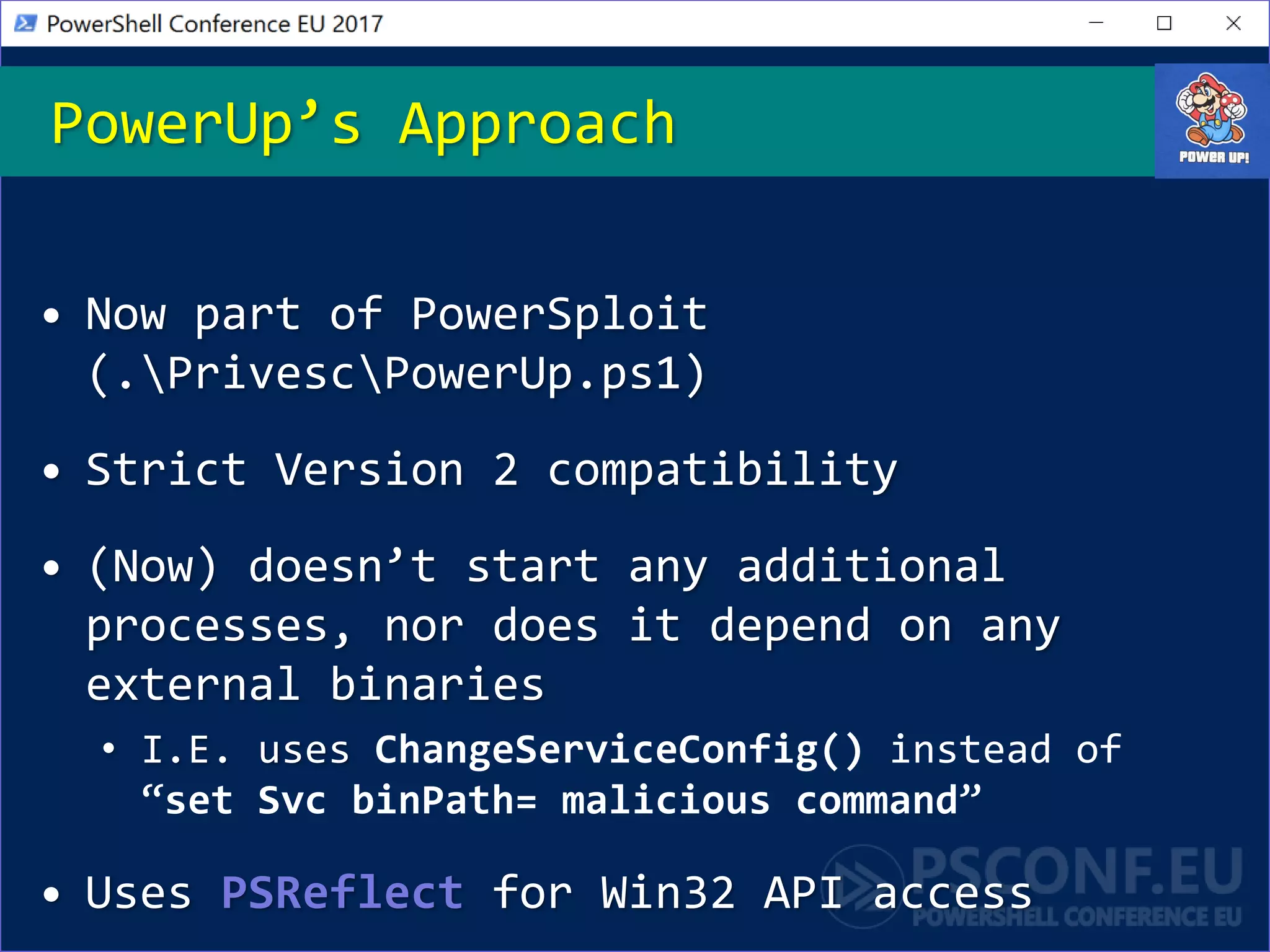
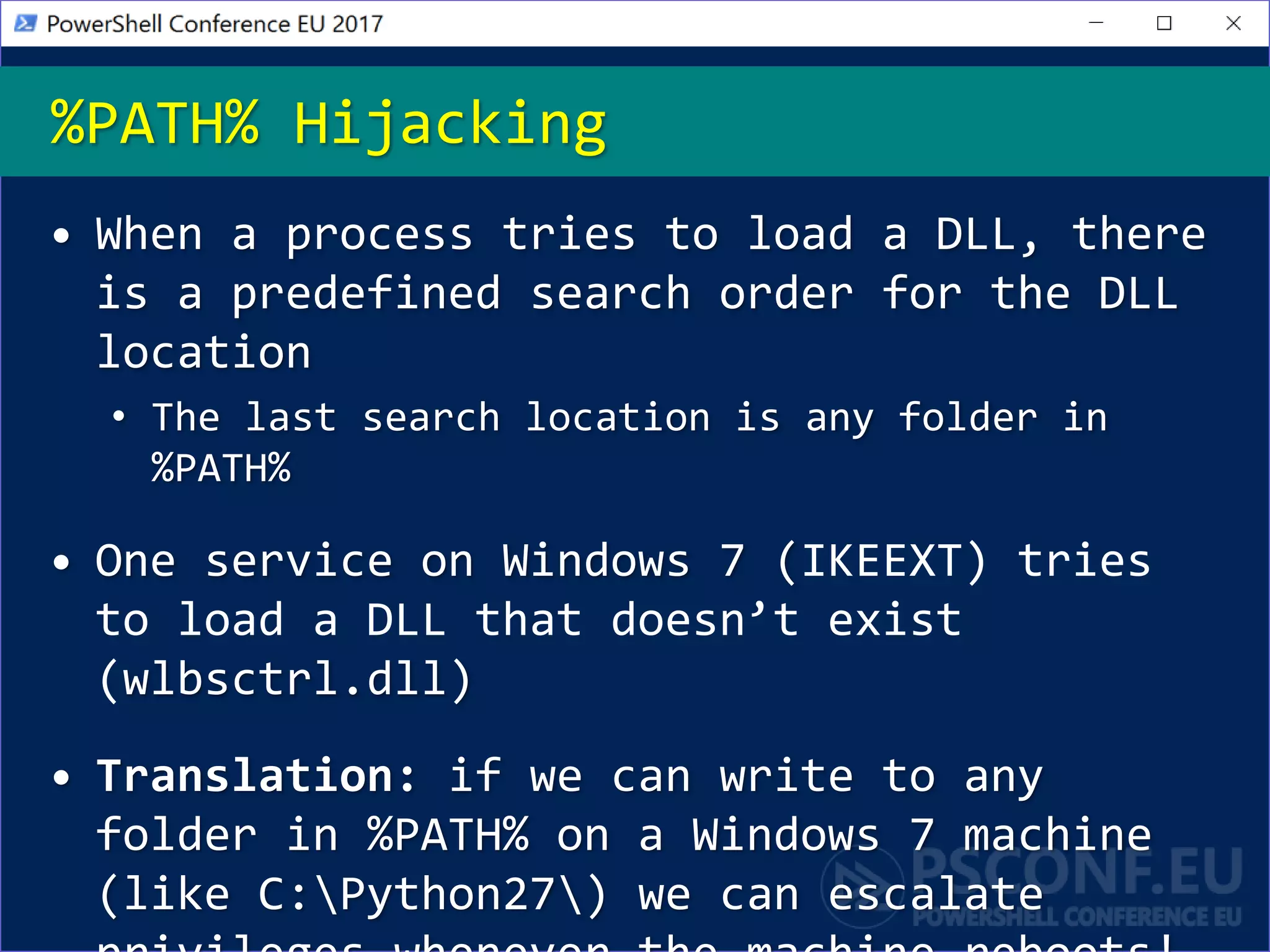
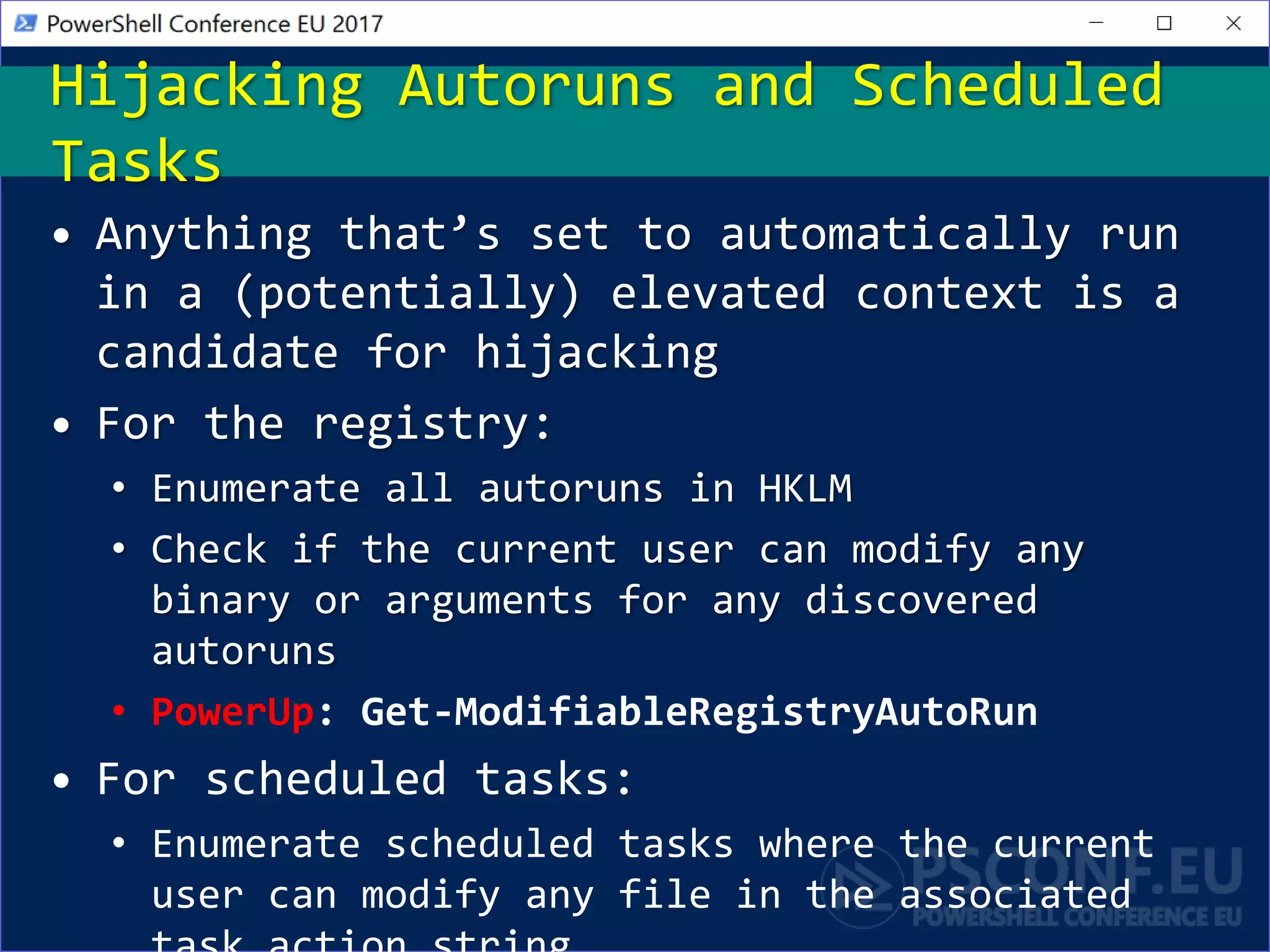
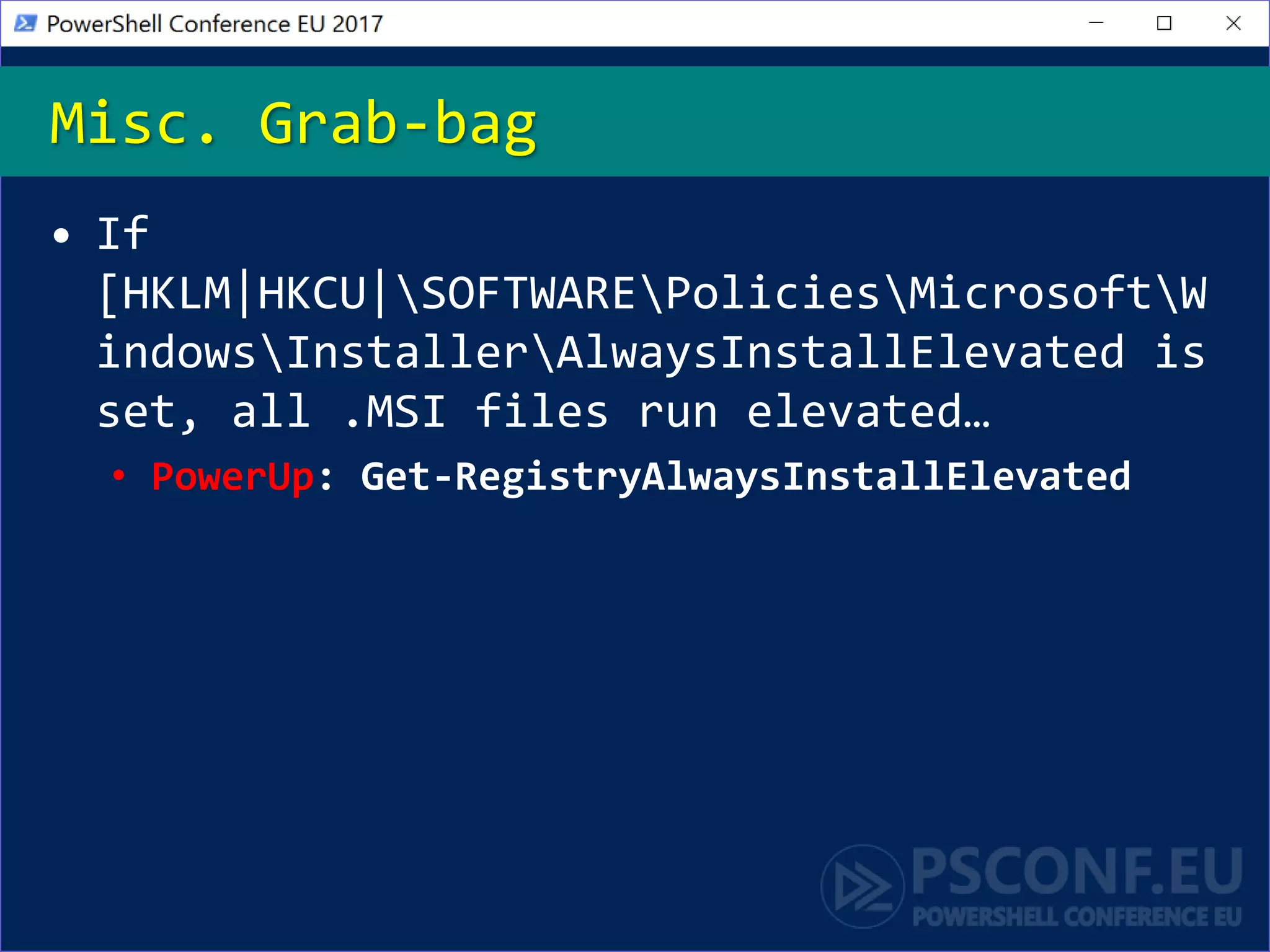
The document discusses techniques for privilege escalation and misconfiguration vulnerabilities in Windows systems, emphasizing the importance of auditing gold base system images after changes. Tools like PowerUp automate the identification of these vulnerabilities, including issues related to service permissions and DLL hijacking. The analysis also highlights risks associated with custom software and unattended installation files that may lead to security breaches.













![• Will Schroeder (@harmj0y)
• http://blog.harmj0y.net | will [at]
harmj0y.net
• Red teamer and offensive engineer for
Specter Ops
• Co-founder:
• Veil-Framework | Empire/EmPyre | BloodHound
• Developer of:
• PowerView | PowerUp | current PowerSploit
developer
• Microsoft CDM/PowerShell MVP
• Veteran trainer
About_Author](https://image.slidesharecdn.com/gold-170514213638/75/Defending-Your-Gold-20-2048.jpg)