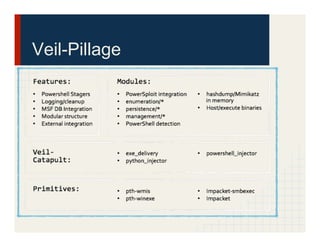
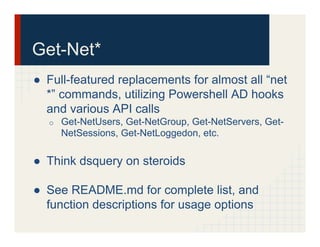
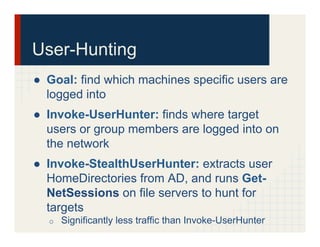
The document discusses the Veil Framework, a set of tools designed for penetration testing and red teaming, emphasizing its capabilities in bypassing antivirus solutions and delivering payloads. It covers the various components of the framework, such as veil-evasion, veil-catapult, veil-pillage, and veil-powerview, and highlights future plans for a major update to the framework. Ethical considerations and community feedback regarding the use of these tools are also addressed.















![How Stagers Work
● 1) a tcp connection is opened to the handler
● 2) the handler sends back 4 bytes indicating
the .dll size, and then transfers the .dll
● 3) the socket number for this tcp connection
is pushed into the edi register
● 4) execution is passed to the .dll just like
regular shellcode (void * or VirtualAlloc)
● reverse_http[s] stagers skip steps 2 and 3](https://image.slidesharecdn.com/thestateoftheveilframework-141114131826-conversion-gate01/85/The-State-of-the-Veil-Framework-20-320.jpg)