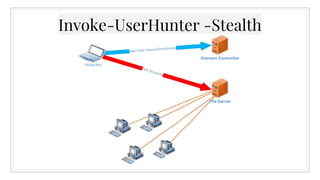
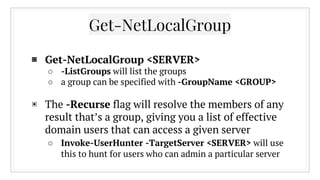
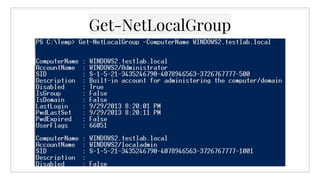
The document provides an overview of offensive Active Directory techniques using PowerShell, focusing on tools like PowerView for enumeration and exploitation. It covers various topics including local administrator enumeration, group policy abuse, Active Directory ACLs, and domain trusts, along with tips for identifying targets and conducting privileged escalation. The author emphasizes the importance of understanding Active Directory's structure to leverage it effectively in red team operations.









![Also: The Pipeline
▣ The PowerShell pipeline allows you to pass full
objects between functions (instead of just strings)
▣ This lets you perform complex chaining and
filtering, allowing you accomplish a lot very
quickly
▣ Users who’ve logged on within the last week:
○ Get-NetUser | ? {$_.lastlogon -gt [DateTime]::Today.
AddDays(-7)} | Sort-Object name](https://image.slidesharecdn.com/ihavethepowerview-160316143143/85/I-Have-the-Power-View-10-320.jpg)


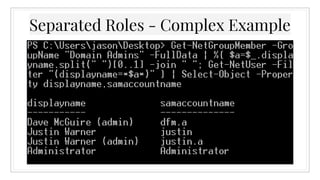
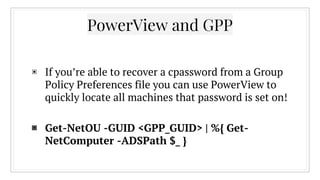
![▣ Get-NetGroupMember -GroupName "Domain
Admins" -FullData | %{ $a=$_.displayname.split
(" ")[0..1] -join " "; Get-NetUser -Filter
"(displayname=*$a*)" } | Select-Object -
Property displayname,samaccountname
Separated Roles - Complex Example](https://image.slidesharecdn.com/ihavethepowerview-160316143143/85/I-Have-the-Power-View-17-320.jpg)



![The WinNT Service Provider
▣ Leftover from Windows NT domain deployments
○ ([ADSI]"WinNT://SERVER/Administrators").psbase.
Invoke('Members') | %{$_.GetType().InvokeMember
("Name", 'GetProperty', $null, $_, $null)}
▣ With an unprivileged domain account, you can use
PowerShell and WinNT to enumerate all members
(local and domain) of a local group on a remote
machine](https://image.slidesharecdn.com/ihavethepowerview-160316143143/85/I-Have-the-Power-View-26-320.jpg)







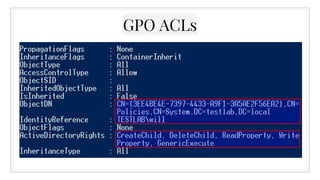
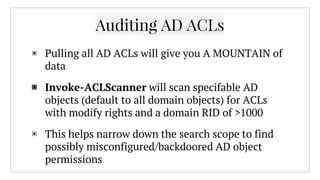
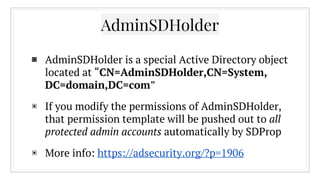
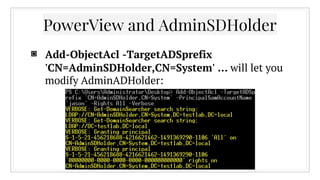
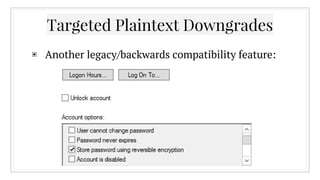
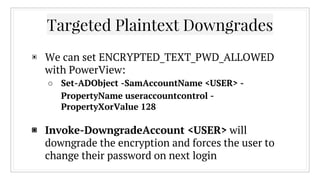
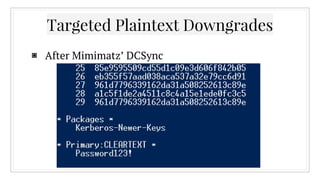

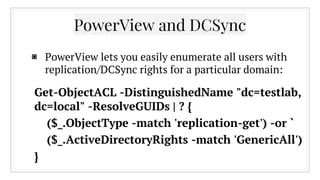










![Any questions?
@harmj0y
http://blog.harmj0y.net/
will [at] harmj0y.net
harmj0y on Freenode in #psempire](https://image.slidesharecdn.com/ihavethepowerview-160316143143/85/I-Have-the-Power-View-70-320.jpg)