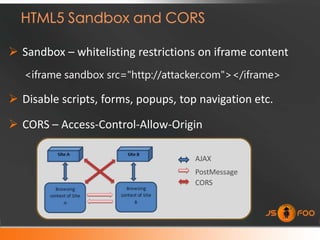
This document discusses security challenges with web applications that combine content from multiple sources (mashups). It covers how the same-origin policy isolates origins but exempts scripts, allowing cross-site scripting attacks. Frame-based communication and the postMessage API provide secure cross-origin messaging capabilities. The document recommends sandboxing iframes and using features like CORS to mitigate risks in mashups.



![ Separate security context for each origin
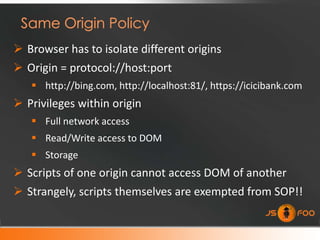
Less interactive than JS approach
Comply with SOP
<!-- This is allowed -->
<iframe src="sameDomainPage.html"> </iframe> //page in same origin
alert(frames[0].contentDocument.body); //works fine
<!-- This is **NOT** allowed -->
<iframe src="http://crossDomain.com"> </iframe> //page outside origin
alert(frames[0].contentDocument.body); //throws error](https://image.slidesharecdn.com/jsfoo-chennai-120219003345-phpapp02/85/JSFoo-Chennai-2012-9-320.jpg)
![ Beware! Frames can be navigated to different origins!
Frame navigation is NOT the same as SOP!
Frame-Frame relationships
Can script in Frame A modify DOM of Frame B?
Can Script in Frame A “navigate” Frame B?
<iframe src=“http://crossDomain.com"> </iframe>
<!-- This is **NOT** allowed -->
alert(frames[0].src); //throws error – SOP restriction
<!-- This is allowed -->
alert(frames[0].src=“http://bing.com”); //works fine - frame navigation](https://image.slidesharecdn.com/jsfoo-chennai-120219003345-phpapp02/85/JSFoo-Chennai-2012-10-320.jpg)
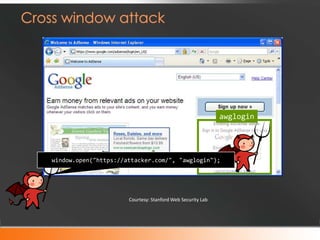
![top.frames[1].location = "http://www.attacker.com/...";
top.frames[2].location = "http://www.attacker.com/...";
...
Courtesy: Stanford Web Security Lab](https://image.slidesharecdn.com/jsfoo-chennai-120219003345-phpapp02/85/JSFoo-Chennai-2012-12-320.jpg)

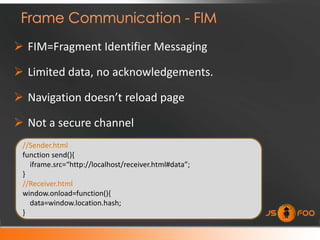

![ Syntax:
otherwindow.postMessage(message, targetOrigin);
targetOrigin can be a trusted source/wildcard *“*”+
//Posting message to a cross domain partner.
frames[0].postMessage(“Hello Partner!”, "http://localhost:81/");
//Retrieving message from the sender
window.onmessage = function (e) {
if (e.origin == 'http://localhost') {
//sanitize and accept data
}
};](https://image.slidesharecdn.com/jsfoo-chennai-120219003345-phpapp02/85/JSFoo-Chennai-2012-16-320.jpg)