The document outlines a week of webinars hosted by SpecterOps, focusing on topics like kerberoasting, adversary tactics, and remote project management. It delves into the mechanics of kerberoasting, including how to exploit service tickets and the various encryption types used in Active Directory. Additionally, it suggests defenses against kerberoasting and introduces tools like Rubeus to enhance offensive capabilities while minimizing exposure and footprint.








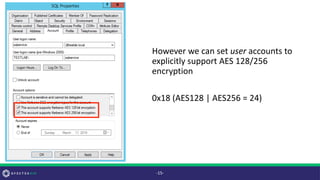
![msDS-SupportedEncryptionTypes
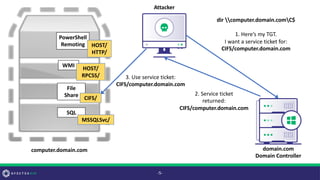
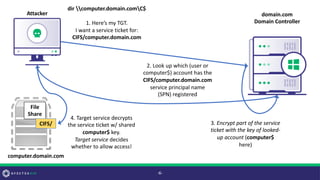
• Active Directory user/computer account property touched on by Jim
Shaver and Mitchell Hennigan in their DerbyCon 7.0 “Return From
The Underworld” talk
• According to Microsoft’s [MS-ADA2], “The Key Distribution Center
(KDC) uses this information [msDS-SupportedEncryptionTypes] while
generating a service ticket for this account.”
• Translation: this property (on an account with a non-null SPN)
determines the encryption used for service tickets requested for that
account’s SPN(s)
-13-](https://image.slidesharecdn.com/harmj0ywebinarkerberoastingrevisited-200408185013/85/SpecterOps-Webinar-Week-Kerberoasting-Revisisted-13-320.jpg)
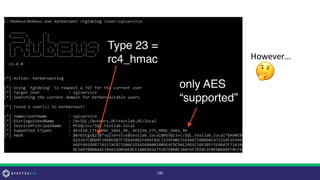
![msDS-SupportedEncryptionTypes
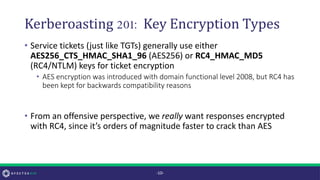
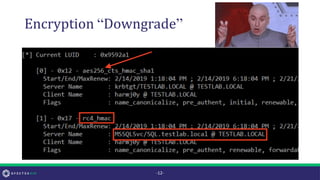
• According to MS-KILE 3.1.1.5 the default value for this field is 0x1C
(RC4 | AES128 | AES256 = 28) for Windows 7+ and Server 2008R2+
• However, this property is only set by default on computer accounts
(not user or trust accounts!)
• If this property is not defined (or is set to 0) [MS-KILE] 3.3.5.7 says default
behavior is to use a value of 0x7 (RC4)
-14-](https://image.slidesharecdn.com/harmj0ywebinarkerberoastingrevisited-200408185013/85/SpecterOps-Webinar-Week-Kerberoasting-Revisisted-14-320.jpg)