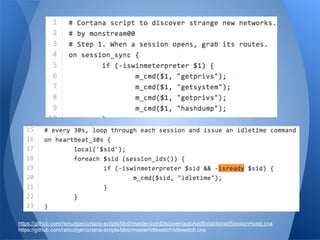
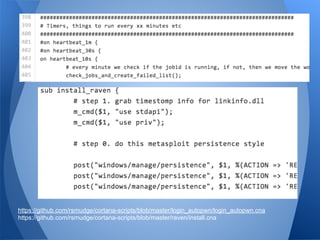
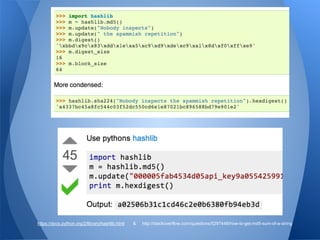
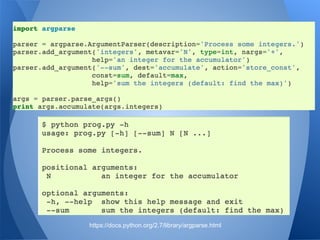
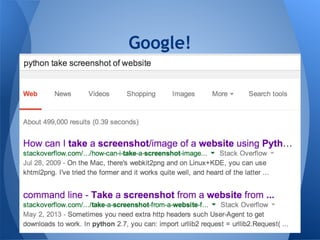
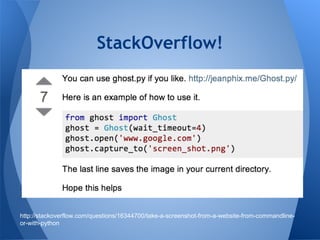
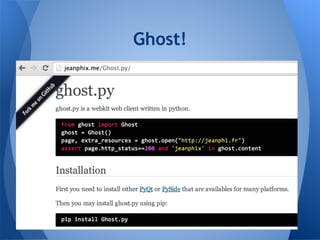
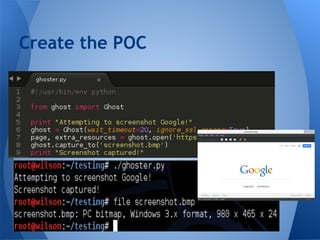
The document presents a talk by a pentester and developer on the importance of scripting and development in security research. It highlights the process of creating functional scripts and frameworks, starting from basic coding principles to more complex tools, specifically focusing on the veil-framework for pentesting. The speaker emphasizes the significance of usability, community involvement, and iterative development in building effective security tools.