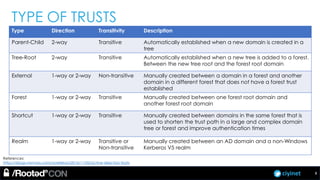
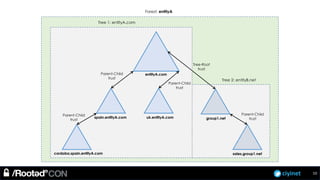
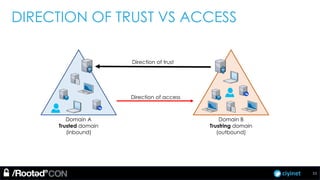
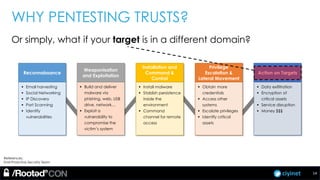
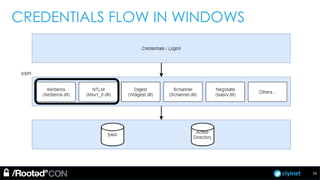
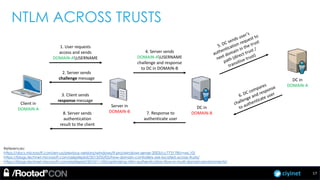
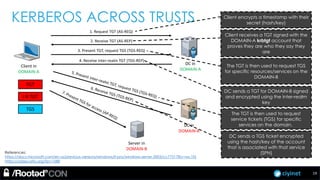
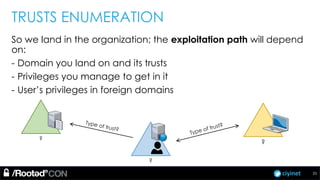
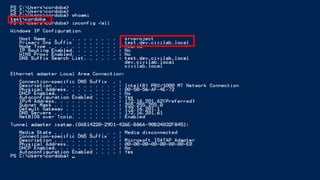
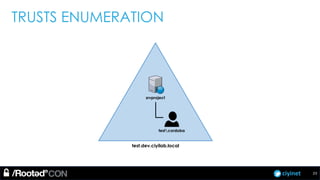
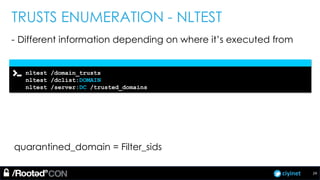
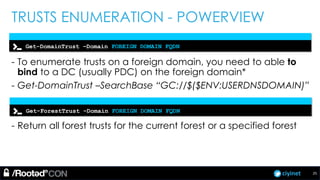
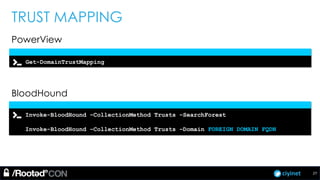
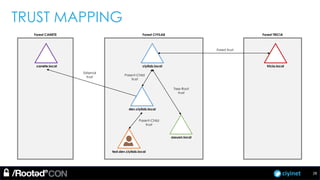
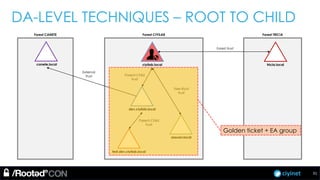
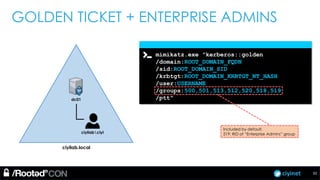
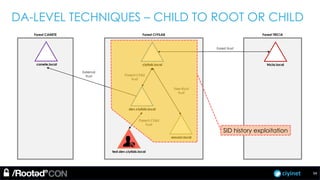
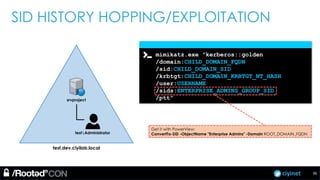
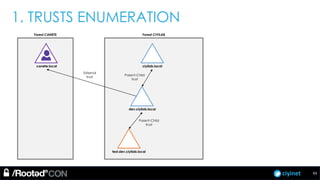
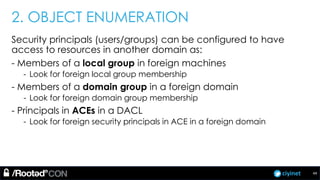
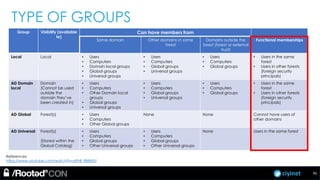
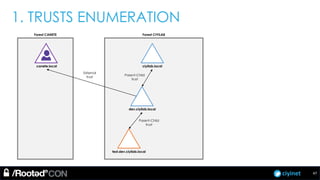
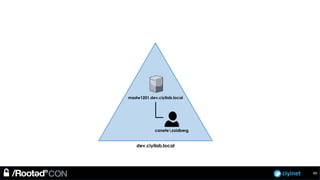
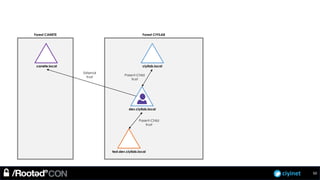
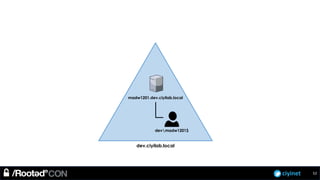
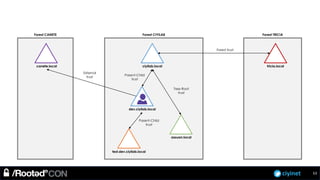
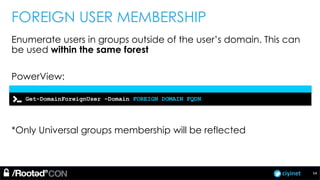
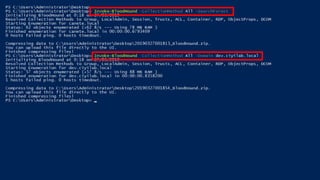
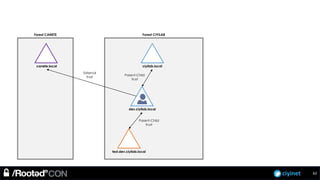
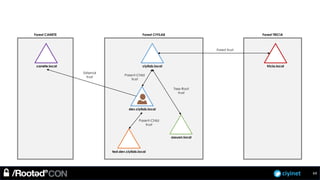
The document discusses penetration testing of Active Directory forests and trusts. It begins with an introduction to forests, domains, and trust types. It then covers authentication protocols like NTLM and Kerberos across trusts. Next, it discusses techniques for enumerating trusts and mapping the trust relationships. The document outlines common attacks when domain admin privileges are available, such as using Golden Tickets and SID history exploitation. For situations without domain admin, it recommends reconnaissance of trusts and objects to map a path to privileged accounts.