This document discusses various web application security vulnerabilities and methods for mitigating them. It begins by summarizing the OWASP Top 10 list of most critical web application security risks. It then provides examples of different types of injection attacks, cross-site scripting, broken authentication and session management issues. The document also discusses insecure cryptographic storage, insufficient transport layer protection and other vulnerabilities. It emphasizes the importance of input and output validation, as well as proper encoding to prevent attacks. The OWASP ESAPI framework is presented as a tool to help developers address many of these security issues.







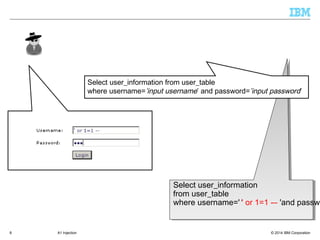
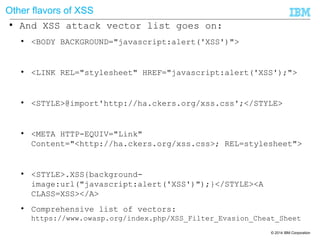
![© 2014 IBM Corporation9 A1 Injection
Xpath injection
FindUserXPath becomes :
//Employee[UserName/text()='blah' or 1=1 or 'a'='a' And
Password/text()='blah']
Web Server Application Server
User Database
User
https
FindUserXPath = "//Employee[UserName/text()='" + Request("Username")
+ "' And Password/text()='" + Request("Password") + "']";
<?xml version="1.0" encoding="utf-8"?>
<Employees>
<Employee ID="1">
<FirstName>Arnold</FirstName>
<LastName>Baker</LastName>
<UserName>ABaker</UserName>
<Password>SoSecret</Password>
<Type>Admin</Type>
</Employee>
<Employee ID="2">
<FirstName>Peter</FirstName>
<LastName>Pan</LastName>
<UserName>PPan</UserName>
<Password>NotTelling</Password>
<Type>User</Type>
</Employee>
</Employees>](https://image.slidesharecdn.com/webapplicationsecurity-140319051153-phpapp01/85/Web-Apps-Security-9-320.jpg)
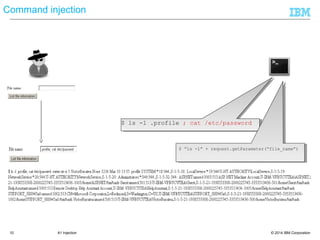






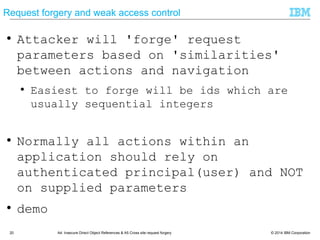


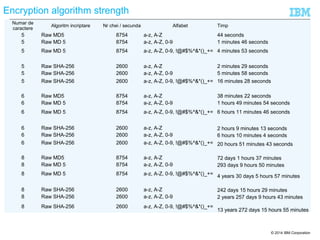
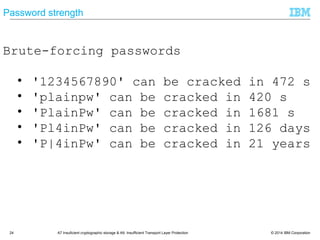






![© 2014 IBM Corporation33
Encoding of output example
● A developer can also encode output. Using the ESAPI.encoder() you
can generate safe HTML, Js, CSS,...
● Below we are encoding this string → <>"'%&.()[]@#//-+
– Encoding for HTML :
– <>"'%&.()[]&#x
40;#//-+
– Encoding for CSS :
– 3c 3e 22 27 25 26 2e 28 29 5b 5d 40 23 2f 2f
2d 2b
– Encoding for JS :
– x3Cx3Ex22x27x25x26.x28x29x5Bx5Dx40x23x2Fx2Fx
2Dx2B
– Encoding for html attribute :
– <>"'%&.()[]&#x
40;#//-+](https://image.slidesharecdn.com/webapplicationsecurity-140319051153-phpapp01/85/Web-Apps-Security-33-320.jpg)

